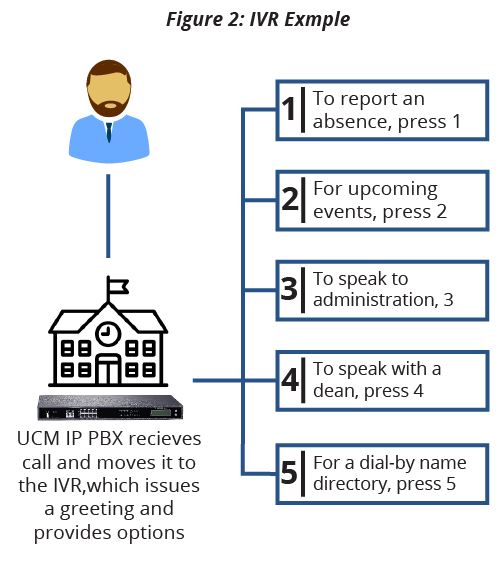
How do I connect to remote desktop from KSU?
See: KSU Guest WiFi Network If you are connecting from off-campus, you must be connected to the campus VPN before you can connect to the Remote Desktop servers. See the KSU VPN page for details on how to obtain and use the VPN client. Logging In
How do I connect to KSU's CS system?
When you run it, you should login with your KSU eID and connect using the "Full Tunnel" option. This routes all your desktop network traffic through the KSU network, effectively putting your desktop behind the campus firewall. You can now use Remote Desktop or SSH client to connect to any CS system.
How do I connect to K-State's VPN?
VPN software (free for K-State faculty/staff/students) is available here . Once connected to the VPN, start the Remote Desktop Connection (Start | All Programs | Accessories | Remote Desktop Connection) and type in the hostname of the computer (in the format of xx0000.engg.ksu.edu, where xx0000 is the CECS-affixed asset tag:Sticker on your desktop)
How do I connect to remote desktop from off campus?
If you are connecting from off-campus, you must be connected to the campus VPN before you can connect to the Remote Desktop servers. See the KSU VPN page for details on how to obtain and use the VPN client. To login to Remote Desktop, you must use your eID and your eID password (This is the same password used for KSIS and Webmail).

How to contact IT Help Desk?
Need help? For self-help, view the IT Knowledge Base articles. Need more help, contact the IT Help Desk 785-532-7722 or your local IT support staff.
Can you take confidential documents to a remote location?
Do not take any electronic or paper documents containing confidential or proprietary data to a remote work location. Employees should consult with their supervisor regarding work requiring the use of confidential or proprietary data. Loss or sharing of confidential or proprietary data is considered a security breach.