See more
What is Kerberos access?
Kerberos is a computer network security protocol that authenticates service requests between two or more trusted hosts across an untrusted network, like the internet. It uses secret-key cryptography and a trusted third party for authenticating client-server applications and verifying users' identities.
Can Kerberos be used over Internet?
Kerberos authentication requires communicating with a domain controller. This is correct, because the domain's KDC is not accessible over the internet.
Can Kerberos be used for authorization?
It is the default authorization technology in Microsoft Windows. It uses third-party ticket authorization and strong cryptography to make it harder for hackers to gain access to a corporate network. With Kerberos, organizations can access the internet without having to worry about compromising their safety.
How does RDP authentication work?
When Duo Authentication for Windows Logon (RDP) is installed on a system where NLA is enabled, the RDP client prompts for the Windows username and password in a local system dialog. That information is used to connect to the remote system and passed through to the Remote Desktop manager.
Does Kerberos work with IP address?
Beginning with Windows 10 version 1507 and Windows Server 2016, Kerberos clients can be configured to support IPv4 and IPv6 hostnames in SPNs. By default Windows will not attempt Kerberos authentication for a host if the hostname is an IP address. It will fall back to other enabled authentication protocols like NTLM.
Does Kerberos require DNS?
All machines in your domain that will participate in your Kerberos realm need to have working DNS entries, both forward and reverse. This means that, for every machine, a DNS entry exists that maps the hostname to an IP address, and a reverse entry exists for that IP address mapping it back to the original hostname.
Which is better Kerberos or LDAP?
LDAP and Kerberos together make for a great combination. Kerberos is used to manage credentials securely (authentication) while LDAP is used for holding authoritative information about the accounts, such as what they're allowed to access (authorization), the user's full name and uid.
Is Kerberos more secure than LDAP?
Kerberos is more secure than LDAP, and they are often used together. For example, when you open up the Active Directory Users and Computers console, your computer first obtains a ticket to access your Domain Controller and then uses LDAP to actually use the console itself when working with objects such as users or OUs.
What is difference between LDAP and Kerberos?
Kerberos is a protocol that serves for network authentication. This is used for authenticating clients/servers in a network using a secret cryptography key....Difference between LDAP and Kerberos :S.No.LDAPKerberos2.LDAP is used for authorizing the accounts details when accessed.Kerberos is used for managing credentials securely.5 more rows•Dec 9, 2020
What is the difference between SSH and RDP?
A Major Difference between RDP and SSH RDP and SSH are designed to provide two distinct solutions for connecting to remote computer systems. RDP furnishes users with a tool for managing remote connections via a GUI. SSH offers a Secure Shell and is used for text-based management of remote machines.
Why RDP is not secure?
The problem is that the same password is often used for RDP remote logins as well. Companies do not typically manage these passwords to ensure their strength, and they often leave these remote connections open to brute force or credential stuffing attacks. Unrestricted port access.
Is RDP TCP or UDP?
Remote Desktop Protocol (RDP) is a Microsoft proprietary protocol that enables remote connections to other computers, typically over TCP port 3389. It provides network access for a remote user over an encrypted channel.
How does Kerberos authentication work browser?
Kerberos and WebAuth By default, WebAuth also asks you for your password the first time you use it each day. It then stores your Kerberos credentials in a browser cookie and uses them to get new authentication tickets, very similar to the regular Kerberos ticket cache, for each authenticated web site you visit.
How do I enable Kerberos authentication on my website?
1) Click on the website, go to authentication and make sure that windows authentication is enabled. 2) Make sure that when you want to use windows authentication, anonymous authentication is not enabled, which is a common mistake I have observed.
How do I enable Kerberos in Chrome?
Go to Kerberos. For Kerberos tickets, select Enable Kerberos. [Optional] [Users & browsers] Automatically request Kerberos tickets for users when they sign in....Set up KerberosSelect Automatically add a Kerberos account.Enter the Principal name. ... Select Use default Kerberos configuration.
How do I enable Kerberos authentication in Internet Explorer?
To enable Kerberos support in Internet Explorer Click the Tools icon and select Internet Options. In the Internet Options dialog box, click the Security tab. In the Local intranet dialog box, click Advanced. In the text box under Add this website to the zone: enter the URL of your Web server and click Add.
