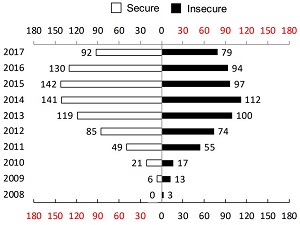
Insecure remote access is one of the leading causes of payment data breaches for businesses. View this infographic on the dangers of insecure remote access and tips and resources to minimize the chances of being breached.
Full Answer
What is meant by secure remote access?
Secure Remote Access is a combination of security processes or solutions that are designed to prevent unauthorized access to an organization's digital assets and prevent the loss of sensitive data.
What is the risk of remote access?
The overriding risk of remote access services and software is a hacker gaining deeper access to your organization, exposing you to a host of IT security threats. Once they gain privileged access to your system, it will be difficult to prevent data loss, prevent phishing, protect against ransomware, etc.
Why is remote access not secure?
In many cases, servers with RDP publicly accessible to the internet have failed to enable multi-factor authentication (MFA). This means that an attacker who compromises a user account by exposing a weak or reused password through a brute force attack can easily gain access to a user's workstation via RDP.
How do you secure remote access?
Basic Security Tips for Remote DesktopUse strong passwords. ... Use Two-factor authentication. ... Update your software. ... Restrict access using firewalls. ... Enable Network Level Authentication. ... Limit users who can log in using Remote Desktop. ... Set an account lockout policy.
What are the types of remote access?
The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), Point-to-Point Protocol over Ethernet (PPPoE), Point-to-Point Tunneling Protocol (PPTP), Remote Access Services (RAS), and Remote Desktop Protocol (RDP).
What types of attacks are remote access servers vulnerable to?
Other attacks which hackers can facilitate through remote access include email phishing, third-party vendor compromise, insider threats, social engineering, and the use of vulnerable applications to compromise systems. Hackers use Common remote access tools to penetrate third-party access to merchant information ...
What are security considerations for remote users examples?
Five Remote Access Security Risks And How To Protect Against ThemWeak remote access policies. ... A deluge of new devices to protect. ... Lack of visibility into remote user activity. ... Users mixing home and business passwords. ... Opportunistic phishing attempts.
Which is the secure standard function for remote access?
MFA is imperative to authenticate users for secure remote access. Many regulations and compliance standards require MFA for privileged remote access.
What are some security issues related to remote desktop?
These are the most important vulnerabilities in RDP:Weak user sign-in credentials. Most desktop computers are protected by a password, and users can typically make this password whatever they want. ... Unrestricted port access. RDP connections almost always take place at port 3389*.
Is IT safe to allow remote access?
Remote access solutions could leave you vulnerable. If you don't have proper security solutions in place, remote connections could act as a gateway for cybercriminals to access your devices and data. Hackers could use remote desktop protocol (RDP) to remotely access Windows computers in particular.
Is Remote Assistance safe?
When you're using remote assistance or remote desktop, the host computer is only as safe as the connection. The security surrounding remote assistance versus remote desktop is similar in the sense that both are vulnerable to cyberattacks.
Why is the remote access domain the most risk prone of all in a typical IT infrastructure?
Why is the Remote Access Domain the most risk prone of all within a typical IT infrastructure? Because it allows users to connect to intranet from remote locations.
What is a responder attack?
‘Responder’ attacks involve tricking Windows systems into connecting to a fake Windows service, which in turn requests authentication and then captures the password hash that is sent. This enables further attacks against Active Directory.
What can an attacker inject into a website?
Once the attacker controls DNS and routing (with a malicious Access Point) they can inject code into legitimate websites to exert remote control over the victim’s computer, eg.using it as a pivot point to tunnel traffic into the corporate network.
How long is the Work from Home Security Awareness training?
Still working from home? Take this 45-minute training to ensure your work set-up is secure: New Training: Work from Home Security Awareness.
Do you need to have unique credentials to allow remote access?
Require unique credentials: If you must allow remote access, make sure your vendors use remote access credentials that are unique to your business and that are not the same ones used for other customers.
What is secure remote access?
Secure remote access describes the ability to securely access networks, devices, and applications from a “remote” location, which means “off the network.”
Why are IPs never exposed to the internet?
IPs are never exposed to the internet, creating a “darknet” and making the network impossible to find. Apps segmentation ensures that once users are authorized, application access is granted on a one-to-one basis so that authorized users have access only to specific applications rather than full access to the network.
What is Zscaler private access?
Looking more closely, Zscaler Private Access (ZPA) service provides secure remote access to internal applications in the cloud without placing users on the corporate network. The cloud service requires no complex remote access VPN gateway appliances and uses cloud-hosted policies to authenticate access and route user traffic to the closest application location to them. ZPA is a true software-defined solution that can work in conjunction with direct access technology. It directly connects customer data centers with cloud service provider data centers.
Can a VPN attack be zero trust?
They can (and do) exploit the VPN attack surface to infiltrate the network, deliver malware such as ransomware, launch denial-of-service attacks, and exfiltrate critical business data. In contrast, the zero trust approach treats all traffic, including traffic already inside the perimeter, as hostile.
What is the only variable that matters in a brute force attack?
The ONLY variable that matters in a brute force attack is password length. length = strength.
Can you restrict RDP to IP?
This is one of those debates that will get heated, quickly, because some people believe if you restrict RDP to only a given IP, with a password the length of a football field in all mixed cases, you'll be fine - but you wont. That said, you (whoever you are) accept the risk by doing so.
Is RDP more common than remote access?
RDP is more common, thus it gets more attention from persistent threat actors than more obscure remote tools. The other tools suffer the same issue as RDP, the mechanism of remote access is inherently dangerous. The dichotomy between operations/accessibility, and security is a ubiquitous conundrum we often face.
Is RDP secure in 2021?
Feb 16, 2021 at 8:34 AM. No, RDP isn't any less secure than many of it's competitors. The weakness of RDP is the choice of poor passwords. If you wanted to secure RDP, you likely could do well but why wouldn't you introduce another layer (a VPN) as we all know, multiple layers are what gives us security.
Can RDP be compromised?
RDP also uses certificates, and by default, self-signed, these too can be compromised, negating password attacks. If you really must use RDP and not a VPN, use an RDP gateway, but where possible, and given how security is moving us, VPN should always be option 1. 3 found this helpful.
Is RDP insecure?
RDP in and of itself is not insecure, although it's not the most secure product out there. The same could be said of Office 365 - if the password is easy to guess or password is compromised in any way, there goes your Office 365 security. I am seeing far more reports of Office 365 being "hacked.".
Examples of Secure remote access in a sentence
Secure remote access to land records shall be by paid subscription service through individual circuit court clerk's offices pursuant to § 17.1-276, or through designated application service providers.
More Definitions of Secure remote access
Secure remote access means remote access through a network (whether a stand -alone network or a virtual network within the Internet ), which is only accessible to Authorized Users approved by the Client whose identity is authenticated at the time of login and periodically thereafter consistent with best practice and whose conduct is subject to regulation by the Client.
How does secure remote access work?
A well-designed remote access tool can enable secure connections to target systems and prevent unauthorized access. The following steps define a general secure remote access process, and are applicable for most of the enterprise remote access architectures.
What are the benefits of adopting secure remote access methods?
Implementing a secure remote access solution as part of their cybersecurity program helps enterprises mitigate security risks, reduce operational complexity, improve visibility into privileged access, and adhere to compliance standards.
What is ManageEngine Access Manager Plus?
ManageEngine Access Manager Plus is a secure remote access solution built to take care of administrative access to remote endpoints and other critical IT systems. The solution's gateway server routes all remote connections through an encrypted channel, protecting enterprise networks from malware and cybercrime. Through robust authentication, granular controls, and session management capabilities, Access Manager Plus minimizes deliberate and unintentional access misuse risks while also letting enterprises choose and design a utilitarian remote access strategy.
What is the most common form of remote access?
VPNs are the most common form of remote access. They use authentication and encryption to establish a secure connection to a private network over the internet.
Why is privileged session monitoring important?
Privileged session monitoring and recording promote organizational transparency and enable IT admins to view and, if necessary, interrupt and terminate a malicious privileged session.
What are the challenges of remote working?
Remote working also presents new challenges, notably employees being caught by sophisticated phishing scams and hacking attempts. Cybercriminals leverage weak and vulnerable points in insecure remote access methods and VPNs to wreak havoc.
Do enterprises trust users?
Enterprises must not automatically trust users or applications trying to access the internal network. It’s crucial to know who or what is requesting access, why, and from where.
