What is remote access IPSec VPN?
Configuring Remote Access IPSec VPNs Remote access VPNs let single users connect to a cent ral site through a secure connection over a TCP/IP network such as the Internet. This chapter describes how to build a remote access VP N connection.
How do I enable IPsec on my Network?
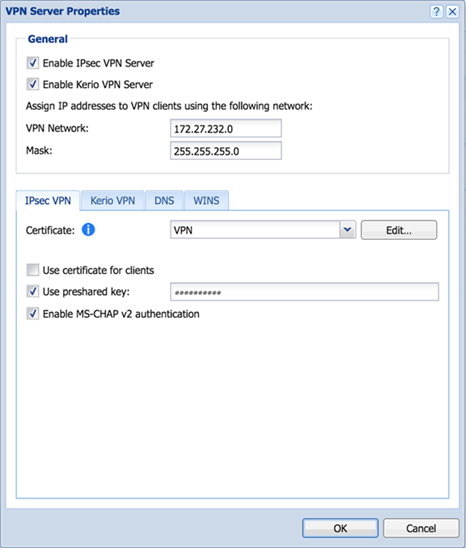
Go to Remote access VPN > IPsec and click Enable. Specify the general settings. Select a WAN port. Select a locally-singed certificate. Alternatively, select a certificate you've uploaded to Certificates > Certificates. The firewall automatically selects the local ID for digital certificates.
How do I configure the source and destination zones for IPsec?
Specify the source and destination zones as follows and click Apply: Under advanced settings for IPsec (remote access), if you select Use as default gateway, the Sophos Connect client sends all traffic, including traffic to the internet, from the remote user through the tunnel.
What is IPsec protocol used for?
IPsec is a group of networking protocols used for setting up secure encrypted connections, such as VPNs, across publicly shared networks.
How do users connect to an IPsec VPN?
What is a VPN? What is an IPsec VPN?
What is IPsec?
What is the difference between IPsec tunnel mode and IPsec transport mode?
What port does IPsec use?
How does IPsec impact MSS and MTU?
How does IPsec work?
See 4 more
About this website
Does remote access VPN use IPsec?
While Remote access VPN supports SSL and IPsec technology.
What is IPsec remote access VPN?
Internet Protocol Security (IPsec) is a suite of protocols that support cryptographically secure communication at the IP layer. With IPsec connections, you can provide secure access between two hosts, two sites, or remote users and a LAN. The firewall supports IPsec as defined in RFC 4301.
Which is better remote access VPN or site site VPN?
Performance wise, Site-to-Site VPN is better, as it allows multiple users/VLANs traffic to flow through each VPN tunnel.
How do I configure IPsec remote access VPN in Sophos XG?
Configure a wireless network.Create a hotspot with a custom sign-in page.Create a mesh network.Deploy a wireless network as a bridge to an access point LAN.Deploy a wireless network as a separate zone.Provide guest access using a hotspot voucher.Restart access points remotely using the CLI.
What are the 3 protocols used in IPSec?
IPsec is a suite of protocols widely used to secure connections over the internet. The three main protocols comprising IPsec are: Authentication Header (AH), Encapsulating Security Payload (ESP), and Internet Key Exchange (IKE).
Is IPSec faster than SSL?
In short: Both are reasonably fast, but IKEv2/IPSec negotiates connections the fastest. Most IPSec-based VPN protocols take longer to negotiate a connection than SSL-based protocols, but this isn't the case with IKEv2/IPSec.
What is the difference between IPSec and site-to-site VPN?
Site-to-Site VPN provides a site-to-site IPSec connection between your on-premises network and your virtual cloud network (VCN). The IPSec protocol suite encrypts IP traffic before the packets are transferred from the source to the destination and decrypts the traffic when it arrives.
What are important characteristics of remote access VPNs?
What is an important characteristic of remote-access VPNs?The VPN configuration is identical between the remote devices.Internal hosts have no knowledge of the VPN.Information required to establish the VPN must remain static.The VPN connection is initiated by the remote user.
How does remote access VPN Work?
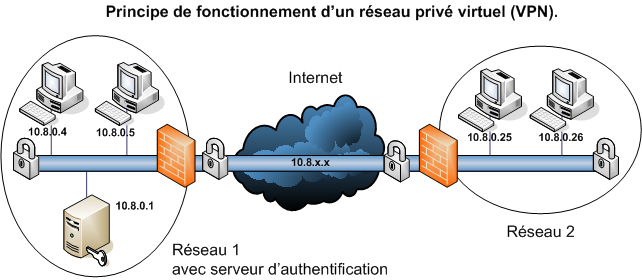
The remote access VPN does this by creating a tunnel between an organization's network and a remote user that is “virtually private,” even though the user may be in a public location. This is because the traffic is encrypted, which makes it unintelligible to any eavesdropper.
What is the difference between an IPsec and an SSL VPN?
Whereas an IPsec VPN enables connections between an authorized remote host and any system inside the enterprise perimeter, an SSL VPN can be configured to enable connections only between authorized remote hosts and specific services offered inside the enterprise perimeter.
What type of authentication can be used for IPsec site to site VPN Sophos?
Create an IPsec VPN connection Set the Authentication Type to RSA key. The local RSA key is loaded automatically. You need to copy and paste the Remote RSA key from Sophos Firewall 2. Note: The RSA key is generated with 2048 bit by default.
What is security heartbeat?
Security Heartbeat is a feature that allows endpoints and firewalls to communicate their health status with each other. Find the details on how it works, what different health statuses there are, and what they mean. Network. Authentication. System services.
What is the difference between VPN and IPSec?
SSL VPNs. The major difference between an IPsec VPN and an SSL VPN comes down to the network layers at which encryption and authentication are performed. IPsec operates at the network layer and can be used to encrypt data being sent between any systems that can be identified by IP addresses.
Which is better IPSec or OpenVPN?
IPSec is generally regarded as faster than OpenVPN. The main reason for this is actually a pro for OpenVPN in another area, and that is how it is implemented. IPSec is implemented in the IP stack of the kernel, whereas OpenVPN is implemented in the userspace.
What is the difference between SSL and IPSec?
Internet protocol security (IPsec) is a set of protocols that provide security for Internet Protocol. SSL is a secure protocol developed for sending information securely over the Internet. It Work in Internet Layer of the OSI model. It Work in Between the transport layer and application layer of the OSI model.
How IPSec works step by step?
Interesting traffic initiates the IPSec process—Traffic is deemed interesting when the IPSec security policy configured in the IPSec peers starts the IKE process....Step 1: Defining Interesting Traffic. ... Step 2: IKE Phase One. ... Step 3: IKE Phase Two. ... Step 4: IPSec Encrypted Tunnel. ... Step 5: Tunnel Termination.
How IPSec Works > VPNs and VPN Technologies | Cisco Press
Step 1: Interesting traffic initiates the IPSec process—Traffic is deemed interesting when the IPSec security policy configured in the IPSec peers starts the IKE process.: Step 2: IKE phase one—IKE authenticates IPSec peers and negotiates IKE SAs during this phase, setting up a secure channel for negotiating IPSec SAs in phase two.
IPSec VPN: What It Is and How It Works - Privacy Affairs
What Is IPSec? IPSec suite of VPN protocols includes Authentication Header (AH), Encapsulated Security Payload (ESP), Internet Security Association and Key Management Protocol (ISAKMP), and IP Payload Compression (IPComp).. Authentication Header (AH): AH offers data origin authentication of IP packets (datagrams), guarantees connectionless integrity, and gives protection against replay attacks ...
How do users connect to an IPsec VPN?
Users can access an IPsec VPN by logging into a VPN application, or "client." This typically requires the user to have installed the application on their device.
What is a VPN? What is an IPsec VPN?
A virtual private network (VPN) is an encrypted connection between two or more computers. VPN connections take place over public networks, but the data exchanged over the VPN is still private because it is encrypted.
What is IPsec?
IPsec is a group of protocols that are used together to set up encrypted connections between devices. It helps keep data sent over public networks secure. IPsec is often used to set up VPNs, and it works by encrypting IP packets, along with authenticating the source where the packets come from.
What is the difference between IPsec tunnel mode and IPsec transport mode?
In IPsec tunnel mode, the original IP header containing the final destination of the packet is encrypted, in addition to the packet payload. To tell intermediary routers where to forward the packets, IPsec adds a new IP header. At each end of the tunnel, the routers decrypt the IP headers to deliver the packets to their destinations.
What port does IPsec use?
IPsec usually uses port 500.
How does IPsec impact MSS and MTU?
Packets can only reach a certain size (measured in bytes) before computers, routers, and switches cannot handle them. MSS measures the size of each packet's payload, while MTU measures the entire packet, including headers. Packets that exceed a network's MTU may be fragmented, meaning broken up into smaller packets and then reassembled. Packets that exceed the MSS are simply dropped.
How does IPsec work?
To tell intermediary routers where to forward the packets, IPsec adds a new IP header. At each end of the tunnel, the routers decrypt the IP headers to deliver the packets to their destinations. In transport mode, the payload of each packet is encrypted, but the original IP header is not.
What is dynamic crypto map?
The security appliance uses dynamic crypto maps to define a policy template where all the parameters do not have to be configured. These dynamic crypto maps let the security appliance receive connections from peers that have unknown IP addresses. Remote access clients fall in this category.
What is the difference between an outside and inside security appliance?
Typically, the outside interface is connected to the public Internet, while the inside interface is connected to a private network and is protected from public access.
How do users connect to an IPsec VPN?
Users can access an IPsec VPN by logging into a VPN application, or "client." This typically requires the user to have installed the application on their device.
What is a VPN? What is an IPsec VPN?
A virtual private network (VPN) is an encrypted connection between two or more computers. VPN connections take place over public networks, but the data exchanged over the VPN is still private because it is encrypted.
What is IPsec?
IPsec is a group of protocols that are used together to set up encrypted connections between devices. It helps keep data sent over public networks secure. IPsec is often used to set up VPNs, and it works by encrypting IP packets, along with authenticating the source where the packets come from.
What is the difference between IPsec tunnel mode and IPsec transport mode?
In IPsec tunnel mode, the original IP header containing the final destination of the packet is encrypted, in addition to the packet payload. To tell intermediary routers where to forward the packets, IPsec adds a new IP header. At each end of the tunnel, the routers decrypt the IP headers to deliver the packets to their destinations.
What port does IPsec use?
IPsec usually uses port 500.
How does IPsec impact MSS and MTU?
Packets can only reach a certain size (measured in bytes) before computers, routers, and switches cannot handle them. MSS measures the size of each packet's payload, while MTU measures the entire packet, including headers. Packets that exceed a network's MTU may be fragmented, meaning broken up into smaller packets and then reassembled. Packets that exceed the MSS are simply dropped.
How does IPsec work?
To tell intermediary routers where to forward the packets, IPsec adds a new IP header. At each end of the tunnel, the routers decrypt the IP headers to deliver the packets to their destinations. In transport mode, the payload of each packet is encrypted, but the original IP header is not.
