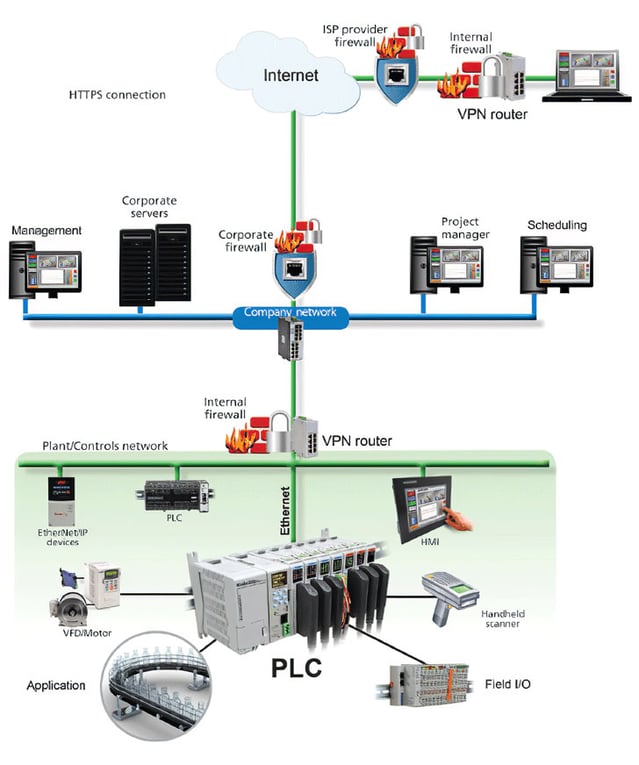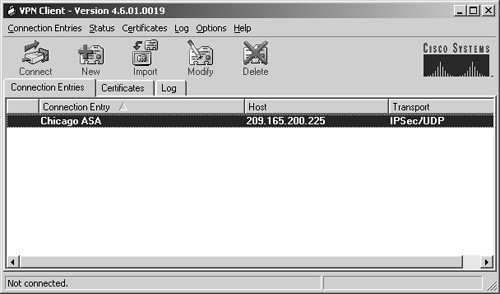
The IPsec Remote Access feature introduces server support for the Cisco VPN Client
Cisco Systems VPN Client
Cisco Systems VPN Client is a software application for connecting to virtual private networks based on Internet Key Exchange version 1. On July 29, 2011, Cisco announced the end of life of the product. No further product updates were released after July 30, 2012, and support ce…
Full Answer
What is remote access IPSec VPN?
Configuring Remote Access IPSec VPNs Remote access VPNs let single users connect to a cent ral site through a secure connection over a TCP/IP network such as the Internet. This chapter describes how to build a remote access VP N connection.
What does L2TP over IPsec stand for?
L2TP over IPSEC (Remote Access VPN) Hello Security Experts, My L2TP over IPSEC doesn't work, kindly help on my "phase2" of my L2TP over IPSEC...
How does the hardware-based VPN client work?
The hardware-based VPN client maintains the IPsec VPN (and GRE tunnel termination) to the concentrator, while allowing cleartext IP communications locally within the small home office or branch.
Does ravpn support NAT-T (IPsec NAT transparency)?
Although IPsec itself can accommodate environments where addresses are being translated, this topology eliminates the NAT processing of VPN traffic firewall and concentrator. Therefore, for RAVPN IPsec tunnels, the need for vendor-specific IPsec extensions such as NAT-T (IPsec NAT Transparency) is avoided.
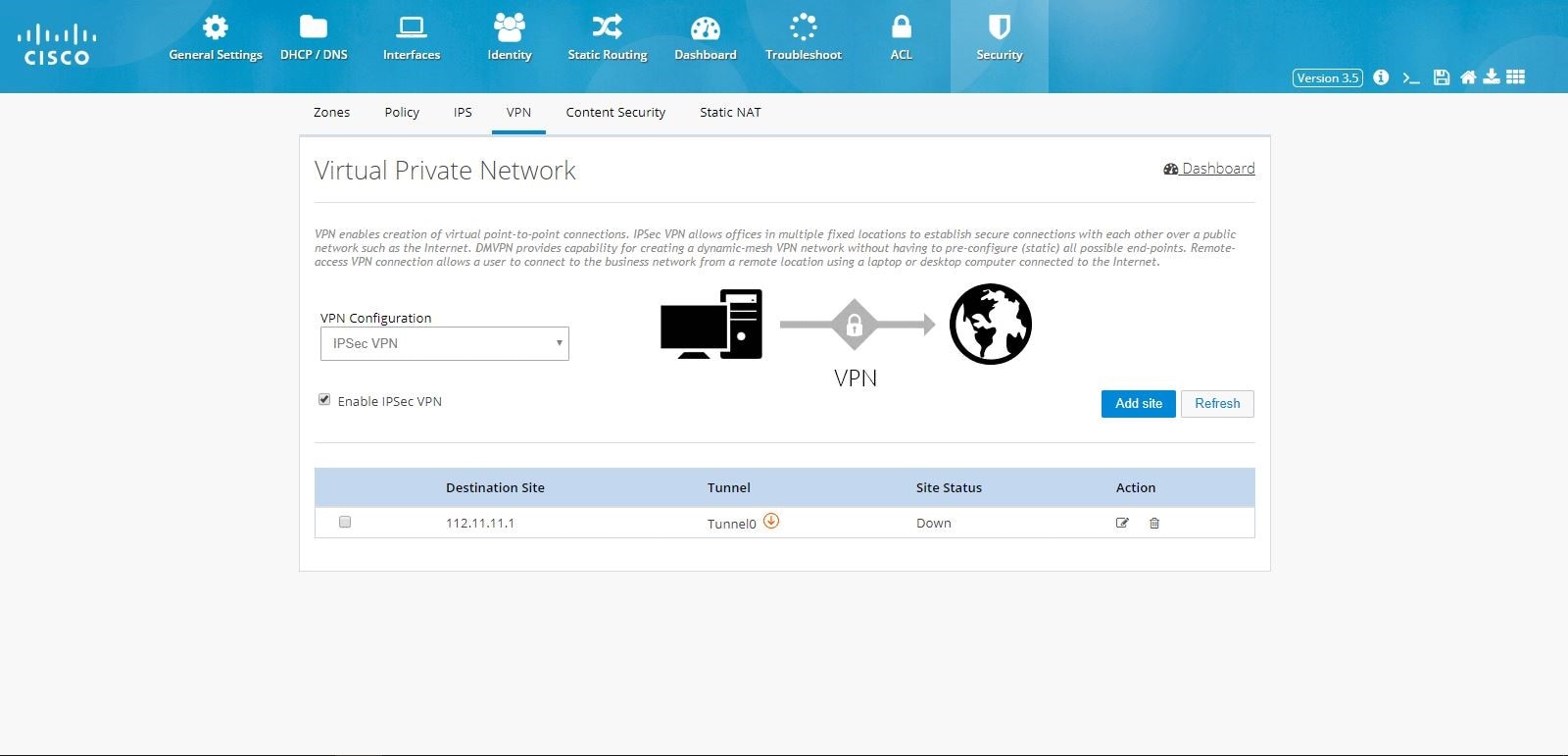
What is IPsec remote access VPN?
Internet Protocol Security (IPsec) is a suite of protocols that support cryptographically secure communication at the IP layer. With IPsec connections, you can provide secure access between two hosts, two sites, or remote users and a LAN. The firewall supports IPsec as defined in RFC 4301.
Does remote access VPN use IPsec?
While Remote access VPN supports SSL and IPsec technology.
Is Cisco VPN IPsec?
Site-to-Site IPSec VPN Tunnels are used to allow the secure transmission of data, voice and video between two sites (e.g offices or branches).
What is remote access VPN Cisco?
This allows remote users to connect to the ASA and access the remote network through an IPsec encrypted tunnel. The remote user requires the Cisco VPN client software on his/her computer, once the connection is established the user will receive a private IP address from the ASA and has access to the network.
What is the difference between VPN and IPsec?
SSL VPNs. The major difference between an IPsec VPN and an SSL VPN comes down to the network layers at which encryption and authentication are performed. IPsec operates at the network layer and can be used to encrypt data being sent between any systems that can be identified by IP addresses.
Is Cisco AnyConnect SSL or IPsec?
Anyconnect is the replacement for the old Cisco VPN client and supports SSL and IKEv2 IPsec. When it comes to SSL, the ASA offers two SSL VPN modes: Clientless WebVPN.
How does Cisco IPsec work?
Authenticates and protects the identities of the IPSec peers. Negotiates a matching IKE SA policy between peers to protect the IKE exchange. Performs an authenticated Diffie-Hellman exchange with the end result of having matching shared secret keys. Sets up a secure tunnel to negotiate IKE phase two parameters.
What type of VPN is Cisco AnyConnect?
Cisco AnyConnect VPNs utilize TLS to authenticate and configure routing, then DTLS to efficiently encrypt and transport the tunneled VPN traffic, and can fall back to TLS-based transport where firewalls block UDP-based traffic.
How do I use IPsec VPN?
Setting up an IPsec VPN connectionEstablish a VPN connection to the private network through SSL or IPsec.Access your server by using its private 10. x.x.x IP address through SSH or RDP.Connect to your server's IPMI IP address for additional server management or rescue needs.
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
How do I setup remote access to VPN?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
How does Cisco AnyConnect VPN Work?
Remote and mobile users use the Cisco AnyConnect Secure VPN client to establish VPN sessions with the adaptive security appliance. The adaptive security appliance sends web traffic to the Web Security appliance along with information identifying the user by IP address and user name.
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
How do I connect to IPsec?
Creating an IPsec VPN connectionNavigate to the Network and Sharing Center. ... Click Set up a new connection or network.Select Connect to a workplace, and then click Next.If prompted with "Do you want to use a connection that you already have?", select No, create a new connection, and then click Next.More items...•
What is IP security in network security?
What is IPsec? IPsec (Internet Protocol Security) is a suite of protocols that secure network communication across IP networks. It provides security services for IP network traffic such as encrypting sensitive data, authentication, protection against replay and data confidentiality.
What is the difference between an outside and inside security appliance?
Typically, the outside interface is connected to the public Internet, while the inside interface is connected to a private network and is protected from public access.
What is dynamic crypto map?
The security appliance uses dynamic crypto maps to define a policy template where all the parameters do not have to be configured. These dynamic crypto maps let the security appliance receive connections from peers that have unknown IP addresses. Remote access clients fall in this category.
Where is a VPN located?
Hardware-based VPN clients are typically found in small, remote locations that do not have dedicated connectivity to a central hub IPsec router. These devices are commonly found at home offices that have DSL- or cable-modem connectivity to the Internet. The hardware-based VPN client maintains the IPsec VPN (and GRE tunnel termination) to the concentrator, while allowing cleartext IP communications locally within the small home office or branch. Therefore, hardware-based VPN components add a networked element to the SOHO (small office, home office) or small branch environment that allows users to extend voice, video, and data securely from the campus.
Why use software based VPN?
Software-based VPN clients are therefore useful for tunneling data from centrally located campus resources to the end user. However, they do have limitations, and because of these limitations, the use of hardware-based VPN clients is merited in some situations. Specifically, software-based VPN clients terminate VPN connectivity locally on ...
Why use VPN concentrator in a DMZ?
Due to the nature of IPsec and firewalls, the placement of the VPN concentrator in a DMZ design is critical to the success of the greater RAVPN architecture. Figures 3-7 through 3-10 outline several DMZ topologies that we will use to explore common design issues which must be addressed in RAVPN design. Each of these designs pertains to an IPsec VPN concentrator deployment for effective termination of client IPsec VPN tunnels in an RAVPN environment.
Why use both software and hardware VPN?
In order to deliver both mobility and breadth of services to remote teleworkers, it is very common to see users deploy both software-based VPN clients and hardware-based VPN clients at the same time. Having the hardware-based VPN connectivity extends virtually all IP services available on the campus to relatively fixed remote locations. Software-based VPN communications allows users to extend communications in highly mobile scenarios. All of these services must be accommodated on the concentrator side of the VPN. For this reason, the variation in RAVPN topology is most commonly seen at the concentrator end of the design, which is what we will focus the remainder of this chapter's RAVPN discussion on.
What is a RAVPN client?
RAVPN clients typically come in two general flavors, hardware-based clients and software-based clients. Software-based VPN clients run locally on the user's remote workstation or laptop, and they are used to connect to a centrally managed VPN concentrator, typically located on the enterprise campus. The strength of software-based VPN clients is rooted in the mobility that they provide. When deployed on a user's laptop, a software-based VPN client can securely extend confidential communications from the campus to anywhere that a VPN client can access Layer 3 communications. Software-based VPN clients are therefore useful for tunneling data from centrally located campus resources to the end user. However, they do have limitations, and because of these limitations, the use of hardware-based VPN clients is merited in some situations. Specifically, software-based VPN clients terminate VPN connectivity locally on teleworkers' laptops and do not allow for the secure networking of other Layer 3 devices at the remote end of the VPN (such as a hardware-based IP Phone) over that VPN. Additionally, software-based clients will not support the termination of GRE locally, and therefore they will not typically support multicast data flows. Hardware-based clients, though inherently less mobile, address many of the functional limitations found in software-based IPsec VPN clients.
How to revise a privacy notice?
We may revise this Privacy Notice through an updated posting. We will identify the effective date of the revision in the posting. Often, updates are made to provide greater clarity or to comply with changes in regulatory requirements. If the updates involve material changes to the collection, protection, use or disclosure of Personal Information, Pearson will provide notice of the change through a conspicuous notice on this site or other appropriate way. Continued use of the site after the effective date of a posted revision evidences acceptance. Please contact us if you have questions or concerns about the Privacy Notice or any objection to any revisions.
How to remove myself from Cisco Press mailing list?
If you choose to remove yourself from our mailing list (s) simply visit the following page and uncheck any communication you no longer want to receive: www.ciscopress.com/u.aspx.