Imminent Monitor Remote Access Trojan infected users from all around the world and was sold to more than 14,500 buyers Imminent Monitor RAT, along with its website, shut down by Europol and other law enforcement agencies around the world
Full Answer
What is imminent monitor and is it still available?
Imminent Monitor was a commodity remote access tool (RAT) offered for sale from 2012 until 2019, when an operation was conducted to take down the Imminent Monitor infrastructure. Various cracked versions and variations of this RAT are still in circulation.
What are some examples of remote access trojan?
Remote Access Trojan Examples 1 Back Orifice. Back Orifice (BO) rootkit is one of the best-known examples of a RAT. ... 2 Sakula. Sakula, also known as Sakurel and VIPER, is another remote access trojan that first surfaced in November 2012. 3 Sub7. Sub7, also known as SubSeven or Sub7Server, is a RAT botnet. ... 4 PoisonIvy. ... 5 DarkComet. ...
What is the imminent monitor Rat?
The Imminent Monitor RAT was created back in 2013 by a malware author going by the name of Shockwave. It was one of the many RATs developed in the past two decades.
Which is the Best Antivirus for remote access trojan detection?
Remote Access Trojan Detection 1 Avast 2 AVG 3 Avira 4 Bitdefender 5 Kaspersky 6 Malwarebytes 7 McAfee 8 Microsoft Windows Defender 9 Norton 10 PC Matic 11 Sophos 12 Trend Micro More ...

Can remote access Trojans be detected?
AIDE—short for Advanced Intrusion Detection Environment—is a HIDS designed specifically to focus on rootkit detection and file signature comparisons, both of which are incredibly useful for detecting APTs like Remote Access Trojans.
Is remote access Trojan a malware?
Remote access trojans (RATs) are malware designed to allow an attacker to remotely control an infected computer. Once the RAT is running on a compromised system, the attacker can send commands to it and receive data back in response.
What is imminent monitor rat?
URLhaus. MITRE describes Imminent Monitor as a commodity remote access tool (RAT) offered for sale from 2012 until 2019, when an operation was conducted to take down the Imminent Monitor infrastructure. Various cracked versions and variations of this RAT are still in circulation.
How are remote access Trojans spread?
These messages have . ZIP files attached which, once opened, reveal an ISO image. The ISO file is equipped with a malicious loader for the Trojans through either JavaScript, a Windows batch file, or a Visual Basic script. If a victim attempts to load the disk image, these scripts will trigger.
How can I find a hidden virus on my computer?
You can also head to Settings > Update & Security > Windows Security > Open Windows Security on Windows 10, or Settings > Privacy and Security > Windows Security > Open Windows Security on Windows 11. To perform an anti-malware scan, click “Virus & threat protection.” Click “Quick Scan” to scan your system for malware.
Can an Iphone get a remote access Trojan?
The iOS Trojan is smart and spies discretely, i.e. does not drain a battery. The RCS mobile Trojans are capable of performing all kinds of spying you can expect from such a tool, including location reporting, taking photos, spying on SMS, WhatsApp and other messengers, stealing contacts and so on.
What is a Trojan virus and what does it do?
A Trojan Horse Virus is a type of malware that downloads onto a computer disguised as a legitimate program. The delivery method typically sees an attacker use social engineering to hide malicious code within legitimate software to try and gain users' system access with their software.
How would users recognize if ones computer is infected?
Signs of an infection include your computer acting strangely, glitching and running abnormally slow. Installing and routinely updating antivirus software can prevent virus and malware infections, as can following cautious best practices.
Which of the following is a remote Trojan?
Troya is a remote Trojan that works remotely for its creator.
Are PUPs malware?
Type and source of infection. Detections categorized as PUPs are not considered as malicious as other forms of malware, and may even be regarded by some as useful. Malwarebytes detects potentially unwanted programs for several reasons, including: They may have been installed without the user's consent.
Is a backdoor malware?
A backdoor is a malware type that negates normal authentication procedures to access a system. As a result, remote access is granted to resources within an application, such as databases and file servers, giving perpetrators the ability to remotely issue system commands and update malware.
Which of the following is a remote Trojan?
Troya is a remote Trojan that works remotely for its creator.
What is crypto malware?
Crypto malware, also known as crypto-mining malware, is malicious software installed by threat actors on victims' devices. It allows threat actors to mine cryptocurrencies using the victim's computing resources without their knowledge.
When was the imminent monitor rat created?
The Imminent Monitor RAT was created back in 2013 by a malware author going by the name of Shockwave. It was one of the many RATs developed in the past two decades. Image: Veronica Valeros.
What is IM-RAT hacking?
Law enforcement agencies from all over the world announced today they took down the infrastructure of the Imminent Monitor remote access trojan (IM-RAT), a hacking tool that has been on sale online for the past six years.
When did the IM-RAT operation take place?
According to a press release from Europol, the operation had two stages. The first occurred in June 2019, when Australian and Belgian police forces searched the homes of the IM-RAT author and one of his employees. The second stage took place earlier this week, when authorities took down the IM-RAT website, its backend servers, ...
What is an imminent monitor?
