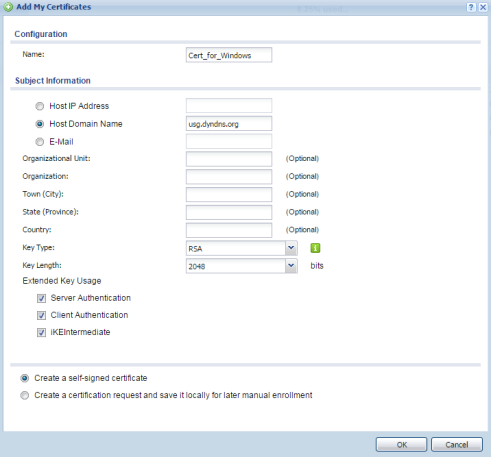
How to setup IKEv2 on Windows 10?
Windows 10 IPSec with IKEv2 Setup Guide
- Open the Control panel by clicking the start menu icon and typing control
- Click Network and Internet followed by Network and Sharing Centre
- Click Setup a new connection or network
- Click Connect to a workplace, then click Next
- Click Use my Internet connection (VPN)
How to setup PureVPN manually on Windows 7 IKEv2?
Insert the following info:
- Enter IKEv2 in the description field.
- Enter the server address. Click here to get the server list.
- Please enter pointtoserver.com in the “Remote ID” field.
- Enter your PureVPN credentials. Here is how you can find your VPN credentials.
- Tap Done
How to manually configure a VPN on Windows 10?
- Right-click the Start button.
- Click Settings. Source: Windows Central
- Click Network & Internet.
- Click VPN. Source: Windows Central
- Click Add a VPN connection.
- Click the dropdown menu below VPN provider. Source: Windows Central
- Click Windows (built-in).
- Click the Connection name field. ...
- Type a name for the VPN connection. ...
- Click the Server name or address field. ...
How to set up a VPN manually?
- Create an account on the VPN website. Go to the official website of the desired VPN provider ( e.g. ...
- Download the VPN software from the official website. ...
- Install the VPN software. ...
- Log in to the software with your account. ...
- Choose the desired VPN server (optional). ...
- Turn on the VPN. ...
How do I enable IKEv2 on my Cisco router?
To enable IKEv2 on a crypto interface, attach an IKEv2 profile to the crypto map or IPsec profile applied to the interface. You need not enable IKEv1 on individual interfaces because IKEv1 is enabled globally on all interfaces in the router.
Does AnyConnect use Ike?
Each of those products only supported their own protocol however with the introduction of Anyconnect Secure Mobility Client 3.0, the client can now use IPsec (IKEv2) or SSL for the transport of the VPN connection.
Does Cisco ASA support IKEv2?
IKEv2 has been published in RFC 5996 in September 2010 and is fully supported on Cisco ASA firewalls.
How do I configure IKEv2?
Make sure you can reach all the devices by pinging all IP Addresses.Step 1: Configure Host name and Domain name in IPSec peer Routers. ... Step 2: Define IKEv2 Keyring. ... Step 3: Define IKEv2 Proposal. ... Step 4: Define IKEv2 Policies. ... Step 5: Define Crypto ACL to identify IPSec secured traffic. ... Step 6: Define Transform Sets.More items...
What type of VPN is Cisco AnyConnect?
Cisco AnyConnect VPNs utilize TLS to authenticate and configure routing, then DTLS to efficiently encrypt and transport the tunneled VPN traffic, and can fall back to TLS-based transport where firewalls block UDP-based traffic.
Does Cisco AnyConnect use IPsec or SSL?
Anyconnect is the replacement for the old Cisco VPN client and supports SSL and IKEv2 IPsec. When it comes to SSL, the ASA offers two SSL VPN modes: Clientless WebVPN.
Which is better IKEv2 or IPSec?