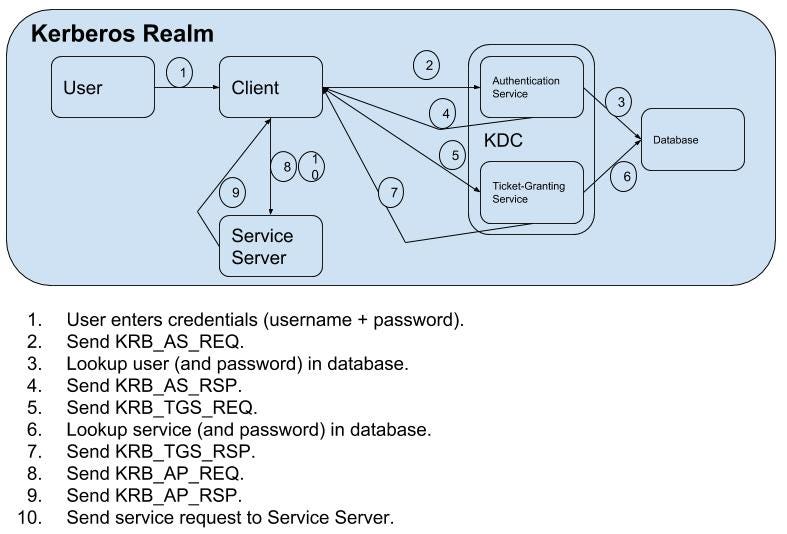
What is Kerberos authentication?
The Kerberos authentication client is implemented as a security support provider (SSP), which can be accessed through the Security Support Provider Interface (SSPI). Initial user authentication is integrated with the Winlogon service single sign-on architecture. The Kerberos Key Distribution Center (KDC) is integrated in the domain controller with other security services in Windows Server. The KDC uses the domain’s Active Directory Domain Services (AD DS) as its security account database. AD DS is required for default Kerberos implementations within the domain or forest. In Windows Server 2012 and Windows 8, Kerberos authentication can be leveraged to address lack of connectivity to the domain controller from outside the corporate firewall. To do so, it proxies Kerberos authentication and password change messages for users who are requesting domain access through DirectAccess or Remote Desktop Services.
What is the Kerberos SSPI setting?
The new Set maximum Kerberos SSPI context token buffer size Kerberos administrative template policy setting enables you to set the value that is returned to applications that request the maximum size of the authentication context token buffer. This Group Policy setting replaces the need to manually set the MaxTokenSize registry value in HKEY_LOCAL_MACHINESYSTEMCurrentControlSetControlLsaKerberosParameters.
What is the KDC in Windows Server 2012?
This compression makes deployments easier when organizations have many users with high resource domain membership. In Windows Server 2012 and Windows 8, the KDC automatically compresses the groups in the resource domain, which can reduce the size of the service ticket and reduce application authentication failures. After the Windows Server 2012 KDC performs the compression, the supported operating systems Windows Server 2012, Windows Server 2008 R2, Windows Server 2008, Windows Server 2003, Windows 8, Windows 7, Windows Vista and Windows XP can use the more compact Kerberos service ticket.
How many bytes are in Kerberos SSPI?
In Windows Server 2012 and Windows 8, the default Kerberos SSPI context token buffer size has been increased to advised to set this value to more than 48,000 bytes.
Why does authentication fail?
When applications query to determine the maximum size of the authentication context token buffer so they can preallocate memory, they can fail authentication when the Kerberos or negotiate message returned is larger than expected.
What is the ISC_REQ_UNVERIFIED_TARGET_NAME flag?
In Windows Server 2012, InitializeSecurityContext () adds support for the ISC_REQ_UNVERIFIED_TARGET_NAME flag for applications to use when they provide target names from an untrusted source. This allows services that are configured for Extended Protection to handle authentication to an untrusted source securely. Because NTLM and Kerberos clients that are attempting to authenticate using an untrusted SPN state that explicitly in their authentication messages, the services then will allow or fail the authentication request based on its Extended Protection configuration:
What is the threshold value for Kerberos tickets?
If the Warning events for large Kerberos ticketssetting is not enabled, the threshold value defaults to 12,000 bytes, which is the default setting for MaxTokenSize for Kerberos tickets in Windows 7, Windows Server 2008 R2, and prior versions.
What is Kerberos?
Kerberos authentication is currently the default authorization technology used by Microsoft Windows, and implementations of Kerberos exist in Apple OS, FreeBSD, UNIX, and Linux.
What is Kerberos's name?
According to myth, Kerberos (you might know him as Cerberus) guards the Gates to the Underworld. He’s a big 3 headed dog with a snake for a tail and a really bad temper.