Imminent Monitor was a commodity remote access tool (RAT) offered for sale from 2012 until 2019, when an operation was conducted to take down the Imminent Monitor infrastructure. Various cracked versions and variations of this RAT are still in circulation. [1]
Does Imminent Monitor encrypt email?
Imminent Monitor has encrypted the spearphish attachments to avoid detection from email gateways; the debugger also encrypts information before sending to the C2. [2]
How many samples of Imminent Monitor are there?
We next focused on “Imminent Monitor,” a RAT offered for sale since 2012. In comparison to Orcus RAT, we have more than 65,000 samples of Imminent Monitor, and observed its use in more than 115,000 unique attacks against Palo Alto Networks customers. This total number of samples includes those shared between antivirus vendors, not just those directly detected by Palo Alto Networks customers. However, the observed attacks figure only reflects actual, in-the-wild samples from Palo Alto Networks customers. In most cases, repeated attacks using the same samples and/or blocked by signature detection will not be reflected in this figure, and so the actual total number of attack attempts will be much higher than reflected in this metric. With such prevalence, we had to wonder why the author of this malware has been allowed to continue to profit from this for almost seven years, unchecked.
What is Unit 42?
Unit 42 referred the identity and activity of Shockwave™ to the Australian Federal Police (AFP) Cybercrime Operations teams. We have subsequently continued to assist the AFP’s “Operation Cepheus” (Figure 13), together with the United States Federal Bureau of Investigation (FBI), and Canadian Radio-television and Telecommunications Commission, Electronic Commerce Enforcement / Conseil de la radiodiffusion et des télécommunications canadiennes, Mise en application du commerce électronique (CRTC ECE). The Australian-led investigation, targeting not only those responsible for the development and management of this malware, but also their customers using the malware illicitly, has yielded evidence suggesting in excess of 14,500 customers of this RAT. We most often observe RATs employed illicitly by financially-motivated actors, or for data theft. Interestingly, the AFP’s investigation noted a significant number of Australian users of the software were also respondents to Domestic Violence Orders. It’s unlikely a coincidence that such a tool might be employed against Intimate Partner Violence victims. AFP’s operation also disabled the licensing system of Imminent Monitor, removing users’ access to victims of the software. Unit 42’s research into the infrastructure and customers of Imminent Monitor and other RATs continues to assist law enforcement internationally in prosecuting the individuals behind such illicit activity, demonstrating the effectiveness and potential of international public/private cooperation in combating cybercrime.
How to identify actors behind the Imminent Monitor?
In order to identify actors behind such operations as Imminent Monitor, it’s important to be thorough with analysis and intelligence collection. The actor will typically attempt to hide or obfuscate their identity. The research will not only aim to directly identify a specific individual but also help to build a corroborative identity picture, increasing confidence in any analysis.
How much is the Imminent Monitor license?
Imminent Monitor was originally licensed to each customer for a $25 fee. Six years later, the price has remained static, though new multi-license options are also offered (Figure 8).
What is commodity malware?
The availability of “commodity malware” – malware offered for sale – empowers a large population of criminals, who make up for their lack of technical sophistication with an abundance of malicious intent.
How many FPS does a shockwave remote desktop have?
Shockwave™ claimed: “ We use new methods not used in any rat, the remote desktop has the potential to get around 60 fps, and the cam I have personally gotten 130 with this. ”
What is HRDP protocol?
More recent versions offer what the author terms “HRDP” – Hidden Remote Desktop Protocol – offering a non-interactive remote desktop connection, hidden from the victim.
Shady RAT
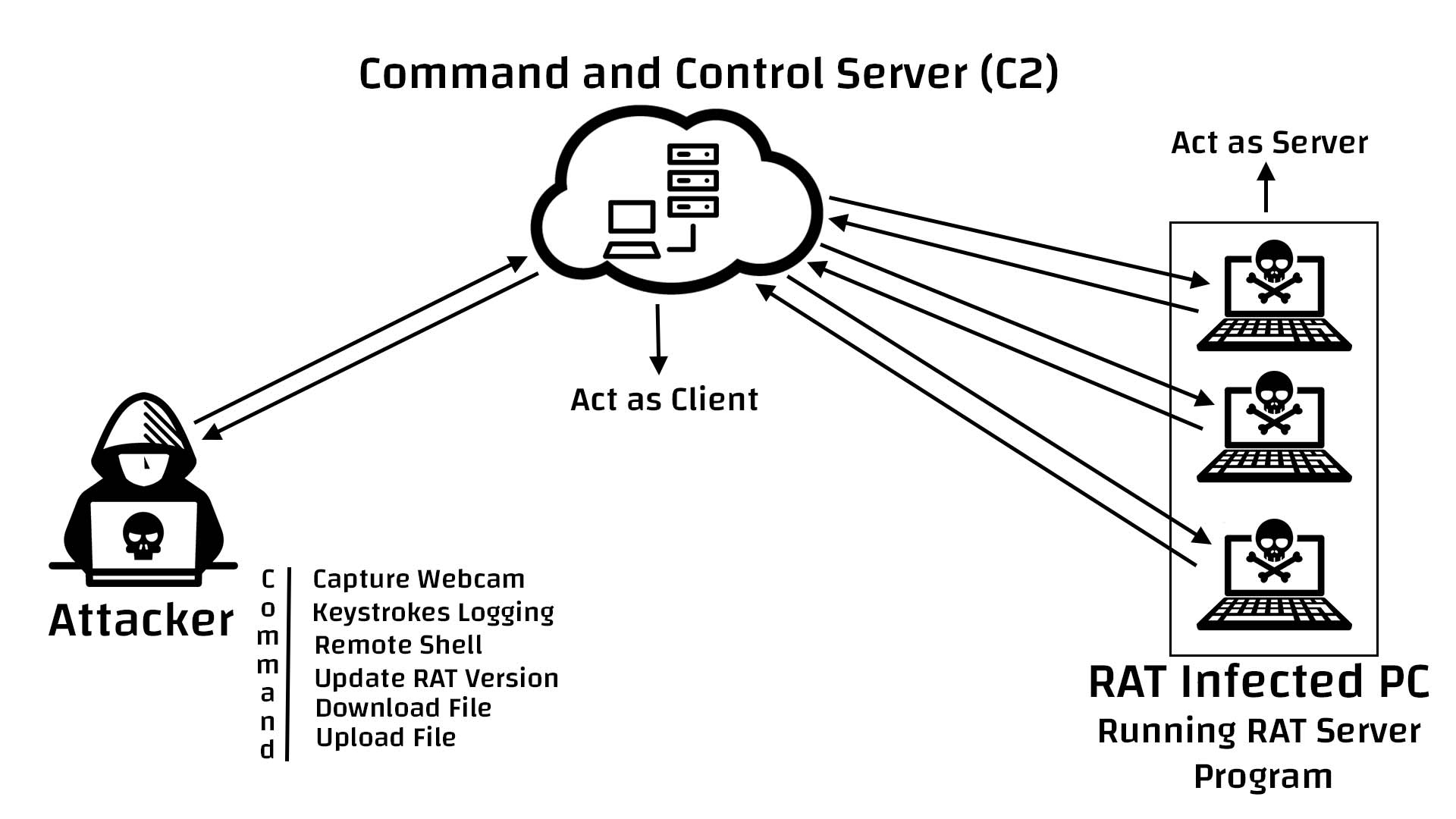
For those not familiar with Remote Access Trojans, or RATs, they are malware programs that when installed on a victim's device allows an attacker to gain full access to the computer. This includes executing any command, taking screenshots, uploading and downloading files, and using the device's webcam to record video.
Hackers suspected Imminent Monitor raid
While authorities stated that they performed searches of the Imminent Monitor developer in June, users of the software suspected that something was up for some time before that.
What Does a RAT Virus Do?
Since a remote access trojan enables administrative control , it is able to do almost everything on the victim machine.
How does RAT malware work?
Once get into the victim’s machine, RAT malware will hide its harmful operations from either the victim or the antivirus or firewall and use the infected host to spread itself to other vulnerable computers to build a botnet.
What is a RAT trojan?
RAT trojan is typically installed on a computer without its owner’s knowledge and often as a trojan horse or payload. For example, it is usually downloaded invisibly with an email attachment, torrent files, weblinks, or a user-desired program like a game. While targeted attacks by a motivated attacker may deceive desired targets into installing RAT ...
How to protect yourself from remote access trojans?
Just like protecting yourself from other network malware threats, for remote access trojan protection, in general, you need to avoid downloading unknown items; keep antimalware and firewall up to date, change your usernames and passwords regularly; (for administrative perspective) block unused ports, turn off unused services, and monitor outgoing traffic.
What is a RAT?
A remote access trojan (RAT), also called cree pware, is a kind of malware that controls a system via a remote network connection. It infects the target computer through specially configured communication protocols and enables the attacker to gain unauthorized remote access to the victim. RAT trojan is typically installed on a computer without its ...
Why is Darkcomet no longer available?
The reason is due to its usage in the Syrian civil war to monitor activists as well as its author’s fear of being arrested for unnamed reasons.
What does RAT stand for?
RAT can also stand for remote administration tool, which is software giving a user full control of a tech device remotely. With it, the user can access your system just like he has physical access to your device. So, the user can access your files, use your camera, and even turn off or turn on your machine.
Imminent Monitor RAT Description
The Imminent Monitor RAT software falls in the category of Remote Access Tools, and there are more than five years of development behind it. The Imminent Monitor RAT is a legitimate remote administration framework developed by Imminent Methods that you can find at https://imminentmethods.net.
Site Disclaimer
Enigmasoftware.com is not associated, affiliated, sponsored or owned by the malware creators or distributors mentioned on this article. This article should NOT be mistaken or confused in being associated in any way with the promotion or endorsement of malware.
Vendors
An Australian-led operation targeting hackers allegedly using the Imminent Monitor Remote Access Trojan (IM-RAT) has resulted in the takedown of the Imminent Monitor web page, from which the remote access tool had been distributed.
Join the newsletter!
Sign up to gain exclusive access to email subscriptions, event invitations, competitions, giveaways, and much more.
