Introduction. Check Point offers multiple enterprise-grade VPN clients to fit a wide variety of organizational needs. The Remote Access VPN stand-alone clients provide a simple and secure way for endpoints to connect remotely to corporate resources over the Internet, through a VPN tunnel, and are all SmartDashboard -managed.
Full Answer
How to setup a remote access VPN?
Use a VPN Router with the built-in VPN server capability
- Launch a browser window from your PC connected to the routers’ network
- Enter the router IP address in the search to login into your router
- Enter the username and password of your router and login into it.
- Go to the Settings page and select VPN Service or setup page.
- Enable the VPN service by selecting the checkbox and apply
How to speed up VPN remote access?
How to speed up a VPN
- Choose another server. Connecting to your nearest server will usually offer the best performance, but there are occasional exceptions.
- Refresh your system. If speeds are notably worse than unusual with several servers, the problem could be closer to home. ...
- Switch protocol. ...
- Tweak protocol settings. ...
- Use a wired connection. ...
- Try split tunneling. ...
How do access remote network with OpenVPN?
Using OpenVPN to Securely Access Your Network Remotely
- Visit http://tplinkwifi.net, and log in with your TP-Link ID or the password you set for the router.
- Go to Advanced > VPN Server > OpenVPN, select the checkbox to enable VPN Server.
- Select the Service Type (communication protocol) for OpenVPN Server: UDP, TCP.
How to activate open VPN?
- Right-click the Start button.
- Click Settings. Source: Windows Central
- Click Network & Internet.
- Click VPN. Source: Windows Central
- Click Add a VPN connection.
- Click the dropdown menu below VPN provider. Source: Windows Central
- Click Windows (built-in).
- Click the Connection name field. ...
- Type a name for the VPN connection. ...
- Click the Server name or address field. ...

What is remote access VPN Check Point?
Provide users with secure, seamless remote access to corporate networks and resources when traveling or working remotely. Privacy and integrity of sensitive information is ensured through multi-factor authentication, endpoint system compliance scanning and encryption of all transmitted data.
What type of VPN is Check Point?
The Check Point secured VPN implementation is based on IPSec (IP Security). IPSec is a commonly used set of protocols that was developed to support the secure exchange of packets at the IP layer between gateways that are connected over a public network (such as the Internet), and to create VPNs.
How do I access Check Point VPN?
Basic Gateway ConfigurationIn SmartConsole, right click the gateway and select Edit. ... In the Network Security tab, select IPsec VPN to enable the blade. ... Add the gateway to the Remote Access VPN Community: ... Set the VPN domain for the Remote Access community. ... Configure Visitor Mode. ... Configure Office Mode. ... Click OK.
How does remote access work with VPN?
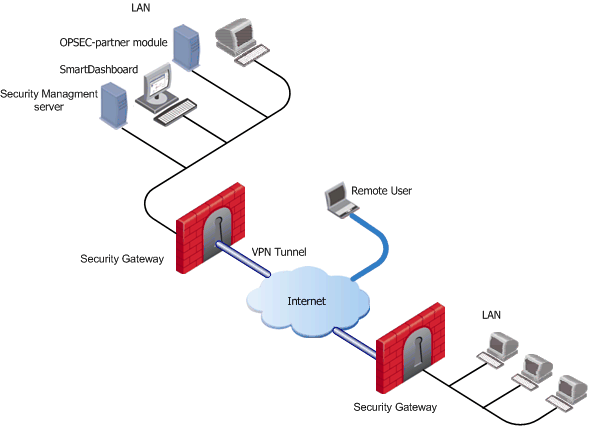
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
What are the 3 types of VPN?
The Three Main Types of VPNs VPNs can be divided into three main categories – remote access, intranet-based site-to-site, and extranet-based site-to-site. Individual users are most likely to encounter remote access VPNs, whereas big businesses often implement site-to-site VPNs for corporate purposes.
What are 2 types of VPN?
Types of VPNsSite-to-Site VPN: A site-to-site VPN is designed to securely connect two geographically-distributed sites. ... Remote Access VPN: A remote access VPN is designed to link remote users securely to a corporate network.More items...
Who makes Checkpoint VPN?
Check Point Software Technologies Ltd. For the last three decades, Check Point Software Technologies Ltd. (www.checkpoint.com) has set the standard for Cyber Security.
How does Checkpoint endpoint security work?
