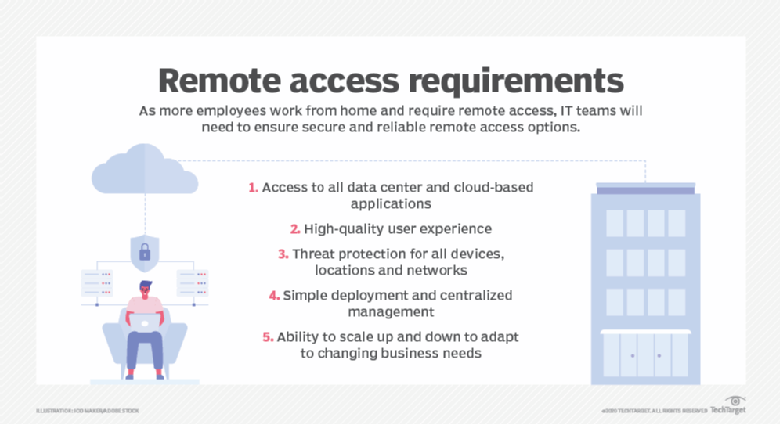
For example, remote access might involve a VPN A virtual private network extends a private network across a public network, and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. Applications running on a computing device, e.g. …Virtual private network
Full Answer
What is the best remote access solution for your business?
Virtual private networks (VPNs): The most common solution for remote access, usually providing unrestricted access to corporate resources Virtual desktop access (VDI): Accessing a corporate-imaged virtual machine in the data center through a corporate internet gateway or directly in the cloud
What are the components of remote access role?
The Remote Access role consists of two components: 1. DirectAccess and Routing and Remote Access Services (RRAS) VPN: DirectAccess and VPN are managed in the Remote Access Management console. 2. RRAS: Features are managed in the Routing and Remote Access console.
What is a remote access policy?
Remote access is any connection made to an organization's internal network and systems from an external source by a device or host. Remote locations can be almost anywhere in the world, from the employee’s home to an off-site office, hotels, transportation hubs, and cafes. What Is a Remote Access (Control) Policy?
What is the use of the remote management console?
- By default on a Remote Access server when the Remote Access role is installed and supports the Remote Management console user interface. - As an option on a server that is not running the Remote Access server role. In this case, it is used for remote management of a Remote Access server.

What is remote access capability?
Remote access is the ability for an authorized person to access a computer or network from a geographical distance through a network connection. Remote access enables users to connect to the systems they need when they are physically far away.
What should be included in a remote access policy?
What Should You Address in a Remote Access Policy?Standardized hardware and software, including firewalls and antivirus/antimalware programs.Data and network encryption standards.Information security and confidentiality.Email usage.Physical and virtual device security.Network connectivity, e.g., VPN access.More items...•
What is example of remote access?
Accessing, writing to and reading from, files that are not local to a computer can be considered remote access. For example, storing and access files in the cloud grants remote access to a network that stores those files. Examples of include services such as Dropbox, Microsoft One Drive, and Google Drive.
What is the importance of remote access?
With remote access, employees can safely work from any device, platform, or network at their home office or abroad. Remote desktop functions allow them to remotely access important files and share their screen for meetings and troubleshooting.
What is a remote access standard?
PURPOSE. Remote Access refers to the ability to access UMW network resources while off campus. Security measures for remote access should be implemented based on sensitivity and risk to University systems and data. Standard.
What is a access policy?
n. Principles or procedures that control the conditions under which individuals have permission and ability to consult a repository's holdings.
What are types of remote access?
The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), Point-to-Point Protocol over Ethernet (PPPoE), Point-to-Point Tunneling Protocol (PPTP), Remote Access Services (RAS), and Remote Desktop Protocol (RDP).
What are the three main types of remote connections?
Remote Access Control MethodsDirect (Physical) Line. The first direct remote access control that can be implemented is a direct line from a computer to the company's LAN. ... Virtual Private Network. Another method which is more common is establishing a VPN. ... Deploying Microsoft RDS.
How do you take remote access?
How to use Remote DesktopMake sure you have Windows 11 Pro. To check this, select Start , and open Settings . ... When you're ready, select Start , and open Settings . Then, under System , select Remote Desktop, set Remote Desktop to On, and then select Confirm.Make note of the name of this PC under PC name.
