
When using Hybrid Authentication mode for IKE (Hybrid Authentication), IKEv1 phase 1 is used to authenticate the VPN gateway only (using either RSA or DSA digital signature authentication). This is a modification to the regular IKEv1 phase 1, which is designed to authenticate both IPsec peers (both the VPN gateway and the VPN client).
What is an IPSec VPN?
What is an IPsec VPN? A virtual private network (VPN) is an encrypted connection between two or more computers. VPN connections take place over public networks, but the data exchanged over the VPN is still private because it is encrypted.
What is IPsec protocol used for?
IPsec is a group of networking protocols used for setting up secure encrypted connections, such as VPNs, across publicly shared networks.
What is the difference between IPsec and Internet Key Exchange?
One of the most common SA protocols is Internet Key Exchange (IKE). Finally, while the Internet Protocol (IP) is not part of the IPsec suite, IPsec runs directly on top of IP. What is the difference between IPsec tunnel mode and IPsec transport mode?
How does IPSec traffic travel across networks?
Transmission: Encrypted IPsec packets travel across one or more networks to their destination using a transport protocol. At this stage, IPsec traffic differs from regular IP traffic in that it most often uses UDP as its transport protocol, rather than TCP.
What is IPsec IKEv1?
In computing, Internet Key Exchange (IKE, sometimes IKEv1 or IKEv2, depending on version) is the protocol used to set up a security association (SA) in the IPsec protocol suite.
What is IPsec remote access VPN?
Internet Protocol Security (IPsec) is a suite of protocols that support cryptographically secure communication at the IP layer. With IPsec connections, you can provide secure access between two hosts, two sites, or remote users and a LAN. The firewall supports IPsec as defined in RFC 4301.
What is IPsec IKE IKEv1 or IKEv2 VPN tunnel?
Internet Key Exchange version 2 (IKEv2) is an IPsec based tunneling protocol that provides a secure VPN communication channel between peer VPN devices and defines negotiation and authentication for IPsec security associations (SAs) in a protected manner.
How does IKEv1 work?
IKE provides a way to manage the key exchange, authenticate the peers and agree on a policy securely. IKE uses a protocol called ISAKMP to negotiate IPSec parameters between two peers. ISAKMP communicates on UDP port 500. This transport is fixed for UDP/500 on both the source and destination port of the packet.
What is the difference between VPN and IPSec?
SSL VPNs. The major difference between an IPsec VPN and an SSL VPN comes down to the network layers at which encryption and authentication are performed. IPsec operates at the network layer and can be used to encrypt data being sent between any systems that can be identified by IP addresses.
What are the 3 protocols used in IPSec?
IPsec is a suite of protocols widely used to secure connections over the internet. The three main protocols comprising IPsec are: Authentication Header (AH), Encapsulating Security Payload (ESP), and Internet Key Exchange (IKE).
Should I use IKEv1 or IKEv2?
IKEv2 is better than IKEv1. IKEv2 supports more features and is faster and more secure than IKEv1. IKEv2 uses leading encryption algorithms and high-end ciphers such as AES and ChaCha20, making it more secure than IKEv1. Its support for NAT-T and MOBIKE also makes it faster and more reliable than its predecessor.
Which is better IKEv2 or IPsec?
IPSec is considered secure and reliable, while IKEv2 is extremely fast and stable – IKEV2 offers quick re-connections when switching networks or during sudden drops. Thus, a combination of IKEv2/IPsec forms one of the best VPN protocols that exhibits the advantages of the two.
Whats the difference between IKEv1 and IKEv2?
IKEv2 uses four messages; IKEv1 uses either six messages (in the main mode) or three messages (in aggressive mode). IKEv2 has Built-in NAT-T functionality which improves compatibility between vendors. IKEv2 supports EAP authentication. IKEv2 has the Keep Alive option enabled as default.
Is IKEv1 secure?
The researchers found that IKEv1 is vulnerable to Bleichenbacher oracle attacks, a cryptographic attack technique that has been known for almost two decades. A Bleichenbacher attack involves sending modified ciphertext to a device and obtaining information about its unencrypted value based on the device's response.
