
From the admin console, click Security then select Identity-Aware Proxy. If you haven’t used Cloud IAP before, you’ll need to configure the oAuth screen: Configure the consent screen to only allow internal users in your domain, and click Save. Next, you need to define users who are allowed to use Cloud IAP to connect remotely.
- Use strong passwords. ...
- Use Two-factor authentication. ...
- Update your software. ...
- Restrict access using firewalls. ...
- Enable Network Level Authentication. ...
- Limit users who can log in using Remote Desktop. ...
- Set an account lockout policy.
How do I configure remote access?
Configure the Remote Access server settings. Configure the infrastructure servers that are used in the organization. Configure the application servers to require authentication and encryption. View the Remote Access configuration summary, and modify the GPOs if desired.
How do I configure the deployment type on the remote access server?
To configure the deployment type On the Remote Access server, open the Remote Access Management console: On the Start screen, type, type Remote Access Management Console, and then press ENTER. If the User Account Control dialog box appears, confirm that the action it displays is what you want, and then click Yes.
How do I install the remote access role on DirectAccess servers?
To install the Remote Access role on DirectAccess servers. On the DirectAccess server, in the Server Manager console, in the Dashboard, click Add roles and features. Click Next three times to get to the server role selection screen. On the Select Server Roles dialog, select Remote Access, and then click Next.
What is remote access in SP_configure?
The remote access option only applies to servers that are added by using sp_addserver, and is included for backward compatibility. Execute permissions on sp_configure with no parameters or with only the first parameter are granted to all users by default.
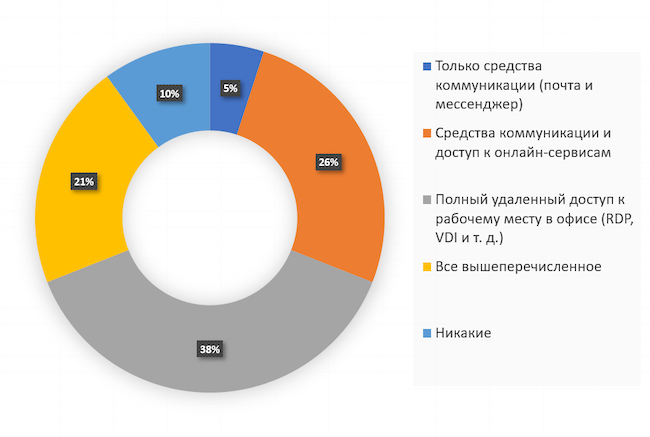
What are the security requirements for remote access?
7 Best Practices For Securing Remote Access for EmployeesDevelop a Cybersecurity Policy For Remote Workers. ... Choose a Remote Access Software. ... Use Encryption. ... Implement a Password Management Software. ... Apply Two-factor Authentication. ... Employ the Principle of Least Privilege. ... Create Employee Cybersecurity Training.
What is remote access in cyber security?
Secure Remote Access is a combination of security processes or solutions that are designed to prevent unauthorized access to an organization's digital assets and prevent the loss of sensitive data.
What security best practices are for connecting to remote systems?
Best Practices For Remote Access SecurityEnable encryption. ... Install antivirus and anti-malware. ... Ensure all operating systems and applications are up to date. ... Enforce a strong password policy. ... Use Mobile Device Management (MDM) ... Use Virtual Private Network (VPN) ... Use two-factor authentication.More items...•
What are the examples of security considerations for remote users?
Five Remote Access Security Risks And How To Protect Against ThemWeak remote access policies. ... A deluge of new devices to protect. ... Lack of visibility into remote user activity. ... Users mixing home and business passwords. ... Opportunistic phishing attempts.
What are the types of remote access?
The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), Point-to-Point Protocol over Ethernet (PPPoE), Point-to-Point Tunneling Protocol (PPTP), Remote Access Services (RAS), and Remote Desktop Protocol (RDP).
What is the purpose of remote access?
Remote access enables remote users to access files and other system resources on any devices or servers that are connected to the network at any time. This increases employee productivity and enables employees to better collaborate with colleagues around the world.
How do you protect a remote?
Best Tips to Protect Remote Desktop ConnectionUse strong passwords. ... Update your software. ... Limit access using firewalls. ... Enable Network Level Verification. ... Limit users who can log in using remote desktop. ... Use two-factor authentication on highly sensitive systems.
What are the most common remote work security risks?
Top Security Risks of Remote WorkingGDPR and remote working. Remote work means an employer has less control and visibility over employees' data security. ... Phishing Emails. ... Weak Passwords. ... Unsecured Home Devices. ... Unencrypted File Sharing. ... Open Home WiFi Networks.
What is the risk of remote access?
The overriding risk of remote access services and software is a hacker gaining deeper access to your organization, exposing you to a host of IT security threats. Once they gain privileged access to your system, it will be difficult to prevent data loss, prevent phishing, protect against ransomware, etc.
What security issue could happen while working remotely?
Another threat that remote workers face is the possibility of attackers sending phishing emails. These are scams designed to fool people into handing over your details or downloading a malicious attachment containing a keylogger.
What practices allow you to be at your best when working remotely?
