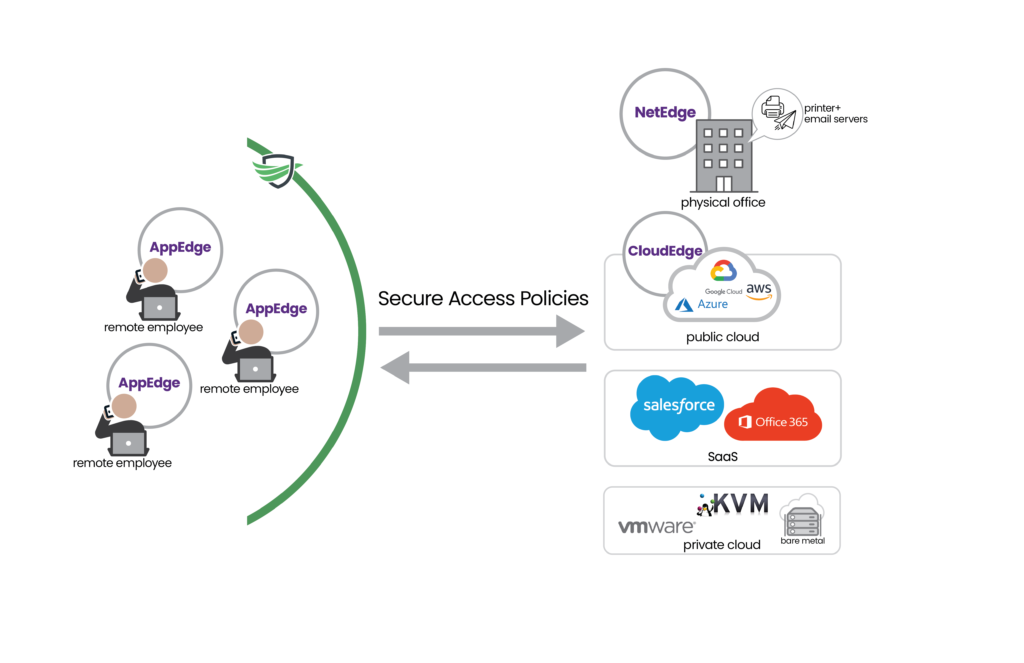
Full Answer
Is your remote access secure?
If businesses can establish secure remote access, remote work can be just as secure as if employees are working onsite. In the following sections, we’ll elaborate more about remote access security concerns and how you can address them. Before we define what secure remote access is, we need to define remote access first.
What is remote access and network protection?
Remote access methods describe how a client connects to the local area network (LAN) remotely. In order for the client to access the LAN, they have to be authenticated through a remote access server. Network protection is a topic that is directly associated with remote access.
Why are some remote access protocols not secure?
Some remote access protocols are not inherently secure. For instance, some of them don’t support data-in-motion encryption. Cybercriminals are out to exploit the vulnerabilities of remote access environments in order to steal personal data, financial data, trade secrets, and other valuable information.
What is secure remote access (SRA)?
What is Secure Remote Access? - Definition | VMware Glossary Secure remote access is a combination of security processes or solutions that are designed to prevent unauthorized access to an organization’s digital assets Skip to Main Content Global Search
Is remote access secure?
Remote access solutions could leave you vulnerable. If you don't have proper security solutions in place, remote connections could act as a gateway for cybercriminals to access your devices and data. Hackers could use remote desktop protocol (RDP) to remotely access Windows computers in particular.
Why is remote access not secure?
In many cases, servers with RDP publicly accessible to the internet have failed to enable multi-factor authentication (MFA). This means that an attacker who compromises a user account by exposing a weak or reused password through a brute force attack can easily gain access to a user's workstation via RDP.
How do you protect remote connections?
Limit access using firewalls On the Windows search bar, type in Windows Firewall. Click on Windows Firewall with Advanced Security. Click on Inbound Rules. Find a rule labeled RDP.
Which method of remote access is the most secure?