What is Phase 1 and 2 IPsec VPN?
VPN negotiations happen in two distinct phases: Phase 1 and Phase 2. The main purpose of Phase 1 is to set up a secure encrypted channel through which the two peers can negotiate Phase 2. When Phase 1 finishes successfully, the peers quickly move on to Phase 2 negotiations.
How secure is IPsec?
IPsec enables secure, two-way communication over private—and even public—networks, including public WiFi networks and the broader internet. IPsec effectively scrambles all information in transit, using an algorithm that allows only authorized recipients to decrypt.
Can IPSec be used for remote access?
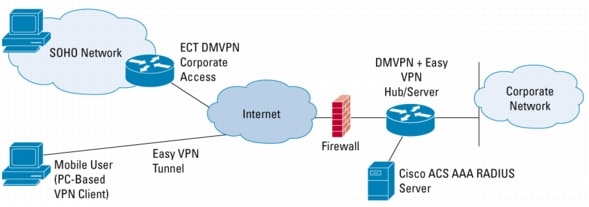
IPSec remote access is used to connect remote-access clients, such as a PC or small office, home office (SOHO) device (a small-end router or firewall appliance) to a corporate network.
What is the difference between IPSec and SSL VPN?
While an IPsec VPN allows users to connect remotely to an entire network and all its applications, SSL VPNs give users remote tunneling access to a specific system or application on the network. Choosing the right application comes down to a balance of convenience for the end-user and security for the organization.
Is IPSec VPN secure?
IPsec enables secure, two-way communication over private—and even public—networks, including public WiFi networks and the broader internet. IPsec effectively scrambles all information in transit, using an algorithm that allows only authorized recipients to decrypt.
Which is better IPSec or OpenVPN?
In site-to-site connections, OpenVPN functions faster and provides more security than IPsec. IPsec encryption operates on a kernel level, whereas OpenVPN functions in user space. Therefore, in terms of endpoint performance, IPsec is more favorable. With OpenVPN, you're limited to the capacity of the software.
What is a VPN? What is an IPsec VPN?
A virtual private network (VPN) is an encrypted connection between two or more computers. VPN connections take place over public networks, but the data exchanged over the VPN is still private because it is encrypted.
How do users connect to an IPsec VPN?
Users can access an IPsec VPN by logging into a VPN application, or "client." This typically requires the user to have installed the application on their device.
What is IPsec?
IPsec is a group of protocols that are used together to set up encrypted connections between devices. It helps keep data sent over public networks secure. IPsec is often used to set up VPNs, and it works by encrypting IP packets, along with authenticating the source where the packets come from.
What is the difference between IPsec tunnel mode and IPsec transport mode?
In IPsec tunnel mode, the original IP header containing the final destination of the packet is encrypted, in addition to the packet payload. To tell intermediary routers where to forward the packets, IPsec adds a new IP header. At each end of the tunnel, the routers decrypt the IP headers to deliver the packets to their destinations.
What port does IPsec use?
IPsec usually uses port 500.
How does IPsec impact MSS and MTU?
Packets can only reach a certain size (measured in bytes) before computers, routers, and switches cannot handle them. MSS measures the size of each packet's payload, while MTU measures the entire packet, including headers. Packets that exceed a network's MTU may be fragmented, meaning broken up into smaller packets and then reassembled. Packets that exceed the MSS are simply dropped.
How does IPsec work?
To tell intermediary routers where to forward the packets, IPsec adds a new IP header. At each end of the tunnel, the routers decrypt the IP headers to deliver the packets to their destinations. In transport mode, the payload of each packet is encrypted, but the original IP header is not.
What is IKEv2 used for?
The current best practice is to use IKEv2 for IPsec Remote Access on modern clients. See IPsec Remote Access VPN Example Using IKEv2 with EAP-MSCHAPv2 for details.
How to refresh IPsec?
In the pfSense webGUI, go to Status > System Logs and there to the IPsec tab. Hit the Clear log button, have the client try and start the connection and click the IPsec tab again to refresh the page. This is usually very inspiring.
How to enter IP address in Shrew Soft VPN?
On the General tab, enter the IP address or host name pfSense firewall. Leave the rest as it is. The default values in new versions of the Shrew Soft VPN client may change so in case of doubt, stick to the screenshots.
Why does Shrew Soft VPN want to know my password?
If a user calls and says Shrew Soft VPN wants to know his user name and password, it’s almost always because the user has either no Internet connection or no dns service. Or they are on a guest network and need to open their browser for identification or something.
How to backup VPN tunnel?
Backup the tunnel profile by selecting it in the VPN Access Manager and going to File > Export. Restoring works by choosing Import.
How to set up mutual PSK?
Under Local Identity, choose Key Identifier as the Identification Type and enter the user’s e-mail address (or whatever was used as an identifier) in the Key ID String field.
Can you change name resolution in PfSense?
Don’t change anything on the Name Resolution tab; these settings are all automatically set by the pfSense software. Relevant information could be entered here but if the settings were configured on the firewall, they need not be set here.
What is the order of preference in BGP?
Order of preference of attributes in BGP The order of preference varies based on whether the attributes are applied for inbound updates or outbound updates. For inbound updates the order of preference is: route-map filter-list prefix-list, distribute-list For outbound updates the order of preference is: prefix-list, distribute-list filter-list route-map NOTE: The attributes prefix-list and distribute-list are mutually exclusive, and only one command (neighbor distribute-list or neighbor prefix-list) can be applied to each inbound or outbound direction for a particular neighbor. Scenario: We own the AS500 and advertising a network block of 192.0.2.0/24 and 180.179.179.0/16 to two different ISPs.
What is Cisco AnyConnect Secure Mobility Solution?
The Cisco AnyConnect Secure Mobility Solution provides a comprehensive, highly secure enterprise mobility solution. the Cisco AnyConnect Secure Mobility Solution continues to lead with next-generation security and encryption, including support for the Suite B set of cryptographic algorithms, and support for IPv6 networks. More importantly, it adapts its tunneling protocol to the most efficient method. In the present scenario, we have to configure Anyconnect SSL remote access VPN for Sales department and Engineering department of a company. Engineering users will have to be provided with access to web server as well as FTP server, while sales users may only have access to the web server.
Does Cisco AnyConnect support SSL VPN?
Even after the release of Cisco AnyConnect Secure Mobility Client which supports SSL VPN in addition to IKEv2 remote-access IPSec VPN, still out there are number of people who use legacy Cisco VPN client to connect IKEv1 remote-access IPSec VPN.
Does VPN work without transparent tunneling?
Connections through the VPN do not work as were connecting through PAT without Transparent Tunneling
Does NATed VPN need UDP?
Connections from the VPN Client work normally. Even though the Staticly NATed VPN Client host doesnt need the UDP encapsulation it still used if your VPN Client connection profile is configured to use it (In the Transport tab of the client software) Connections from the VPN Client work normally.

Introduction
- This document describes the Internet Key Exchange (IKEv1) protocol process for a Virtual Private Network (VPN) establishment in order to understand the packet exchange for simpler troubleshoot for any kind of Internet Protocol Security (IPsec) issue with IKEv1. Contributed by A…
Prerequisites
- Requirements
Cisco recommends that you have knowledge of basic security concepts: 1. Authentication 2. Confidentiality 3. Integrity 4. IPsec
Quick Mode
- Quick mode occurs after the Main monde and the IKE has established the secure tunnel in phase 1. Quick Mode negotiates the shared IPSec policy, for the IPSec security algorithms and manages the key exchange for the IPSec SA establishment. The nonces are used to generate new shared secret key material and prevent replay attacks from bogus SAs generated. Three packets are ex…
Ikev2 vs IKEv1 Packet Exchange
- In the IKEv2 negotiation, fewer messages are exchanged to establish a tunnel. IKEv2 uses four messages; IKEv1 uses either six messages (in the main mode) or three messages (in aggressive mode). The IKEv2 message types are defined as Request and Response pairs. The image shows the packets comparison and payload content of IKEv2 versus IKEv1.
Related Information