Configure via ASDM
- Start ASDM
- Wizards -> VPN Wizards -> AnyConnect Wizard
- Configure a name for the tunnel group - RemoteAccessIKEv2
- Configure the connection protocols. ...
- Upload Anyconnect images to the ASA for each platform that need supporting (Windows, Mac, Linux)
- Configure the user database. ...
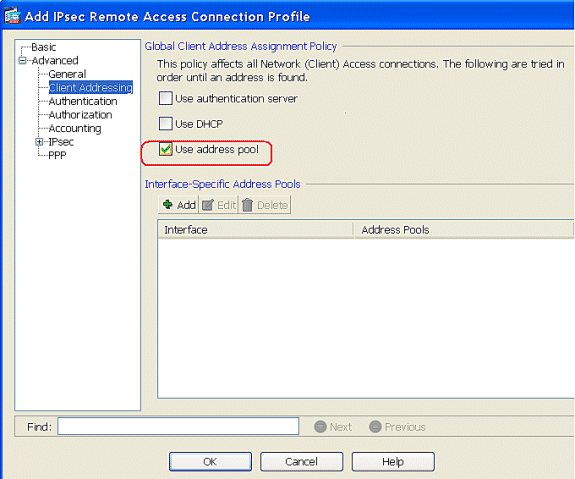
- Create a pool of addresses that will get assigned to the vpn clients.
Full Answer
Can the Cisco ASA be used as a router?
The ASA is NOT a router, though and while you can do things on the ASA that can make it act something like a router it is important to understand the differences between true routing and what the ASA actually does.
How to setup Cisco VPN?
Setting up Cisco AnyConnect VPN on a Chromebook or Android device
- Download the Cisco AnyConnect Chrome extension from here.
- Select Add to Chrome and allow access to anything it asks for.
- Select Launch App to configure it.
- Select Add New Connection and enter your VPN login details.
How do I connect to a Cisco VPN?
VPN access with Cisco AnyConnect VPN (Windows)
- Cisco AnyConnect VPN. ...
- Connect with the Cisco AnyConnect Client. ...
- Disconnect from the Cisco Anyconnect VPN client. ...
- Import Certificate for Multifactor Authentication. ...
- Downloading AnyConnect VPN Client for Windows / MAC / Linux. ...
Is IKEv2 support on Cisco ASA firewall?
It is on the roadmap, however to have support for IKEv2 across the board, including ASA. 02-26-2011 04:43 AM 02-26-2011 04:43 AM Please note that IKEv2 is supported on the Cisco ASA Firewalls starting from software v8.4, please see the following link:
How do I configure IPsec on ASA firewall?
To configure the IPSec VPN tunnel on Cisco ASA 55xx:Configure IKE. Establish a policy for the supported ISAKMP encryption, authentication Diffie-Hellman, lifetime, and key parameters. ... Create the Access Control List (ACL) ... Configure IPSec. ... Configure the Port Filter. ... Configure Network Address Translation (NAT)
How do I access my ASA remotely?
There are eight basic steps in setting up remote access for users with the Cisco ASA.Configure an Identity Certificate.Upload the SSL VPN Client Image to the ASA.Enable AnyConnect VPN Access.Create a Group Policy.Configure Access List Bypass.Create a Connection Profile and Tunnel Group.Configure NAT Exemption.More items...•
Does remote access VPN use IPsec?
While Remote access VPN supports SSL and IPsec technology.
What is IPsec remote access VPN?
Internet Protocol Security (IPsec) is a suite of protocols that support cryptographically secure communication at the IP layer. With IPsec connections, you can provide secure access between two hosts, two sites, or remote users and a LAN. The firewall supports IPsec as defined in RFC 4301.
How configure AnyConnect Cisco ASA?
5 Steps to Configure Cisco AnyConnect VPNConfigure AAA authentication. The first thing to configure is AAA authentication. ... Define VPN protocols. When users connect their VPN, they'll need an IP address for the VPN session. ... Configure tunnel groups. ... Set group policies. ... Apply the configuration. ... Authenticating logic flow.
What VPN types are supported by ASA?
For VPN Services, the ASA 5500 Series provides a complete remote-access VPN solution that supports numerous connectivity options, including Cisco VPN Client for IP Security (IPSec), Cisco Clientless SSL VPN, network-aware site-to-site VPN connectivity, and Cisco AnyConnect VPN client.
What are the 3 protocols used in IPsec?
IPsec is a suite of protocols widely used to secure connections over the internet. The three main protocols comprising IPsec are: Authentication Header (AH), Encapsulating Security Payload (ESP), and Internet Key Exchange (IKE).
What is the difference between VPN and IPsec?
SSL VPNs. The major difference between an IPsec VPN and an SSL VPN comes down to the network layers at which encryption and authentication are performed. IPsec operates at the network layer and can be used to encrypt data being sent between any systems that can be identified by IP addresses.
How do I connect to IPsec?
Creating an IPsec VPN connectionNavigate to the Network and Sharing Center. ... Click Set up a new connection or network.Select Connect to a workplace, and then click Next.If prompted with "Do you want to use a connection that you already have?", select No, create a new connection, and then click Next.More items...•
How IPSec works step by step?
Interesting traffic initiates the IPSec process—Traffic is deemed interesting when the IPSec security policy configured in the IPSec peers starts the IKE process....Step 1: Defining Interesting Traffic. ... Step 2: IKE Phase One. ... Step 3: IKE Phase Two. ... Step 4: IPSec Encrypted Tunnel. ... Step 5: Tunnel Termination.
Is IPSec VPN better than SSL VPN?
When it comes to corporate VPNs that provide access to a company network rather than the internet, the general consensus is that IPSec is preferable for site-to-site VPNs, and SSL is better for remote access.
What is the difference between site-to-site VPN and remote access VPN?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
What is IP security in network security?
What is IPsec? IPsec (Internet Protocol Security) is a suite of protocols that secure network communication across IP networks. It provides security services for IP network traffic such as encrypting sensitive data, authentication, protection against replay and data confidentiality.
Which crypto protocol allows the IPsec client and the ASA to establish a shared secret key?
Specify the Diffie-Hellman group for the IKE policy—the crypto protocol that allows the IPsec client and the ASA to establish a shared secret key.
What happens if a Cisco VPN client has a different preshared key size?
If a Cisco VPN Client with a different preshared key size tries to connect, the client logs an error message indicating it failed to authenticate the peer.
What is the default LAN to LAN tunnel group?
There are two default tunnel groups in the ASA system: DefaultRAGroup, which is the default remote-access tunnel group, and DefaultL2Lgroup, which is the default LAN-to-LAN tunnel group. You can change these groups, but do not delete them. The ASA uses these groups to configure default tunnel parameters for remote access and LAN-to-LAN tunnel groups when there is no specific tunnel group identified during tunnel negotiation.
What files can Cisco AnyConnect have?
Virtual File System creation for each context can have Cisco Anyconnect files like Image and profile.
How many interfaces does an ASA have?
An ASA has at least two interfaces, referred to here as outside and inside. Typically, the outside interface is connected to the public Internet, while the inside interface is connected to a private network and is protected from public access.
What is the first phase of ISAKMP?
Phase 1 creates the first tunnel to protect later ISAKMP negotiation messages. Phase 2 creates the tunnel that protects data travelling across the secure connection.
Do you need a mask for a VPN?
The address mask is optional. However, You must supply the mask value when the IP addresses assigned to VPN clients belong to a non-standard network and the data could be routed incorrectly if you use the default mask. A typical example is when the IP local pool contains 10.10.10.0/255.255.255.0 addresses, since this is a Class A network by default. This could cause routing issues when the VPN client needs to access different subnets within the 10 network over different interfaces.
What is VPN debug?
Run a VPN debug that is filtered for the peer IP on the VPN tunnel you're troubleshooting. The VPN debug will show each VPN phase as they establish and will give verbose errors about what goes wrong when the VPN tunnel fails to connect.
Can you run a packet tracer from ASA?
You can run a packet-tracer from the ASA CLI to simulate VPN traffic and see where traffic may be failing. In the following command, "inside" is our local interface, 192.168.1.100 is the local IP we're testing traffic from, 12345 is the source port (it can be anything you choose), and 192.168.2.100 is the remote IP we're trying to reach. This packet-tracer will simulate ICMP traffic.
How many interfaces does an ASA have?
The ASA has two interfaces: inside and outside. Imagine the outside interface is connected to the Internet where a remote user wants to connect to the ASA. On the inside we find R1, I will only use this router so the remote user has something to connect to on the inside network. Let’s look at the configuration!
What is VPN_POLICY?
The group policy is called VPN_POLICY and it’s an internal group policy which means it is created locally on the ASA. You can also specify an external group policy on a RADIUS server. I added some attributes, for example a DNS server and an idle timeout (15 minutes). Split tunneling is optional but I added it to show you how to use it, it refers to the access-list we created earlier.
Does Cisco VPN require ASA?
The remote user requires the Cisco VP N client software on his/her computer, once the connection is established the user will receive a private IP address from the ASA and has access to the network .
Can remote VPN users access certain networks?
If you want to configure an access-list so the remote VPN users can only reach certain networks , IP addresses or ports then you can apply this under the group policy.
Can you use VPN on remote network?
If you don’t want this then you can enable split tunneling. With split tunneling enabled, we will use the VPN only for access to the remote network. Here’s how to enable it:
How many interfaces does an ASA have?
An ASA has at least two interfaces, referred to here as outside and inside. Typically, the outside interface is connected to the public Internet, while the inside interface is connected to a private network and is protected from public access.
What is the first phase of ISAKMP?
Phase 1 creates the first tunnel to protect later ISAKMP negotiation messages. Phase 2 creates the tunnel that protects data travelling across the secure connection.
What is the default LAN to LAN tunnel group?
There are two default tunnel groups in the ASA system: DefaultRAGroup, which is the default remote-access tunnel group, and DefaultL2Lgroup, which is the default LAN-to-LAN tunnel group. You can change them but not delete them. The ASA uses these groups to configure default tunnel parameters for remote access and LAN-to-LAN tunnel groups when there is no specific tunnel group identified during tunnel negotiation.
Is IPv6 supported for SSL?
Assigning an IPv6 address to the client is supported for the SSL protocol. This feature is not supported for the IKEv2/IPsec protocol.
Do you need a mask for a VPN?
The address mask is optional. However, You must supply the mask value when the IP addresses assigned to VPN clients belong to a non-standard network and the data could be routed incorrectly if you use the default mask. A typical example is when the IP local pool contains 10.10.10.0/255.255.255.0 addresses, since this is a Class A network by default. This could cause routing issues when the VPN client needs to access different subnets within the 10 network over different interfaces.
Can ASA assign IPv4 and IPv6?
You can configure the ASA to assign an IPv4 address, an IPv6 address, or both an IPv4 and an IPv6 address to an AnyConnect client by creating internal pools of addresses on the ASA or by assigning a dedicated address to a local user on the ASA.
What version of ASA is AnyConnect?
The ASA supports the AnyConnect client firewall feature with ASA version 8.3 (1) or later, and ASDM version 6.3 (1) or later. This section describes how to configure the client firewall to allow access to local printers, and how to configure the client profile to use the firewall when the VPN connection fails.
What is DPD in ASA?
Dead Peer Detection (DPD) ensures that the ASA (gateway) or the client can quickly detect a condition where the peer is not responding, and the connection has failed. To enable dead peer detection (DPD) and set the frequency with which either the AnyConnect client or the ASA gateway performs DPD, do the following:
What is ACL AnyConnect_Client_Local_Print?
The ACL AnyConnect_Client_Local_Print is provided with ASDM to make it easy to configure the client firewall. When you choose that ACL for Public Network Rule in the Client Firewall pane of a group policy, that list contains the following ACEs:
Does ASA support LDAP?
The other parameters are valid for AAA servers that support such notification; that is, RADIUS, RADIUS with an NT server, and LDAP servers. The ASA ignores this command if RADIUS or LDAP authentication has not been configured.
Does AnyConnect SSL VPN work with IPsec?
This feature applies to connectivity between the ASA gateway and the AnyConnect SSL VPN Client only. It does not work with IPsec since DPD is based on the standards implementation that does not allow padding, and CLientless SSL VPN is not supported.