Implement a Secure Connection for Remote Network AccessWired Connection: A wired connection is the most secure method for remote network access.Home Wi-Fi: The second most secure network connection is using a secured home Wi-Fi connection.More items...•
What happens if you give someone remote access to your computer?
This can be even worse than just conning you out of money, as undetected malware can allow hackers to steal your identity, including your passwords and financial information, over and over again, even if you get new passwords and account numbers.
How secure is remote PC?
Yes, RemotePC by IDrive is considered secure. Communications between remote and local computers are protected with industry-standard TLS version 1.2 and AES-256 encryption. RemotePC also utilizes personal keys as a secondary password to access each computer and two-step verification with a time-based OTP authenticator.
What are potential risks associated with remote access?
Five Remote Access Security Risks And How To Protect Against ThemWeak remote access policies. ... A deluge of new devices to protect. ... Lack of visibility into remote user activity. ... Users mixing home and business passwords. ... Opportunistic phishing attempts.
Is Remote Desktop secure without VPN?
Remote Desktop Protocol (RDP) Integrated in BeyondTrust Establishing remote desktop connections to computers on remote networks usually requires VPN tunneling, port-forwarding, and firewall configurations that compromise security - such as opening the default listening port, TCP 3389.
How do I secure a remote to my home network?
How to change the name of your default home networkUse a strong password for your router. ... Strengthen your Wi-Fri encryption. ... Use a VPN for additional network security. ... Keep your router firmware up to date. ... Use a firewall to protect the devices on your network. ... Consider changing your router's IP address.More items...
Which protocol for remote access is more secure and why?
POINT-TO-POINT TUNNELING PROTOCOL (PPTP) It's used to establish virtual connections across the internet via PPP and TCP/IP, enabling two networks to use the internet as their WAN link while retaining the security benefits of a private network. PPTP is a great option because it's simple and secure.
What are the types of remote access?
Remote Access Control MethodsDirect (Physical) Line. The first direct remote access control that can be implemented is a direct line from a computer to the company's LAN. ... Virtual Private Network. Another method which is more common is establishing a VPN. ... Deploying Microsoft RDS.
What types of attacks are remote access servers vulnerable to?
Other attacks which hackers can facilitate through remote access include email phishing, third-party vendor compromise, insider threats, social engineering, and the use of vulnerable applications to compromise systems. Hackers use Common remote access tools to penetrate third-party access to merchant information ...
Why is the remote access domain the most risk prone of all in a typical IT infrastructure?
Why is the Remote Access Domain the most risk prone of all within a typical IT infrastructure? Because it allows users to connect to intranet from remote locations.
Why Is Secure Remote Access Important?
Secure remote access is important for three reasons: to safeguard and protect intellectual property; to increase employee productivity, and to enhance an organization’s competitive advantage. Organizations can confidently deliver on their current goals and innovate to achieve new ones when employees can work securely from everywhere.
What is remote desktop access?
Remote desktop access is an older and still popular method for accessing resources, typically on a corporate LAN. In this case, a user will connect to a physical or virtual computing instance located on the LAN. Popular examples include Remote Desktop Protocol (RDP) and Virtual Network Computing (VNC).
Why do people use VPNs?
Organizations, governments, and businesses of all sizes use VPNs for secure remote access to data center resources or corporate local area networks (LAN). Personal VPNs have also become widely popular as they keep users’ locations private, ...
Is Google Chrome secure?
Most web browsers, like Google Chrome, provide some level of security for a secure web browsing experience. However, a successful secure remote access strategy provides organizations more control of the web browsing experience, eliminating reliance solely on web browser vendors for a secure web browsing experience.
Why is it important to enforce access based on user identity?
Recommendation: It’s critical that companies enforce access based on user identity, allowing specific groups access to only what they need to get their jobs done, and expanding access from there on an as-needed basis.
What should security teams do if on-premises network and email security mechanisms are no longer available?