What is the greatest benefit of remote access to an organization?
Flexibility. By allowing your staff to perform tasks outside the office using remote access, you can facilitate more flexible work arrangements and help employees create a better work/life balance.
What are the advantages of remote management?
Boost Unassisted Sales.Increase Online Revenue.Lead Follow up and Conversion.Increase Lead Volume & Quality.Improve Buying Experience & Boost NPS.Increase operational efficiency.
Why you must create a remote access policy for VPN connectivity?
Remote access VPN can be an attractive ground for hackers and malicious attackers, so an organization's server must be protected by a security or network administrator. By having an effective VPN remote access policy, you can reduce the risk of your organization's network assets and support calls from end users.
Why should an organization have a remote access policy even if IT already has an acceptable use policy AUP for employees?
A remote access policy is vital to ensure that your organization can maintain its cybersecurity protocols even with all the uncertainty that remote access brings: unknown users (you can't see the person, after all), using potentially unknown devices on unknown networks, to access your corporate data center and all the ...
What is a network access policy?
Network policies are sets of conditions, constraints, and settings that allow you to designate who is authorized to connect to the network and the circumstances under which they can or cannot connect.
Where are the implementation instructions defined in a remote access policy definition?
Where are the implementation instructions defined in a remote access policy definition? Does this section describe how to support the two different remote access users and requirements as described in this lab's XYZ Health Care Provider scenario? · The implementation instructions are defined in Remote Access Domain.
What is Remote Access Guide?
The Remote Access guide provides you with an overview of the Remote Access server role in Windows Server 2016, and covers the following subjects:
How to install Remote Access as a LAN router?
To install Remote Access as a LAN router, either use the Add Roles and Features Wizard in Server Manager and select the Remote Access server role and the Routing role service; or type the following command at a Windows PowerShell prompt, and then press ENTER. Install-RemoteAccess -VpnType RoutingOnly.
What is a RAS gateway?
RAS Gateway - Multitenant. You can deploy RAS Gateway as a multitenant, software-based edge gateway and router when you are using Hyper-V Network Virtualization or you have VM networks deployed with virtual Local Area Networks (VLANs). With the RAS Gateway, Cloud Service Providers (CSPs) and Enterprises can enable datacenter and cloud network traffic routing between virtual and physical networks, including the Internet. With the RAS Gateway, your tenants can use point-so-site VPN connections to access their VM network resources in the datacenter from anywhere. You can also provide tenants with site-to-site VPN connections between their remote sites and your CSP datacenter. In addition, you can configure the RAS Gateway with BGP for dynamic routing, and you can enable Network Address Translation (NAT) to provide Internet access for VMs on VM networks.
What is always on VPN?
Always On VPN enables remote users to securely access shared resources, intranet Web sites, and applications on an internal network without connecting to a VPN. For more information, see RAS Gateway and Border Gateway Protocol (BGP).
What is web application proxy?
Web Application Proxy provides reverse proxy functionality for web applications inside your corporate network to allow users on any device to access them from outside the corporate network. Web Application Proxy pre-authenticates access to web applications using Active Directory Federation Services (AD FS), and also functions as an AD FS proxy.
Can you use remote access in Azure?
Using Remote Access in Microsoft Azure is not supported. You cannot use Remote Access in an Azure VM to deploy VPN, DirectAccess, or any other Remote Access feature in Windows Server 2016 or earlier versions of Windows Server. For more information, see Microsoft server software support for Microsoft Azure virtual machines.
What is Remote Access Software?
Remote access software (RAS) allows a local user in one location to perform useful functions elsewhere. With RAS, users can connect with, access, and control a remote computer, network, or server in another location.
Accomplish More for IT Clients with Datto RMM Remote Access Tools
Remote access tools are a critical component of Remote Monitoring and Management solutions used by Managed Service Providers (MSPs) to support their clients. MSPs rely on remote access capabilities to immediately work with client systems without having to travel onsite. This enables them to efficiently service their entire customer base.
How to get started with Datto RMM
Your clients want to know that you can be there for them, literally on a moment’s notice. As the networks you monitor and manage expand, Datto RMM’s remote access software for MSPs helps you to exceed expectations.
What is mobile access?
Mobile access to applications: Accessing email and other applications via managed mobile devices
Why create a persona for key user types?
Creating personas for key user types will help you get a handle on varying system and application needs.
Why is cloud adoption important?
With increased cloud adoption, firms achieve greater scalability and can provide end-user and business capabilities more rapidly. The optimal balance for cloud deployment maintains sufficient security while also enhancing the end-user experience.
Why should personas be aligned to the service catalog?
The personas should then be aligned to the service catalog to understand capacity requirements for each key service, standardizing offerings where possible. The data should be leveraged to model remote access scenarios such as financial staff needing full VPN/trusted access to internal accounting systems while sales associates might only need access to cloud-based services.
What is a dynamic and results-driven technology executive?
Dynamic and results-driven technology executive. Enabling digital and cloud transformation service capability in the financial services industry.
Why is it important to lock down all configurations?
In all cases it is important to ensure security hardening and immutability of the changes to the environment, locking down all of the configurations, such as network and access control. Moreover, some of the changes, like direct internet access, may require additional security monitoring and tooling.
Can an application developer work remotely?
Different business functions have different technical requirements. For example, an application developer may be able to work remotely full-time with just a laptop, while an equities trader may require tools and technologies available only at an office location.
Know your users
Creating personas for key user types will help you get a handle on varying system and application needs.
Juggling capacity and load
Cloud-based services and the smart use of regional network hubs can help lessen the strain for some businesses.
Managing remote access risk
Even as remote connectivity ramps up during a crisis, security and risk considerations cannot be neglected.
What Is Remote Access Software?
Remote access software lets one computer view or control another computer, not merely across a network, but from anywhere in the world. You might use it to log into your customers' computers and show them how to run a program, or sort out their technical troubles. Or you can even use it to invite friends or clients to view your desktop while you run a demo for them. You can use the screen as a temporary whiteboard, drawing lines and circles that help friends or clients understand what you're doing on your machine or theirs.
What is remote PC?
RemotePC is one of the best low-frills remote-access apps, offering identical features on PCs and Macs, fast performance, and a minimal, but intuitive, interface .
What is GoToMyPC?
GoToMyPC is a mature, easy-to-use remote access software with the best available balance between features and ease of use. Unless you need support for Linux or enterprise-level operating systems, this is the app you want.
Is VNC Connect secure?
VNC Connect is solid, secure, and simple to use, once you get the hang of it. It has fewer features than other corporate-level remote access software, but it's also a lot less expensive.
Does GoToMyPC work with TeamViewer?
GoToMyPC and LogMeIn add the ability to drag and drop files between the local desktop and the viewer window that displays the desktop of the remote machine, but this feature works only when connecting to and from Windows computers. TeamViewer has a FileBox window into which you can drag files that will be accessible to both machines. LogMeIn, TeamViewer, and VNC Connect include whiteboard features for drawing lines in the viewer. For more on each remote access apps individual features, see the individual reviews, which are linked to below.
What Is Remote Access?
Remote access is any connection made to an organization's internal network and systems from an external source by a device or host. Remote locations can be almost anywhere in the world, from the employee’s home to an off-site office, hotels, transportation hubs, and cafes.
Why is remote access important?
Software organizations where development engineers need to connect across multiple locations, small organizations lacking office-space, and large, enterprise organizations all want to offer the most flexible work options in order to attract high-ranking candidates and reap the rewards of having such a policy.
Why Is a Remote Access Policy Necessary?
The numerous types of mobile devices and the different ways to connect pose challenges for the IT department. Devices can include cell phones, tablets, laptops, and any other device a remote worker relies on to conduct business. They can be company owned and secured, personally owned and authorized by a Bring Your Own Device (BYOD) policy, or a combination. Each class of device has its own set of security challenges. According to the National Institute for Standards and Technology’s Guidelines for Managing the Security of Mobile Devices in the Enterprise, “…Security controls available for laptops today are quite different than those available for smartphones, tablets, and other mobile device types.” Since different devices demand different controls, the policy has to detail what is allowed, compliant, and secure. The policy should answer the following questions:
What Problems Arise Without a Remote Access Policy?
