
What is a remote access policy?
The remote access policy makes sure that devices that work for the company remotely are protected. That is, both in physical and network security provisions. What are some examples of its application? For example, an employee may be carelessly working on a train with people around him.
What are the top security concerns with VPN remote access policies?
The following are the top security concerns that raise the need of an effective VPN remote access policy: Man in the middle: If remote access was set up using IKE or another insecure authentication protocol, man in the middle attacks are possible.
What are the requirements for remote access security?
The password, username and dial-in access are required for a user to be granted access to the VPN. 3. Ensure safe encryption and SSL connection Encryption is a major part of remote access security.
What are the responsibilities of the Infosec team?
Defines acceptable use of equipment and computing services, and the appropriate employee security measures to protect the organization's corporate resources and proprietary information. Defines responsibilities regarding corporate acquisitions, and defines the minimum requirements of an acquisition assessment to be completed by the Infosec Team.
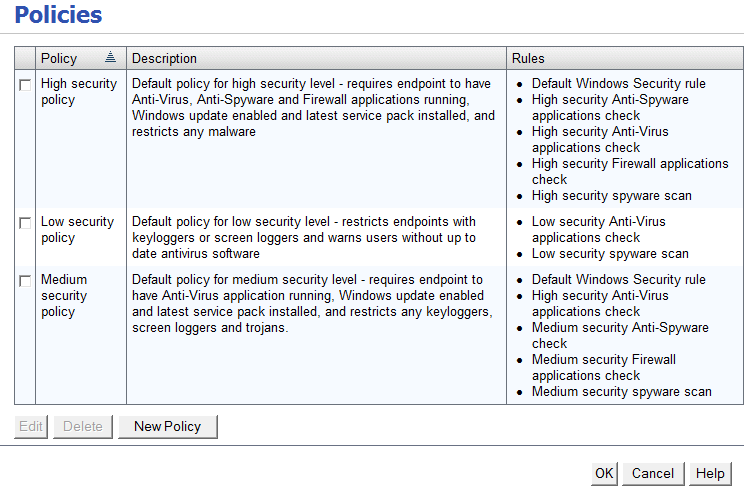
What is remote access security policy?
A remote access policy serves as a guide for remote users connecting to the network. It extends the policies governing network and computer use in the office, e.g., password policy.
How a remote access policy may be used and its purpose?
The purpose of a remote access policy is to outline the expectations of those users' behaviors while connecting to your network in an attempt to safeguard that network from viruses, threats or other security incidents.
Why you must create a remote access policy for VPN connectivity?
Remote access VPN can be an attractive ground for hackers and malicious attackers, so an organization's server must be protected by a security or network administrator. By having an effective VPN remote access policy, you can reduce the risk of your organization's network assets and support calls from end users.
What is the remote access domain?
... is the domain in which a mobile user can access the local network remotely, usually through a VPN (Figure 7). ...
What belongs to an AUP policy?
An AUP sets rules related to an organization's IT security policies. These include rules around accessing restricted information; changing access data, such as passwords; opening questionable email attachments; using public Wi-Fi services; and using company approved authentication procedures.
What tab must be configured for a user to obtain remote access?
Click Start, point to Administrative Tools, and then click Active Directory Users and Computers. Right-click the user account that you want to allow remote access, and then click Properties. Click the Dial-in tab, click Allow access, and then click OK.
Is VPN considered remote access?
A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive.
What is a network access policy?
Network policies are sets of conditions, constraints, and settings that allow you to designate who is authorized to connect to the network and the circumstances under which they can or cannot connect.
How do I setup remote access to VPN?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
What are the types of remote access?
The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), Point-to-Point Protocol over Ethernet (PPPoE), Point-to-Point Tunneling Protocol (PPTP), Remote Access Services (RAS), and Remote Desktop Protocol (RDP).
What is remote access examples?
Accessing, writing to and reading from, files that are not local to a computer can be considered remote access. For example, storing and access files in the cloud grants remote access to a network that stores those files. Examples of include services such as Dropbox, Microsoft One Drive, and Google Drive.
What is required for remote access?
Remote computer access requires a reliable internet connection. You'll need to activate or install software on the device you want to access, as well as on the device — or devices — you want to use to get that access.
What is the purpose of a password policy?