IPSec is considered secure and reliable, while IKEv2 is extremely fast and stable – IKEV2 offers quick re-connections when switching networks or during sudden drops. Thus, a combination of IKEv2/IPsec forms one of the best VPN protocols that exhibits the advantages of the two.
What ports does IKEv2 use?
By default, IKEv2 uses IPSec, which requires UDP ports 500 and 4500, and ESP IP Protocol 50.
What is the difference between IKEv1 and IKEv2?
IKEv2 uses four messages; IKEv1 uses either six messages (in the main mode) or three messages (in aggressive mode). IKEv2 has Built-in NAT-T functionality which improves compatibility between vendors. IKEv2 supports EAP authentication. IKEv2 has the Keep Alive option enabled as default.
How do I get IKEv2?
How to set up IKEv2 VPN protocolDownload the NordVPN app for your device.Launch the NordVPN app.Go to Settings.Choose the IKEv2 VPN Protocol.Enjoy a fast and safe VPN connection!
What is IKEv2 IPSec or l2tp?
Internet Key Exchange version 2 (IKEv2) is one of the latest VPN protocols developed by Cisco and Microsoft. It is suitable for mobile platforms across all devices. IKEv2 is seen paired with IPSec for encryption and authentication.
How do I troubleshoot IKEv2?
Suggestions: Troubleshoot connectivity between Aviatrix gateway and peer VPN router. Verify that both VPN settings use the same IKEv2 version. Verify that all IKEv2/IPsec algorithm parameters (i.e., Authentication/DH Groups/Encryption) match on both VPN configuration.
How do I troubleshoot IKEv2 tunnel?
Suggestions: Troubleshoot connectivity between Aviatrix gateway and peer VPN router. Verify that both VPN settings use the same IKEv2 version. Verify that all IKEv2/IPsec algorithm parameters (i.e., Authentication/DH Groups/Encryption) match on both VPN configuration.
What is crypto map in Asa?
Static crypto map - identifies peer and traffic to be encrypted explicitly.
What is PRF in IPsec?
A Pseudo-Random Function (PRF) is similar to an integrity algorithm, but instead of being used to authenticate messages, it is only used to provide randomness for purposes such as keying material.
What is sha96?
HMAC-SHA–96. In the System Management Agent, the Secure Hash Algorithm (SHA) implementation is HMAC-SHA–96. This one-way encryption uses a 96–bit hash and a 20–octet key length. The algorithm takes as input a message of less than 264 bits in length. The input message is processed in 512–bit blocks.
What is AnyConnect's default IKE?
Note: AnyConnect uses '*$AnyConnectClient$*' as its default IKE identity of type key-id. However, this identity can be manually changed in the AnyConnect profile to match deployment needs.
When to use profile in AnyConnect?
The profile is used when it is being selected from the drop-down list of AnyConnect address bar. The name that will appear is the same name as specified in "Display Name" in AnyConnect profile editor. In this example the user should select the following:
Does AnyConnect need to be delivered to the client machine?
Note: The AnyConnect profile needs to be delivered to the client machine. Please refer to the next section for more information.
Can you configure eap before local authentication?
Note: Configuring the remote authentication method before the local authentication method will be accepted by the CLI, but will not take effect on versions that do not have the fix for the enhancement request CSCvb29701, if the remote authentication method is eap. For these versions, when configuring eap as the remote authentication method, ensure the local authentication method is configured as rsa-sig first. This problem is not seen with any other form of remote authentication method.
What is IKEv2 session?
The IKEv2 session is completed by the ASA, final configuration (configuration reply with values such as an assigned IP address), transform sets, and traffic selectors are pushed to the VPN client.
What is EAP encapsulated in?
All subsequent EAP packets are encapsulated in IKE_AUTH. After the supplicant confirms the method (EAP-PEAP), it starts to build an Secure Sockets Layer (SSL) tunnel which protects the MSCHAPv2 session used for authentication.
Does AnyConnect support EAP?