Therefore, consequences for misuse can also be clearly outlined to compel compliance and appropriate precautions for data use and access. Elements such as firewalls, connectivity guidelines, personal use restrictions, and antivirus updates can help IT prevent both malicious and accidental loss and disruption of corporate information assets. The remote access control policies also provide protections for confidentiality, intellectual property, and information compliance.
What is VPN policy?
Policies for VPN remote access can be standardized. These policies “shore up” and prevent the use of rogue devices and access by non-authorized users , including the worker's family members or housemates. The policy also enforces proper email protocols to protect information from being sent through unsecured or untrusted sources, and also provides rules that limit or prohibit split tunnel configurations that allow mobile users to access both secure and unsecure networks simultaneously.
What is telecommuting?
“Telecommuting,” a term coined in the 1970s, has experienced explosive growth in today’s era of mobile connectivity. Now called distributed offices, remote work, telework, mobile work, smart work, and work shifting, many people are finding flexibility and increased productivity conducting business away from a centralized office environment. Researchers have long studied the benefits of remote work - from the successes that remote work had on traffic reduction during the 1984 Los Angeles Olympics to the 2016 findings by a Gallup survey on the increased hours for remote work.
What percentage of people work remotely?
According to research conducted by Gallup, 43 percent of workers in the U.S. worked remotely at least some of the time in 2016. Remote workers report higher job satisfaction and flexibility, experience fewer distractions and interruptions, and are more productive. Companies experience less absenteeism, less stress on office accommodations, and realize greater employee retention. A recent New York Times article found that finance, insurance, real estate, and transportation were most likely to have and support remote work (retail and education were least likely candidates). The trend is only increasing: the 2016 Gallup poll also found that those who work remotely log more hours away from the office than was reported in their 2012 findings. Not only are people logging more hours, but remote workers are saving money when it comes to commuting costs and businesses are saving on office space expenses.
When do you need to connect to a remote support?
As a remote support technician, you might often need to connect to a client’s computer when no one’s being physically present at the remote end. Or if you have to support specific customers on a regular basis.
What is remote screen scaling?
The remote screen scaling feature makes it easier for you to work on a remote machine that has a larger or smaller screen resolution than yours. With FixMe.IT, you can always choose between three scaling options to adjust the remote control window based on the remote user’s screen resolution settings, or according to your own preferences.
What is clipboard sharing?
The clipboard sharing feature, in turn, is essential for tasks such as copying scripts or commands to the remote computer or an error message from the client’s computer.
Why is it important to multitask?
Being able to multi-task effectively is key to providing high quality remote support. Unfortunately, many remote desktop software vendors put certain limitations on the number of support sessions you can run simultaneously.
What is built in chat?
As soon as the remote connection is established, built-in chat will allow you and your client to exchange messages and stay updated on what’s happening on the remote end without having to pick up the phone or send an email every time a new issue arises.
What is log off/log on?
With the log off/log on feature, you’ll be able to install software or updates for each individual remote user. Otherwise, you’d be required to start a new session under each Windows user, which would significantly delay and complicate the job at hand.
Why is it important to run session reports?
Being able to run session reports is another vital feature to have. If you operate a one-man tech support business, it will allow you to keep track of your own work, or if you’re a manager of a large company’s helpdesk team, this feature will help you stay on top of how and when your software’s being used.
What are the factors that must be addressed with remote surveillance?
Then come other considerations such as software management platforms, mobile apps, and user permissions , among others. But none of these aspects need to be seen as barriers. With the right system, nothing should stand in ...
What is remote camera security?
Remote camera security surveillance is the ability to view, manage, and operate video cameras from afar. In some cases, this just means looking in at a live feed on the go, while some systems are set up to be managed entirely offsite. Such capabilities were rare with traditional video security but are now easy with many modern camera systems.
Why is it important to secure remote video cameras?
It is also important to properly configure user permissions, maintain strong passwords, and potentially encrypt devices. Given how much attention most IT departments now pay to securing various devices with network access, securing remote video cameras can easily be integrated into their protocol.
Can a company remotely manage a video camera?
With traditional video camera security, a company would typically set up, manage, and operate its entire surveillance system onsite. Today, these aspects are often handled remotely and secure remote access is the key to it all. Remote management is especially common among enterprises with multiple locations — and modern technology makes it easy to deploy such a system at scale.