A password policy is a set of rules designed to enhance computer security by encouraging users to employ strong passwords and use them properly. A password policy is often part of an organization's official regulations and may be taught as part of security awareness training.
What is the use of policy?
A policy is a set of rules or guidelines for your organization and employees to follow in or to achieve compliance. Policies answer questions about what employees do and why they do it. A procedure is the instructions on how a policy is followed.
What constraints are available for use in a remote access policy?
Once a remote access policy has authorized a connection, it can also set connection restrictions (called constraints) based on the following: Encryption strength. Idle timeout. IP packet filters.
What is an example of remote control operations for providing security to an organization?
Popular examples include Remote Desktop Protocol (RDP) and Virtual Network Computing (VNC). While remote desktop access can have convenience advantages, this method is not typically recommended as it introduces significant security risks to the corporate network.
What is IPsec remote access?
IPsec remote access offers customizability and versatility through modification of VPN client software. With APIs in IPsec software, organizations are able to control the function and appearance of the VPN client for applications and special case uses.
Why is remote access important?
Remote access VPN can be an attractive ground for hackers and malicious attackers, so an organization’s server must be protected by a security or network administrator. By having an effective VPN remote access policy, you can reduce the risk of your organization’s network assets and support calls from end users.
What is a Radius server?
It is a software application that provides access to all users, so when a user logs in, the VPN contacts the RADIUS application which authenticates the user through the Mac, Windows or another OS.
What is the importance of remote access VPN?
Before the implementation of a remote-access VPN solution, it is imperative for organizations to define who can use the VPN, what it can be used for, and the security policies that prevent improper or malicious use.
How to keep remote devices up to date?
The operating system of all remote devices must be kept up-to-date by applying patches as soon as they become available to download.
How to reduce exposure to corporate network security threats?
Organizations must consider the following: 1. Avoid split tunneling.
Is encryption good for remote access?
Encryption is a major part of remote access security. Less secured protocols such as IPSEC6 and PPTP connections should be avoided if possible. Organizations should aim for the most secure encryption standards such as IPSEC (3DES) and 256-bit AES. SSL-backed VPN should be considered if it is compatible with company applications: in this case, a connection only allows access to individual ports, IP addresses and applications, which makes it more secure than standard connections that grant access to the whole network.
Updating Remote Access Policies
The first step in understanding whether your access policy is geared for a remote-reliant workforce is by auditing it against your organization’s security objectives.
Focus on Users: Who, What and How
It’s not a new idea that supporting remote workers increases the number of security risks facing your organization. However, with a massive increase in successful ransomware and phishing attacks since the pandemic started, it’s become more obvious that remote employees are opening entry points for attackers.
Remote Workforces of Tomorrow
Reducing the risks of remote work starts with updating the access policies of yesterday. This is the biggest and most crucial effort, and the first step involves throwing away the old perimeter-focused access model and adopting a user-centric approach.
What is the purpose of the ECuras policy?
The purpose of this policy is to define rules and requirements for connecting to eCuras’s network from any host. These rules and conditions are designed to minimize the potential exposure to eCuras from damages which may result from unauthorized use of eCuras resources. Damages include the loss of sensitive or company confidential data, intellectual property, damage to public image, damage to critical eCuras internal systems, and fines or other financial liabilities incurred due to those losses.
Does eCuras use a personal computer?
This policy applies to all eCuras employees, contractors, vendors, and agents with a eCuras-owned or personally-owned computer or workstation used to connect to the eCuras network. This policy applies to remote access connections used to do work on behalf of eCuras, including reading or sending email and viewing intranet web resources. This policy covers any, and all technical implementations of remote access used to connect to eCuras networks.
What is remote access policy?
The remote access policy makes sure that devices that work for the company remotely are protected. That is, both in physical and network security provisions.
Can corporate data and networks expose sensitive information?
However, visiting these sites and platforms using corporate data and networks can expose sensitive information.
Can a criminal steal private corporate data?
Another, a criminal might have a chance to steal private corporate data through an employee’s device left unattended.
Can you avoid remote access instances?
So by applying the remote access policy, you can avoid these instances from happening.
What Is a Remote Access Policy?
For example, sales personnel can now use tablets and other mobile devices to connect remotely to their office networks while on client calls and bring up data that may be important for closing deals . Recent events have further boosted the number of remote workers to an estimated 42% of the US workforce.
What are the considerations when formulating a remote access policy?
Other considerations when formulating a remote access policy include but are not limited to the following: Standardized hardware and software, including firewalls and antivirus/antimalware programs. Data and network encryption standards. Information security and confidentiality. Email usage.
Why Is a Remote Access Policy Important?
If a remote access policy is not in place, such risky behavior could go on unmitigated, without the organization finding out about it until after the occurrence of a breach.
What is remote work?
Remote work has brought with it a few challenges, including potential computer and network security risks. There is a real need for guidelines surrounding remote access, along with other policies. A remote access policy serves as a guide for remote users connecting to the network. It extends the policies governing network and computer use in ...
Why is password policy important?
It helps ensure that only those users who need it are given network access, as long as their devices are also compliant with the guidelines. When implemented properly, it helps safeguard the network from potential security threats.
What is RAS in IT?
Parallels® Remote Application Server (RAS) provides secure remote access for your networks out of the box. It features granular permission policies that enable administrators to enforce access restrictions and settings based on the end-users device or Active Directory group, helping ease the workloads of IT administrators by not requiring any further configuration.
How to ensure that you do not miss anything when updating your remote access policy?
To ensure that you do not miss anything when updating your remote access policy, consider your organizational, legal, contractual and regulatory obligations when you compile the list of policy requirements. After that, identify the procedural and technical controls required to fulfill the policy, making sure to reinforce or replace existing controls that have not been effective.
What is remote access?
Remote access refers to the process of connecting to internal resources from an external source (home, hotel, district, or other public area). The ability to securely and reliably connect to business resources from a remote location increases productivity.
What is information security?
Information security shall determine the appropriate access methodology and hardening technologies up to and including two factor password authentication, smart card, or PKI technology with strong passphrases
What is LEP password policy?
All user passwords shall be strong and follow guidelines and procedures in the [LEP] Access Control and Password Policy. Staff shall ensure that devices used for work purposes are not shared in a multi-user capacity, violate AUP conditions, or used in any inappropriate activity.
What is LEP policy?
This policy defines standards for staff to connect to the [LEP] network from a remote location. These standards are designed to minimize potential exposures including loss of sensitive information, and limit exposure to security concerns through a consistent and standardized access method.
What happens if a staff member is found in a policy violation?
Staff members found in policy violation may be subject to disciplinary action, up to and including termination.
Who bears full responsibility for any access misuse?
Users shall bear full responsibility for any access misuse
Can you use personal equipment to connect to a LEP network?
Personal equipment shall not be used to connect to the [LEP] network using remote connection software and exceptions require [Insert Appropriate Role] written approval
Overview
Purpose
- The purpose of this policy is to define rules and requirements for connecting to eCuras’s network from any host. These rules and conditions are designed to minimize the potential exposure to eCuras from damages which may result from unauthorized use of eCuras resources. Damages include the loss of sensitive or company confidential data, intellectual property, damage to publi…
Scope
- This policy applies to all eCuras employees, contractors, vendors, and agents with a eCuras-owned or personally-owned computer or workstation used to connect to the eCuras network. This policy applies to remote access connections used to do work on behalf of eCuras, including reading or sending email and viewing intranet web resources. This policy ...
Policy
- It is the responsibility of eCuras employees, contractors, vendors, and agents with remote access privileges to eCuras’s corporate network to ensure that their remote access connection is given the same consideration as the user’s on-site connection to eCuras. Public access to the Internet for recreational use through the eCuras network is strictly limited to eCuras employees, contract…
Policy Compliance
- 5.1 Compliance Measurement The Infosec Team will verify compliance with this policy through various methods, including but not limited to periodic walk-thrus, video monitoring, business tool reports, internal and external audits, and inspection. It will provide feedback to the policy owner and appropriate business unit manager. 5.2 Exceptions Any exception to the policy must be app…
Related Standards, Policies, and Processes
- Please review the following policies for details of protecting information when accessing the corporate network via remote access methods and acceptable use of eCuras’s network: 1. 1. Acceptable Encryption Policy 2. 2. Acceptable Use Policy 3. 10. Password Construction Guidelines 4. 11. Password Protection Policy 5. 17. Remote Access Tools Policy Revised: March 14th, 2018
Table of Content