Configure IPsec (remote access)
| Name | Setting |
| Interface | Select a WAN port. |
| Authentication type | Specify a preshared key or the local and ... |
| Local ID Remote ID | Specify the IDs if required. |
| Allowed user | Select the users you want to allow. |
Full Answer
What are remote access VPNs?
Remote access VPNs allow users to connect to a central site through a secure connection over a TCP/IP network. The Internet Security Association and Key Management Protocol, also called IKE, is the negotiation protocol that lets the IPsec client on the remote PC and the ASA agree on how to build an IPsec Security Association.
How do I configure IPsec remote access?
†Set the connection type to IPSec remote access. †Configure the address assignment method, in the following example, address pool. †Configure an authentication method, in the following example, preshared key.
How do I set up a SonicWall VPN connection?
Input the WAN IP Address or Domain Name of the SonicWall that the User it VPN connecting to. Click on the new connection that is created and click Enable. When prompted, enter the Preshared Secret for the connection, as well as the Username and Password.
How do I enable IPsec xauth for a user?
Add a user, grant the user the User - VPN - IPsec xauth Dialin permission, or add them to a group with this permission. Note that for xauth, the password used is the password for the user, not the “IPsec Pre-Shared Key” field. That is used for non-xauth IPsec.

What is IPsec remote access VPN?
The IPsec Remote Access feature introduces server support for the Cisco VPN Client (Release 4. x and 5. x) software clients and the Cisco VPN hardware clients. This feature allows remote users to establish the VPN tunnels to securely access the corporate network resources.
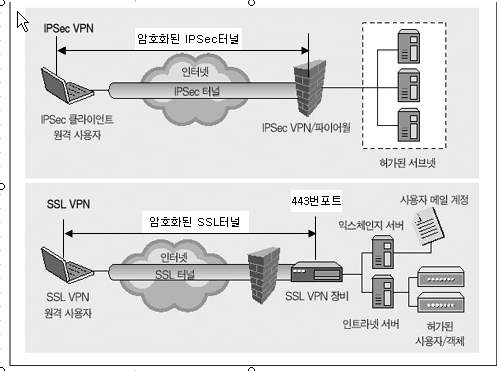
Does remote access VPN use IPsec?
While Remote access VPN supports SSL and IPsec technology.
Is VPN and IPsec same?
The major difference between an IPsec VPN and an SSL VPN comes down to the network layers at which encryption and authentication are performed. IPsec operates at the network layer and can be used to encrypt data being sent between any systems that can be identified by IP addresses.
What is IPsec remote access VPN Sophos XG?
Internet Protocol Security (IPsec) is a suite of protocols that support cryptographically secure communication at the IP layer. With IPsec connections, you can provide secure access between two hosts, two sites, or remote users and a LAN. The firewall supports IPsec as defined in RFC 4301.
Which is better IPsec or SSL VPN?
When it comes to corporate VPNs that provide access to a company network rather than the internet, the general consensus is that IPSec is preferable for site-to-site VPNs, and SSL is better for remote access.
Is Cisco Anyconnect SSL or IPsec?
Anyconnect is the replacement for the old Cisco VPN client and supports SSL and IKEv2 IPsec. When it comes to SSL, the ASA offers two SSL VPN modes: Clientless WebVPN.
Is IPsec only used for VPN?
While IPsec isn't the only protocol out there, it's strong in three scenarios: VPN security, application security, and routing security. VPN security—particularly for businesses—is noteworthy. The IPsec standard comes with baked-in support for multiple cryptographic methodologies.
Can IPsec be hacked?
Hackers Could Decrypt IPsec Information However, a team of researchers discovered numerous security vulnerabilities related to an internet key exchange protocol called “IKEv1.” IPsec maintains encrypted connections between two parties when both of them define and exchange shared keys during communications.
What are the 3 protocol used in IPsec?
IPsec is a suite of protocols widely used to secure connections over the internet. The three main protocols comprising IPsec are: Authentication Header (AH), Encapsulating Security Payload (ESP), and Internet Key Exchange (IKE).
How do I configure IPsec remote access VPN in Sophos XG firewall?
3:5113:14Sophos Firewall: Configure IPsec and SSL VPN Remote Access - YouTubeYouTubeStart of suggested clipEnd of suggested clipYou will need to port forward port udp 500 udp 4500 and the esp protocol with ip protocol number 50MoreYou will need to port forward port udp 500 udp 4500 and the esp protocol with ip protocol number 50 from the upstream router for authentication type select pre-shared key and enter the phrase.
How do I configure IPsec remote VPN in Sophos XG firewall?
Configure IPsec remote access VPN with Sophos Connect clientSpecify the settings on the Sophos Connect client page.Send the configuration file to users.Add a firewall rule.Send the Sophos Connect client to users. ... Users install the client, import the configuration file into the client, and establish the connection.
How do I enable IPsec VPN Sophos?
From Sophos Firewall, go to Rules and policies > Firewall rules and verify that the VPN rules allow ingress and egress traffic. Go to Current activities > IPsec connections to view the existing connections. Go to Reports > VPN and verify the IPsec usage. Click the connection name for details.
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
What is the difference between a site-to-site VPN and a remote access VPN?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
How does a remote access VPN differ from a host to host VPN?
**With a remote access VPN, a server on the edge of a network (called a VPN concentrator) is configured to accept VPN connections from individual hosts in a client to site configuration. Hosts that are allowed to connect using the VPN connection are granted access to resources on the VPN server or the private network.
What types of protocols are used in VPNs?
6 common VPN protocolsOpenVPN. OpenVPN is a very popular and highly secure protocol used by many VPN providers. ... IPSec/IKEv2. IKEv2 sets the foundation for a secure VPN connection by establishing an authenticated and encrypted connection. ... WireGuard. ... SSTP. ... L2TP/IPSec. ... PPTP.
Objectives
The Sophos Connect client allows you to enforce advanced security and flexibility settings, such as connecting the tunnel automatically. To configure and establish IPsec remote access connections over the Sophos Connect client, the article shows how to do the following:
Add a firewall rule
Configure a firewall rule to allow traffic from VPN to LAN and DMZ since you want to allow remote users to access these zones in this example.
Install and configure Sophos Connect Admin
If you want to configure advanced security settings, you can install the Sophos Connect Admin tool and specify the settings. This is an optional task.
Import the connection to remote endpoints
You must share the Sophos Connect client and the .tgb or the .scx configuration file with users. They must install the Sophos Connect client on their endpoints and import the configuration file into the client.
What is the difference between an outside and inside security appliance?
Typically, the outside interface is connected to the public Internet, while the inside interface is connected to a private network and is protected from public access.
What is dynamic crypto map?
The security appliance uses dynamic crypto maps to define a policy template where all the parameters do not have to be configured. These dynamic crypto maps let the security appliance receive connections from peers that have unknown IP addresses. Remote access clients fall in this category.
Description
This article will walk you through configuring, installing, and using the Global VPN Client (GVC) Software for Remote IPSec VPN connections.
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