If there is a need for a specific split tunnel policy, AnyConnect should be used. AnyConnect does not support standardized EAP methods which are terminated on the AAA server (PEAP, Transport Layer Security). If there is a need to terminate EAP sessions on the AAA server then the Microsoft client can be used.
Does IKEv2 support split tunnel?
The native Windows IKEv2 client does not support split tunnel (there are no CONF REPLY attributes which could be accepted by the Windows 7 client), so the only possible policy with the Microsoft client is to tunnel all traffic (0/0 traffic selectors).
IKEv2 IPSec Remote Access VPN with Anyconnect on Cisco ASA
The Cisco AnyConnect Secure Mobility Solution provides a comprehensive, highly secure enterprise mobility solution. the Cisco AnyConnect Secure Mobility Solution continues to lead with next-generation security and encryption, including support for the Suite B set of cryptographic algorithms, and support for IPv6 networks.
Filtering Routes in BGP using Route-maps and Prefix-list
Order of preference of attributes in BGP The order of preference varies based on whether the attributes are applied for inbound updates or outbound updates.
Ansible-playbook for backing up running config of Cisco IOS
This ansible-playbook can be used to backup running configuration from Cisco IOS devices. You can refer to my earlier post Getting Started with your first ansible-playbook for Network Automation to know about the parameters used in this playbook.
Export or Backup Azure Virtual Networks or Subnet information into CSV using PowerShell
There may be times when you want to get a report that contains information of all VNETS along with their subnets and address prefixes. You might have question, how to export or backup Azure VNET or subnets information into CSV.
Ansible Playbook for Network OS Upgrade with pre and post checks
You have 100s of network switches or routers that you need to upgrade. How much time would it take for you to do the upgrades? There are a lot number of sub-tasks involved while upgrading IOS image of a Cisco router or a switch.
Export or Backup Azure Route Table into CSV using PowerShell
There could be many use cases where you may want to export Azure route tables into CSV. Here is the PowerShell script that you can use to export Azure Route Tables into CSV using PowerShell script. This script will export Azure Route Tables along with routes of all Active subscriptions into a CSV.
Download Visio Stencils for Network Topology
Microsoft Visio is a great way to draft network diagrams for documentation, and network diagrams looks more nice if correct icons are used for the devices. So, download the Visio stencils from the following link. If you have more such links, you can post them in comments and they will be added here.
What does IKE stand for in IPSEC?
IKE stands for Internet Key exchange, it is the version 2 of the IKE and it has been created to provide a better solution than IKEv1 in setting up security association (SA) in IPSEC.
Which is newer, IPSEC or crypto?
NOTE: you can also create a crypto map which is the legacy way, while IPSEC profile is the newer way.

Introduction
Prerequisites
- Requirements
Cisco recommends that you have knowledge of these topics: 1. Basic VPN and IKEv2 knowledge 2. Basic Authentication, Authorization, and Accounting (AAA) and RADIUS knowledge 3. Experience with ASA VPN configuration 4. Experience with Identity Services Engine (ISE) configu… - Components Used
The information in this document is based on these software and hardware versions: 1. Microsoft Windows 7 2. Cisco ASA software, Version 9.3.2 and later 3. Cisco ISE, Release 1.2 and later
Background Information
- AnyConnect Secure Mobility Client Considerations
The native Windows IKEv2 client does not support split tunnel (there are no CONF REPLY attributes which could be accepted by the Windows 7 client), so the only possible policy with the Microsoft client is to tunnel all traffic (0/0 traffic selectors). If there is a need for a specific split t…
Configure
- Note: Use the Command Lookup Tool (registeredcustomers only) in order to obtain more information on the commands used in this section.
Verify
- Use this section to confirm that your configuration works properly. The Output Interpreter Tool (registered customers only) supports certain show commands. Use the Output Interpreter Tool in order to view an analysis of showcommand output.
Related Information