
What VPN license do I need to use IPSEC remote access VPN?
IPsec remote access VPN using IKEv2 requires an AnyConnect Plus or Apex license, available separately. IPsec remote access VPN using IKEv1 and IPsec site-to-site VPN using IKEv1 or IKEv2 uses the Other VPN license that comes with the base license.
What are remote access VPNs?
Remote access VPNs allow users to connect to a central site through a secure connection over a TCP/IP network. The Internet Security Association and Key Management Protocol, also called IKE, is the negotiation protocol that lets the IPsec client on the remote PC and the ASA agree on how to build an IPsec Security Association.
How to configure client-to-site VPN tunnels with IPsec?
Step 1. Log in to the router web-based utility and choose VPN > Client-to-Site. Step 2. Click the Add button under IPSec Client-to-Site Tunnels section.
Does topology require a license?
Does the PA220 have a VPN?
About this website
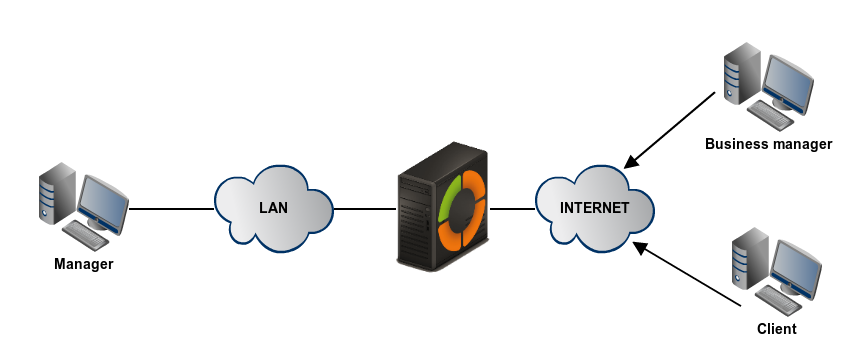
Which 2 methods of authentication can be used for IPsec remote access connections?
Remote access supports two types of authentication: device and user. I discussed the three different methods of performing device authentication in Chapter 19, "IPSec Site-to-Site Connections": preshared keys, RSA encrypted nonces, and RSA signatures (digital certificates).
Does remote access VPN use IPsec?
While Remote access VPN supports SSL and IPsec technology.
What is IPsec remote access VPN?
Internet Protocol Security (IPsec) is a suite of protocols that support cryptographically secure communication at the IP layer. With IPsec connections, you can provide secure access between two hosts, two sites, or remote users and a LAN. The firewall supports IPsec as defined in RFC 4301.
What is the difference between remote access VPN and site-to-site VPN?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
What is the difference between IPsec and site-to-site VPN?
Site-to-Site VPN provides a site-to-site IPSec connection between your on-premises network and your virtual cloud network (VCN). The IPSec protocol suite encrypts IP traffic before the packets are transferred from the source to the destination and decrypts the traffic when it arrives.
What are the 3 protocols used in IPsec?
IPsec is a suite of protocols widely used to secure connections over the internet. The three main protocols comprising IPsec are: Authentication Header (AH), Encapsulating Security Payload (ESP), and Internet Key Exchange (IKE).
What is a site-to-site IPSec?
A site-to-site IPsec tunnel interconnects two networks as if they were directly connected by a router. Systems at Site A can reach servers or other systems at Site B, and vice versa. This traffic may also be regulated via firewall rules, as with any other network interface.
Is IPSec VPN better than SSL VPN?
When it comes to corporate VPNs that provide access to a company network rather than the internet, the general consensus is that IPSec is preferable for site-to-site VPNs, and SSL is better for remote access.
How do I connect my site-to-site VPN?
To set up a Site-to-Site VPN connection using a virtual private gateway, complete the following steps:Prerequisites.Step 1: Create a customer gateway.Step 2: Create a target gateway.Step 3: Configure routing.Step 4: Update your security group.Step 5: Create a Site-to-Site VPN connection.More items...
What are 3 types of VPN tunnels?