Is Kerberos Obsolete?
Kerberos is far from obsolete and has proven itself an adequate security-access control protocol, despite attackers’ ability to crack it. The primary advantage of Kerberos is the ability to use strong encryption algorithms to protect passwords and authentication tickets. With today’s computers, any brute force attack of the AES encryption protocol used by the current version of Kerberos will take approximately longer than this solar system has left to survive. Suffice to say: Kerberos is going to be around for a while in one form or another.
What is going to replace Kerberos?
There are no real contenders to replace Kerberos in the pipeline. Most of the advancements in security are to protect your password or provide a different method of validating who you are to Kerberos. Kerberos is still the back-end technology. Kerberos excels at Single-Sign-On (SSO), which makes it much more usable in a modern internet based and connected workplace. With SSO you prove your identity once to Kerberos, and then Kerberos passes your TGT to other services or machines as proof of your identity.
How does Varonis monitor Kerberos?
Varonis monitors Active Directory domains for Kerberos attacks, privilege escalations, brute force attacks, and more . Our security analytics combines user events, security events, and perimeter telemetry – to detect and alert on potential attacks and security vulnerabilities.
What does KDC do?
The KDC verifies the credentials and sends back an encrypted TGT and session key
What is NTLM authentication?
Before Kerberos, Microsoft used an authentication technology called NTLM. NTLM stands for NT Lan Manager and is a challenge-response authentication protocol. The target computer or domain controller challenge and check the password, and store password hashes for continued use.
What is remote access?
The remote access commands were designed for smaller networks, such as intranets. They enable you to log in remotely to another account on another system and to copy files from one system to another. You can also obtain information about another system, such as who is logged on currently (see Table 15-3 ). Many of the remote commands have comparable network communication utilities used for the Internet. For example, rlogin, which remotely logs into a system, is similar to telnet. The rcp command, which remotely copies files, performs much the same function as ftp.
How to access someone else's account?
You could access an account on another system by first logging into your own and then remotely logging in across your network to the account on the other system. You can perform such a remote login using the rlogin command, which takes as its argument a system name. The command connects you to the other system and begins login procedures. Bear in mind that if you are using an SSH-enabled network connection, you would use slogin instead of rlogin. The slogin command or Kerberos rlogin will provide secure encrypted login access.
What is LTWRE-RT-MEM1 service?
There is a service running on LTWRE-RT-MEM1 server that runs starts /runs as “LocalSystem” account. This service connects to a file share on LTWRE-CHD-MEM1 named “AppShare” to access some files. The Service is failing to retrieve the files and is giving you an error of “Access is denied”. When you attempt to access the share as a domain user account on LTWRE-RT-MEM1 you are able to access the share.
Is my Echo remote ping able?
Yep, the remote system is ping able. See the Echo request and reply. So the system is up and available.
Can you use Wireshark to capture network trace?
You can use any network capture utility that you feel comfortable with. I prefer Netmon , nmcap (part of Netmon 3.x) or netcap (XP and 2003 support tools) to collect the network trace, and I use Wireshark to view the network capture. This is in no way an endorsement of Wireshark – feel free to use Ethereal , Packetyzer , etc .
Prerequisites
Prior to integrating the B Series Appliance with your Kerberos configuration, ensure the following requirements are met:
Kerberos Security Provider Settings
The most appropriate configuration for your Kerberos security provider depends on your overall authentication and network infrastructure, as well as where your B Series Appliance is located in your network.
SPN Use in BeyondTrust Software
Browsers may use different methods to canonicalize the hostname for a site, including performing a reverse lookup of the IP of the hostname specified in the URL. The SPN canonicalization of this address may cause the browser to request an SPN based on an internal hostname rather than the B Series Appliance hostname.
Question
I've setup test lab, at the end of the configuration wizard there is an error on Kerberos status
All replies
Are you trying to run DirectAccess on a server that is already hosting Exchange? This is not going to be supported, and will be difficult, maybe impossible, to get working. Both DirectAccess and Exchange make use of IIS for website bindings - they will conflict with each other.
Remote access options for your device type
HINT: CryptoCard/YubiKey to Sandia Anywhere: Internal (intranet site) for detailed information on working remotely, plus how-to, task-based instructions for these remote access methods.
Need help?
CryptoCard/YubiKey to these additional resources for detailed instruction and how-tos. Or contact CCHD ( chat or 505-845-2243) M – F, 7 am to 5 pm MT.