How to properly secure remote access?
- Windows or Mac login when connecting remotely
- Request permission to connect to the user’s computer
- Automatically blank the remote screen when connected
- Automatically lock remote computer when disconnected
- Lock the remote computer’s keyboard and mouse while in session
- Lock the streamer settings using Splashtop admin credentials
How secure is enabling remote access?
- iOS/Android: Swap album and artist titles in CarPlay/Android Auto.
- iOS/Android: Rare crash if your library had ~200,000 items.
- Desktop: Reduce hover play background size to allow clicking on poster.
- iOS: Crash for high CPU in some cases if server disks were offline.
- CarPlay/Android Auto: Show all albums when album types are enabled.
Is it safe to allow remote access to my machine?
Remote access is a useful tool to allow a trusted individual access to your computer for support or other purposes. The key is that you must know and trust the individual, just as you would if you handed the computer to them. NEVER allow remote access to someone whom you don’t know or who contacts you.
What is remote access and how can I use it?
Windows 10 Fall Creator Update (1709) or later
- On the device you want to connect to, select Start and then click the Settings icon on the left.
- Select the System group followed by the Remote Desktop item.
- Use the slider to enable Remote Desktop.
- It is also recommended to keep the PC awake and discoverable to facilitate connections. ...
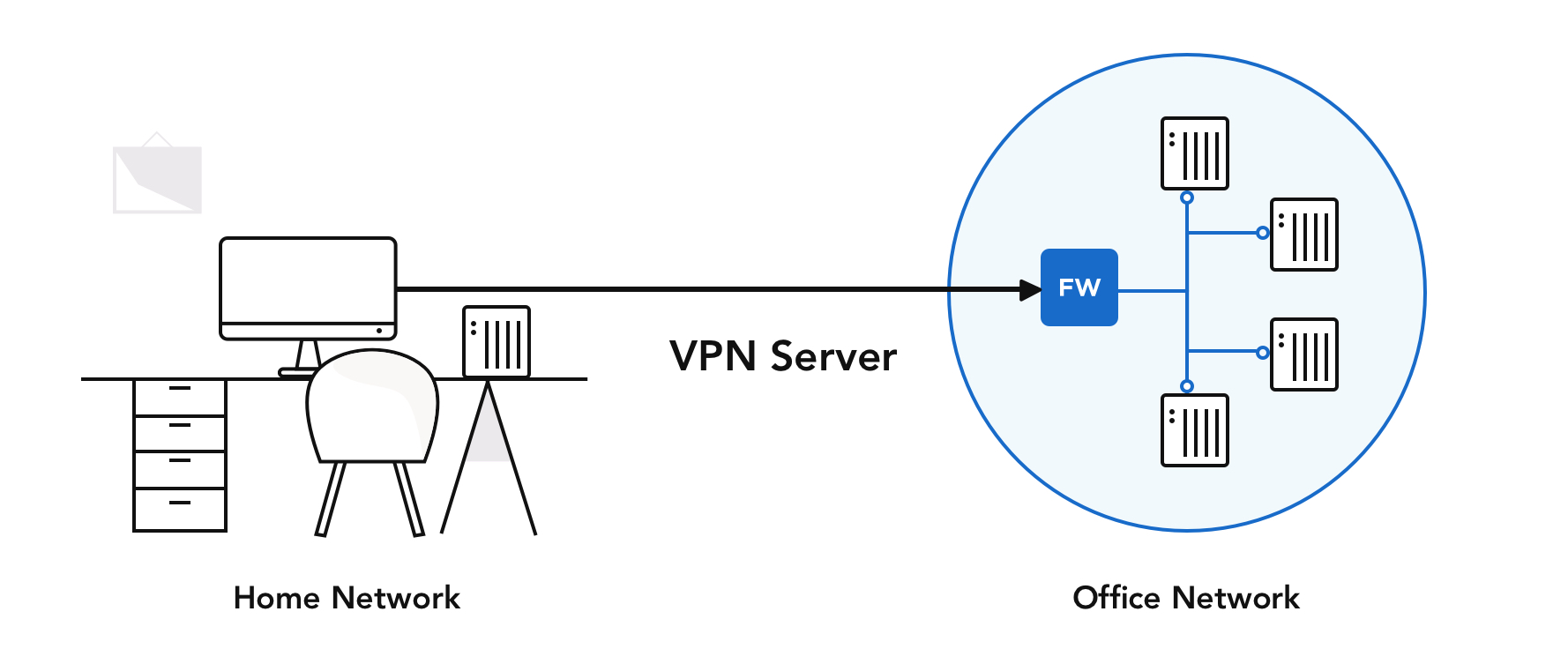
Is connecting to a remote desktop safe?
