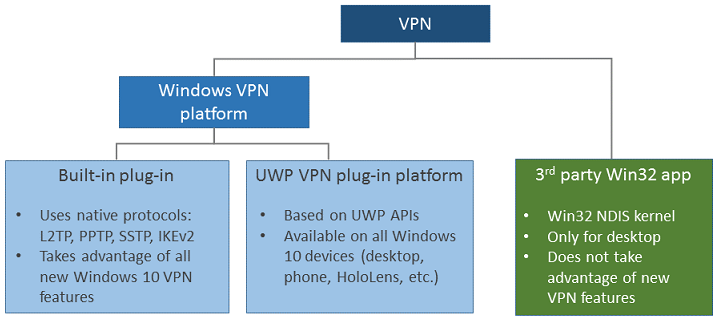
IPsec remote access VPN
Virtual private network
A virtual private network extends a private network across a public network, and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. Applications running on a computing device, e.g. …
Internet Key Exchange
In computing, Internet Key Exchange (IKE or IKEv2) is the protocol used to set up a security association (SA) in the IPsec protocol suite. IKE builds upon the Oakley protocol and ISAKMP.
- Navigate to System > Cert Manager.
- Click Add to create a new certificate authority.
- Set the options as follows: Descriptive Name. Mobile IPsec CA. Method. Create an internal Certificate Authority. ...
- Leave the rest of the fields at their default values or adjust to suit local preferences.
- Click Save.
What is the difference between IKEv2 and IPsec profile?
NOTE: you can also create a crypto map which is the legacy way, while IPSEC profile is the newer way. Note: you can use IKEv2 for Remote Access VPN as well but it will need to work with remote authentication server (RADIUS) when you configure on Cisco ASA and it will not allow you to create users locally.
Can I use IKEv2 with Cisco ASA remote access VPN?
Note: you can use IKEv2 for Remote Access VPN as well but it will need to work with remote authentication server (RADIUS) when you configure on Cisco ASA and it will not allow you to create users locally. but you might be able to do a workaround if you edit the group policy after you finish the configuration like below:
How do I configure IKEv2 through the user interface?
You cannot configure IKEv2 through the user interface. You can use IKEv2 as a virtual private network (VPN) tunneling protocol that supports automatic VPN reconnection. IKEv2 allows the security association to remain unchanged despite changes in the underlying connection. Note: This topic includes sample Windows PowerShell cmdlets.
What VPN license do I need to use IPSEC remote access VPN?
IPsec remote access VPN using IKEv2 requires an AnyConnect Plus or Apex license, available separately. IPsec remote access VPN using IKEv1 and IPsec site-to-site VPN using IKEv1 or IKEv2 uses the Other VPN license that comes with the base license.
Does IPsec use IKEv2?
In fact, IPSec's authentication suite already uses IKEv2 within its own collection of protocols. IPSec is a popular system for a reason: it's secure and reliable, and its operations are invisible to third-parties. Likewise, IKEv2 is a great basis for stability, rapid data-flow, and connection hopping.
Does remote access VPN use IPsec?
While Remote access VPN supports SSL and IPsec technology.
What is IPsec remote access VPN?
Internet Protocol Security (IPsec) is a suite of protocols that support cryptographically secure communication at the IP layer. With IPsec connections, you can provide secure access between two hosts, two sites, or remote users and a LAN. The firewall supports IPsec as defined in RFC 4301.
What VPN uses IKEv2?
IKEv2 stands for Internet Key Exchange Version 2. IKEv2 is one of the newest protocols and has significant strengths, particularly its speed. It's well-suited for mobile devices across all platforms. ExpressVPN recommends you to use Lightway as your VPN protocol, with OpenVPN and IKEv2 also solid choices.
What are the 3 protocols used in IPSec?
IPsec is a suite of protocols widely used to secure connections over the internet. The three main protocols comprising IPsec are: Authentication Header (AH), Encapsulating Security Payload (ESP), and Internet Key Exchange (IKE).
What is the main advantage of IKE v2 over IKE v1?
IKEv2 provides the following benefits over IKEv1: In IKEv2 Tunnel endpoints exchange fewer messages to establish a tunnel. IKEv2 uses four messages; IKEv1 uses either six messages (in the main mode) or three messages (in aggressive mode).
What is the difference between VPN and IPSec?
SSL VPNs. The major difference between an IPsec VPN and an SSL VPN comes down to the network layers at which encryption and authentication are performed. IPsec operates at the network layer and can be used to encrypt data being sent between any systems that can be identified by IP addresses.
Which port does IPSec VPN use?
IPSec VPN. IPSec VPN is a layer 3 protocol that communicates over IP protocol 50, Encapsulating Security Payload (ESP). It might also require UDP port 500 for Internet Key Exchange (IKE) to manage encryption keys, and UDP port 4500 for IPSec NAT-Traversal (NAT-T).
How IPSec works step by step?
Interesting traffic initiates the IPSec process—Traffic is deemed interesting when the IPSec security policy configured in the IPSec peers starts the IKE process....Step 1: Defining Interesting Traffic. ... Step 2: IKE Phase One. ... Step 3: IKE Phase Two. ... Step 4: IPSec Encrypted Tunnel. ... Step 5: Tunnel Termination.
Is IKEv2 and IPSec the same?
