
What does the JFHQ–Dodin do?
JFHQ–DoDIN’s mission is to oversee the day-to-day operation of DoD’s networks and mount an active defense of them, securing their key cyber terrain and being prepared to neutralize any adversary who manages to bypass their perimeter defenses. The JFHQ–DoDIN commander is dual–hatted as the director of the Defense Information Systems Agency (DISA).
What is the DoD CIO approval process for Dodin commercial connections?
This Appendix describes the process used by a DoD Component to request DoD CIO review and approval of commercial alternatives to DISN-provided transport (referred to in this appendix as a DODIN commercial connection) and non-standard cloud services, and use of Boundary Cloud Access Points (BCAP) that lack an existing DoD CIO approval.
Who is responsible for USCYBERCOM and JFHQ Dodin operational orders (OPORDs)?
C.10.3. Comply with USCYBERCOM and JFHQ DODIN operational orders (OPORDS). In the case that a USCYBERCOM or JFHQ DODIN operational order affects a CSO or C-ITP, the Cybersecurity Services Provider and Contract Officer are responsible for providing the unclassified portion of the OPORD to the CSP and ensuring compliance.
Does the DISN Cao forward expired ATC to JFHQ?
The DISN CAO forwards the list of connections with an expired ATC to JFHQ DODIN for action as described in Section 2.15 of this guide. 2.13 Does the ATC expire within 90 days? Each week, DISN CAO also runs a 90-day-pull report that builds a list of DISN connections with ATCs that expire within the next 30, 60, or 90 days.
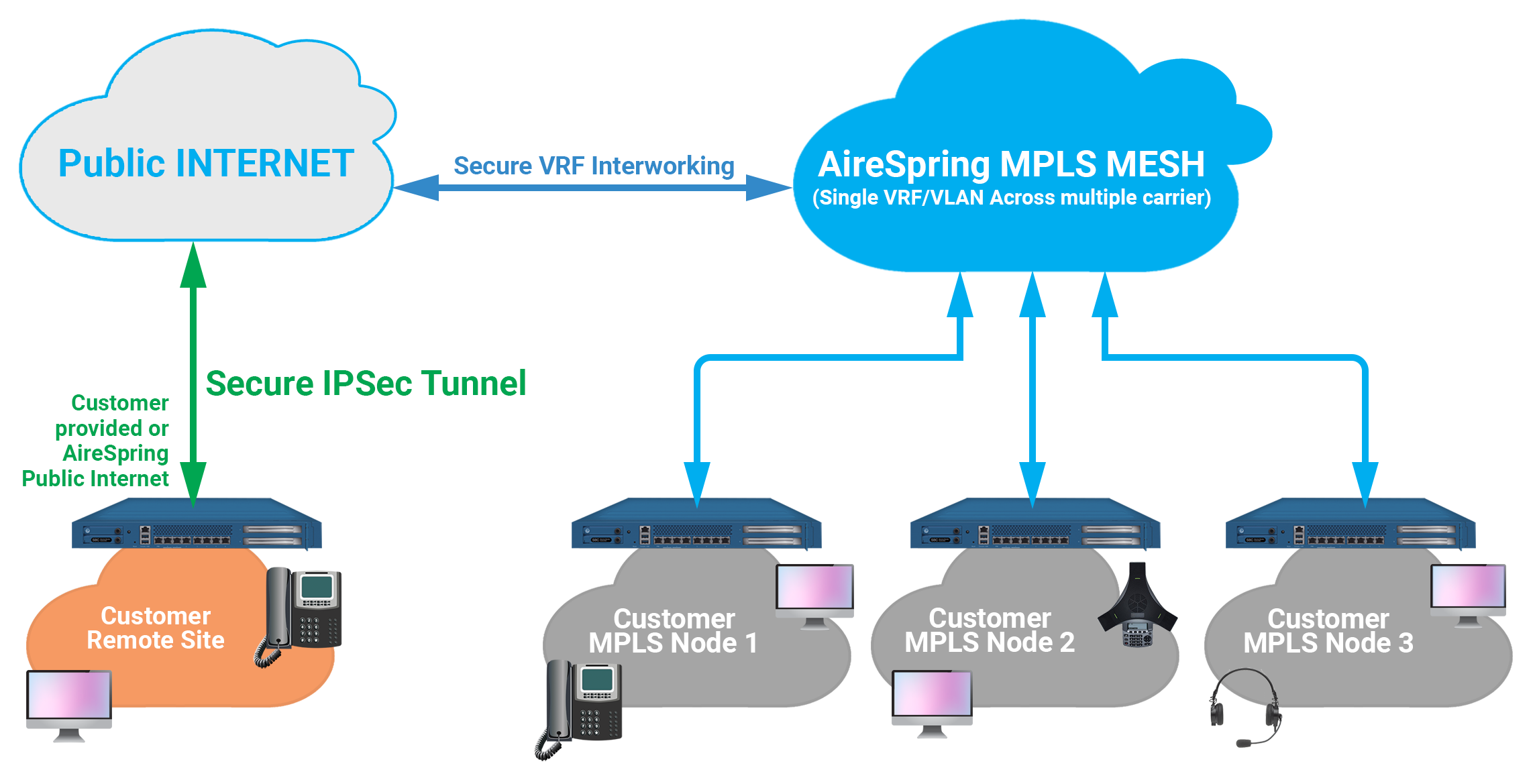
What is Jfhq Dodin?
