How do I log in to Keycloak?
The Keycloak Login page opens. Log in as alice using the password you specified for that user. After authenticating, the following page is displayed: The default settings defined by Keycloak when you enable authorization services for a client application provide a simple policy that always grants access to the resources protected by this policy.
What is Keycloak authentication?
Keycloak is an open source Identity and Access Management solution aimed at modern applications and services. It makes it easy to secure applications and services with little to no code. Authentication with Keycloak brings to the table virtually every feature you might want regarding user authentication and authorization.
What is the client configuration for Keycloak?
The client configuration is defined in a keycloak.json file as follows: The name of the realm. The base URL of the Keycloak server. All other Keycloak pages and REST service endpoints are derived from this. It is usually in the form https://host:port/auth. The client-id of the application.
What is Keycloak and how does it work?
Keycloak can then act as a sharing management service from which resource owners can manage their resources. Keycloak is a UMA 2.0 compliant authorization server that provides most UMA capabilities. As an example, consider a user Alice (resource owner) using an Internet Banking Service (resource server) to manage her Bank Account (resource).

How do I access a Keycloak?
Open command prompt and run docker-compose up to run keycloak. Open browser and enter the keycloak url. Click on Administration Console. Default username and password is 'admin' , 'admin'.
How do I get a Keycloak UI?
Keycloak Admin UInode --version. In order to run the Keycloak server you will also have to install the Java Development Kit (JDK). ... npm install. ... npm run server:start. ... npm run server:import-client. ... npm run start. ... npm run lint. ... THEME_NAME=rh-sso npm run build. ... THEME_NAME=rh-sso npm run start.More items...
Are Keycloaks free?
Is Keycloak free? Yes, as for now Keycloak is open-source and has Apache License 2.0.
How do I run a Keycloak server on a different port?
The above commands will add the offset of 100 to the defaults ports available for Keycloak server. For example, previously the ports where 8443 and 8000. Now the new ports become 8443 + 100 = 8543 and 8080 + 100 = 8180.
Which is better Okta or Keycloak?
So Okta provides the same features as Keycloak and the only difference is that Okta is a paid enterprise solution and Keyclock is a open-source solution? Yes. But you can also sign up for an Okta developer account and get 1000 MAU (monthly active users) for free!
How many users can Keycloak handle?
As far as I know there are no known limitations to the number of clients. One suggesting is to give Keycloak as much memory as you can so things can be cached and accessed quickly.
How secure is Keycloak?
Security with keycloak Once authenticated, the user can access other allowed web applications and is not prompted to enter login credentials again. User information and meta data is stored; based on this information a security token is generated and is sent across to applications for subsequent authentication.
Are Keycloaks stable?
Keycloak is an open source software product to allow single sign-on with Identity and Access Management aimed at modern applications and services....Keycloak.Developer(s)WildFly, a division of Red HatStable release18.0.1 / June 16, 2022Repositorygithub.com/keycloak/keycloakWritten inJavaTypeSingle sign-on system5 more rows
What is the difference between Keycloak and Red Hat SSO?
Keycloak is the upstream open source community project for Red Hat Single Sign-On (RH-SSO). RH-SSO is a core service that is part of a number of products such as Red Hat JBoss Enterprise Application Platform. If you've logged into to developers.redhat.com or openshift.com you are using Keycloak.
Does Keycloak need a database?
Keycloak comes with its own embedded Java-based relational database called H2. This is the default database that Keycloak will use to persist data and really only exists so that you can run the authentication server out of the box. We highly recommend that you replace it with a more production ready external database.
What is realm Keycloak?
A realm manages a set of users, credentials, roles, and groups. A user belongs to and logs into a realm. Realms are isolated from one another and can only manage and authenticate the users that they control. clients. Clients are entities that can request Keycloak to authenticate a user.
What port does Keycloak use?
8080By default, Keycloak is available on http://127.0.0.1:8080/auth/ and https://127.0.0.1:8443/auth/.
How do I download a Keycloak?
To install the Keycloak Service Pack, it must be installed on a different server instance.Change to the root directory of your WildFly distribution.Unzip the keycloak-overlay-18.0. [zip|tar. gz] file.Open the bin directory in a shell.Run ./jboss-cli. [sh|bat] --file=keycloak-install. cli .
How do I set up a Keycloak?
Configure Keycloak serverCreate a Realm (or use an existing one).Create a Client. The client represents an instance of the EBICS Client application.Define one or more Roles for the client. ... Optionally, you can create Groups, which are logical groupings or sets of permissions. ... Create Users. ... Assign roles to the users.
How do I install a local Keycloak?
Setting Up a Keycloak ServerDownload and install keycloak. Download the latest version of keycloak from here . ... Creating a Realm. A successful login will take us to the console and open up the default Master realm for us. ... Creating a client. Now we'll navigate to the Clients page. ... Creating a Role and a User.
How do I start a Keycloak standalone?
To do first this open the Keycloak admin console (localhost:8180/admin or http://
Single-Sign On
Users authenticate with Keycloak rather than individual applications. This means that your applications don't have to deal with login forms, authenticating users, and storing users. Once logged-in to Keycloak, users don't have to login again to access a different application.
Identity Brokering and Social Login
Enabling login with social networks is easy to add through the admin console. It's just a matter of selecting the social network you want to add. No code or changes to your application is required.
User Federation
Keycloak has built-in support to connect to existing LDAP or Active Directory servers. You can also implement your own provider if you have users in other stores, such as a relational database.
Admin Console
Through the admin console administrators can centrally manage all aspects of the Keycloak server.
Account Management Console
Through the account management console users can manage their own accounts. They can update the profile, change passwords, and setup two-factor authentication.
Standard Protocols
Keycloak is based on standard protocols and provides support for OpenID Connect, OAuth 2.0, and SAML.
Authorization Services
If role based authorization doesn't cover your needs, Keycloak provides fine-grained authorization services as well. This allows you to manage permissions for all your services from the Keycloak admin console and gives you the power to define exactly the policies you need.
How to enable user managed access in Keycloak?
To do so, open the realm settings page in Keycloak Administration Console and enable the User-Managed Access switch.
How to get permissions from Keycloak?
To obtain permissions from Keycloak you send an authorization request to the token endpoint. As a result, Keycloak will evaluate all policies associated with the resource (s) and scope (s) being requested and issue an RPT with all permissions granted by the server.
What is Keycloak policy?
As mentioned previously, Keycloak allows you to build a policy of policies, a concept referred to as policy aggregation. You can use policy aggregation to reuse existing policies to build more complex ones and keep your permissions even more decoupled from the policies that are evaluated during the processing of authorization requests.
What is an OAuth2 token?
OAuth2 clients (such as front end applications) can obtain access tokens from the server using the token endpoint and use these same tokens to access resources protected by a resource server (such as back end services). In the same way, Keycloak Authorization Services provide extensions to OAuth2 to allow access tokens to be issued based on the processing of all policies associated with the resource (s) or scope (s) being requested. This means that resource servers can enforce access to their protected resources based on the permissions granted by the server and held by an access token. In Keycloak Authorization Services the access token with permissions is called a Requesting Party Token or RPT for short.
What does AuthzClient do?
With an AuthzClient instance in hands, resource servers can interact with the server in order to create resources or check for specific permissions programmatically.
When creating a role-based policy, can you specify a specific role as Required?
When creating a role-based policy, you can specify a specific role as Required. When you do that, the policy will grant access only if the user requesting access has been granted all the required roles. Both realm and client roles can be configured as such.
Can a resource server check for permissions?
Depending on your requirements, a resource server should be able to manage resources remotely or even check for permissions programmatically. If you are using Java, you can access the Keycloak Authorization Services using the Authorization Client API.
What does Keycloak do after authentication?
To enable Cloud Identity and Google Workspace to verify the integrity and authenticity of that assertion, Keycloak signs the assertion with a special token-signing key and provides a certificate that enables Cloud Identity or Google Workspace to check the signature.
What to do if you don't have a Cloud Identity account?
Before you begin. If you don't have a Cloud Identity account, sign up for an account. Make sure your Cloud Identity account has super-admin privileges. If your Keycloak server is used to manage more than one realm, decide which realm you want to use for the federation.
Does Cloud Identity have superadmin privileges?
The Cloud Identity user does not have super-admin privileges. User accounts that have super-admin privileges must always sign in by using Google credentials, so they aren't suitable for testing single sign-on. Open a new browser window and go to the Google Cloud Console.
Does Keycloak have built in integration?
Note: Keycloak does not provide built- in integration for automatically provisioning users and groups to Cloud Identity or Google Workspace. To automate user and group provisioning, you must combine Keycloak with Google Cloud Directory Sync or other provisioning tools.
Reporting Security Vulnerabilities
If you've found a security vulnerability, please look at the instructions on how to properly report it
Reporting an issue
If you believe you have discovered a defect in Keycloak please open an issue . Please remember to provide a good summary, description as well as steps to reproduce the issue.
Getting started
To run Keycloak download the distribution from our website. Unzip and run:
Building from Source
To build from source refer to the building and working with the code base guide.
