RemoteIoT offers a simple way to monitor Raspberry Pi
Raspberry Pi
The Raspberry Pi is a series of small single-board computers developed in the United Kingdom by the Raspberry Pi Foundation to promote teaching of basic computer science in schools and in developing countries. The original model became far more popular than anticipated, selling outsid…
Full Answer
How to remotely connect to a closed device behind a firewall?
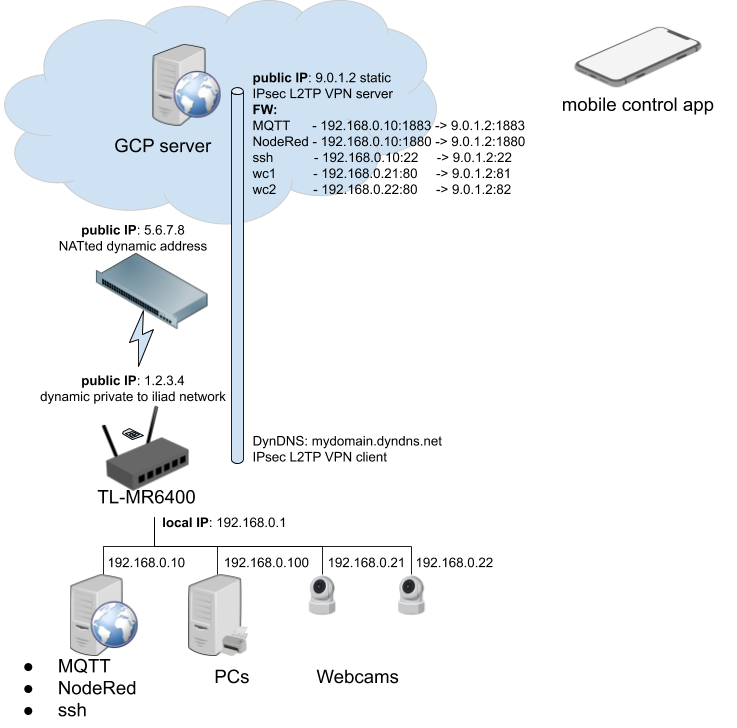
Often web server access to remote devices behind a firewall is needed (Wifi router, smart home). This is how you can solve this securely. Using ssh port forwarding to remotely connect to a closed device running a web server behind a firewall
What is remote access for IoT devices?
JFrog Connect remote access tools are capable of providing you all kinds of remote access to your IoT devices that reside at client premises that can either be behind wired or wireless NAT, double NAT networks, restricted networks, or even 3G/4G/5G cellular networks.
Is your industrial IoT application running on a firewall?
Many industrial IoT applications have parameters that need to be configured or they contain interesting information but the device they are running on is not accessible in terms of OS (operating system) and it is protected from external access through firewalls.
How to protect your IoT devices from DDoS attacks?
Make your IoT device virtually invisible to any port scans and protect against DDoS attacks. The RemoteIoT API enables greater automation and integration of Remote IoT services into your system. To access your IoT device from anywhere with these web services. Our easy-to-use interface allows you to manage machines from any kind of device!
Do IoT devices have firewall?
The IoT Firewall is a User-Plane firewall, deployed in the Service Provider's core network, that features key differences from traditional network firewalls to allow better efficacy when deployed within the IoT domain. The IoT Firewall provides device-aware, application-centric firewall policies.
Can IoT be remotely controlled?
IoT remote control is useful for any situation in which you want to securely manage IoT devices at scale from a remote dashboard. You can monitor device sensor readings, system and network performance, hardware vitals, and proactively troubleshoot issues. Some applications include: Robotics.
What is the use of firewall in IoT networks?
IoT firewalls aim to protect IoT devices from internal and external threats, in addition to attacks on the network like DDoS and MiTM. Moreover, they can provide device-specific IP address mapping and apply device-based rules and policies.
How do I access IoT devices?
Usually, since these embedded IoT devices run a flavor of Linux operating system, there are many ways to access them remotely through the internet such as:SSH connections.VPN connections.Proxy connections.RDP connections etc.
What is remote IoT?
IoT is a network of various connected systems, devices, and sensors. Gateways, machines, and computers are aligned together to transfer information over the wireless network without human interference. IoT links people with things remotely, as well as things to things at the same time.
What is remote monitoring IoT?
Remote Monitoring of IoT Devices utilizes AWS IoT Events to collect, analyze, and detect faults and/or suboptimal performance to generate events in real time. These events are then used to invoke automatic alerts and actions to automate diagnostics and initiate maintenance requests for that device.
