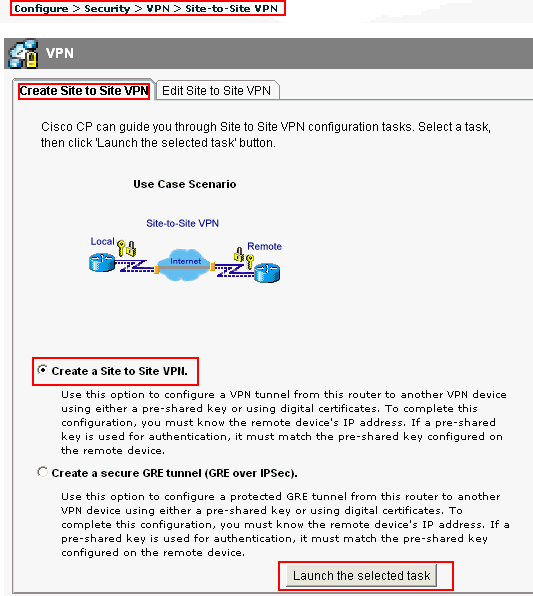
Configuring the IPsec VPN
- To create the VPN, go to VPN > IPsec Wizard and create a new tunnel using a pre-existing template.
- Name the VPN. ...
- Set the Incoming Interface to wan1 and Authentication Method to Pre-shared Key.
- Enter a pre-shared key. ...
- Set Local Interface to lan and set Local Address to the local network address.
- Enter a Client Address Range for VPN users. ...
- Go to VPN > Sophos Connect client and click Enable.
- Specify the general settings: Name. ...
- Specify the client information. ...
- Click Export connection. ...
- Optional To assign a static IP address to a user connecting through the Sophos Connect client, do as follows:
How to configure IPSec VPN on pfSense firewall?
PfSense firewall is configured using web interface so following window open after clicking on IPsec sub-menu under VPN. Check Enable IPsec option to create tunnel on PfSense. Click on plus button to add new policy of IPsec tunnel on local side (side-a in this case).
How to install and configure a VPN?
- Create an account on the VPN website. Go to the official website of the desired VPN provider ( e.g. ...
- Download the VPN software from the official website. ...
- Install the VPN software. ...
- Log in to the software with your account. ...
- Choose the desired VPN server (optional). ...
- Turn on the VPN. ...
How to configure IPsec?
To configure a route-based or policy-based IPsec VPN using autokey IKE:
- Configure interfaces, security zones, and address book information. (For route-based VPNs) Configure a secure tunnel st0.x interface. ...
- Configure Phase 1 of the IPsec VPN tunnel. ...
- Configure Phase 2 of the IPsec VPN tunnel. ...
- Configure a security policy to permit traffic from the source zone to the destination zone. ...
- Update your global VPN settings.
How to create your own IPSec VPN server in Linux?
Setting Up IPsec/L2TP VPN Server in Linux
- VPN_IPSEC_PSK – Your IPsec pre-shared key.
- VPN_USER – Your VPN username.
- VPN_PASSWORD – Your VPN password.
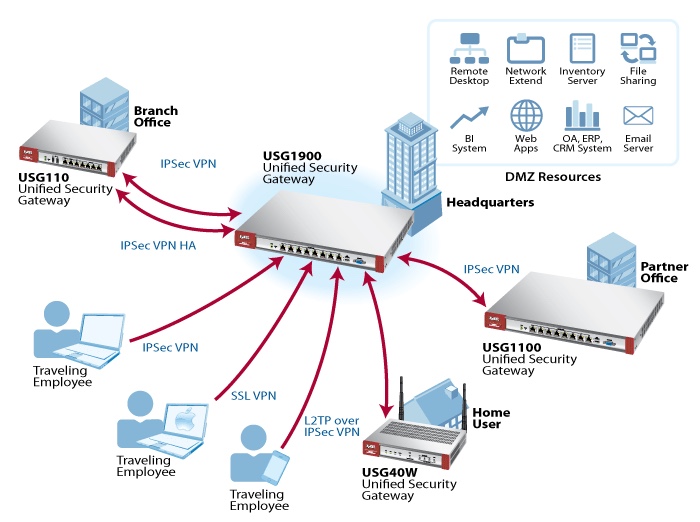
How is IPsec VPN configured?
To configure a route-based or policy-based IPsec VPN using autokey IKE:Configure interfaces, security zones, and address book information. ... Configure Phase 1 of the IPsec VPN tunnel. ... Configure Phase 2 of the IPsec VPN tunnel. ... Configure a security policy to permit traffic from the source zone to the destination zone.More items...
Does remote access VPN use IPsec?
While Remote access VPN supports SSL and IPsec technology.
How do I configure IPsec remote access VPN in Sophos XG?
Configure a wireless network.Create a hotspot with a custom sign-in page.Create a mesh network.Deploy a wireless network as a bridge to an access point LAN.Deploy a wireless network as a separate zone.Provide guest access using a hotspot voucher.Restart access points remotely using the CLI.
What is the difference between an IPsec and an SSL VPN?
Whereas an IPsec VPN enables connections between an authorized remote host and any system inside the enterprise perimeter, an SSL VPN can be configured to enable connections only between authorized remote hosts and specific services offered inside the enterprise perimeter.
What are the 3 protocols used in IPSec?
IPsec is a suite of protocols widely used to secure connections over the internet. The three main protocols comprising IPsec are: Authentication Header (AH), Encapsulating Security Payload (ESP), and Internet Key Exchange (IKE).
What is the purpose of IPSec VPN?
IPsec VPN is a protocol, consists of set of standards used to establish a VPN connection. A VPN provides a means by which remote computers communicate securely across a public WAN such as the Internet. A VPN connection can link two LANs (site-to-site VPN) or a remote dial-up user and a LAN.
How do I configure intrusion prevention system in Sophos XG?
Enabling the Sophos Intrusion Prevention System In Sophos XG, navigate to Protect | Firewall. Edit the #Default_Network_Policy (or relevant rule name) In the Advanced section under Intrusion Prevention select LAN TO WAN. Click Save.
How does SSL VPN Work?
An SSL tunnel VPN allows a web browser to securely access multiple network services that are not just web-based via a tunnel that is under SSL. These services could be proprietary networks or software built for corporate use only that cannot be accessed directly via the internet.
What is VPN in Sophos?
Sophos VPN Clients. Securely connects mobile users to your headquarters. Ì One-click VPN: Simply install individual VPN packages with a click of the mouse from the Sophos UTM UserPortal. Ì Automatic installation: The complete client installation is done within minutes—no configuration required by the user.
Does IPsec use TCP or UDP?
UDPIPsec uses UDP because this allows IPsec packets to get through firewalls. Decryption: At the other end of the communication, the packets are decrypted, and applications (e.g. a browser) can now use the delivered data.
What ports are needed for IPsec VPN?
Portability refers to the network environments from which the VPN client can connect. By default, IKEv2 uses IPSec, which requires UDP ports 500 and 4500, and ESP IP Protocol 50. You cannot disable IPSec. By default, L2TP uses IPSec, which requires UDP ports 500 and 4500, and ESP IP Protocol 50.
Can IPsec be hacked?
Hackers Could Decrypt IPsec Information Ordinarily, IPsec ensures cryptographically secured communications when people use insecure and publicly accessible portals, such as when browsing the internet.
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
What is IP security in network security?
What is IPsec? IPsec (Internet Protocol Security) is a suite of protocols that secure network communication across IP networks. It provides security services for IP network traffic such as encrypting sensitive data, authentication, protection against replay and data confidentiality.
What is the difference between an outside and inside security appliance?
Typically, the outside interface is connected to the public Internet, while the inside interface is connected to a private network and is protected from public access.
What is dynamic crypto map?
The security appliance uses dynamic crypto maps to define a policy template where all the parameters do not have to be configured. These dynamic crypto maps let the security appliance receive connections from peers that have unknown IP addresses. Remote access clients fall in this category.
Description
This article will walk you through configuring, installing, and using the Global VPN Client (GVC) Software for Remote IPSec VPN connections.
Resolution for SonicOS 7.X
This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware.
Resolution for SonicOS 6.5
This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware.
What to do before configuring IPsec?
Before configuring the IPsec portion, setup the L2TP server as described in L2TP Server Configuration and add users, firewall rules, etc, as covered there.
Is StrongSwan IPsec compatible with Windows?
As warned at the start of the chapter, the Windows client, among others, and the strongSwan IPsec daemon are not always compatible, leading to failure in many cases. We strongly recommend using another solution such as IKEv2 instead of L2TP/IPsec.
What are the two types of VPNs?
Two types of VPNs are supported—site-to-site and remote access. Site-to-site VPNs are used to connect branch offices to corporate offices, for example. Remote access VPNs are used by remote clients to log in to a corporate network. The example in this chapter illustrates the configuration of a remote access VPN that uses ...
What is Cisco Easy VPN?
The Cisco Easy VPN client feature eliminates much of the tedious configuration work by implementing the Cisco Unity Client protocol. This protocol allows most VPN parameters, such as internal IP addresses, internal subnet masks, DHCP server addresses, WINS server addresses, and split-tunneling flags, to be defined at a VPN server, such as a Cisco VPN 3000 series concentrator that is acting as an IPSec server.
What is a Cisco 870 router?
The Cisco 870 series routers support the creation of Virtual Private Networks (VPNs). Cisco routers and other broadband devices provide high-performance connections to the Internet, but many applications also require the security of VPN connections which perform a high level of authentication and which encrypt the data between two particular ...
Does Cisco 850 support VPN?
Note The material in this chapter does not apply to Cisco 850 series routers. Cisco 850 series routers do not support Cisco Easy VPN.
Can you negotiate with a peer in a security association?
Note With manually established security associations, there is no negotiation with the peer , and both sides must specify the same transform set.
Does Cisco Easy VPN support multiple destinations?
Note The Cisco Easy VPN client feature supports configuration of only one destination peer. If your application requires creation of multiple VPN tunnels, you must manually configure the IPSec VPN and Network Address Translation/Peer Address Translation (NAT/PAT) parameters on both the client and the server.

Description
- This article will walk you through configuring, installing, and using the Global VPN Client (GVC) Software for Remote IPSec VPN connections. CAUTION:Please make sure to read this article to completion and follow the included steps closely. Even one missed step will result in a failed configuration.
Resolution For SonicOS 7.x
- This release includes significant user interface changes and many new features that are different from the SonicOS 6.5 and earlier firmware. The below resolution is for customers using SonicOS 7.X firmware. Configure WAN Group VPN on the SonicWall 1. Login to the SonicWall management GUI. 2. ClickNetworkin the top navigation menu. 3. Navigate toIPSec VPN | Rules and Settings. 4…
Olution For SonicOS 6.5
- This release includes significant user interface changes and many new features that are different from the SonicOS 6.2 and earlier firmware. The below resolution is for customers using SonicOS 6.5 firmware. Configure WAN Group VPN on the SonicWall 1. Login to the SonicWall management GUI. 2. Click Managein the top navigation menu. 3. Navigate toVPN | Base Settings. 4. Ensure th…
Related Articles
Categories
- Firewalls> TZ Series> GVC/L2TP
- Firewalls> NSa Series> GVC/L2TP
- Firewalls> NSv Series> GVC/L2TP