UNCLASSIFIED. Exercise Global Command and Control of DOD Information Network Operations and DCO-IDM in order to synchronize the protection of DOD component capabilities to enable power projection and freedom of action across all warfighting domains. JFHQ-DODIN Mission.
What is the DOD Dodin?
The DoDIN is the Department of Defense's (DoD) globally interconnected, end-to-end set of electronic information capabilities and associated processes for collecting, processing, storing, disseminating, and managing digital information on-demand to warfighters, policy makers, and support personnel, including owned and ...
Can contractors access SIPRNet?
NISP contractors are NOT permitted unfiltered access to the SIPRNet (CJCSI 6211.02). Sponsor determines access requirements on initial Non-DOD validation letter. If sponsor requires contractor to have additional accesses, the sponsor will be required to fill out a Disclosure Authorization form and submit to disa.
What are the three categorizations of cyberspace operations?
Cyberspace Operations Forces USCYBERCOM accomplishes its missions within three primary lines of operation: secure, operate, and defend the DODIN; defend the nation from attack in cyberspace; and provide cyberspace support as required to combatant commanders (CCDRs).
How big is the Dodin?
Océane DodinCountry (sports)FranceResidenceVilleneuve-d'Ascq, FranceBorn24 October 1996 Lille, FranceHeight1.83 m (6 ft 0 in)Singles26 more rows
What is Gig connected?
Gig Connected is tackling economic mobility and labor shortage by directly connecting blue collar workers with companies. This platform provides a place for workers to find jobs, get rated, and potentially gain skills all while also allowing them to rate their employers.
What is the difference between SIPRNet and Niprnet?
Summary: “NIPRNet” means “Non-classified Internet Protocol Router Network” while “SIPRNet” stands for “Secret Internet Protocol Router Network.” NIPRNet is used to handle less sensitive unclassified data. SIPRNet is used to handle classified information up to the top-secret level.
When did RMF replace Diacap?
May 2015As of May 2015, the DIACAP was replaced by the "Risk Management Framework (RMF) for DoD Information Technology (IT)". Although re-accreditations via DIACAP continued through late 2016, systems that had not yet started accreditation by May 2015 were required to transition to the RMF processes.
How long does it take to get Nipr access?
Transactions may take up to 24 hours to complete processing dependant on the time of day the payment was processed. If items are not posted to your account within 24 hours, please check back or utilize the Contact Us page to notify Accounts Receivable of the payment information.
Is cyberspace the fifth domain?
Cyberspace-The Fifth Operational Domain.
How many warfighting domains are there?
U.S. military operations can be divided into six domains depending on your perspective: subsurface naval, surface naval, ground (which is just another surface), air, space and cyberspace. As we expanded domains, conflicts arise first on the relevance, and then on the ownership of those domains.
Why is Anonymization a challenge of cybersecurity?
Anonymity challenges By anonymizing the data, some of the information they contain is lost and, therefore, its usefulness is diminished. The main challenge of anonymization is therefore to maintain an appropriate balance between the level of privacy and utility of the data.
What are the DoD mission areas within cyberspace?
There are three categories of cyberspace missions for attaining these two objectives: DOD information network operations (DODIN Ops) defensive cyberspace operations (DCO) offensive cyberspace operations (OCO).
What is a Jwics account?
The Joint Worldwide Intelligence Communications System (JWICS) is a secure intranet system utilized by the United States Department of Defense to house "Top Secret/Sensitive Compartmented Information" In day-to-day usage, the JWICS is used primarily by members of the Intelligence Community, such as the DIA within the ...
What is DCO IDM?
DCO-IDM Definition: According to Joint Publication 3-12, Defensive Cyberspace Operations-Internal Defensive Measures (DCO-IDM) are the form of DCO mission where authorized defense actions occur within the defended network or portion of cyberspace.