What are the 3 types of firewalls?
Firewall delivery methodsHardware-based firewalls. A hardware-based firewall is an appliance that acts as a secure gateway between devices inside the network perimeter and those outside it. ... Software-based firewalls. A software-based firewall, or host firewall, runs on a server or other device. ... Cloud/hosted firewalls.
What are the three functions of a firewall?
The functions of a firewall in a network are:Controlling and Monitoring Data Packet Flow.Become a Network Security Post.Log User Activity.Prevent Information Leakage.
What are the two main types of firewall?
The most common firewall types based on methods of operation are: Packet-filtering firewalls. Proxy firewalls.
How does IoT connect to the internet?
The first step or “hop” in IoT communication will either be wired or wireless. Wired connections may use a simple serial protocol, though most frequently a networking system like Ethernet will be employed, allowing “direct” Internet protocol (TCP/IP) connections to a network server or cloud application.
How do I secure my IoT devices on my home network?
Securing IoT Networks and DevicesChange the name and password of the router. ... Use strong passwords that are random passwords containing a mix of letters, characters, and symbols.Avoid using public Wi-Fi when you're accessing your IoT network through your laptop or smartphone. ... Start using guest networks.More items...
How do IoT devices work with networking?
IoT devices share the sensor data they collect by connecting to an IoT gateway or other edge device where data is either sent to the cloud to be analyzed or analyzed locally. Sometimes, these devices communicate with other related devices and act on the information they get from one another.
What ports do IoT devices use?
Top 20 Attacked IoT PortsServicePortIoT Device TypeHTTPPort 80Mainly web apps but includes common IoT devices, ICS and gaming consolesTelnetPort 23ALLSIPPort 5060ALL VoIP phones, video conferencingHTTP_AltPort 8080SOHO routers, smart sprinklers, ICS16 more rows•Oct 24, 2018
Why do we need IoT devices?
Why is IoT important? The internet of things helps people live and work smarter, as well as gain complete control over their lives. In addition to offering smart devices to automate homes, IoT is essential to business.
What are the characteristics of Internet of things?
Seven IoT characteristicsConnectivity. This doesn't need too much further explanation. ... Things. Anything that can be tagged or connected as such as it's designed to be connected. ... Data. ... Communication. ... Intelligence. ... Action. ... Ecosystem.
Which two technologies are considered 4th generation cellular based technologies that commonly require monthly payments to connect IoT devices choose two?
Explanation: Both LTE and WiMAX use cellular data networks to connect IoT devices and require monthly payments with specific data caps.
Solution overview
I will walk you through the steps for building a web based local proxy to gain access to remote devices using secure tunneling. The local proxy is a software proxy that runs on the source, and destination devices. The local proxy relays a data stream over a WebSocket secure connection between the Secure tunneling service and the device application.
Walkthrough
The first step is to open a tunnel and download the access tokens for the source and destination as described in open a tunnel and start SSH session to remote device.
Cleaning up
To avoid incurring future charges, delete the resources created during this walkthrough.
Conclusion
Secure Tunneling provides a secure, remote access solution that directly integrates with AWS IoT to allow you to access your IoT devices remotely from anywhere.
How is IoT protected?
Many industrial IoT applications have parameters that need to be configured or they contain interesting information but the device they are running on is not accessible in terms of OS (operating system) and it is protected from external access through firewalls. Often that makes sense as they operate an open web server on port 80 (http) or they have a low security web application setup with only basic login. Therefore these devices are isolated from the outside by firewall and NAT.
What port is used to tunnel through VPN?
This device usually needs to provide a VPN to be reachable from the outside. So any secure or non-secure port (80, 443 or any port) can be tunnelled through the secure VPN of the second device. Then on the local desktop machine ssh is used to make the specific port accessible.
What port is used to tunnel through VPN?
This device usually needs to provide a VPN to be reachable from the outside. So any secure or non-secure port (80, 443 or any port) can be tunnelled through the secure VPN of the second device. Then on the local desktop machine ssh is used to make the specific port accessible.
What is ssh port forwarding?
ssh port forwarding through VPN: But there is a technique called ssh port forwarding that can resolve this . The idea is to have another device in the local network that can be accessed through a virtual private network with ssh.
Is IoT protected from external access?
Many industrial IoT applications have parameters that need to be configured or they contain interesting information but the device they are running on is not accessible in terms of OS (operating system) and it is protected from external access through firewalls.
