Full Answer
How do I configure a firewall to allow remote access to memcached?
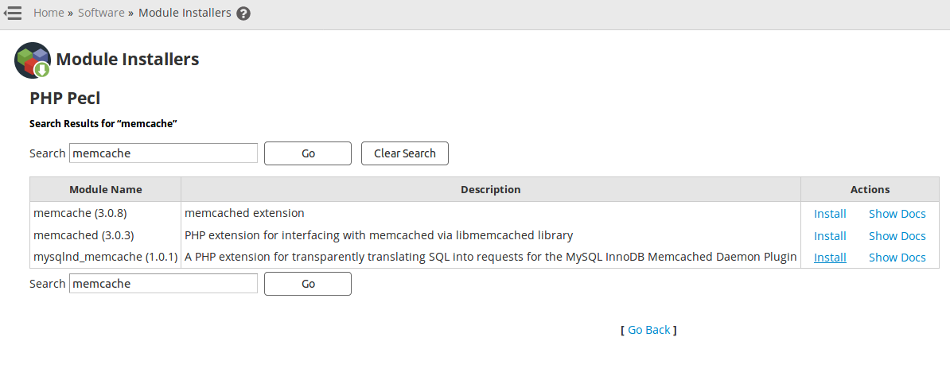
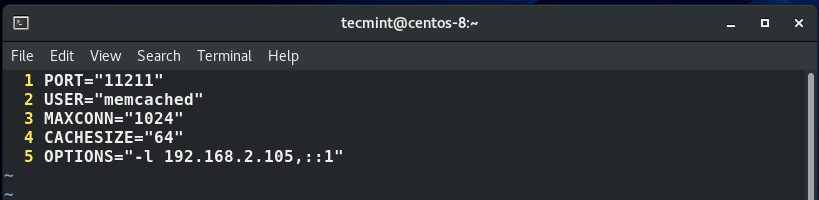
If you do require the use of UDP and require remote access to memcached servers (for example, in a clustering scenario), it is recommended to configure a firewall to allow connections only from trusted hosts. To configure memcached, edit the file /etc/sysconfig/memcached as follows
How to make a connection to memcached using telnet?
To make a connection to Memcached using Telnet, use the following command: [jcollins@redhat memcached]$ telnet localhost 11211 Trying 127.0.0.1... Connected to localhost. Escape character is '^]'.
Do I need to use UDP for Memcached?
Do not allow external traffic to ports used by memcached (e.g. 11211 as used by default). If you are not required to use UDP for memcached, we highly recomment switching to TCP connections for your memcached server (add "-U 0" to the OPTIONS variable in /etc/sysconfig/memcached).
How can I protect my network from Memcached traffic?
First and foremost, set up a firewall in your LAN if memcached servers should be accessible only from within your local network. Do not allow external traffic to ports used by memcached (e.g. 11211 as used by default).
How do I connect to Memcached?
Connecting to a Memcached instance from a Google Kubernetes Engine clusterGo to the Google Kubernetes Engine page in the GCP Console. ... Click on the GKE cluster you'd like to connect from. ... Click the Connect button to the right of your cluster's name, then click the Run in Cloud Shell button in the window that appears.More items...
Does Memcached have authentication?
Memcached now supports SASL. This will allow you to perform strong authentication for your memchaced service.
How do I view Memcached connections?
By running this command, we can see the port where Memcached is running:ps -eaf | grep memcached.# structure telnet hostname/ip port # example telnet 127.0.0.1 11211 telnet localhost 11211.More items...•
How do I enable SASL in Memcached?
In order to enable SASL support in the server you must use the -S flag....Running MemcachedEnable all of the SASL commands.Require binary protocol only.Require authentication to have been successful before commands may be issued on a connection.
Is Memcached secure?
By default, Memcached is not protected by authentication. If the server is accessible, anyone can access the data stored on it. For this reason, it is highly important that you secure this database.
How do I authenticate Redis?
When the authorization layer is enabled, Redis will refuse any query by unauthenticated clients. A client can authenticate itself by sending the AUTH command followed by the password. The password is set by the system administrator in clear text inside the redis. conf file.
How many connections can memcached handle?
Specify the maximum number of simultaneous connections to the memcached service. The default is 1024. Use this option, either to reduce the number of connections (to prevent overloading memcached service) or to increase the number to make more effective use of the server running memcached server.
How do I monitor memcache?
Using memcstat. Installing the libmemcached-tools package will give you access to the memcstat command, which displays the operating status of a single or group of memcached servers. Usage is very simple. Once again we've filtered stats out to retrieve memcached HITS only.
What is the difference between Memcache and memcached?
They both have very basic difference while storing value. Memcache mostly considers every value as string whereas Memcached stores it value's original type. Thumbs up for your answer !
What does Sasl stand for?
Simple Authentication and Security LayerSimple Authentication and Security Layer (SASL) is a framework for authentication and data security in Internet protocols.
What port does Memcached use?
port 11211/tcpMemcached is an open-source distributed memory object caching system which is generic in nature but often used for speeding up dynamic web applications. In the default configuration, memcached listens on port 11211/tcp and (up to including version 1.5. 5) also on port 11211/udp.
Can we run multiple Memcached processes in single instance?
You can run multiple instances of Memcached server through a single installation.
What is the default memory pool of Memcached?
For example, the default allocation of memory to memcached on a web server is 64M.
Which file contains the configuration of Memached?
These properties control Memcached settings, and are set in the memcached-config. xml file in the /WEB-INF/classes/ directory inside of your deployed pentaho.