How many conditions do you need for cyberspace protection?
INFOCON has five levels (see below) ranging from normal conditions all the way to responding to a general attack.
When did JFCC and JTF merge?
The two task forces soon merged, becoming United States Cyber Command, on 21 May 2010. General Keith Alexander (USA), who was also the Director, National Security Agency (DIRNSA), was USCYBERCOM’s first Commander. This dual–hat arrangement for the Commander, USCYBERCOM and DIRNSA remains in effect.
How do national mission forces defend the nation?
National Mission Force teams defend the nation by seeing adversary activity, blocking attacks, and maneuvering to defeat them.
How many teams are there in the CMF?
All 133 teams of the CMF achieved IOC in 2016, the threshold capacity whereby the units could execute their fundamental missions. The CMF reached Full Operational Capability (FOC) in 2018, when all CMF units had reached their projected full strength. At the time of the announcement, the CMF had about 5,000 military and civilian personnel across the 133 teams.
What is the DoD policy on CDS?
IAW DoDI 8540.01, paragraph 3.g, it is DoD Policy that “the DoD-level risk decision on use of a CDS to access or transfer information between different interconnected security domains must be made by the designated DoD risk executive as a CDS authorization (CDSA) ….” IAW DoDI 8540.01, Enclosure 2, paragraph 8.u. (1) DoD Component Heads shall: ”Require the issuance of a DoD ISMRC [sic] or DSAWG CDSA before allowing a CDS to access or transfer information between different interconnected security domains. A CDSA is required for use of a CDS.”
What is JITC certified for?
Work with the JITC to have the product tested and certified for Interoperability and cybersecurity, and placed on the UC APL.
The Power of Women in the STEM Workforce
A significant gender gap has persisted throughout the years at all levels of science, technology, engineering...
Nakasone emphasizes growing partnerships between..
On February 10, 2022, U.S. Army Gen. Paul M. Nakasone, commander of U.S. Cyber Command, director of the...
Iranian intel cyber suite of malware uses open s..
To better enable defense against malicious cyber actors, U.S. Cyber Command’s Cyber National Mission Force has...
Learn more
Learn about small business opportunities and how you can help support our mission.
JOIN OUR TEAM
Join a community of 7K+ professionals that connect and protect the warfighter in cyberspace.
How does a 3ft water line work?
A 3ft pipe comes from the city water pumping station and connects via 2ft pipes to 6” pipes to a 3/4” or so line to you meter and then into your house. It doesn’t matter if you connect to the meter with a 6” pipe, you are still limited by that 3/4” line to your meter. 5G is that line from your house to the meter. Great if your issue was an old 1/2” line. But if the problem is the 3/4” line, the 3ft line, or even the pump itself, your 6” line doesn’t do anything except make it worse because you increased your potential usage rate (up to the limit of the 3/4” line) meaning the overloaded 2ft section just got that much more overloaded.
How many simultaneous connections can NMCI support?
Currently, NMCI and ONE-NET can support roughly 240,000 simultaneous connections for Outlook Web Access (OWA) and 40,000 for Virtual Private Network (VPN) access.”
Why is the network slowed down?
The network has slowed to a crawl because many of our civilians are working from home. All those web-based applications use bandwidth and server processing power which would normally not be used when the civilians' computers are directly connected to the network. Outlook uses your computer's processing power, and the only data moving from the server to the local computer is the email itself, and the only processing the server does is send the email data when the local computer asks for it. With OWA, the server has to use processing power to run the whole application, and the network has to carry all the data necessary to draw the screen, keep track of what you're doing in your mailbox, etc.
Does JFHQ-DODIN block YouTube?
The Joint Force Headquarters for Department of Defense Information Networks (JFHQ-DODIN) has already begun blocking streaming websites such as YouTube, Netflix and Pandora, and it may block social media sites too “to maximize operational bandwidth available for COVID-19 response,” reads a message from the Navy’s Information Dominance Directorate (OPNAV N2/N6) and Fleet Cyber Command/ U.S. 10th Fleet.
Is the Navy being affected by remote users?
Navy spokesman Joe Gradisher told USNI News that the Navy networks are being affected by so many remote users but that it would JFHQ-DODIN’s decision to make regarding blocking social media websites.
Can Navy telework be expanded?
In some places, capacity cannot be expanded, though. For example, according to the message, a limited number of Mobikey and Enhanced Virtual Desktop (EVD)/Virtual Desktop Infrastructure (VDI) instances can be used to support telework, and Navy does not intend to negotiate any more licenses than it already has.