We'll look at three of the most common: IPsec tunnels, Dynamic multi point VPNs, and MPLS-based L3VPNs.IPsec Tunnels. In principle, a network-based VPN tunnel is no different from a client-based IPsec tunnel. ... Dynamic Multi point VPN (DMVPN) ... MPLS-based L3VPN.
How does remote access VPN Work?
The remote access VPN does this by creating a tunnel between an organization's network and a remote user that is “virtually private,” even though the user may be in a public location. This is because the traffic is encrypted, which makes it unintelligible to any eavesdropper.
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
How do I connect to IPsec?
Creating an IPsec VPN connectionNavigate to the Network and Sharing Center. ... Click Set up a new connection or network.Select Connect to a workplace, and then click Next.If prompted with "Do you want to use a connection that you already have?", select No, create a new connection, and then click Next.More items...•
What is IP security in network security?
What is IPsec? IPsec (Internet Protocol Security) is a suite of protocols that secure network communication across IP networks. It provides security services for IP network traffic such as encrypting sensitive data, authentication, protection against replay and data confidentiality.
How to Troubleshoot IPSec VPN connectivity issues - Palo Alto Networks
This document is intended to help troubleshoot IPSec VPN connectivity issues. It is divided into two parts, one for each Phase of an IPSec VPN. Phas
Palo Alto VPN tunnel up with no traffic | Blue Network Security
Looking at the above snippet there was a couple of interesting things. NAT-T seemed to be failing between the two firewalls, and it looked like the remote ASA was not using port 4500/udp as it should have.
Does topology require a license?
For such topology, does not require any special license.
Does the PA220 have a VPN?
In case this isn't clear.... the WAN interface of the PA220 would service both the remote access vpn and the ipsec site -to-site vpn.
What is client IP?
Client — This option allows the client to request for an IP address and the server supplies the IP addresses from the configured address range.
How to add VPN to Cisco router?
Step 1. Log in to the router web-based utility and choose VPN > Client-to-Site. Step 2. Click the Add button under IPSec Client-to-Site Tunnels section. Step 3. In the Add a New Tunnel area, click the Cisco VPN Client radio button. Step 4. Check the Enable check box to enable the configuration. Step 5.
What is VPN client?
In a Client-to-Site Virtual Private Network (VPN) connection, clients from the Internet can connect to the server to access the corporate network or Local Area Network (LAN) behind the server but still maintains the security of the network and its resources. This feature is very useful since it creates a new VPN tunnel that would allow teleworkers and business travelers to access your network by using a VPN client software without compromising privacy and security.
How does IKE peer authentication work?
Pre-shared Key — IKE peers authenticate each other by computing and sending a keyed hash of data that includes the Pre-shared Key. If the receiving peer is able to create the same hash independently using its Pre-shared key, it knows that both peers must share the same secret, thus authenticating the other peer.
Which crypto protocol allows the IPsec client and the ASA to establish a shared secret key?
Specify the Diffie-Hellman group for the IKE policy—the crypto protocol that allows the IPsec client and the ASA to establish a shared secret key.
What happens if a Cisco VPN client has a different preshared key size?
If a Cisco VPN Client with a different preshared key size tries to connect, the client logs an error message indicating it failed to authenticate the peer.
What files can Cisco AnyConnect have?
Virtual File System creation for each context can have Cisco Anyconnect files like Image and profile.
What is the first phase of ISAKMP?
Phase 1 creates the first tunnel to protect later ISAKMP negotiation messages. Phase 2 creates the tunnel that protects data travelling across the secure connection.
Do you need a mask for a VPN?
The address mask is optional. However, You must supply the mask value when the IP addresses assigned to VPN clients belong to a non-standard network and the data could be routed incorrectly if you use the default mask. A typical example is when the IP local pool contains 10.10.10.0/255.255.255.0 addresses, since this is a Class A network by default. This could cause routing issues when the VPN client needs to access different subnets within the 10 network over different interfaces.
Does topology require a license?
For such topology, does not require any special license.
Does the PA220 have a VPN?
In case this isn't clear.... the WAN interface of the PA220 would service both the remote access vpn and the ipsec site -to-site vpn.