Recommendation: If some on-premises network and email security mechanisms are no longer available, security teams should double down on educating users to identify phishing attempts and to choose strong, unique passwords, encouraging the use of a password manager. They should also implement client certificates and multi-factor authentication in order to prevent attackers from gaining access through unsecured devices.
What are the risks of using a VPN?
Here are five top security risks that teams must deal with, as well as technology and user education best practices to keep users and data safe: 1. Weak remote access policies. Once attackers get access to a virtual private network (VPN), they can often penetrate the rest of the network like a hot knife through butter.
What is XDR in security?
Recommendation: Rather than invest in point solutions, consider security platforms that maximize integration between systems, limiting the amount of switching between tools and providing visibility into all data – including remote user activity. Extended detection and response (XDR) not only protects endpoints, but also applies analytics across all your data to find threats like unusual access or lateral movement, and simplifies investigations by stitching together data and identifying the root cause.
What is Windows Defender Remote Credential Guard?
Introduced in Windows 10, version 1607, Windows Defender Remote Credential Guard helps you protect your credentials over a Remote Desktop connection by redirecting Kerberos requests back to the device that's requesting the connection. It also provides single sign-on experiences for Remote Desktop sessions.
What version of Windows can a remote computer run?
Version support. The remote computer can run any Windows operating system. Both the client and the remote computer must be running at least Windows 10, version 1607, or Windows Server 2016. The remote computer must be running at least patched Windows 7 or patched Windows Server 2008 R2.
What version of Windows Defender is used for remote credentials?
To use Windows Defender Remote Credential Guard, the Remote Desktop client and remote host must meet the following requirements: The Remote Desktop client device: Must be running at least Windows 10, version 1703 to be able to supply credentials, which is sent to the remote device.
Why does Windows Defender not allow NTLM fallback?
Windows Defender Remote Credential Guard does not allow NTLM fallback because this would expose credentials to risk. The Remote Desktop remote host: Must be running at least Windows 10, version 1607 or Windows Server 2016.
Why is Windows Defender not exposed?
By using Windows Defender Remote Credential Guard to connect during Remote Desktop sessions, if the target device is compromised, your credentials are not exposed because both credential and credential derivatives are never passed over the network to the target device.
What version of Windows 10 is needed for remote host?
The remote host must be running at least Windows 10 version 1607, or Windows Server 2016.
How to ensure that Group Policy object is applied?
From a command prompt, run gpupdate.exe /force to ensure that the Group Policy object is applied.
Types of Tunneling and Encryption
Tunneling involves using protocols to encapsulate or encrypt data packets so that will pass through the Internet in a secure fashion. Think of encapsulation and tunneling like peas in a pod. The peas are the data packets (unencrypted) and the pod encapsulates or encrypts the peas so they cannot be seen.
Remote Access
Here is a high level example (Figure 1) of how a remote host can connect to an internal corporate network which can be referred to when reviewing the types of remote access solutions: Remote Access Service (RAS), Point-to-Point over Ethernet (PPPoE), Remote Desktop Protocol (RDP), Independent Computing Architecture (ICA), and Secure Shell (SSH).
Network Intrusion & Protection
An Intrusion Detection System (IDS) and Intrusion Prevention System (IPS) are network security appliances that can be host-based, network-based or a combination of both.
Network Security Traps
A honeypot is a computer host that has been set up to attract hackers to learn what tactics they are using to infiltrate a network. It monitors their movements and gives a network administrator insight to where future attacks may come from.
What is protected harbor?
Protected Harbor provides a Daas secure access point for users and simplifies desktop and app management processes and procedures.
Can employees access their desktops?
All employees and contractors can access their applications, desktops, and data from anywhere, keeping them productive, no matter where they work.
Does Protected Harbor have remote access?
Protected Harbor Includes Remote Access at No Additional Cost. Given the COVID-19 virus, many companies have been forced to work from home, with little or no warning. Because of Protected Harbor’s modern architecture, we are able to move employees to work from home within hours.
