
Secure remote access is important because: You need to protect your digital assets from unauthorized and malicious individuals. Most users don’t apply or may not even be capable of applying security measures when performing remote access.
What is remote access technology and why do you need it?
With the right technology in place, IT can deliver full access to apps, content and services employees need to get work done – wherever it needs to happen – and ensure their corporate information and devices remain safe. Traditional remote access solutions connect a remote person to a network.
What do businesses look for in a remote access solution?
Deployment, ease of use, mobile access, security, and scalability are key features businesses need to look for when considering a remote access solution. Another important aspect is affordability, in today’s world, many businesses are struggling and have budget constraints, but still require remote access.
How freelancers can benefit from remote access?
Freelancers who are always on the go but still need to accomplish projects can utilize remote access for their own benefit. By investing in the right remote access solution, they can access everything on their own computer from anywhere at any time. Remote access is a great business and work solution in today’s fast-paced environment.
What should be included in a remote access policy?
A remote access policy should cover everything—from the types of users who can be given network access from outside the office to device types that can be used when connecting to the network. Once written, employees must sign a remote access policy acceptance form. Other documents referenced in the policy should be attached to it as well.
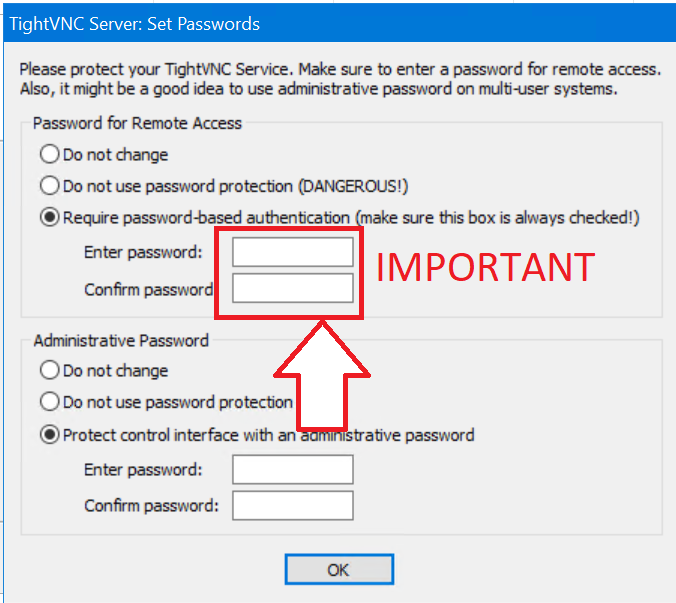
What is important when selecting remote connections?
Usability. First and foremost, your future remote support tool should be easy to use and understand. Remember that the remote user is not as tech savvy as you are, and therefore simplicity (in a good sense) is key to delivering fast customer support. The remote connection speed also matters a lot.
What do you need to consider when determining your remote access needs?
You should consider these security factors when making your decision: Prompt, automated security updates and patches. Multi-level authentication and authorization steps each time users log in on any device. End-to-end encryption of all connections.
What should I look for in remote access software?
Finding the right remote access software can be tough if you don't know what to look for....FunctionalityThird-party integrations.Remote printing.Multiple monitor access.File sharing.Live chat.Screen recording.Unattended access.
What is the importance of remote administration?
Remote Administration It allows system administrators the power to manage as well as monitor the corporate network remotely. They can easily edit the permissions provided to the users depending upon the specific needs.
What are potential risks associated with remote access?
Five Remote Access Security Risks And How To Protect Against ThemWeak remote access policies. ... A deluge of new devices to protect. ... Lack of visibility into remote user activity. ... Users mixing home and business passwords. ... Opportunistic phishing attempts.
What security considerations do you think are important for users accessing their company desktops remotely?
Why do I need to secure remote access?1) Assume threats will occur.2) Create a telework policy.3) Encrypt sensitive information.4) Designate and secure specific remote work devices.5) Employ user authentication.6) Set up a VPN.7) Manage sensitive data securely.8) Collaborate with third-party partners and vendors.
What is the best way to remotely access a computer?
How to use Remote DesktopSet up the PC you want to connect to so it allows remote connections: Make sure you have Windows 11 Pro. ... Use Remote Desktop to connect to the PC you set up: On your local Windows PC: In the search box on the taskbar, type Remote Desktop Connection, and then select Remote Desktop Connection.
What is remote access tools?
Remote access programs and tools (sometimes referred to as RATs) allow access and manipulation of systems remotely from another location. Many remote access programs are legitimate tools used by all types of users to access files and data on remote computers.
How can I remotely access someones computer?
Share your computer with someone else On your computer, open Chrome. In the address bar at the top, enter remotedesktop.google.com/support , and press Enter. Follow the onscreen directions to download and install Chrome Remote Desktop. Under “Get Support,” select Generate Code.
