What is the difference between IKEv2 and IPsec profile?
NOTE: you can also create a crypto map which is the legacy way, while IPSEC profile is the newer way. Note: you can use IKEv2 for Remote Access VPN as well but it will need to work with remote authentication server (RADIUS) when you configure on Cisco ASA and it will not allow you to create users locally.
What is the IKEv2?
What is the IKEv2? IKE stands for Internet Key exchange, it is the version 2 of the IKE and it has been created to provide a better solution than IKEv1 in setting up security association (SA) in IPSEC. Why the IKEv2?
Can I use IKEv2 with Cisco ASA remote access VPN?
Note: you can use IKEv2 for Remote Access VPN as well but it will need to work with remote authentication server (RADIUS) when you configure on Cisco ASA and it will not allow you to create users locally. but you might be able to do a workaround if you edit the group policy after you finish the configuration like below:
How do I associate an IKEv2 profile with a crypto map?
An IKEv2 profile must be configured and associated with either a crypto map or an IPsec profile on the IKEv2 initiator. Use the set ikev2-profile profile-name command to associate a profile with a crypto map or an IPsec profile.
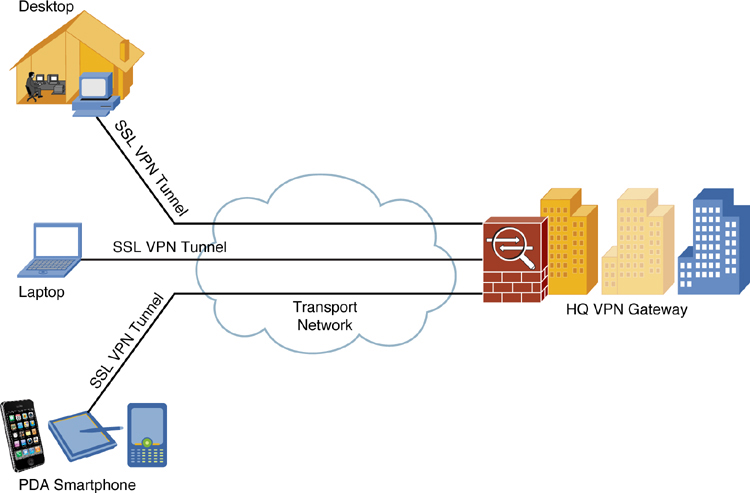
How do I enable IKEv2 on my Cisco router?
To enable IKEv2 on a crypto interface, attach an IKEv2 profile to the crypto map or IPsec profile applied to the interface. You need not enable IKEv1 on individual interfaces because IKEv1 is enabled globally on all interfaces in the router.
Which is better IKEv2 or IPSec?
IPSec is considered secure and reliable, while IKEv2 is extremely fast and stable – IKEV2 offers quick re-connections when switching networks or during sudden drops. Thus, a combination of IKEv2/IPsec forms one of the best VPN protocols that exhibits the advantages of the two.
Is Cisco Anyconnect a remote access VPN?
Anyconnect VPN offers full network access. The remote user will use the anyconnect client to connect to the ASA and will receive an IP address from a VPN pool, allowing full access to the network. Above we have the ASA firewall with two security zones: inside and outside.
Does Cisco ASA support IKEv2?
IKEv2 has been published in RFC 5996 in September 2010 and is fully supported on Cisco ASA firewalls.
How does IKEv2 IPSec work?
Working together, IKEv2 uses a few data packets to establish a security association with the server. It then takes all the data – the IP addresses, the security measures used, the ports utilized in the connection – and gives it to IPsec, which then uses the security associations to encrypt the traffic.
What is IKEv2 VPN Iphone?
Internet Key Exchange version 2 (IKEv2) is the default VPN setting for iOS. The IKEv2 is used to create a security association in the IPSec (Internet Protocol Security) suite. A security association (SA) establishes shared security attributes between two network entities to support secure communication.
What type of VPN is Cisco AnyConnect?
Cisco AnyConnect VPNs utilize TLS to authenticate and configure routing, then DTLS to efficiently encrypt and transport the tunneled VPN traffic, and can fall back to TLS-based transport where firewalls block UDP-based traffic.
Is Cisco AnyConnect VPN free?
Cisco AnyConnect is a free, easy to use, and worthwhile VPN client for Microsoft Windows computers. It's secure and doesn't require a lot of maintenance.
How does Cisco AnyConnect VPN client work?
When a user opens a VPN session using Cisco AnyConnect, the AnyConnect client connects to the adaptive security appliance using SSL. The client authenticates with the adaptive security appliance and is assigned an internal IP address on the network.
What is the difference between IKEv1 and IKEv2?
IKEv2 uses four messages; IKEv1 uses either six messages (in the main mode) or three messages (in aggressive mode). IKEv2 has Built-in NAT-T functionality which improves compatibility between vendors. IKEv2 supports EAP authentication. IKEv2 has the Keep Alive option enabled as default.
What ports does IKEv2 use?
By default, IKEv2 uses IPSec, which requires UDP ports 500 and 4500, and ESP IP Protocol 50.
How do I enable IKEv1 on Cisco ASA?
Enable IKEv1 on the the interfaceIntroduction.Define the Encryption Domain.Specify the Phase 1 Policy.Specify the Phase 2 Proposal.Define the connection profile.Configure the Crypto Map.Bind the Crypto Map to the interface.Enable IKEv1 on the the interface.
Is IKEv2 and IPSec the same?
IKEv2 (Internet key exchange version 2) is part of the IPSec protocol suite. Standardized in RFC 7296. IPSec has become the defacto standard protocol for secure Internet communications, providing confidentiality, authentication and integrity. Open-source VPN protocol developed by OpenVPN technologies.
What is the difference between IKEv2 and IPSec?
IKEv2 stands for Internet key exchange version two, and IPSec refers to the Internet protocol security suite. Together, they form a VPN protocol.
Is IKEv2 more secure?
Security: IKEv2 is much more secure than IKEv1. IKEv2 uses leading encryption algorithms and high-end ciphers such as AES, Camellia, and ChaCha20. IKEv2 also uses encryption keys for both sides while IKEv1 doesn't, making it more secure.
Does IKEv2 use IPSec?
IKEv2 works by using an IPSec-based tunneling protocol to establish a secure connection.
What is AnyConnect's default IKE?
Note: AnyConnect uses '*$AnyConnectClient$*' as its default IKE identity of type key-id. However, this identity can be manually changed in the AnyConnect profile to match deployment needs.
When to use profile in AnyConnect?
The profile is used when it is being selected from the drop-down list of AnyConnect address bar. The name that will appear is the same name as specified in "Display Name" in AnyConnect profile editor. In this example the user should select the following:
Can you configure eap before local authentication?
Note: Configuring the remote authentication method before the local authentication method will be accepted by the CLI, but will not take effect on versions that do not have the fix for the enhancement request CSCvb29701, if the remote authentication method is eap. For these versions, when configuring eap as the remote authentication method, ensure the local authentication method is configured as rsa-sig first. This problem is not seen with any other form of remote authentication method.
How to set up a VPN?
Setup the VPN Connection ¶ 1 Leave Local ID blank 2 Set User Authentication to Username 3 Enter the Username and Password
What is the username for EAP-MSCHAPv2?
With EAP-MSCHAPv2 the Username is the Identifier configured for the user’s entry on the Pre-Shared Keys tab under VPN > IPsec . With EAP-RADIUS this would be the username set on the RADIUS server.
Does iOS 9 have IKEv2?
As of version 9, iOS has built-in support for IKEv2 that can be configured from the GUI without requiring a VPN Profile. As with other clients, the CA Certificate must be installed.
What does IKE stand for in IPSEC?
IKE stands for Internet Key exchange, it is the version 2 of the IKE and it has been created to provide a better solution than IKEv1 in setting up security association (SA) in IPSEC.
Which is newer, IPSEC or crypto?
NOTE: you can also create a crypto map which is the legacy way, while IPSEC profile is the newer way.
