
The Secure Remote Access capability provides a workflow for ICS operators, that enables them to define the access policies both for devices and staff to be remotely connected. The system also provides full auditing for the remote ICS network access. The idea of remote access is not entirely new for ICS systems.
How secure is remote access architecture in ICS?
Ideally, remote connections into ICS should pass through the demilitarized zone (DMZ) between the IT and OT segments, and in this edition of the series we will take a closer look at secure remote access architecture. Firewalls, authentication services, jump servers, and file servers all play crucial roles in conducting these connections securely.
How to manage remote access to industrial control systems?
From the DMZ, after authentication, user-initiated remote access should follow a trusted path to the industrial control system—where the user will authenticate again, this time using the local identity and access management solution for the industrial control system. All remote access communications should be logged and monitored.
What is a remote access solution?
Specific remote access solution: there are specific devices and solutions that provide secure remote access to OT. These are solutions that include hardware and/or software elements to control which ports and applications are exposed to the external network and which users can access them.
What are Industrial Control Systems (ICS)?
Industrial control systems (ICS) were designed for operations. Meaning they were designed to accept commands from good guys—from engineers. The idea that a malicious actor would enter bad commands to jeopardize reliability, cause equipment failure, or otherwise risk safety is not something that designers had ever considered.
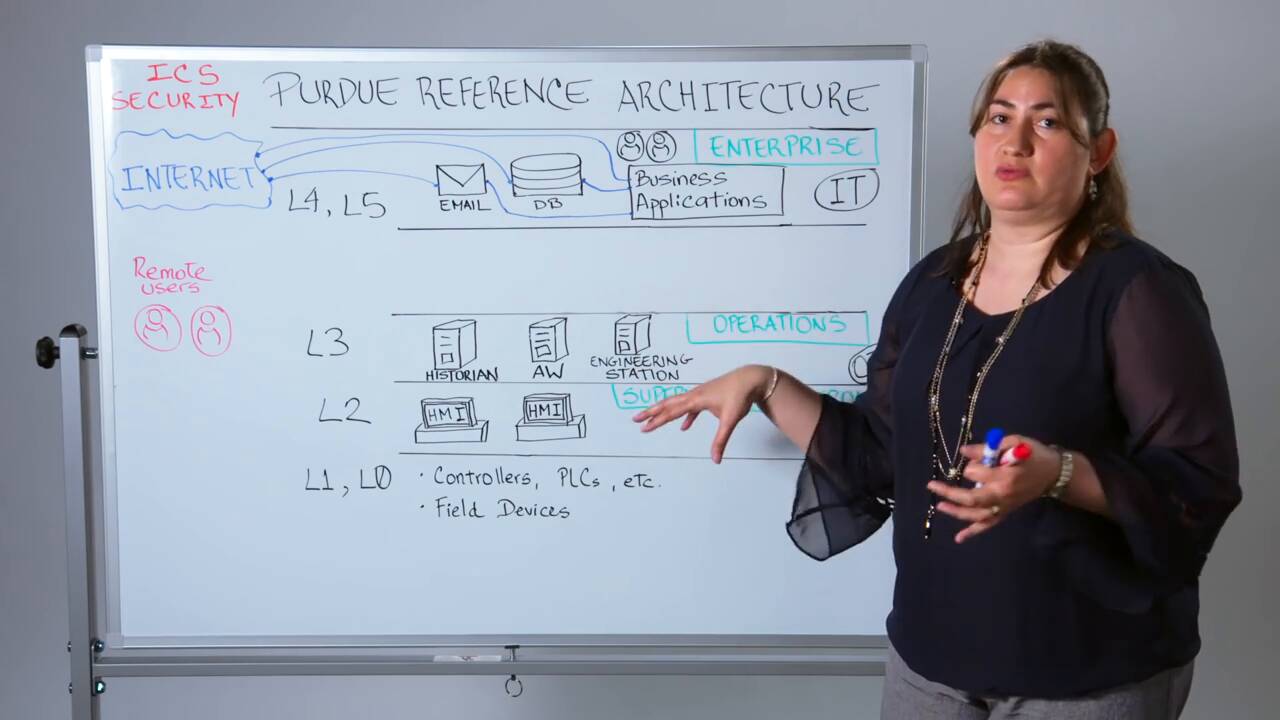
What is ICS security?
