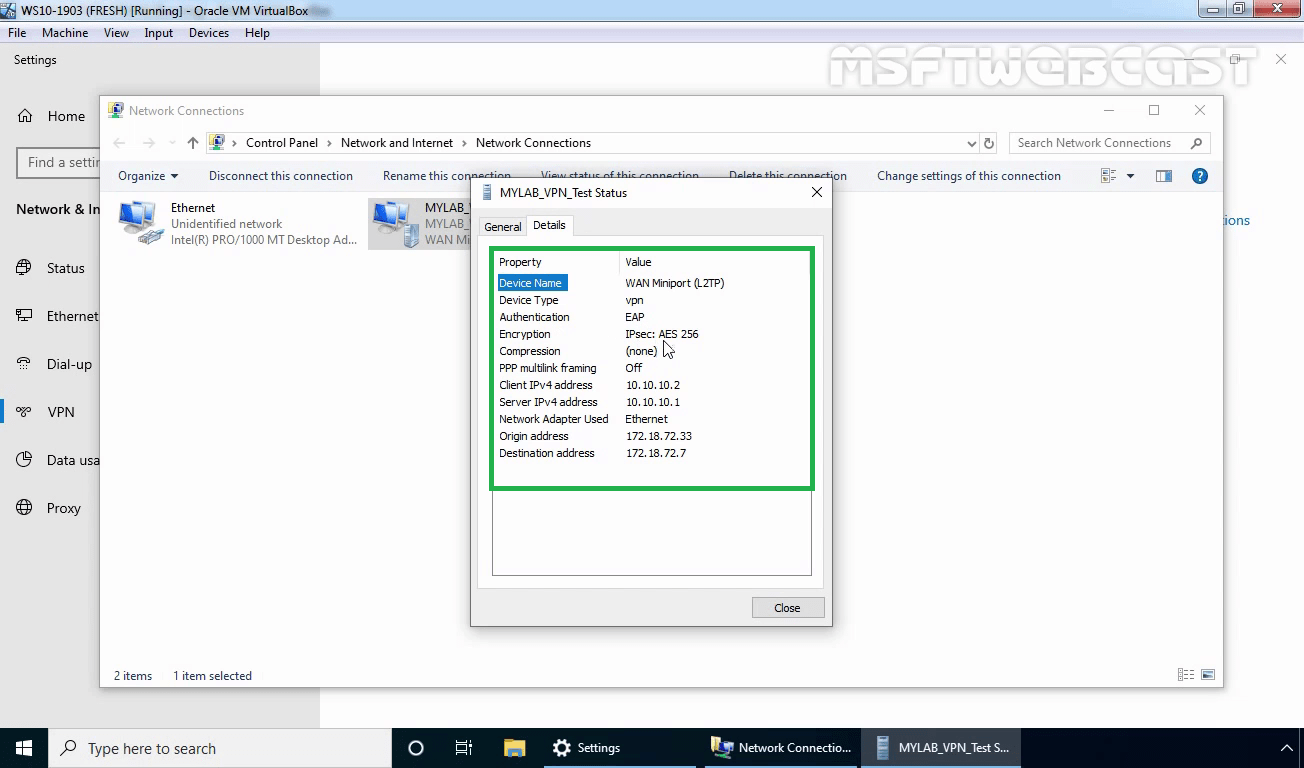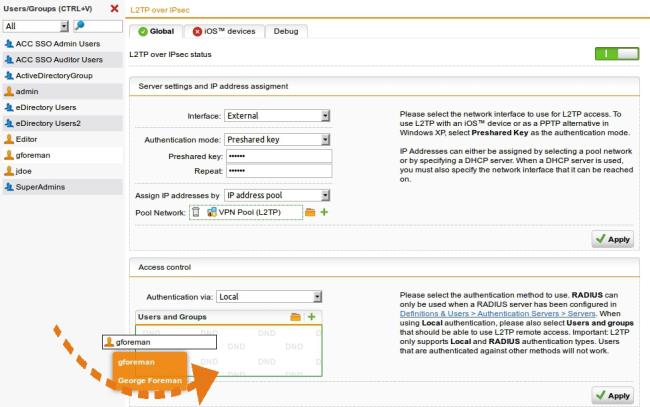
Create an L2TP connection
- Go to Remote access VPN > L2TP and click L2TP global settings.
- Select Enable L2TP to turn on L2TP connections.
- Specify the general settings: Name Description Assign IP from Enter the IP address range to lease. Allow leasing IP...
- Specify the client information: Name Description Primary DNS server Select a DNS server from the drop-down list, or...
How do I enable L2TP on my Network?
