What services are disabled by default in Junos OS?
These services are all disabled by default in Junos OS. The SSH protocol uses strong authentication and encryption for remote access across a network that is not secure. SSH provides remote login, remote program execution, file copy, and other functions.
How do I manage a juniper device remotely?
You can manage a Juniper Networks device remotely through the J-Web interface. To communicate with the device, the J-Web interface uses the Hypertext Transfer Protocol (HTTP). HTTP allows easy Web access but no encryption. The data that is transmitted between the Web browser and the device by means of HTTP is vulnerable to interception and attack.
Is the SSH server in Junos OS secure?
The SSH server in Junos OS is based on OpenSSH 7 and defaults to a more secure set of ciphers and key-exchange algorithms. OpenSSH 7 omits some legacy cryptography. Lack of support for legacy cryptography in devices causes Junos Space device discovery to fail.
How do I enable/disable incoming SFTP connections in Junos?
Starting in Junos OS Release 19.1R1, we have globally disabled the incoming SFTP connections by default. If desired, you can globally enable incoming SFTP connections by configuring the statement sftp-server at the [edit system services ssh] hierarchy level

How do I access my Juniper router?
How to Access a Juniper Networks Device the First TimeConnect a laptop or a desktop PC to the console port on the front panel of the device.Power on the device and wait for it to boot. ... Log in as the user root . ... Type cli to start the Junos OS CLI. ... Type configure to access CLI configuration mode.
Is Juniper network Connect a VPN?
Juniper Secure Connect is a client-based SSL-VPN application that allows you to securely connect and access protected resources on your network.
How do I SSH into a Juniper switch?
To set up remote access and file-transfer services:Enable SSH access. [edit groups global] user@host# set system services ssh.Enable Telnet access. [edit groups global] user@host# set system services telnet.Enable FTP. ... (Optional) Apply the configuration group. ... Commit the configuration.
How do I connect to Juniper VPN?
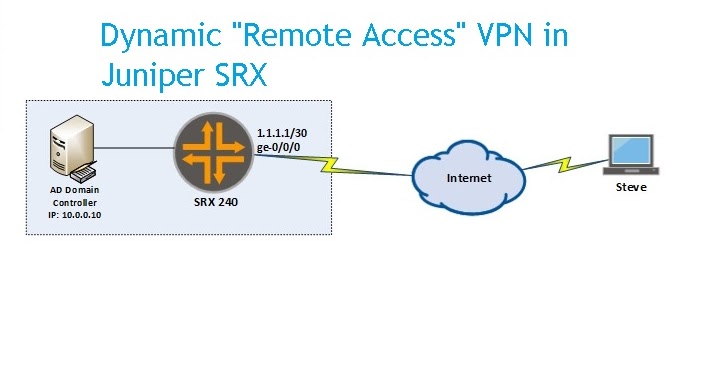
IPsec access is provided through a gateway on the Juniper Networks device....In the Pulse Secure remote client program, the user does the following:Click Add connection.For Type, select Firewall (SRX).For Name, enter the hostname of the SRX gateway. ... For Server URL Name, enter the IP address of the SRX gateway.
What is Juniper Networks network Connect?
Juniper Networks, Inc. is the leader in high-performance networking. Juniper offers a high-performance network infrastructure that creates a responsive and trusted environment for accelerating the deployment of services and applications over a single network.
How do I use Juniper Secure Connect?
0:1922:33Configuring Juniper Secure Connect – J-Web - YouTubeYouTubeStart of suggested clipEnd of suggested clipSo we have that remote worker up top that will be using the juniper secure connect application toMoreSo we have that remote worker up top that will be using the juniper secure connect application to connect into the gateway which is vsrx1. To access internal resources. And so speaking of vs or x1.
How do I access Junos CLI?
To log in to a device and start the CLI:Log in as root . The root login account has superuser privileges, with access to all commands and statements.Start the CLI: root# cli root@> The > command prompt shows that you are in operational mode. Later, when you enter configuration mode, the prompt will change to #.
What is remote SSH?
SSH or Secure Shell is a network protocol that connects users to a remote computer over a secure connection. This allows administrators and other authorized users to connect to secure computers over a network that is not secure, like the Internet. This is accomplished through the use of encryption.
How do I enable SFTP in Juniper?
To enable the incoming SFTP connections, configure sftp-server:To enable incoming SFTP connections include the sftp-server statement at the [edit system services ssh] hierarchy level: [edit system services ssh] user@host# set sftp-server.Commit the configuration. [edit system services ssh] user@host# commit.
What is Junos Pulse VPN?
Pulse Policy Secure provides visibility into the network by detecting and continuously monitoring the network. It provides visibility for on-site and remote endpoints/users connecting through VPN.
Is Pulse secure part of Juniper?
About Pulse Secure Pulse Secure is a new company born from the sale of Juniper Networks Junos Pulse product line to Siris Capital, a leading private equity firm. As a standalone company, Pulse Secure now concentrates resources and focus to solve enterprise mobility challenges.