IKEv2 (Internet key exchange version 2) is part of the IPSec protocol suite. Standardized in RFC 7296. IPSec has become the defacto standard protocol for secure Internet communications, providing confidentiality, authentication and integrity. Open-source VPN protocol developed by OpenVPN technologies.
Which is better IKEv2 or IPSec?
IPSec is considered secure and reliable, while IKEv2 is extremely fast and stable – IKEV2 offers quick re-connections when switching networks or during sudden drops. Thus, a combination of IKEv2/IPsec forms one of the best VPN protocols that exhibits the advantages of the two.
How does IKEv2 VPN Work?
How Does IKEv2 Work? Using a Diffie–Hellman key exchange algorithm, the protocol sets up a secure communication channel between your device and the VPN server. IKEv2 then uses that secure communication channel to establish what is called a security association.
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
How do I connect to IPsec?
Creating an IPsec VPN connectionNavigate to the Network and Sharing Center. ... Click Set up a new connection or network.Select Connect to a workplace, and then click Next.If prompted with "Do you want to use a connection that you already have?", select No, create a new connection, and then click Next.More items...•
What is IP security in network security?
What is IPsec? IPsec (Internet Protocol Security) is a suite of protocols that secure network communication across IP networks. It provides security services for IP network traffic such as encrypting sensitive data, authentication, protection against replay and data confidentiality.
Which crypto protocol allows the IPsec client and the ASA to establish a shared secret key?
Specify the Diffie-Hellman group for the IKE policy—the crypto protocol that allows the IPsec client and the ASA to establish a shared secret key.
What happens if a Cisco VPN client has a different preshared key size?
If a Cisco VPN Client with a different preshared key size tries to connect, the client logs an error message indicating it failed to authenticate the peer.
What is the default LAN to LAN tunnel group?
There are two default tunnel groups in the ASA system: DefaultRAGroup, which is the default remote-access tunnel group, and DefaultL2Lgroup, which is the default LAN-to-LAN tunnel group. You can change these groups, but do not delete them. The ASA uses these groups to configure default tunnel parameters for remote access and LAN-to-LAN tunnel groups when there is no specific tunnel group identified during tunnel negotiation.
What is the first phase of ISAKMP?
Phase 1 creates the first tunnel to protect later ISAKMP negotiation messages. Phase 2 creates the tunnel that protects data travelling across the secure connection.
What is priority in IKE?
Priority uniquely identifies the Internet Key Exchange (IKE) policy and assigns a priority to the policy. Use an integer from 1 to 65,534, with 1 being the highest priority and 65,534 the lowest.
Do you need a mask for a VPN?
The address mask is optional. However, You must supply the mask value when the IP addresses assigned to VPN clients belong to a non-standard network and the data could be routed incorrectly if you use the default mask. A typical example is when the IP local pool contains 10.10.10.0/255.255.255.0 addresses, since this is a Class A network by default. This could cause routing issues when the VPN client needs to access different subnets within the 10 network over different interfaces.
What is the best way to secure end to end IPsec?
Securing End-to-End IPsec connections by using IKEv2
Where is the connection security rule in Windows Defender?
In the left pane of the Windows Defender Firewall with Advanced Security snap-in, click Connection Security Rules, and then verify that there is an enabled connection security rule.
Can IKEv2 be configured through the user interface?
Uses the Windows PowerShell interface exclusively for configuration. You cannot configure IKEv2 through the user interface.
What does IKE stand for in IPSEC?
IKE stands for Internet Key exchange, it is the version 2 of the IKE and it has been created to provide a better solution than IKEv1 in setting up security association (SA) in IPSEC.
Which is newer, IPSEC or crypto?
NOTE: you can also create a crypto map which is the legacy way, while IPSEC profile is the newer way.
Setup Certificates
Similar to OpenVPN, a set of certificates is required for the server and clients.
Create Client Pre-Shared Keys
With the IPsec tunnel itself ready, now the users need pre-shared keys.
Windows Client Setup
The server setup is complete, the following tasks configure the client.
Ubuntu-based Client Setup
Before starting, install network-manager-strongswan and strongswan-plugin-eap-mschapv2 using apt-get or a similar mechanism.
Security
IKEv2 uses multi-layer security due to requiring a certificate and username/password instead of just a pre-shared key.
Portability
IKEv2 uses IPsec so relies on UDP ports 500, 4500 and ESP IP Protocol 50.
Performance
IKEv2 is a very lightweight protocol and as a result, is typically the least impacting on performance with little overhead also.
Prerequisites
Devices Joined to A Domain
- The following Windows PowerShell script establishes a connection security rule that uses IKEv2 for communication between two computers (CLIENT1 and SERVER1) that are joined to the corp.contoso.com domain as shown in Figure 1. Figure 1The Contoso corporate network This script does the following: 1. Creates a security group called IPsec client and serversand adds CL…
Devices Not Joined to A Domain
- Use a Windows PowerShell script similar to the following to create a local IPsec policy on the devices that you want to include in the secure connection. Windows PowerShell commands Type each cmdlet on a single line, even though they may appear to wrap across several lines because of formatting constraints. Make sure that you install the required certificates on the participatin…
Troubleshooting
- Follow these procedures to verify and troubleshoot your IKEv2 IPsec connections: Use the Windows Defender Firewall with Advanced Security snap-in to verify that a connection security rule is enabled. 1. Open the Windows Defender Firewall with Advanced Security console. 2. In the left pane of the Windows Defender Firewall with Advanced Security snap...