Create a firewall rule to allow inbound VPN traffic. Go to Remote access VPN > L2TP and click L2TP global settings. Select Enable L2TP to turn on L2TP connections. Enter the IP address range to lease.
Can I use IKEv2 instead of L2TP/IPsec for remote access VPN?
We strongly recommend using another solution such as IKEv2 instead of L2TP/IPsec. IPsec Remote Access VPN Example Using IKEv2 with EAP-MSCHAPv2 contains a walkthrough for configuring IKEv2. Before configuring the IPsec portion, setup the L2TP server as described in L2TP Server Configuration and add users, firewall rules, etc, as covered there.
How to configure an L2TP VPN on Ubiquiti edge router?
How to configure an L2TP VPN on a Ubiquiti Edge Router 1 Firewall rules. The next step is to create the Firewall rules, to allow the VPN tunnel establishment and the VPN traffic to go through the Router. 2 Configure the authentication. ... 3 Create a user. ... 4 Assign the IP range. ... 5 Select the interface. ...
What is L2TP over IPSec VPN in Windows Server 2019?
In this tutorial, we will configure a fresh VPS running Windows Server 2019 as an L2TP over IPSec VPN. L2TP or Layer 2 Tunneling Protocol is a tunneling protocol but it does not provide strong encryption. IPSec comes into picture here, which provides very strong encryption to data exchanged between the remote server and client machine.

How do I access L2TP VPN?
Start the L2TP ConnectionIn the Windows notification area (System Tray), click the Network icon. A list of available networks and VPNs appears.Click the VPN connection. The Network & Internet VPN settings appear.Select the VPN connection. Click Connect. ... Type your user name and password.Click OK.
What is the difference between PPTP and L2TP?
PPTP VPN is easy to setup and use with faster speeds, but can result in a less secure connection. L2TP VPN, on the other hand, has slower speeds, but offers stronger security which makes it a good choice.
Is L2TP better than OpenVPN?
In Summary: L2TP/IPsec is theoretically secure, but there are some concerns. It's easy to set up, but has trouble getting around firewalls and isn't as efficient as OpenVPN. Stick with OpenVPN if possible, but definitely use this over PPTP.
How do I access VPN remotely?
Simply go to Start -> Accessories -> Remote Desktop Connection and enter the IP address of the other Windows computer. desktop software. From HOME Mac to OFFICE Windows: Connect with VPN, then use Remote Desktop Client. From HOME Windows to OFFICE Mac: Connect with VPN, then use VNC client.
Is L2TP a VPN?
L2TP is a VPN protocol that doesn't offer any encryption or protection from the traffic that passes through the connection. For this reason, it's usually paired with IPSec, which is an encryption protocol.
What is L2TP used for?
Layer Two Tunneling Protocol (L2TP) is an extension of the Point-to-Point Tunneling Protocol (PPTP) used by internet service providers (ISPs) to enable virtual private networks (VPNs).
Why is L2TP not secure?
L2TP doesn't actually specify any mandatory encryption, but relies on PPP's MPPE encryption method. This is why it is almost always paired with IPSec, which supports up to AES-256. A big issue with IPSec is that it uses UDP port 500 and this makes it pretty easy to block by firewalls.
Is L2TP still secure?
The L2TP protocol can be highly secure when used in conjunction with IPSec. It is highly compatible, working on operating systems like Windows and macOS by default. L2TP (and L2TP/IPSec) are relatively easy to set up due to their high compatibility. More firewall-friendly as it runs over UDP protocol.
Which VPN is most secure?
OpenVPNOpenVPN is the most secure VPN protocol. It's compatible with a range of encryption ciphers including AES-256, Blowfish, and ChaCha20. It has no known vulnerabilities and is natively supported by almost every VPN service. While we recommend OpenVPN, WireGuard is a secure and faster alternative.
How can I remotely access my computer from anywhere?
On your Windows, Android, or iOS device: Open the Remote Desktop app (available for free from Microsoft Store, Google Play, and the Mac App Store), and add the name of the PC that you want to connect to (from Step 1). Select the remote PC name that you added, and then wait for the connection to complete.
Can I remote into my work computer from home?
There are two main methods remote workers can use to connect to their work computer from home: either use a VPN to connect to a work network, or use a remote desktop solution.
What is the difference between Pppoe and L2TP?
The most and noticeable different is layer of tunneling. PPPOE is a Layer 2 (Data Link Layer) tunneling protocol while L2TP is a Layer 3 (Network Layer) tunneling protocol.
Is L2TP secure?
The L2TP protocol can be highly secure when used in conjunction with IPSec. It is highly compatible, working on operating systems like Windows and macOS by default. L2TP (and L2TP/IPSec) are relatively easy to set up due to their high compatibility. More firewall-friendly as it runs over UDP protocol.