What is IKE profile?
The IKE Profile Based Tunnel Selection feature uses the Internet Key Exchange (IKE) or Internet Key Exchange version 2 (IKEv2) profile to select a tunnel interface for an IPsec session. Use keywords isakmp-profile or ikev2-profile keyword in the tunnel protection command to specify an IKE profile or IKEv2 profile respectively.
What is DVTI Easy VPN?
The DVTI Easy VPN server can be configured behind a virtual firewall. Behind-the-firewall configuration allows users to enter the network, while the network firewall is protected from unauthorized access. The virtual firewall uses Context-Based Access Control (CBAC) and NAT applied to the Internet interface as well as to the virtual template.
What is flexvpn mixed mode?
The FlexVPN Mixed Mode feature provides support for carrying IPv4 traffic over IPsec IPv6 transport. This is the first phase towards providing dual stack support on the IPsec stack. This implementation does not support using a single IPsec security association (SA) pair for both IPv4 and IPv6 traffic.
What is SVTI configuration?
SVTI configurations can be used for site-to-site connectivity in which a tunnel provides always-on access between two sites.
When is IPsec session closed?
The interface is deleted when the IPsec session to the peer is closed. The IPsec session is closed when both IKE and IPsec SAs to the peer are deleted.
How to add QoS to DVTI?
You can add QoS to the DVTI tunnel by applying the service policy to the virtual template. When the template is cloned to make the virtual access interface, the service policy will also be applied to the virtual access interface. The following example shows the basic DVTI configuration with QoS added.
Can you fragment packets in IPsec tunnel?
Fragmentation is not supported over IPsec tunnel. You can choose to set the lower MTU on hosts to avoid packet fragments or choose to fragment the packets on any device before it reaches ASR 920.
What is IKEv2?
Internet Key Exchange version 2, IKEv2 for short, is a request/response protocol developed by both Cisco and Microsoft. It is used to establish — and secure — IPv4/IPv6 connections, be it a site-to-site VPN or from a road-warrior connecting to a hub site. IKEv2, when run in point-to-multipoint, or remote-access/road-warrior mode, secures the server-side with another layer by using an x509 signed server certificate — thus we needed a better way to handle server certificates than we did in the past by simply dropping them as files into the /config/auth directory.
What is the IPv4 address for Remote Access Pool?
We provide one IPv4 and IPv6 pool. Authorized clients will receive an IPv4 address from the 192.0.2.128/25 prefix and an IPv6 address from the 2001:db8:2000::/64 prefix. We can also send some DNS nameservers down to our clients used on their connection.
What encryption is supported by Vyos?
Encryption is supported with up to 256-bit and can use ciphers like AES, 3DES, Camellia, and ChaCha20. This is nothing new, as we already support this for site-to-site VPNs as early as of VyOS 1.1.
What is IPSec profile import?
During profile import, the user is asked to enter its IPSec credentials (username and password) which is stored on the mobile. If a custom CA is used that is not present on your mobile — no problem — we will always embed the CA certificate into the profile so that you won't experience any certificate issues.
Can VyOS be used as an IPSec gateway?
Configuring VyOS to act as your IPSec access concentrator is one thing, but you also need to setup your client connecting to the server so they can talk to the IPSec gateway.
Is Vyos a strong VPN?
VyOS was always strong in supporting a multitude of different VPN techniques ranging from old school IPsec site-to -site/DMVPN setups to new kids on the block like SSTP, OpenVPN, and WireGuard. Today I want to present a new feature that was added to VyOS in the current 1.4 (Sagitta) development cycle — IKEv2 remote-access VPN.
Is Vyos a cloud service?
VyOS can be deployed on Azure, which is a Microsoft Cloud provider offering more than 600 IaaS, PaaS, and SaaS Services. While Microsoft centric Azure also supports open and 3rd party software so your environments are not just limited to Windows platforms. Users can also deploy and manage Azure infrastructure with their DevOps tools of choice, including Hashicorp’s Terraform and Red Hat Ansible.