Endpoint protection works via a combination of network and device-level defenses. At the network level, the organization may restrict access to the enterprise network based on a device's compliance with corporate security policies and least privilege.
What is mobile checkpoint VPN?
Remote Access with Encrypted VPN Technology Check Point Mobile Access uses SSL/TLS VPN and IPsec technologies to secure encrypted communication from unmanaged Smartphones, tablets, PCs, and laptops to your corporate IT infrastructure.
What is the difference between VPN and remote access?
A VPN is a smaller private network that runs on top of a larger public network, while Remote Desktop is a type of software that allows users to remotely control a computer. 2. Remote Desktop allows access and control to a specific computer, while VPN only allows access to shared network resources.
Which VPN is best for remote access?
NordVPN is one of the best remote access VPNs on the market with support for enterprises and consumers alike. It has over 5,000 servers in 60 countries.
What are the types of remote access?
The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), Point-to-Point Protocol over Ethernet (PPPoE), Point-to-Point Tunneling Protocol (PPTP), Remote Access Services (RAS), and Remote Desktop Protocol (RDP).
How does f5 VPN Work?
An even more secure version of the VPN is the Secure Sockets Layer Virtual Private Network (SSL VPN). An SSL VPN uses the Secure Sockets Layer (SSL) protocol to create a secure and encrypted connection over the Internet. The SSL VPN was created to ensure enhanced security and privacy.
How do I troubleshoot my VPN checkpoint?
Things to look for when troubleshooting a Checkpoint VPN connection:VPN domains. Review setup in the topology of an item. ... Encryption Domains. Your firewall contains your networks. ... Rule Setup. ... Pre-shared secret or certificate. ... RuleSet. ... Address Translation. ... TRADITIONAL MODE NOTES. ... SIMPLIFIED MODE NOTES.More items...•
How do I configure site to site VPN in Checkpoint firewall?
Configuration - Check Point security gatewayOpen SmartConsole > Security Policies > Access Tools > VPN Communities.Click Star Community. ... Enter an Object Name for the VPN Community.In the Center Gateways area, click the plus sign to add a Check Point Security Gateway object for the center of the community.More items...•
How do I get around location checkpoint Roobet?
Using a VPN to Unblock Roobet A VPN will mask your real IP address by routing your Internet traffic through a securely encrypted server. Before connecting to a VPN, you can pick a server from a list of countries. After you've connected, any website or app you access will think you are located in that server's country.
Remote Access VPN Products
Remote access is integrated into every Check Point network firewall. Configure client-to-site VPN or set up an SSL VPN Portal to connect from any browser.
What is Remote Access VPN?
Remote Access VPN ensures that the connections between corporate networks and remote and mobile devices are secure and can be accessed virtually anywhere users are located. A secure remote access solution promotes collaboration by connecting global virtual teams at headquarters, branch offices, remote locations, or mobile users on the go.
Technical Resources
The place to discuss all of Check Point’s Remote Access VPN solutions, including Mobile Access Software Blade, Endpoint Remote Access VPN, SNX, Capsule Connect, and more!
Our Customers Love Us
Versatile Security Protection –Like A Swiss Army Knife For Security Checkpoint Next Generation Firewall proves to be a great solution for our small business infrastructure. R80 Security Management has allowed our company to easily (and significantly) improve our protections over time. read more >
Quantum is powered by ThreatCloud
ThreatCloud, the brain behind all of Check Point’s products, combines the latest AI technologies with big data threat intelligence to prevent the most advanced attacks, while reducing false positives.
What is a remote access VPN community?
By default, the Remote Access VPN Community includes a user group, All Users, that includes all defined users. You can use this group or add different user groups to the Remote Access VPN Community. The community can contain users defined in LDAP, which includes Active Directory, or users defined on the Security Management Server.
How to enable IPsec VPN?