Contributing
Before contributing to Keycloak please read our contributing guidelines.
Running a Keycloak server
There are multiple ways to host your Keycloak instance. If you’d like to do it the traditional way, you can download the distribution file from https://www.keycloak.org/downloads.html and run the bin/standalone.sh script.
Server configuration
What you’re seeing on the page above is the default (master) realm. A realm is a domain in which several types of entities can be defined, the most prominent being:
Creating the web app
We’re going to create a simple React-based app that allows the user to navigate between two components: one public and one that requires logging in. Instructions will be step-by-step, for the benefit of those readers who have had no previous exposure with React.
Useful links
UPDATE: The second part is now available! Continue reading here: User Authentication with Keycloak – Part 2: Akka HTTP backend [/av_textblock]
Create Realm
After logging in to the Keycloak console, in the top left corner there is an option of adding a new Realm.
Create Client
In the left pane, there is an option for Clients. This will show all the clients in the new realm. Firstly, we will create a new client with the following configurations.
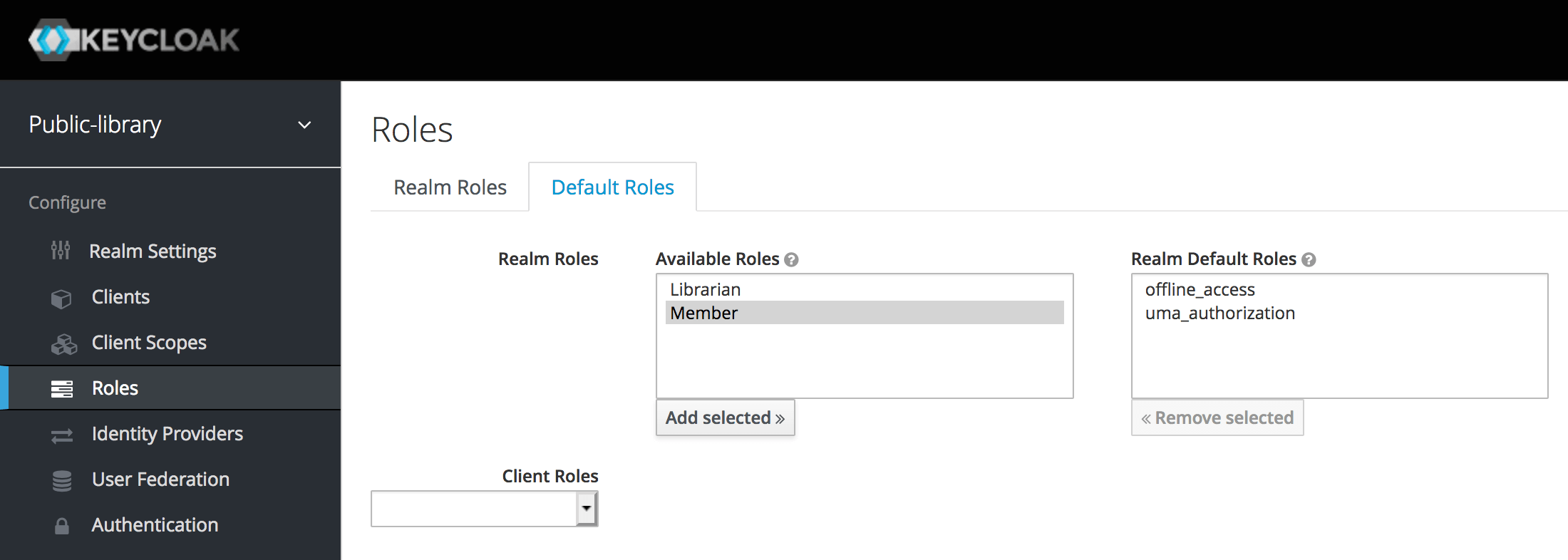
Create Realm roles
Now we will create Realm roles named app-member and app-admin, respectively, by assigning corresponding springboot-rolebased-microservice roles ( Member, Admin ). Following are the steps to do what is stated above.
Create Users
Now we will create two users, one with admin privileges and the other with member privileges. To create a user, go to the Users option in the left pane and then click Add User.
Generate Access Tokens
Now we will generate access tokens for our users. First, go to Realm Settings. In the Endpoints field, click on OpenID Endpoint configuration. Here you will find a URL for token_endpoint.
Spring Boot Application Configuration
We will proceed with the development of our Maven, Spring Boot Project for a simple use case of the Research Journal Management System.
Testing
According to our KeyCloak Security Configuration class, the user with the role Member can access /member API, and the user with the role Admin can access /admin API. Let’s test our application using Postman.