7 Best Practices for Working Remotely to Follow in 2022Make communication your top priority.Push yourself to experiment and find ways to be more productive.Be ready to work at different times of the day.Schedule in-person meetings every once in a while.Socialize and put efforts to strengthen your bond with the team.More items...
What is a best practice for compliance in the remote access domain?
Instead, a best practice is to adopt the principle of least privilege, which means that access for all users should be blocked by default and enabled only for the specific accounts that require it.
Which protocol would be used to provide security for employees that access systems remotely from home?
Which protocol would be used to provide security for employees that access systems remotely from home? Explanation: Various application layer protocols are used to for communications between systems. A secure protocol provides a secure channel over an unsecured network.
How to access remote access server?
On the Remote Access server, open the Remote Access Management console: On the Start screen, type, type Remote Access Management Console, and then press ENTER. If the User Account Control dialog box appears, confirm that the action it displays is what you want, and then click Yes.
Where is the Configure button in Remote Access Management Console?
In the middle pane of the Remote Access Management console, in the Step 3 Infrastructure Servers area, click Configure.
How to deploy DirectAccess for remote management only?
In the DirectAccess Client Setup Wizard, on the Deployment Scenario page , click Deploy DirectAccess for remote management only, and then click Next.
How to add roles and features to DirectAccess?
On the DirectAccess server, in the Server Manager console, in the Dashboard, click Add roles and features.
How to install Remote Access on DirectAccess?
On the DirectAccess server, in the Server Manager console, in the Dashboard, click Add roles and features. Click Next three times to get to the server role selection screen. On the Select Server Roles dialog, select Remote Access, and then click Next.
What group does DirectAccess belong to?
For a client computer to be provisioned to use DirectAccess, it must belong to the selected security group . After DirectAccess is configured, client computers in the security group are provisioned to receive the DirectAccess Group Policy Objects (GPOs) for remote management.
How to add domain suffix in remote access?
On the DNS Suffix Search List page, the Remote Access server automatically detects domain suffixes in the deployment. Use the Add and Remove buttons to create the list of domain suffixes that you want to use. To add a new domain suffix, in New Suffix, enter the suffix, and then click Add. Click Next.
What permissions are granted to all users in sp_configure?
Execute permissions on sp_configure with no parameters or with only the first parameter are granted to all users by default. To execute sp_configure with both parameters to change a configuration option or to run the RECONFIGURE statement, a user must be granted the ALTER SETTINGS server-level permission. The ALTER SETTINGS permission is implicitly held by the sysadmin and serveradmin fixed server roles.
How to find properties of a server in Object Explorer?
In Object Explorer, right-click a server and select Properties.
Can you run sp_configure with no parameters?
Execute permissions on sp_configure with no parameters or with only the first parameter are granted to all users by default. To execute sp_configure with both parameters to change a configuration option or to run the RECONFIGURE statement, a user must be granted the ALTER SETTINGS server-level permission. The ALTER SETTINGS permission is implicitly held by the sysadmin and serveradmin fixed server roles.
Static Routes
One way to build a routing table is to have an administrator enter each route manually, using either the RRAS snap-in or the netsh utility. The problem is that the amount of administration is quite often prohibitive, especially on larger networks.
Summarization Routes
The concept of static routes is simple—an administrator programs each and every destination route into the routing table of the RRAS server. When a packet comes in to the server from one interface, the server checks its routing table to determine where the packet should be forwarded to.
Continued
There is a possible price to be paid, however. In our example, any destination network that has the 192.168 root would be considered "reachable" by the server.
Is password management secure?
Unfortunately, these passwords aren’t secure and can easily be used by attackers, making your whole software and data vulnerable. Most default passwords and settings are well known by hackers and are easily found via an Internet search. So having a password will do you no good if it’s not a secure one.#N#SEE ALSO: How to Do Passwords Right: Password Management Best Practices#N#Having default usernames#N#Hackers want to find the easiest way to steal data. For them, an easy way is gaining credentials of remote access. By gaining the credentials, hackers can bypass firewalls. Which is easier, going up against a heavy duty firewall, or finding the password to slip by it?#N#Similar to the password dilemma, by not changing default usernames with security in mind, you’re leaving your remote access vulnerable to attacks.
Is remote desktop access secure?
While remote access is one of the top avenue for hackers to steal data, there are ways to secure it. Here are some tips to make sure your remote desktop connection is secured properly:
Why you need a remote access policy
Access to IT and business resources -- data, databases, systems and networks -- must be protected from unauthorized and potentially damaging attacks. Securing access to company resources from employees working remotely ensures IT assets and employees are shielded from potential disruptions.
How to create a remote access security policy
Remote access security policies should be developed by a cross-functional team to address operational, legal, competitive and other issues associated with remote access to information resources. The team should coordinate with internal departments for input on their remote access requirements and with HR to ensure uniform compliance by employees.
Remote access security policy sample
A remote access security policy can be simple. In fact, a few paragraphs added to an existing cybersecurity policy may be sufficient. The policy language should define remote access security activities and how they build on existing security policies and procedures, noting the metrics discussed previously.