What is the difference between VPN and Dmvpn?
While a VPN acts as a connector between remote sites and HQ, or between different branches, the DMVPN creates a mesh VPN protocol that can be applied selectively to connections being utilized in the business already. Each different site (or spoke) can connect to one another securely.
Which two authentication methods are part of Juniper Secure Connect?
Authentication Methods There are two ways to authenticate users establishing secure connectivity with juniper secure connect, either local or external authentication, each of these two ways have certain restrictions described below.
Is Pulse Secure owned by Juniper?
In 2014, Siris Capital acquired the Junos Pulse business from Juniper Networks and formed the standalone entity, Pulse Secure.
How does f5 VPN Work?
An even more secure version of the VPN is the Secure Sockets Layer Virtual Private Network (SSL VPN). An SSL VPN uses the Secure Sockets Layer (SSL) protocol to create a secure and encrypted connection over the Internet. The SSL VPN was created to ensure enhanced security and privacy.
How does SSL VPN Work?
An SSL tunnel VPN allows a web browser to securely access multiple network services that are not just web-based via a tunnel that is under SSL. These services could be proprietary networks or software built for corporate use only that cannot be accessed directly via the internet.
How to manage a Juniper network?
You can manage a Juniper Networks device remotely through the J-Web interface. To enable secure Web access, the Juniper Networks devices support HTTP over Secure Sockets Layer (HTTPS). You can enable HTTP or HTTPS access on specific interfaces and ports on the device as needed. Read this topic for information.
What is a self signed certificate on a Juniper switch?
When you initialize a Juniper Networks EX Series Ethernet Switch with the factory default configuration, the switch generates a self-signed certificate, allowing secure access to the switch through the Secure Sockets Layer (SSL) protocol. Hypertext Transfer Protocol over Secure Sockets Layer (HTTPS) and XML Network Management over Secure Sockets Layer (XNM-SSL) are the two services that can make use of the self-signed certificates.
What is SSL in Juniper?
You can enable HTTP or HTTPS access on specific interfaces and ports as needed. The Juniper Networks device uses the Secure Sockets Layer (SSL) protocol to provide secure device management through the Web interface. SSL uses public-private key technology that requires a paired private key and an authentication certificate for providing ...
What protocol does J-Web use?
To communicate with the device, the J-Web interface uses the Hypertext Transfer Protocol (HTTP). HTTP allows easy Web access but no encryption. The data that is transmitted between the Web browser and the device by means of HTTP is vulnerable to interception and attack. To enable secure Web access, the Juniper Networks devices support HTTP ...
How to enable secure web access on EX series switch?
To enable secure Web access, you must generate a digital Secure Sockets Layer (SSL) certificate and then enable HTTPS access on the switch.
What port is secure remote access?
Secure remote access is ensured even when a device between the client and the gateway blocks Internet Key Exchange (IKE) (UDP port 500).
What is SRX traffic selector?
Traffic selectors configured on the SRX Series device and the NCP client determine the client traffic that is sent through the IPsec VPN tunnel. Traffic in and out of the tunnel is allowed only for the negotiated traffic selectors. If the route lookup for a packet’s destination address points to an st0 interface (on which traffic selectors are configured) and the packet’s traffic selector does not match the negotiated traffic selector, the packet is dropped. Multiple Phase 2 IPsec SAs and auto route insertion (ARI) are supported with the NCP Exclusive Remote Access Client. Traffic selector flexible match with port and protocols is not supported. For this feature, the remote address of the traffic selector must be 0.0.0.0/0.
What is split tunneling?
Split tunneling uses a shorter prefix than 0.0.0.0/0 as the protected resource’s address for the local address in a traffic selector configured on the SRX Series device. A corresponding traffic selector can be configured on the remote access client. The SRX Series device allows traffic on the VPN tunnel that matches the results of the flexible match from both traffic selectors. If the traffic selector configured on the remote access client cannot be matched with the traffic selector configured on the SRX Series device, tunnel negotiation fails. For IKEv1, the local and remote addresses in the client's traffic selector configuration must be the same addresses or a subset of the addresses in the corresponding traffic selector configured on the SRX Series device.
What is an ARI in a VPN?
After the tunnel is established, auto route insertion (ARI) automatically inserts a static route to the remote client’s IP address so that traffic from behind the SRX Series device can be sent into the VPN tunnel to the client’s IP address.
How long does it take to log off a remote server?
This is because when a user disconnects, it can take up to one minute for the user to be logged off.
Can SRX support SSL?
In many public hotspot environments, UDP traffic is blocked while TCP connections over port 443 are normally allowed. For these environments, SRX Series devices can support SSL Remote Access VPNs by encapsulating IPsec messages within a TCP connection. This implementation is compatible with the third-party NCP Exclusive Remote Access Client. This section describes the support for NCP Exclusive Remote Access Client on SRX Series devices.