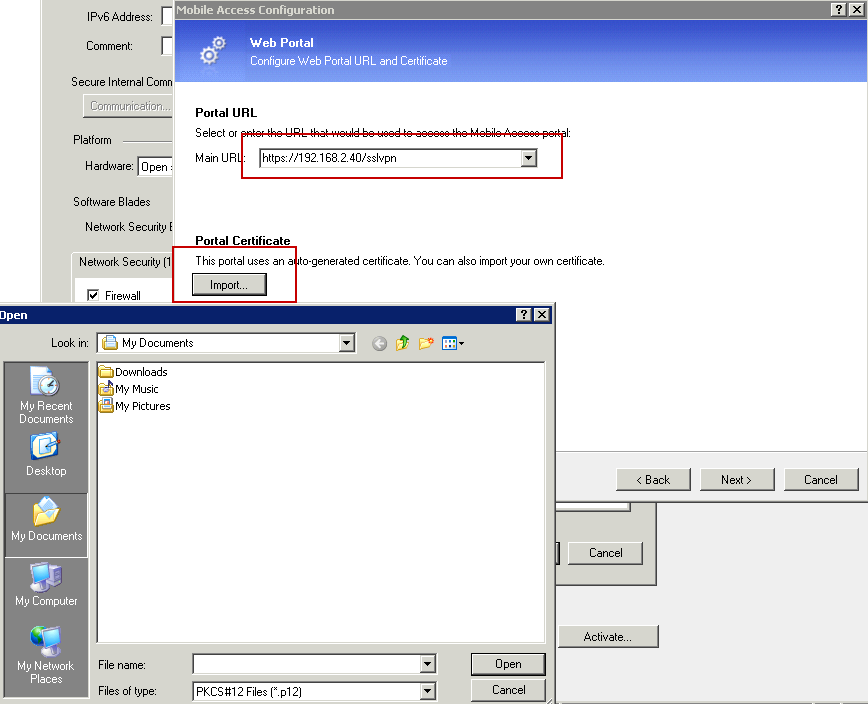
From SmartConsole, use the Gateways & Servers menu to configure the gateway and blades. Double-click the gateway. The Check Point Gateway window opens. In the Network Security tab at the bottom, select I Psec VPN to enable the blade.
What happens when no authentication methods are defined for the gateway?
If no authentication methods are defined for the gateway, users select an authentication method from the client.
Does any VPN rule apply to all VPN communities?
Any - The rules applies to all VPN Communities. If you configure a new VPN Community after the rule was created, the rule also applies to the new VPN Community. One or more specified VPN communities - For example, RemoteAccess. Right-click in the VPN column of a rule and select Specific VPN Communities.
Which service defines the protocol and port of client connections to the gateway?
Optional - Select the Visitor Mode Service, which defines the protocol and port of client connections to the gateway.
Do you need to authenticate to a VPN gateway?
Users must authenticate to the VPN gateway with a supported authentication method. You can configure authentication methods for the remote access gateway in:
What is remote access client?
Remote Access Clients Selective Routing lets you define different encryption domains for each VPN site-to- site community and Remote Access (RA) Community. You must have a VPN domain configured. The domain includes participating Security Gateways.
What is location awareness remote access?
Location Awareness Remote Access Clients intelligently detects if it is in the VPN domain (Enterprise LAN), and automatically connects or disconnects as required. If the client senses that it is in the internal network, the VPN connection is terminated. In Always-Connect mode, the VPN connection is established whenever the client exits the internal network.
What is SCV in VPN?
Compliance Policy - Secure Configuration Verification (SCV) SCV monitors the configuration of remote computers, to confirm that the configuration complies with organization Security Policy, and the Security Gateway blocks connectivity for computers that do not comply. It is available in Endpoint Security VPN and Check Point Mobile for Windows.
What is SCV policy?
The SCV policy inspects elements of the client configuration, and returns the compliance status of the client. During installation, Remote Access Clients register their SCV DLLs as SCV plug-ins in the system registry.
What is VPN firewall?
Desktop FirewallEndpoint Security VPN enforces a Desktop Firewall on remote clients. The administrator defines the Desktop Security Policy in the form of a Rule Base. Rules can be assigned to either specific user groups or all users; this permits the definition of flexible policies.
What is E75.10 VPN?
Remote Access Clients E75.10 are lightweight remote access clients for seamless, secure IPSec VPN connectivity to remote resources . They authenticate the parties and encrypt the data that passes between them. Remote Access Clients E75.10 are intended to replace the current Check Point remote access clients: SecureClient NGX, Endpoint Connect NGX, and SecuRemote client NGX. The clients offered in this release are: Endpoint Security VPN- Replaces SecureClient and Endpoint Connect. Check Point Mobile for Windows- New Remote Access Client. SecuRemote- Replaces SecuRemote client NGX.
What is a certificate in security?
certificate is a digital ID card. It is issued by a trusted third party known as a Certification Authority (CA). Remote Access Clients can use the digital certificates issued by the Security Gateway, which has its own Internal Certificate Authority (ICA). A digital certificate has: