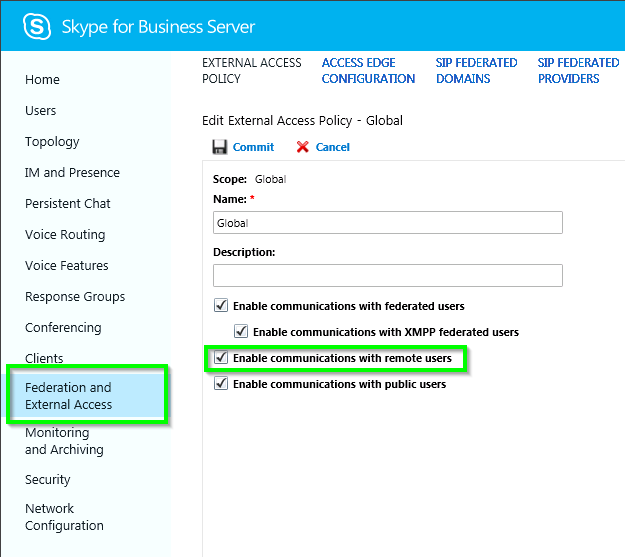
To configure an external access policy to support remote user access
- From a user account that is a member of the RTCUniversalServerAdmins group (or has equivalent user rights), or is assigned to the CsAdministrator role, log on to any computer in your internal deployment.
- Open a browser window, and then enter the Admin URL to open the Lync Server Control Panel. ...
- In the left navigation bar, click External User Access, and then click External Access Policy.
Full Answer
How do I configure external access policy in Lync Server?
In the left navigation bar, click Users, and then search on the user account that you want to configure. In the table that lists the search results, click the user account, click Edit, and then click Show details. In Edit Lync Server User under External access policy, select the user policy that you want to apply.
How do I configure SIP Federation in Lync Server?
If a user has been enabled for Lync Server, you can configure SIP federation, XMPP federation, remote user access, and public instant messaging (IM) connectivity in the Lync Server Control Panel by applying the appropriate policies to specific users.
What is a remote access policy?
A remote access policy is a written document containing the guidelines for connecting to an organization’s network from outside the office.
What are the requirements for remote access to company information?
Remote users must be required to authenticate before being granted access to company information. Remote access must be logged in a central database and kept for a period of at least 30 days. Access logs must be reviewed regularly.

What is Lync Server policy?
This means that the closer the policy setting is to the object that the policy is affecting, the more influence it has on the object.
What is site policy?
Site policy You can create and configure one or more site policies to limit support for external user access to specific sites. The configuration in the site policy overrides the global policy, but only for the specific site covered by the site policy. For example, if you enable remote user access in the global policy, ...
What happens if you delete a global policy?
The global policy applies to all users in your organization, but site policies and user policies override the global policy. If you delete the global policy, you do not remove it. Instead, you reset it to the default setting. Site policy You can create and configure one or more site policies to limit support for external user access ...
What is global policy?
Global policy The global policy is created when you deploy your Edge Servers. By default, no external user access options are enabled in the global policy. To support external user access at the global level, you configure the global policy to support one or more types of external user access options. The global policy applies to all users in your ...
Can you configure external user access?
By default, there are no policies configured to support external user access, including remote user access, federated user access, even if you have already enabled external user access support for your organization. To control the use of external user access, you must configure one or more policies, specifying the type of external user access ...
What is external access policy?
External access policies determine whether or not your users can: 1) communicate with users who have Session Initiation Protocol (SIP) accounts with a federated organization; 2) communicate with users who have SIP accounts with a public instant messaging (IM) provider such as MSN; and, 3) access Skype for Business Server over the Internet, without having to log on to your internal network.
What command is used to apply external access policy to an OU?
Once we have the naming context of the Organizational Unit, we can pipe the Get-CSUser command with Grant-CSExternalAccessPolicy to apply the external access policy on the entire OU.
Can you use SIP federation in Lync?
If a user has been enabled for Lync Server, you can configure SIP federation, XMPP federation, remote user access, and public instant messaging (IM) connectivity in the Lync Server Control Panel by applying the appropriate policies to specific users. For example, if you created an external access policy and you are in a closed federation, you can allow or restrict users from collaborating and contacting external users of a federated domain using external access policies for the users.
What Is a Remote Access Policy?
For example, sales personnel can now use tablets and other mobile devices to connect remotely to their office networks while on client calls and bring up data that may be important for closing deals . Recent events have further boosted the number of remote workers to an estimated 42% of the US workforce.
How to ensure that you do not miss anything when updating your remote access policy?
To ensure that you do not miss anything when updating your remote access policy, consider your organizational, legal, contractual and regulatory obligations when you compile the list of policy requirements. After that, identify the procedural and technical controls required to fulfill the policy, making sure to reinforce or replace existing controls that have not been effective.
Why Is a Remote Access Policy Important?
If a remote access policy is not in place, such risky behavior could go on unmitigated, without the organization finding out about it until after the occurrence of a breach.
What is remote work?
Remote work has brought with it a few challenges, including potential computer and network security risks. There is a real need for guidelines surrounding remote access, along with other policies. A remote access policy serves as a guide for remote users connecting to the network. It extends the policies governing network and computer use in ...
Why is password policy important?
It helps ensure that only those users who need it are given network access, as long as their devices are also compliant with the guidelines. When implemented properly, it helps safeguard the network from potential security threats.
What are the considerations when formulating a remote access policy?
Other considerations when formulating a remote access policy include but are not limited to the following: Standardized hardware and software, including firewalls and antivirus/antimalware programs. Data and network encryption standards. Information security and confidentiality. Email usage.
Can you customize remote access policy?
Always ensure that your remote access policy is not an exact copy of another organization’s template; rather, you should customize it depending on your requirements. Otherwise, it might not be that useful for your organization.