Is PPTP good enough?
PPTP is one of the easiest types of VPN to set up and comes pre-installed on most Windows, Mac OSX, Android, and iOS devices. Not only is it easier, it's faster than other built-in protocols like L2TP/IPSec, SSTP, and IKEv2. But PPTP is widely regarded as obsolete.
What is the safest VPN protocol?
Many VPN experts recommend OpenVPN as the most secure protocol. It uses 256-bit encryption as a default but also offers other ciphers such as 3DES (triple data encryption standard), Blowfish, CAST-128, and AES (Advanced Encryption Standard).
Configuring the L2TP Server
The EdgeRouter L2TP server provides VPN access to the LAN (192.168.1.0/24) for authenticated L2TP clients.
Setting up the L2TP Client
The next step is to configure the L2TP VPN settings on the client (s). Make sure to match the credentials on the client and server (EdgeRouter).
What is L2TP in the Internet?
L2TP is most commonly deployed in remote-access-type scenarios that use the Internet to offer intranet-type services. The concept is that of a Virtual Private Network (VPN). The two primary physical elements of L2TP are the L2TP Access Concentrator (LAC) and the L2TP Network Server (LNS):
What port does L2TP use?
L2TP uses the registered User Datagram Protocol (UDP) port 1701, and the whole L2TP packet is encapsulated within the UDP datagram. As per normal UDP operation, the tunnel initiator selects an available UDP port and sends port number 1701 to the UDP destination.
What is LNS in L2TP?
LNS—The LNS is a peer to the LAC that acts as one side of the tunnel endpoint. The LNS is the termination point for the LAC PPP tunneled sessions. This is used to aggregate the multiple LAC-tunneled PPP sessions and ingress into the private network. There are two different message types that L2TP uses:
What is the LCP function in PPP?
Link establishing—As part of the link establishing phase, PPP uses an LCP function that must be completed and declared open before the link enters the authentication phase , if applicable, and negotiates the opening of the network layer. LCP is also used to terminate the PPP link.
What is L2TP in PPP?
L2TP provides an encapsulation method for the transmit of tunneled PPP frames, which allows the PPP endpoints to be tunneled over a packet-switched network. L2TP is most commonly deployed in remote-access-type scenarios that use the Internet to offer intranet-type services. The concept is that of a Virtual Private Network (VPN).
What is the source port number?
In Cisco IOS Software, the source and destination port numbers are always set to UDP port number 1701.
Is authentication required for LCP to NCP?
Authentication—The authentication phase is implementation-specific and is not a mandatory requirement for a move from LCP to NCP. If negotiated and agreed upon during the LCP phase, the remote peer must identify itself and pass the agreed authentication method before PPP moves to the network layer.
Firewall
Additional configuration may be needed if you have a firewall policy on the external interface.
Allow clients to reach external hosts
If you want the VPN to be used for external access (that is, allow clients connected to reach external hosts from the VPN server), SNAT will need to be properly configured:
Additional Configuration Options
A full list of configuration options for L2TP can be seen by hitting the tab key after typing set vpn l2tp remote-access:
Introduction
A VPN or Virtual Private Network is used to securely tunnel the data from a local computer to a remote server. You can visualize VPN as a private network distributed across the internet or public network. Using VPN, different devices can securely talk to each other as if they are connected over a private network.
Conclusion
In this tutorial, we have successfully configured a fresh Windows Server 2019 server as an L2TP/IPSec VPN servers. You can now use the VPN server to securely connect to the other connected devices. You can also use this VPN server as a proxy server to securely access the internet.
Firewall rules
The next step is to create the Firewall rules, to allow the VPN tunnel establishment and the VPN traffic to go through the Router. Copy and paste the following commands, note that you may need to change the rule names, depending on the rules that you already have in place.
Configure the authentication
Then we are going to configure the authentication, here you need to replace the pre-shared-secret key with some strong password.
Create a user
Now, we will create a user, repeat this steps several times if you have more users.
Assign the IP range
Now, we are going to assign the IP range for the SNAT Pool. This is a range of IP addresses on your network that will be used for DHCP to assign internal IP addresses to the users. As an example we will use 192.168.2.30-192.168.2.130, which means we have enough IP addresses for 100 users.
Select the interface
We will select the interface where will allow the VPN Tunnel to be established, this is your Internet facing interface. In our example eth2
Windows 10 setting
Following these steps the VPN tunnel should be established without issues. If your Windows 10 users are having connection fails, make sure you enable MSCHAPv2 on the VPN adapter as this is required for L2TP tunnels with Ubiquiti EdgeRouter to work as shown below: