Configure IPsec (remote access)
- Go to VPN > IPsec (remote access) and click Enable.
- Specify the general settings.
- Specify the client information.
- Specify the advanced settings you want and click Apply.
- Click Export connection at the bottom of the page.
- Send the .scx file to users.
- Optionally, download the client and send it to users.
Full Answer
What are remote access VPNs?
Remote access VPNs allow users to connect to a central site through a secure connection over a TCP/IP network. The Internet Security Association and Key Management Protocol, also called IKE, is the negotiation protocol that lets the IPsec client on the remote PC and the ASA agree on how to build an IPsec Security Association.
How do I configure IPsec remote access?
†Set the connection type to IPSec remote access. †Configure the address assignment method, in the following example, address pool. †Configure an authentication method, in the following example, preshared key.
What is the difference between SSL and IPsec?
You can use an SSL VPN to securely connect via a remote access tunnel, a layer 7 connection to a specific application. SSL is typically much more versatile than IPsec, but with that versatility comes additional risk.
What is IPsec and how does it work?
IPsec has been around for decades and is the tried-and-true solution. As time goes on, IPsec adapts by adding supported encryption and hash algorithms, like DES, which gave way to 3DES, which gave way to AES and so on. Every IPsec VPN connection goes through two phases.
What is IPsec remote access VPN?
Internet Protocol Security (IPsec) is a suite of protocols that support cryptographically secure communication at the IP layer. With IPsec connections, you can provide secure access between two hosts, two sites, or remote users and a LAN. The firewall supports IPsec as defined in RFC 4301.
Can IPsec be used for remote access?
IPSec remote access is used to connect remote-access clients, such as a PC or small office, home office (SOHO) device (a small-end router or firewall appliance) to a corporate network.
Does VPN allow remote access?
A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive.
How do I configure IPsec remote access VPN in Sophos XG?
Configure a wireless network.Create a hotspot with a custom sign-in page.Create a mesh network.Deploy a wireless network as a bridge to an access point LAN.Deploy a wireless network as a separate zone.Provide guest access using a hotspot voucher.Restart access points remotely using the CLI.
Which is better IPsec or OpenVPN?
IPSec is generally regarded as faster than OpenVPN. The main reason for this is actually a pro for OpenVPN in another area, and that is how it is implemented. IPSec is implemented in the IP stack of the kernel, whereas OpenVPN is implemented in the userspace.
What is the difference between IPsec and VPN?
The major difference between an IPsec VPN and an SSL VPN comes down to the network layers at which encryption and authentication are performed. IPsec operates at the network layer and can be used to encrypt data being sent between any systems that can be identified by IP addresses.
Which VPN is best for remote access?
NordVPN is one of the best remote access VPNs on the market with support for enterprises and consumers alike. It has over 5,000 servers in 60 countries.
How do I setup a VPN remote access?
Configure Remote Access as a VPN ServerOn the VPN server, in Server Manager, select the Notifications flag.In the Tasks menu, select Open the Getting Started Wizard. ... Select Deploy VPN only. ... Right-click the VPN server, then select Configure and Enable Routing and Remote Access.More items...•
How do I remotely connect to a VPN?
Simply go to Start -> Accessories -> Remote Desktop Connection and enter the IP address of the other Windows computer. desktop software. From HOME Mac to OFFICE Windows: Connect with VPN, then use Remote Desktop Client. From HOME Windows to OFFICE Mac: Connect with VPN, then use VNC client.
What is IPsec remote access VPN Sophos XG?
Internet Protocol Security (IPsec) is a suite of protocols that support cryptographically secure communication at the IP layer. With IPsec connections, you can provide secure access between two hosts, two sites, or remote users and a LAN. The firewall supports IPsec as defined in RFC 4301.
How does SSL VPN Work?
An SSL tunnel VPN allows a web browser to securely access multiple network services that are not just web-based via a tunnel that is under SSL. These services could be proprietary networks or software built for corporate use only that cannot be accessed directly via the internet.
What is red device?
The RED or Remote Ethernet Device is a small box you deploy to your remote sites, and it establishes a VPN back to your central Sophos UTM so that anything connected to the RED is seen as part of your network.
How do users connect to an IPsec VPN?
How do users connect to an IPsec VPN? Users can access an IPsec VPN by logging into a VPN application, or "client." This typically requires the user to have installed the application on their device. VPN logins are usually password-based.
How do I connect to IPsec?
Creating an IPsec VPN connectionNavigate to the Network and Sharing Center. ... Click Set up a new connection or network.Select Connect to a workplace, and then click Next.If prompted with "Do you want to use a connection that you already have?", select No, create a new connection, and then click Next.More items...•
How do I create an IPsec tunnel?
Preshared key authenticationIn the administration interface, go to Interfaces.Click Add > VPN Tunnel.Type a name of the new tunnel.Set the tunnel as active and type the hostname of the remote endpoint. ... Select Type: IPsec.Select Preshared key and type the key.More items...
What is IP security in network security?
What is IPsec? IPsec (Internet Protocol Security) is a suite of protocols that secure network communication across IP networks. It provides security services for IP network traffic such as encrypting sensitive data, authentication, protection against replay and data confidentiality.
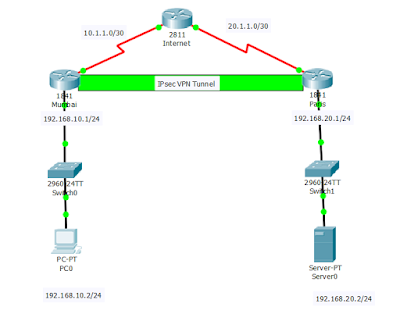
IPSec VPN Remote Access
Enable your employees at home, on the go, or in a remote/branch office to seamlessly and securely connect to your corporate network (MPLS or SD-WAN) via public Internet with IPSec VPN Remote Access from AireSpring. Even without an MPLS or SD-WAN circuit, enable employees to access existing AireSpring networks over the Internet while simultaneously safeguarding your data and improving cost efficiencies. AireSpring will work with you to customize an AireSpring IPSec VPN Remote Access solution that meets your security and connectivity needs..
Features
Remotely connect securely and seamlessly to your AireSpring private network using the public Internet, without an MPLS or SD-WAN circuit.
What is the difference between an outside and inside security appliance?
Typically, the outside interface is connected to the public Internet, while the inside interface is connected to a private network and is protected from public access.
What is dynamic crypto map?
The security appliance uses dynamic crypto maps to define a policy template where all the parameters do not have to be configured. These dynamic crypto maps let the security appliance receive connections from peers that have unknown IP addresses. Remote access clients fall in this category.
How many phases does IPsec VPN go through?
Every IPsec VPN connection goes through two phases. During phase one of the connection, the VPN peer devices negotiate how the are going to encrypt and pass traffic. If you must use the Internet Key Exchange (IKEv1) protocol here, there are a couple of important things to remember.
What is SSL VPN?
SSL VPN. The new hotness in terms of VPN is secure socket layer (SSL). You can use an SSL VPN to securely connect via a remote access tunnel, a layer 7 connection to a specific application. SSL is typically much more versatile than IPsec, but with that versatility comes additional risk.
What are the two major protocols that are used in VPN?
In today’s world there are two heavyweights in the realm of maximum security, support and functionality: IPsec and SSL.
How has VPN revolutionized the world?
The VPN has revolutionized the way we work. For over 20 years it’s allowed everyone from executives on down a company’s organizational chart to work anywhere, from home to the airport to the resort. (The debate of work/life balance versus always available connectivity will not be solved by me and not here.) This ability to connect almost anywhere in the world has not only revolutionized how we work, but it has saved many on-call engineers late-night trips to the datacenter.
Can you use Active Directory for VPN?
Most environments will leverage Active Directory as the authentication source for the VPN using either RADIUS or LDAP. Both protocol options are relatively easy to set up and it’s easy to forget to use the secure options for both. Once connected, a VPN client has access to the business network.