What is Memcached?
Memcached is an easy-to-use, high-performance, in-memory data store. It offers a mature, scalable, open-source solution for delivering sub-millisecond response times making it useful as a cache or session store. Memcached is a popular choice for powering real-time applications in Web, Mobile Apps, Gaming, Ad-Tech, and E-Commerce.
How does Memcached work?
Unlike databases that store data on disk or SSDs, Memcached keeps its data in memory. By eliminating the need to access disks, in-memory key-value stores such as Memcached avoid seek time delays and can access data in microseconds. Memcached is also distributed, meaning that it is easy to scale out by adding new nodes.
Benefits of Memcached
Memcached keeps all of its data in the server’s main memory. Unlike databases such as PostgreSQL, Cassandra, and MongoDB which store most of their data on disk or SSDs, in-memory data stores don’t have to make repeated round trips to disk. This allows them to support an order of magnitude more operations and faster response times.
Popular Memcached Use Cases
Memcached is a great choice for implementing a high performance in-memory cache to decrease data access latency, increase throughput, and ease the load off your back-end systems. Memcached can serve cached items in less than a millisecond, and enables you to easily and cost effectively scale for higher loads.
Language support
Memcached supports most leading programming languages and protocols, including:
Redis vs. Memcached
Redis and Memcached are the two most popular in-memory key-value data stores. Memcached is designed for simplicity while Redis offers a rich set of features that make it effective for a wide range of use cases. Understand the differences between the two engines to decide which solution better meets your needs. Learn more about Redis vs. Memcached »
What is the best way to access a memcached server?
There are many web and GUI interfaces available for accessing Memcached server instances, my personal favourite is phpMemCacheAdmin . Sometimes however you may need to access a Memcached instance from the command line.
How does memcached work?
So Memcached allocates your data into different "slabs" (think of these as partitions) of memory automatically, based on the size of your data, which in turn makes memory allocation more optimal.
What information is returned in Memcached?
Some useful information is returned, such as the uptime for the server, the version of Memcached installed, the total number of items in the cache, and the amount of client connections to the instance.
How to terminate telnet session?
If at any time you wish to terminate the Telnet session, simply type "quit" and hit return:
Is Memcached a good application?
Memcached is an amazing piece of software in terms of its many potential applications to increase web application performance. While powerful, it is simple to use and configure, and I find the API very intuitive. I am looking forward to using it on a many projects in the future.
What is the default interface for memcached?
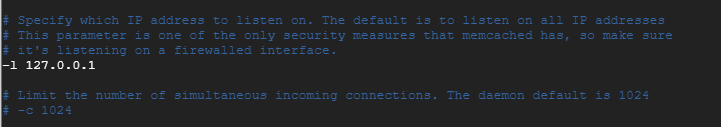
By default, Ubuntu and Debian bind Memcached to the local interface 127.0.0.1. Installation s bound to 127.0.0.1 are not vulnerable to amplification attacks from the network. Check that the -l option is set to this address to confirm the behavior:
What address is memcached bound to?
You should see memcached bound to the 127.0.0.1 address using only TCP.
How to mitigate a memcached attack?
In order to mitigate the attack, the best option is to bind Memcached to a local interface, disable UDP, and protect your server with conventional network security best practices. In this guide, we will cover how to do this, as well as how to expose the service to selective external clients.
What is memcached amplification?
Memcached, a popular object caching system, is frequently used to reduce response times and the load on components throughout a deployment. The amplification attack targets Memcached deployments exposed on the public network using UDP.
Why test connectivity from external client?
Test connectivity from your external client to ensure that you can still reach the service. It is a good idea to also check access from a non-authorized client to ensure that your firewall rules are effective.
Can you use memcached to block unauthorized requests?
For additional security, if you need Memcached access between Droplets within the same data center, binding to your Droplet’s private network interface and using firewall rules to limit the source addresses allowed will help prevent unauthorized requests.
Can Memcached bind to private network?
Afterwards, you can adjust the Memcached service to bind to your server’s private networking interface.
How to use memcached with a domain?
If you would like to use Memcached with Unix Domain Sockets, you can enable this support by editing the /etc/memcached.conf configuration file. Note that if you configure Memcached to use a Unix Domain Socket, Memcached will disable TCP and UDP support so be sure that your applications do not need to connect using those protocols before enabling socket support.
How does Memcached help with database performance?
Memory object caching systems like Memcached can optimize back end database performance by temporarily storing information in memory, retaining frequently or recently requested records. In this way, they reduce the number of direct requests to your databases.
What is the default loopback for memcached?
By default Memcached is only configured to listen on the local loopback ( 127.0.0.1) interface, which protects the Memcached interface from exposure to outside parties. However, there may be instances where you will need to allow access from other servers. In this case, you can adjust your configuration settings to bind Memcached to a private network interface.
What is libmemcached-tools?
You can also install libmemcached-tools, which is a package that contains various tools that you can use to examine, test, and manage your Memcached server. Add the package to your server with the following command:
How to enable UDP support in Memcached?
If you would like to use Memcached with UDP sockets, you can enable UDP support by editing the /etc/memcached.conf configuration file.
How to close a file in Memcached?
Save and close the file by pressing CTRL+O then ENTER to save, then CTRL+X to exit nano. Then restart Memcached using the systemctl command:
Can you limit access to a Memcached instance?
If you are using the UFW firewall, you can limit access to your Memcached instance by typing the following on your Memcached server: