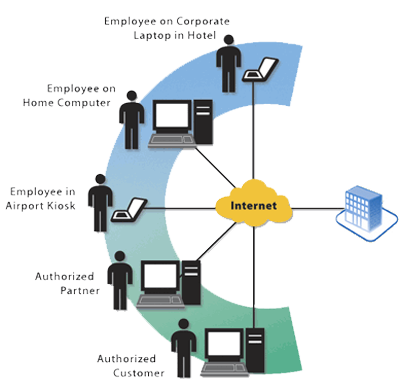
Managed Remote Access Services. RAS or Remote Access Services are provider-based solutions that enable Internet-capable devices to connect to the company’s IT infrastructure from remote locations. In a world where the workforce is becoming increasingly more mobile, the importance of establishing secure end-to-end communications while maintaining the safety and integrity of the corporate network is crucial.
Full Answer
How to setup remote access?
Once installed, you can now connect to remote endpoints by following the steps below:
- The software needs to be downloaded on both the local and remote computers.
- Open the software on both the local and remote computers.
- Write down the ITarian ID number and password of the remote computer.
- Click “Start Connection.”
- Enter the ID number and password of the remote computer.
- Click “Connect.”
How do I enable remote access in Windows 10?
Windows 10 Fall Creator Update (1709) or later
- On the device you want to connect to, select Start and then click the Settings icon on the left.
- Select the System group followed by the Remote Desktop item.
- Use the slider to enable Remote Desktop.
- It is also recommended to keep the PC awake and discoverable to facilitate connections. ...
Can someone help me with remote access?
Windows Remote Assistance lets someone you trust take over your PC and fix a problem from wherever they are. Before you can use it, you'll need to enable access. In the search box on the taskbar, type remote assistance, and then select Allow Remote Assistance invitations to be sent from this computer from the list of results.
Does Someone have remote access to my computer?
You can detect remote access on your computer by identifying the software programs currently in use and recognizing any abnormalities. If you have ever wondered "Is someone else controlling my computer," you are not alone.

How do I manage remote access?
7 Best Practices For Securing Remote Access for EmployeesDevelop a Cybersecurity Policy For Remote Workers. ... Choose a Remote Access Software. ... Use Encryption. ... Implement a Password Management Software. ... Apply Two-factor Authentication. ... Employ the Principle of Least Privilege. ... Create Employee Cybersecurity Training.
What are the different types of remote access methods?
The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), Point-to-Point Protocol over Ethernet (PPPoE), Point-to-Point Tunneling Protocol (PPTP), Remote Access Services (RAS), and Remote Desktop Protocol (RDP).
Is IIS required for RRAS?
RRAS: Features are managed in the Routing and Remote Access console. The Remote Access server role is dependent on the following features: - Web Server (IIS): Required to configure the network location server and default web probe.
What is remote secure access?
Secure Remote Access is a combination of security processes or solutions that are designed to prevent unauthorized access to an organization's digital assets and prevent the loss of sensitive data.
What are the three main types of remote connections?
Remote Access Control MethodsDirect (Physical) Line. The first direct remote access control that can be implemented is a direct line from a computer to the company's LAN. ... Virtual Private Network. Another method which is more common is establishing a VPN. ... Deploying Microsoft RDS.
What are the two types of remote access server?
Remote Access Methods1- Remote Access Server: It's one server in organization network that it is the destination of all remote access connections.2- Remote Access Client: All computers that remote connect to network, called remote access client or remote computer.More items...•
How do I setup an RRAS server?
Right-click the VPN server, then select Configure and Enable Routing and Remote Access. The Routing and Remote Access Server Setup Wizard opens. In the Welcome to the Routing and Remote Access Server Setup Wizard, select Next. In Configuration, select Custom Configuration, and then select Next.
What is Remote Access management tools?
RSAT enables IT administrators to remotely manage roles and features in Windows Server from a computer that is running Windows 10 and Windows 7 Service Pack 1.
What is the main purpose of a RAS server?
A remote access server (RAS) is a type of server that provides a suite of services to remotely connected users over a network or the Internet. It operates as a remote gateway or central server that connects remote users with an organization's internal local area network (LAN).
Why is remote access important?
Remote access enables remote users to access files and other system resources on any devices or servers that are connected to the network at any time. This increases employee productivity and enables employees to better collaborate with colleagues around the world.
Why is secure remote access important?
A secure remote access system protects your employees from web-based threats such as phishing attacks, ransomware and malware while they're logged in to your company's network. These cyber incidents can lead to unauthorized access and use of both the company's business data and the employee's personal data.
What are potential risks associated with remote access?
Five Remote Access Security Risks And How To Protect Against ThemWeak remote access policies. ... A deluge of new devices to protect. ... Lack of visibility into remote user activity. ... Users mixing home and business passwords. ... Opportunistic phishing attempts.
What is remote access explain with example?
Remote access refers to the ability to access a computer, such as a home computer or an office network computer, from a remote location. This allows employees to work offsite, such as at home or in another location, while still having access to a distant computer or network, such as the office network.
What are remote devices?
Remote Device means any device acceptable to us from time to time that provides for the capture of images from Items and for transmission through the clearing process.
Which devices can access remotely in networking?
Remote access gateway devices can be computers running remote access software and connected through multiport serial boards with 4, 8, 12, or more asynchronous communication ports that are connected to analog modem banks or ISDN terminal adapters, or they can be routers with built-in modem or Integrated Services ...
Which type of cable is used for remote access?
coaxial cable1.1) Accessing the Internet through a cable network is a popular option that teleworkers use to access their enterprise network. The cable system uses a coaxial cable that carries radio frequency (RF) signals across the network. Coaxial cable is the primary medium used to build cable TV systems.
Rapid scalability
Get users up and running quickly for rapid time-to-value and enhance business continuity.
Greater ROI
Our flexible, subscription-based pricing allows you to reduce costs by paying only for what you need.
Seamless user experience
Always-on connectivity and security provide end users with a great experience regardless of location.
Highly available, secure network access
Provide users with highly secure access to corporate resources from any location or device. Our service autodetects trusted networks and disconnections, automatically enforcing appropriate policies and remedies where needed.
Trusted security across Mac, Windows, iOS, and Android devices
Enjoy greater flexibility when bringing personal devices to the corporate network—without compromising security.
Cloud-based, scalable architecture
Our service is built on a cloud-based, highly available infrastructure that provides scalable remote access to get users up and running quickly.
Always-on service monitoring, performance metrics, and alerts
Cisco provides 24x7x365 monitoring of infrastructure, including continuous device health, performance metrics, and alerting.
What is Cisco Secure Managed Remote Access?
Cisco Secure Managed Remote Access is a scalable cloud service delivering on-demand, secure remote connectivity for your organization. It is managed by Cisco and enables you to rapidly scale up and provide your workforce with access to corporate resources from any location. Flexible, OpEx-based subscription pricing allows you to reduce your costs by paying only for what you need. The service is currently available in the United States, with global expansion to follow. It provides outcomes-based management and monitoring, ensuring uptime and reliable service.
How has the shift to remote work changed organizations?
The shift to remote work has changed organizations’ IT and security needs and expectations. The demand for anytime, anywhere access is unprecedented. Users are accessing sensitive corporate resources across their data centers, private cloud, and public cloud applications from multiple devices and locations. Companies recognize that remote work is here to stay, creating new network and security demands.
Why is remote work important?
Remote work has often shifted the focus of IT teams to ensure their workforce has secure remote access. To enable business continuity and growth, organizations must be able to respond to changes quickly and deliver consistent, secure remote access to workers everywhere.
What is single sign on portal?
Single sign-on service portal provides an integrated dashboard for service monitoring and incident management.
TOP RATED PROTECTION
PCH offers business continuity and disaster recovery services to ensure that your business experiences no downtime if data loss occurs.
ADVANCED SECURITY
At PCH, we have the ability to eliminate your need for an in-house IT staff by handling all of your information technology support remotely.
INDUSTRY EXPERTS
We have the experience and the resources to identify and solve your IT-related problems. That’s what IT consulting is—both simple and powerful.
Managed Remote Access Solutions
More and more companies are adopting work from home models to minimize office expenses and to grow their companies quicker. There are tons of benefits to working from home. Employees tend to be happier without having a commute and less reluctant to put in extra time when it’s needed.
Remote Solutions For The Mobile Workforce
A robust solution can be created for the exact needs of your company. You may find that you need different levels of access an security for various roles within your business workflow. All of this can be configured while enforcing the highest security protocols, encryption and VPN technology.
Keeping It Secure
Many business owners find that even keeping a small pool of computers secure and up to date against the latest threats with virus scanners, hotfixes, patches and other updates can be a tiring and complicated job. By leveraging security vendors, your managed solution can take advantage of bulletproof security measures that are already in place.
Where To Begin
Are you ready to expand your business and availability, while at the same time making your employees happy by giving them more flexibility?