How is remote access critical for a company?
Remote access will allow your employees to safely work from any platform, device, or network whether at their home office, at an internet cafe, or abroad. They can access, edit, and share important files with colleagues, which makes collaboration easy and helps to streamline work for all employees concerned.
What should be included in an access control policy?
Organizations planning to implement an access control system should consider three abstractions: access control policies, models, and mechanisms. Access control policies are high-level requirements that specify how access is managed and who may access information under what circumstances.
What the common remote access domain policies are?
Through remote access policies you can define the following: Grant or deny dial-in based on connection parameters such as type and time of the day. Authentication protocols (Password Authentication Protocol (PAP), CHAP, EAP, MS-CHAP) Validation of the caller id.
What is a remote access plan?
A well-designed remote access plan provides access to the required corporate data and applications for users when they're off-premises.
How Important Remote Access is These Days?
According to Forbes, almost 50% of the US workforce is expected to be working remotely by the year 2027. So what does this mean to modern businesses? Well, if remote working is going to be the trend in the coming years, businesses that want to make it in the long run should start embracing remote access as soon as they can. This isn’t only going to be beneficial to the employees themselves, but to companies and organizations as well.
Why is remote access important?
Providing your employees the freedom to work anywhere they want to sounds like the best job to many . With this, they can maintain a work-life balance culture where they have more time to spend with themselves and their loved ones. This, in return, increases their work satisfaction rate and improves your company’s turnover rate.
What is remote access?
Remote access is defined as the ability to access a computer, device, or a specific network from an offsite location. This can refer to employees who still have access to their office equipment such as computers and laptops even outside of office hours. Technical support organizations can also utilize remote access to connect to their clients devices in order to resolve any technical problems.
What is work from home culture?
Providing a work from home culture means reducing the costs you’ll most likely spend on office equipment such as laptops, computers, desktops, etc. You can also address business emergencies more effectively using remote access. The thing about business demands is that they don’t recognize if it’s weekend or your day-off.
Can freelancers access their own computer?
Freelancers who are always on the go but still need to accomplish projects can utilize remote access for their own benefit. By investing in the right remote access solution, they can access everything on their own computer from anywhere at any time.
Can you use remote access on multiple devices?
Even simple device users can use remote access to accomplish day-to-day functions. Those who have multiple devices can use this technology to connect them remotely all at the same time. You can also provide technical help to your loved ones who live in a different city without needing to be at their exact locations.
Is remote access good?
Remote access is a great business and work solution in today’s fast-paced environment. It’s incredible to know that with this technology, locations and business emergencies no longer impede work productivity and business opportunities from coming. Now that you know how important remote access is, it’s time for you to utilize it for your own good ...
Why do organizations need remote access?
On a more granular level, organizations have several reasons for enabling remote access to their OT environments. Software Toolbox identified three such factors: 1 Empowering decision-makers with data access and visibility: Decision-makers need access to and visibility over data if they are to safeguard the organization’s interests. They need timely information to make the right decisions. 2 Centralizing access across geographically distributed systems: Many organizations that own or operate OT environments have assets that are scattered across different countries and continents. This makes it difficult for people like remote workers to monitor those devices all at once. Remote access solves this problem by enabling an authenticated user to access those systems from anywhere in the world. Alternatively, organizations can centralize these access sessions within a single operations center. 3 Streamlining work with third parties: Organizations that own or operate OT environments need to be able to work with their third-party vendors, contractors and suppliers. This can be difficult depending on the scope of the supply chain. As a result, organizations could use remote access to share key important data with third parties rather than grant them full access to their entire environments. 4 Facilitating the implementation of updates: Per Security Week, many industrial control systems come with a contract through which equipment manufacturers are responsible for providing remote maintenance. It’s therefore critical that organizations ensure there’s remote access available to these device manufacturers. Otherwise, they could risk those OT assets not receiving an important update or fix when it’s misbehaving, for example.
Why do decision makers need access to data?
Empowering decision-makers with data access and visibility: Decision-makers need access to and visibility over data if they are to safeguard the organization’s interests. They need timely information to make the right decisions.
What is Remote Access?
Remote access refers to two separate, yet related purposes that allow access to a computer system from a geographical distance.
How Does Remote Access Work?
Remote access lets you connect with other devices that are not in your physical vicinity by using a combination of software, hardware tools, and network configurations to send data from one device to the other through encrypted channels.
Why is Remote Access So Important?
Due to the growth of remote work in the wake of the COVID-19 pandemic, remote access and team communication methods have become extremely important for businesses in 2021.
Examples of Remote Access
Below, we’re going to take a look at 6 different examples of remote access and why each is important in a business.
How to identify remote access?
Identifying the right remote access solution for your business starts by understanding the needs of your workforce and the specifics of the working environment. Then creating criteria that will ensure that your solution has the right capabilities, and core functionality to deliver sustainable success.
What is remote access?
Traditional remote access solutions connect a remote person to a network. In a world where staff have become used to working from anywhere, this needs to be reconsidered. It only adds complexity and security risks. Organizations shouldn’t think about remote access in a siloed way, but reimagine their network, application, and security infrastructure.
What security features should an enterprise look for?
Security features: Enterprises should look for remote access that offers security features, such as SSO, 2/MFA and device authentication that are in line with Enterprise security policies, so that there are no exceptions.
Why should IT leaders invest in integrated remote management solutions?
IT leaders should invest in integrated remote management solutions that allow technicians to manage their entire IT infrastructure from one console. This allows technicians to reclaim the “space between,” or the valuable time IT professionals waste moving between disparate applications and processes, and ensures a more efficient allocation of internal resources.
Why do businesses need a complete solution?
Businesses need a solution that is complete to manage everything , automated for ultimate efficiency and priced right to deliver exceptional value as IT teams must continue to contend with the demands to do more with fewer resources.
Why is instant connectivity important?
Instant connectivity: This is important so your users can connect easily from any device (whether that’s the desktop, Android, iOS or Windows) with an internet connection.
How to meet user expectations for fast access?
To meet the user’s expectations for fast access, the system must connect the user to the application via the shortest possible route, without latency. This is where zero trust network access can help to guide the user to the relevant application based on rules and context.
Why Is a Remote Access Policy Important?
If a remote access policy is not in place, such risky behavior could go on unmitigated, without the organization finding out about it until after the occurrence of a breach.
What are the considerations when formulating a remote access policy?
Other considerations when formulating a remote access policy include but are not limited to the following: Standardized hardware and software, including firewalls and antivirus/antimalware programs. Data and network encryption standards. Information security and confidentiality. Email usage.
What Is a Remote Access Policy?
For example, sales personnel can now use tablets and other mobile devices to connect remotely to their office networks while on client calls and bring up data that may be important for closing deals . Recent events have further boosted the number of remote workers to an estimated 42% of the US workforce.
What is remote work?
Remote work has brought with it a few challenges, including potential computer and network security risks. There is a real need for guidelines surrounding remote access, along with other policies. A remote access policy serves as a guide for remote users connecting to the network. It extends the policies governing network and computer use in ...
Why is password policy important?
It helps ensure that only those users who need it are given network access, as long as their devices are also compliant with the guidelines. When implemented properly, it helps safeguard the network from potential security threats.
How to ensure that you do not miss anything when updating your remote access policy?
To ensure that you do not miss anything when updating your remote access policy, consider your organizational, legal, contractual and regulatory obligations when you compile the list of policy requirements. After that, identify the procedural and technical controls required to fulfill the policy, making sure to reinforce or replace existing controls that have not been effective.
What should the IT department do?
For its part, the IT department should implement centralized management of data access to ensure that only authorized users are allowed access into the network . A comprehensive audit mechanism to ensure policy conformance is also recommended. In case anomalies are detected during audits, the IT department should recommend remediation measures to prevent future occurrences.
What is remote desktop?
The term ‘remote desktop’ when it comes to the IT world pertains to an operating software or an app which grants a personal desktop’s permission for it to be controlled or ran remotely on another system (a separate desktop computer, most of the time). While doing it, whatever you have in your PC screen will display to the other device at the same time and he has the power to control your computer. Below in this article, we will cover the 6 Important Features That You Should you use Remote Desktop Software.
Why are big names in the software industry so overwhelmed?
Big names in the software provider industry tend to become overwhelmed especially when the number of support problems that they need to address is increasing. Instead of prioritizing the satisfaction of their customers, they tend to focus on improving their software or app. That’s, of course, understandable.
Usability
First and foremost, your future remote support tool should be easy to use and understand. Remember that the remote user is not as tech savvy as you are, and therefore simplicity (in a good sense) is key to delivering fast customer support.
Security & data protection
Let’s say you’ve done some quick search and found a remote support solution that might be the right fit for your needs and bills. Before you buy it, ask yourself these two simple questions:
Compliance
Running an ecommerce website that processes credit card data? If so, you’ll have to get your business PCI-ready by ensuring that all of the tools you use to support your customers offer two-factor authentication. Remote support software is no exception.
Customer support
Huge software providers get overwhelmed with the number of support issues they have to address and often focus on product development and marketing instead of trying to serve and delight each and every customer. And that’s partly understandable.
Branding options
Asking customers to run a third-party application may cause confusion – “why should I let this software access my computer, is this legit?” To avoid that, you may want your remote support tool to reflect your brand and match the looks of your website.
Upgrade fees & license sharing
Ok, everything seems promising, both feature and security-wise. However, now it’s high time you reviewed any licensing tricks that your potential software provider has up its sleeves.