ICS security is the area of concern involving the safeguarding of industrial control systems, the integrated hardware and software designed to monitor and control the operation of machinery and associated devices in industrial environments.
What is an ICS network?
ICS are command and control networks and systems designed to support industrial processes. The largest subgroup of ICS is SCADA (Supervisory Control and Data Acquisition) systems.
What is an ICS device?
What is an Industrial Control System (ICS)? ICS assets are the digital devices that are used in industrial processes. This includes all of the various components of critical infrastructure (power grid, water treatment, etc.), manufacturing, and similar applications. A number of different devices are classified as ICS.
What is the difference between ICS and Scada?
I use both terms together because SCADA is often better known by the press, government officials and the public, but ICS is probably the technically correct term to use if you are referring to industrial automation of all types. Traditionally “SCADA” is used for control systems that cover a wide geographic area.
Why is ICS security important?
NIST's Guide to Industrial Control Systems (ICS) Security helps industry strengthen the cybersecurity of its computer-controlled systems. These systems are used in industries such as utilities and manufacturing to automate or remotely control product production, handling or distribution.
What are the main elements of a typical ICS system?
The Incident Command System comprises five major functional areas: Command, Operations, Planning, Logistics, and Finance/Administration.
How does incident command system work?
The Incident Command System or ICS is a standardized, on-scene, all-risk incident management concept. ICS allows its users to adopt an integrated organizational structure to match the complexities and demands of single or multiple incidents without being hindered by jurisdictional boundaries.
Is a PLC an ICS?
This article will detail the different types of ICS, including Programmable Logic Controllers (PLC), Distributed Control Systems (DCS), Supervisory Control and Data Acquisition (SCADA) and Industrial Automation and Control Systems (IACS).
What is ICS DMZ?
Up-to-date security patches and anti-malware updates for both the plant IT system and the ICS. The DMZ is a buffer zone between the plant network and the ICS through which all traffic to the ICS must pass. It should be protected on both sides by firewalls with restrictive rule sets.
What is SCADA security?
SCADA Security is broad term used to describe the protection of SCADA networks. These networks are made up of computer hardware and applications and are utilized to control and monitor vital infrastructure in nations where they are employed.
What is ICS analyst?
The ICS/SCADA Security Analyst skill path provides you with the knowledge needed to defend the systems that control critical infrastructure. You'll learn about assessing the security of industrial control and SCADA systems and protecting them from cyber threats.
What is the difference between IT and OT?
IT/OT convergence is the integration of information technology (IT) systems with operational technology (OT) systems. IT systems are used for data-centric computing; OT systems monitor events, processes and devices, and make adjustments in enterprise and industrial operations.
What is Scada in cyber security?
Supervisory control and data acquisition (SCADA) networks are widely used in modern industrial organizations to monitor and analyze real-time data, control both local and remote industrial processes, interact with devices, and log data and events for auditing and other purposes.
IoT and modern Industrial Connectivity allow manufacturers to access ICS and remotely monitor their plants
Not long ago, on-site access, control and maintenance to Industrial Control Systems was the only way for operators and managers to get to know what was going on the factory floor. For an organisation to make changes of any nature to critical systems, it was crucial to have readily available onsite engineers and support.
How does secure remote access work?
Remote Access is a plant optimisation system that let your team connect to ICS remotely through Virtual Desktop Interfaces. Basically, it mirrors your plant’s systems, so operators and managers can access the factory floor data through a “virtually direct” connection to the SCADA, HMIs, PLCs, IACs and other systems.
Committing to a SECURE Remote Access System
Zero Trust. That is all you need to commit to a Remote Access solution. No, really... it has been calculated that the industry loses about $100, 560 million per minute when their productive systems are stopped due to unpredicted maintenance, systems intrusion, or malfunctioning. And that number does not include ransoms demanded by hackers.
Benefits of having a SECURE Remote Access
Secure Remote Access to ICS allows quick efficiency wins, helping accelerate the strategic pipeline of production by securely grant access to real-time manufacturing data from every system, on any device, to those who have authorised access to it. Remote Access systems also make virtual commissioning and predictive maintenance more streamlined.
Virtual Commissioning and its Importance
Virtual commissioning or Remote Commissioning involves performing certain functions (designing, installation, testing, control) on industrial control systems through a virtual machine or VDI to avoid system errors. Using a secure cloud connection, you have now remote access to your plants’ systems from anywhere in the world.
What is remote access?
Remote access is a relatively new capability for industrial control systems —one that comes with specific engineering and financial benefits. However, when considering new remote access connections, organizations need to involve the necessary stakeholders to make security and reliability-based decisions.
What are remote access requirements?
Remote access requirements should be determined, including what IP addresses, what communication types, and what processes can be monitored. All others should be disabled by default. Remote access including process control should be limited as much as possible.
Why is on site support important?
If an organization was going to make any changes – digital or otherwise – to critical systems often under 24/7 operating conditions, it was important to have engineers and support readily available . Financially such support can be expensive and difficult to coordinate across many disparate stakeholders. So, in the age of connectivity, many of these systems were retrofitted or re-engineered to include remote monitoring and access in order to lessen the burden for organizations and increase visibility into operations. While TCP/IP connections in OT environments were becoming increasingly popular in the early 2000s, many organizations were learning the hard way that cybersecurity needs to be “built in” and not “bolted on” later.
Do not enable remote access?
First and foremost, do not enable remote access by default. This is not a strict anti-remote access stance— rather a pro-engineering discussion. Because remote access is a “gate” through the (hopefully robust) perimeter and moat and walls of your fort, you want to make sure it is secure. This requires multiple stakeholders to be involved, including OT security, IT security, engineering, vendors, and any maintenance support teams. It is not something that is easily pre-packaged and it is never a “set it and forget it” capability.
What was the ICS environment before the Internet?
Prior to the arrival of the Internet, the ICS/OT environment at most organizations was “air-gapped”, meaning it had no connections to external networks. As a result, network security measures were not major considerations for ICS. As discussed in Part One of this series, however, the persistence of this mindset into the Internet era must be overcome, as ICS environments are now more connected and relied upon for real-time operational data. Subsequently, they have become high-value targets to threat groups.
How to secure file transfers over remote connections?
This method requires the technician to first plug the USB drive into a server at this location that scans all the files on the USB drive and copies the “cleaned” files to another USB drive plugged into the server. The technician then takes the “cleaned” USB drive and uses it to transfer the files onto a particular ICS system.
How to remote access OT?
Remote connectivity for OT staff should require two separate steps: a VPN connection into the ICS DMZ, followed by a second connection using hardened Remote Desktop (RD) via a jump host (or jump server) that provides carefully controlled, role-based access into OT systems.
How to address vendor impatience with security protocols?
To address user or vendor impatience with security protocols, administrators must strike the balance between effective security and ease of use. If vendor personnel require their own remote access connection into ICS, ensure that they are truly authorized, and put appropriate access controls in place, adhering to least-privilege and zero-trust principles so these users can only perform the tasks required of them. If possible, disable these connections by default and enable them manually only when required. Work with vendors to figure out their requirements and build a suitable solution that includes appropriate security controls. If the vendor requires a dedicated connection for monitoring, ensure that it runs through the remote access DMZ and is restricted to only a single segment of the network, by way of a jump server if possible.
What zone should remote access be in?
Ideally, remote connections into ICS should pass through the demilitarized zone (DMZ) between the IT and OT segments, and in this edition of the series we will take a closer look at secure remote access architecture. Firewalls, authentication services, jump servers, and file servers all play crucial roles in conducting these connections securely.
What is remote connection?
To clarify, the remote connections to which we’re referring are connections from the Internet and/or an organization’s business network into its OT environment. These connections provide access to devices residing at Levels 3 and below of the Purdue Enterprise Reference Architecture, which we covered in depth in Part Two of this series:
Why is remote access important?
The benefits of remote access connections into ICS are so significant that many organizations now rely on these types of connections in their day-to-day operations. For example, when an organization needs to check, reprogram, or update their ICS, flying a vendor technician to the site from another location is far less preferable than having the technician remotely connect to the equipment to immediately perform the work with no travel cost. Remote access is also preferable for ongoing management of ICS located at remote field sites because it enables one technician to manage several sites, maximizing his/her efficiency.