RDP itself is not a secure setup and therefore requires additional security measures to keep workstations and servers protected. Without proper security protocols in place, organizations face several potential risks, including the increased risk of cyberattacks.
Is Microsoft remote desktop encrypted?
Microsoft RDP includes the following features and capabilities: Encryption. RDP uses RSA Security's RC4 cipher, a stream cipher designed to efficiently encrypt small amounts of data. RC4 is designed for secure communications over networks.
Can ransomware spread through RDP?
Once the user's offsite computer connects to the infected onsite server, the attacker gains access to the offsite computer by traversing the RDP connection. With access granted, the ransomware attack commences.
How do I stop remote access to my computer?
How to Disable Remote Access in Windows 10Type “remote settings” into the Cortana search box. Select “Allow remote access to your computer”. ... Check “Don't Allow Remote Connections” to this Computer. You've now disabled remote access to your computer.
How do I know if my RDP is encrypted?
You can check the encryption level on target server where you got connected, open TS Manager and check the status of RDP connection, there you see encryption level.
Is RDP end to end encrypted?
The short answer to, “Is RDP encrypted?” is yes – but that comes with a big caveat. By default, Impero and other remote desktop service providers also create remote connections that are encrypted at the highest possible level.
What level of encryption does RDP use?
RDP uses RSA's RD4 encryption to cipher all data transmitted to and from the local and remote desktop. The system administrators can choose whether to encrypt data using a 56-bit key or a 128-bit key, the 128-bit being the more secure route.
Why RDP is not secure?
The problem is that the same password is often used for RDP remote logins as well. Companies do not typically manage these passwords to ensure their strength, and they often leave these remote connections open to brute force or credential stuffing attacks. Unrestricted port access.
Is Microsoft Support a scam?
Shouldn't be an issue if you are only using it internally, but there is a common scam going around where people claim to be from Microsoft Support and they said that they detected a very harmful virus on your computer and they need remote access to your computer to clean it before its too late.
Is remote assistance okay?
Remote assistance is okay when you are already on the same network, you would have some additional security via VPN, RADIUS, wifi, etc. The benefit of a GoToAssist is that you can connect both to attended, or unattended sessions without having direct IP access to those machines.
Does RDP support Linux?
RDP/RA is also not available on all Windows OSes (ie., Win7 home, starter, etc.). Doesn't support MAC nor Linux out-of the box... need to procure other 3rd party solution. & only older versions of RDP are supported on iOS and Android devices.
Why is remote access important?
However, remote access is also necessary for IT technicians to provide timely support, conduct routine updates, and reduce the cost of location visits. Furthermore, while it may seem like a security breach to grant remote control over your systems, it’s actually no less secure than allowing someone to log-on in person.
Why is control so uncomfortable?
The primary reason control feels so uncomfortable for users is because we can’t see the person on the other end. Even if we can watch what they do on our computers and talk to them on the phone while they do it, watching a cursor move around the screen and open files without any action on our end feels almost ghostly.
Can you access someone who contacts you first?
Never allow access to someone who contacts you first . There are, unfortunately, many remote access scams. They usually follow a similar formula: the scammer calls a user, claiming to be from a large IT-related corporation, such as Microsoft.
What does it mean when someone gives you remote access to your computer?
When you grant somebody remote access to your computer, in effect, you are physically handing over your machine to them - the person will be able to do almost anything with your system. This fact is quite concerning, especially if there’s a hacker on the other side.
What is remote desktop?
A remote desktop is a computer which you connect to from your local computer, so the device you’re using.
How do scammers gain access to your computer?
Scammers usually use social engineering tactics to gain access to your computer. They will pretend to be from a large telecommunication company, convincing you your computer needs an urgent fix via a remote connection. When you grant access, they can install malware or ransomware to breach your security or demand payment for the repair.
Is remote access a double edged sword?
Remote access is a double-edged sword: it can either save you time and effort or potentially expose your computer to infection from malware. Let’s dive deeper into the topic to understand the possible risks and learn the best ways to protect yourself.
Is it safe to use a remote desktop?
The remote connection itself is quite safe: Windows and macOS have inbuilt remote desktop clients allowing remote connection between computers. Security concerns are more a matter of who accesses your computer and what they are doing there.
What is remote access?
Remote access is a useful tool to allow a trusted individual access to your computer for support or other purposes. The key is that you must know and trust the individual, just as you would if you handed the computer to them. NEVER allow remote access to someone whom you don’t know or who contacts you.
What is a tech support scam?
Recent years have seen rise to something called the “tech support scam”. Using lies and threats, scammers try to get you to give them remote access to your machine. Once they have it, they install malware — often including ransomware — or they leave back doors allowing them continued access when you’re not around.
Can a technician visit your home?
They can do whatever they want. It’s like having a technician visit your home or taking your machine into a shop for repair. You’re giving that person control. Presumably, that means resolving the issues bringing you to them in the first place, and nothing else malicious along the way. It’s all about trust.
Can you watch a remote technician?
Watching isn’t always enough. Most remote access tools let you watch the technician’s activities. That’s often instructive. Some include voice, so you can talk to the technician and they can explain what they’re doing or answer questions along the way. The problem is this can lead to a false sense of security.
Do remote access companies care about their reputation?
Presumably, they care about their reputation and your power to impact it. Companies that provide remote access support are often distant, faceless entities on the internet. It’s not uncommon for them to be in a completely different country.
How to secure RDP?
Ananth: There are some built-in, no-cost defenses that can secure RDP. These include: 1 Patching: Keep servers especially up to date. 2 Complex passwords: Also use two-factor authentication, and implement lockout policies. 3 Default port: Change the default port used by RDP from 3389 to something else via the Registry. 4 Windows firewall: Use the built-in Windows firewall to restrict RDP sessions by IP address. 5 Network Level Authentication (NLA): Enable NLA, which is non-default on older versions. 6 Limit RDP access: Limit RDP access to a specific user group. Don't allow any domain admin to access RDP. 7 Tunnel RDP access: Tunnel access via IPSec or Secure Shell (SSH).
What is the RDP vulnerability?
Most notably, 2019 gave rise to a vulnerability known as BlueKeep that could allow cybercriminals to remotely take over a connected PC that's not properly patched.
What are some built-in, no-cost defenses that can secure RDP?
Ananth: There are some built-in, no-cost defenses that can secure RDP. These include: Patching: Keep servers especially up to date. Complex passwords: Also use two-factor authentication, and implement lockout policies. Default port: Change the default port used by RDP from 3389 to something else via the Registry.
How many systems are exposed to the internet via RDP?
Web crawlers like shodan.io make it easy for attackers to quickly identify vulnerable public-facing machines. Worldwide, more than two million systems are exposed to the internet via RDP, of which more than 500,000 are in the US.
Do all RDP instances need a VPN?
Gamblin: Without many exceptions, all RDP instances should require multiple levels of access and authentication controls. This would include the use of a VPN to access an RDP instance and requiring a second factor (like Duo) for authentication.
Can RDP be placed on the internet?
Some major organizations place RDP directly on the internet, but most (hopefully) are doing this unknowingly. Checking on this is pretty simple; just fire up your favorite internet-wide scanner and look at all the RDP instances directly exposed. Ananth: There are some built-in, no-cost defenses that can secure RDP.
How to protect your computer when using remote access?
Here are some steps you can take to help protect your computer and data while relying on remote access. Maintain strong passwords.
Why is remote access important?
Remote access software is helpful when you’re in a meeting at another office with your laptop — or telecommuting — and need an important file that’s on your office computer. Remote computer access can help you assist someone in your personal life who might be far away.
Why is it important to limit the number of users who can log in?
Remote computer access can help businesses, individuals, and families in a variety of ways. But it’s important to make remote access secure .
Is there a third party remote access program?
For instance, there are Windows-only and Mac-only programs if your computers and devices all use the same operating system.
Can hackers use RDP?
Hackers could use remote desktop protocol (RDP) to remotely access Windows computers in particular. Remote desktop servers connect directly to the Internet when you forward ports on your router. Hackers and malware may be able to attack a weakness in those routers.