These are the primary remote access protocols that are in use today: Serial Line Internet Protocol (SLIP) Point-to-Point Protocol (PPP) and Point-to-Point Protocol over Ethernet (PPPoE
Point-to-point protocol over Ethernet
The Point-to-Point Protocol over Ethernet is a network protocol for encapsulating PPP frames inside Ethernet frames. It appeared in 1999, in the context of the boom of DSL as the solution for tunneling packets over the DSL connection to the ISP's IP network, and from there to the rest of the Internet. A 2005 networking book noted that "Most DSL providers use PPPoE, which provides authentication, encr…
- PPP. Point-to-Point Protocol is used to create dial-up connections between a dial-up client and a remote access server, or between a dial-up client and an Internet Service Provider (ISP).
- IPsec. ...
- PPTP. ...
- L2TP. ...
- RADIUS. ...
- TACACS/XTACACS. ...
- TACACS+.
How to properly secure remote access?
- Windows or Mac login when connecting remotely
- Request permission to connect to the user’s computer
- Automatically blank the remote screen when connected
- Automatically lock remote computer when disconnected
- Lock the remote computer’s keyboard and mouse while in session
- Lock the streamer settings using Splashtop admin credentials
What is the best remote access for PC?
What is the Best Remote Desktop Software?
- GoToMyPC. GoToMyPC is the best remote desktop software on this list. ...
- AnyDesk. AnyDesk is one of the most popular remote desktop software platforms, used by over 100 million users globally.
- LogMeIn. ...
- Parallels. ...
- Splashtop Business Access. ...
- Zoho Assist. ...
- ConnectWise Control. ...
- RemotePC. ...
- TeamViewer. ...
- Remote Utilities for Windows. ...
How do you connect to your computer remotely?
To set up it:
- Go to Menu > System Preferences > Sharing
- Select Remote Management - it should appear as a checkbox.
- Now you can select who has remote desktop access. Either select, All Users, which means any other device on your network, or Mac you own, can access and connect, or ...
How to enable remote access for remote management?
To set up remote management:
- Launch a web browser from a computer or mobile device that is connected to your router’s network.
- Enter http://www.routerlogin.net. ...
- Enter the router user name and password. ...
- Select ADVANCED > Advanced Setup > Remote Management. ...
- Select the Turn Remote Management On check box.
What protocols are used in remote access?
The primary remote access protocols in use today are the Serial Line Internet Protocol (SLIP), Point-to-Point Protocol (PPP), Point-to-Point Protocol over Ethernet (PPPoE), Point-to-Point Tunneling Protocol (PPTP), Remote Access Services (RAS), and Remote Desktop Protocol (RDP).
How do I access a network remotely?
Today, remote access is more commonly accomplished using: Software: Using a secure software solution like a VPN. Hardware: By connecting hosts through a hard-wired network interface or Wi-Fi network interface. Network: By connecting via the internet.
What protocol is used for secure remote connectivity for configuration?
Remote Desktop Protocol or RDP is a communications protocol designed to manage remote access to desktops, files, systems, and even private networks.
Which of the following protocol is used to remote login?
Notes: Telnet is a protocol used to log in to remote computers. terminals over the Internet or a TCP/IP computer network.
Which of the following protocols provide access to a remote host?
DNS is important because it can quickly provide users with information, as well as access to remote hosts and resources across the internet. Dynamic Host Configuration Protocol.
Which TCP IP protocol is used for remote connection?
TELNETOverview of TCP/IPTELNETa remote terminal connection service that supports remote login.FTPa File Transfer Protocol that transfers files from one machine to another.X11a graphical user interface that can operate in a network environment. This protocol is not limited to TCP/IP.1 more row
Which protocol facilitates remote login on a computer?
The correct answer is Telnet. Any application that empowers users to remotely access another computer(no matter how far away) is called remote access. Telnet is an application protocol that uses a virtual terminal connection to offer bidirectional interactive text-oriented communication over the Internet.
Can I log into my router away from home?
When you want to access your router from inside the network; all you have to do is type in the router's IP address in the web browser. Similarly, to access your router from outside, you need to type in your public IP address followed by remote control port no i.e. 8080.
How do I connect to a network in a different location?
What you need is a Branch Office VPN(Virtual Private Network). A VPN is a method of connecting two separate networks securely through the internet using shared credentials. This technology is installed on your routers/firewals, and knows the internal network range and external IP address of the other router.
How do I connect to Wi-Fi from far away?
If you want to connect to your neighbor's wifi, which is a mile away, then the only way to get free internet from that far away is to have a directional antenna with a line of sight, or in layman terms, no barriers in between.
What is remote access protocol?
A remote access protocol manages the connection between a remote computer and a remote access server. These are the primary remote access protocols that are in use today:
What is PPP protocol?
Point-to-Point Protocol (PPP) PPP is used to implement TCP/IP over point-to-point connections (for example, serial and parallel connections). It is most commonly used for remote connections to ISPs and LANs. PPP uses the Link Control Protocol (LCP) to communicate between PPP client and host. LCP tests the link between client and PPP host ...
How to use PPTP?
To use PPTP, you set up a PPP session between the client and server, typically over the Internet. Once the session is established, you create a second dial-up session that dials through the existing PPP session, using PPTP. The PPTP session tunnels through the existing PPP connection , creating a secure session.
How does PPTP work?
PPTP is both simple and secure. To use PPTP, you set up a PPP session between the client and server, typically over the Internet.
How to dial into a modem?
Type the name of the system you will be dialing into in the Type a Name for the Computer You Are Dialing field. This field defaults to My Connection. Select the modem installed in your computer that you want to use for this connection from the Select a Device dropdown list.
What is DHCP used for?
DHCP is the protocol within the TCP/IP protocol stack that is used to assign TCP/IP addressing information, including host IP address, subnet mask, and DNS configuration. This information can be assigned over a LAN connection or a dial-up connection.
What is SLIP in networking?
Serial Line Internet Protocol (SLIP) In 1984, students at the University of California at Berkeley developed SLIP for Unix as a way to transmit TCP/IP over serial connections (such as modem connections over POTS). SLIP operates at both the Physical and Data Link layers of the OSI model. Today, SLIP is found in many network operating systems in ...
Remote Access Protocols and Services
Today, there are many ways to establish remote access into networks. Some of these include such things as virtual private networks (VPNs) or plain old modem dial-up access. Regardless of the technique used for remote access or the speed at which access is achieved, certain technologies need to be in place in order for the magic to happen.
Remote Access Service (RAS)
RAS is a remote access solution included with Windows Server products. RAS is a feature-rich, easy-to-configure, and easy-to-use method of configuring remote access.
What is the best way to make sure RDP is working?
The first and most effective recommendation is to make sure that both your local workstation and destination server are current on their Windows updates. There have been a considerable number of vulnerabilities discovered over the years in regard to RDP, and these have been addressed regularly through Windows updates.
What is RDS gateway?
Similar to the recommendation above regarding using SSL/TLS to secure the connection to a remote server, a Remote Desktop Services (RDS) gateway allows for a similar method to be used via a standard online portal. This provides a central access location that users can RDP from to a large number of target servers, as well as the use of remote apps. In addition to permitting access in a secure manner, this also allows for logging of legitimate users as well as potential brute-force attack attempts.
What is a VPN connection?
If you need more than just RDP access or require more than what just one RDS gateway will allow, then a Virtual Private Network (VPN) connection may be just what you require. These access methods are highly secure and allow for any supported device to communicate as if it were directly attached to your network.
What is the default port for RDP?
The default port for RDP traffic is TCP 3389, and anyone scanning the network deliberately for this port will be able to quickly find any number of servers listening. Changing this port to something less obvious would be tremendously helpful, but can take a considerable amount of time to initially set up.
Can you connect to a server remotely?
There are dozens of different ways to connect remotely to server s, but the recommended method for quite some time has been through the use of remote desktop connections. Unfortunately, while the use of the Remote Desktop Protocol (RDP) is relatively well protected over short distances, it can be vulnerable to attacks if left unsecured on the web. Worse, it’s become an even more lucrative target to exploit with the recent increases in working from home.
Is RDP secure?
In addition, we want to make sure that our RDP sessions are using secure protocols to communicate to and from the servers. This is because while the RDP channel itself is encrypted, it is possible in older versions of RDP to leverage a vulnerability in order to allow unauthorized access via a man-in-the-middle attack. Therefore it is strongly recommended wherever possible to secure your connections via SSL/TLS.
Is it safe to leave your network exposed?
While it is certainly possible to leave your systems directly exposed on the internet and RDP in directly with no security at all, this is a very bad idea. Fortunately there are two very well-used and secure methods that can help to not only keep your network more secure but to log who is attempting to breach it.
Why is POTS a popular remote access connection method?
POTS is a popular remote access connection method because few minor disadvantages are associated with it. The disadvantages are limited bandwidth, and thus a limited maximum data transfer rate, and the inferior analog signal when compared to digital methods, such as ISDN and DSL.
Why is remote access not part of my network?
Because a computer using remote access is not a part of your network, it will not use local area network (LAN) technologies to connect to the network. The remote computer will instead use other kinds of connection methods to connect to the LAN, including the following: Other digital connection methods (including one of the digital subscriber lines, ...
How many channels are there in an ISDN line?
An ISDN line has two types of channels. The data is carried on special Bearer channels, or B channels, each of which can carry 64Kbps of data. A BRI ISDN line has two B channels. One channel can be used for a voice call while the other is being used for data transmissions, and this occurs through time division multiplexing on one pair of copper wires. The second type of channel is also multiplexed onto the one copper pair, is used for call setup and link management, and is known as the signaling channel, or D channel (also referred to as the Delta channel ). This channel has only 16Kbps of bandwidth.
How to connect a cable modem to a computer?
If you are going to connect the cable modem via USB, simply install the software driver for the cable modem on the computer, and then plug in the cable modem. The computer will detect the modem and configure it automatically.
What are the advantages of ISDN?
These are the main advantages of ISDN: 1 It has a fast connection. 2 It offers higher bandwidth than POTS. BONDING yields 128Kbps bandwidth. 3 There is no conversion from digital to analog.
Why is ISDN used?
Because it is capable of much higher data rates at a fairly low cost, ISDN is becoming a viable remote user connection method, especially for those who work out of their homes. ISDN uses the same UTP wiring as POTS, but it can transmit data at much higher speeds. But that’s where the similarity ends. What makes ISDN different from a regular POTS line is how it uses the copper wiring. Instead of carrying an analog (voice) signal, it carries digital signals. This is the source of several differences.
How to connect Ethernet to modem?
If you are using Ethernet to connect, you must have an Ethernet NIC in your computer that is properly installed and configured. Then, once the NIC is installed, all you need to do is connect the cable modem to the NIC with an appropriate 10Base-T patch cable (RJ-45 connector on both ends, usually supplied with the cable modem). The thing to keep in mind is that the cable modem’s Ethernet connection is physically and electronically the same as a medium dependent interface-crossover (MDI-X) port on a hub or switch, meaning that you can connect your computer, which has a medium dependent interface (MDI) to the cable modem with a straight-though cable.
What is remote access VPN?
VPN: VPN, short for Virtual Private Network, is a private network formed using public Internet.
What is IPSEC protocol?
IPSEC is the most widely used protocol in Virtual Private Networks (VPNs). IPsec provides Authentication Header (AH), which essentially allows authentication of the sender of data, and Encapsulating Security Payload (ESP), which supports both authentication of the sender and encryption of data as well.
What is SSL VPN?
Kerboros is an authentication system used to authenticate users that log on to the network. An SSL VPN is a form of VPN that can be used with a standard Web browser.
What is the unit of transmission in Layer 2?
In layer 2, the unit of transmission is known as frame. The Layer 2 Tunnel Protocol (L2TP) is a standard that combines the best features of Cisco's Layer 2 Forwarding (L2F) and Microsoft's Point-to-Point Tunneling Protocol (PPTP). L2TP does not provide information confidentiality by itself.
What is IPSEC used for?
IPSec is normally used in combination with L2Tp for providing confidentiality of communication. IPSEC: IPSEC stands for IP SECurity, is the protocol developed by IETF and supports secure exchange of packets at IP layer. When using IPSEC, the sending and receiving devices share a public key.
Why is VPN important?
A VPN provides a mechanism to access corporate networks safely using Internet. VPN uses encryption to ensure only authorized user can access the corporate resources. A secure tunnel is created through the public network through which ...
What is a VNC?
VNC (Virtual Network Computing): VNC is a technology for remote desktop sharing, a form of remote access on computer networks.
Types of Tunneling and Encryption
Tunneling involves using protocols to encapsulate or encrypt data packets so that will pass through the Internet in a secure fashion. Think of encapsulation and tunneling like peas in a pod. The peas are the data packets (unencrypted) and the pod encapsulates or encrypts the peas so they cannot be seen.
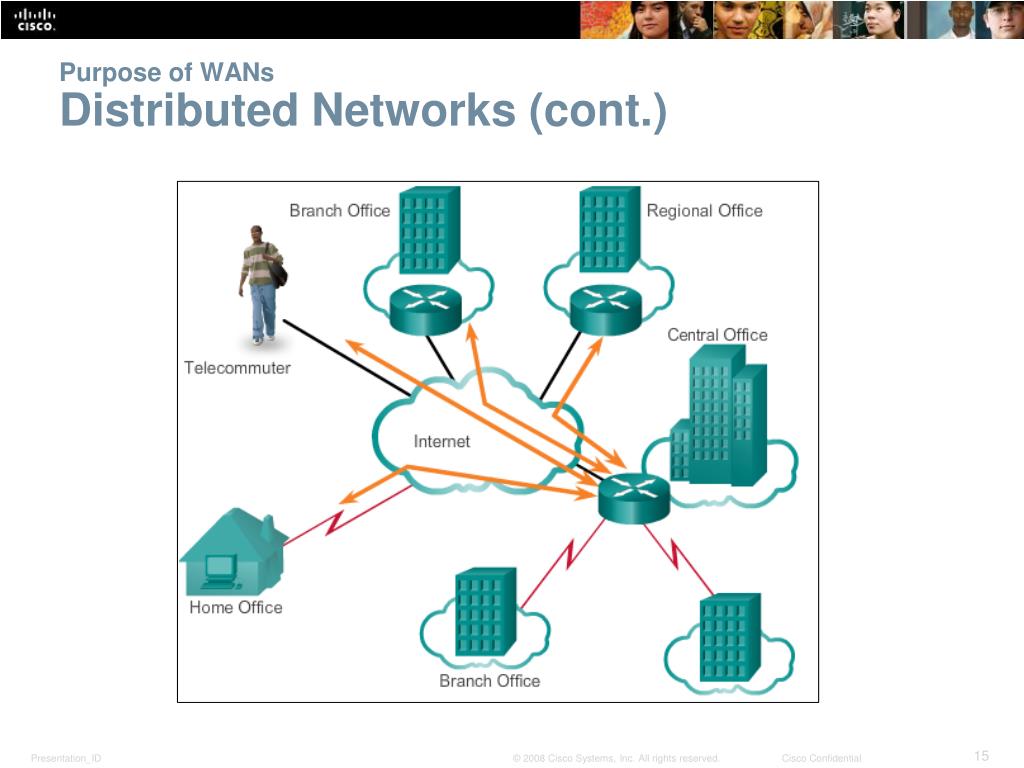
Remote Access
Here is a high level example (Figure 1) of how a remote host can connect to an internal corporate network which can be referred to when reviewing the types of remote access solutions: Remote Access Service (RAS), Point-to-Point over Ethernet (PPPoE), Remote Desktop Protocol (RDP), Independent Computing Architecture (ICA), and Secure Shell (SSH).
Network Intrusion & Protection
An Intrusion Detection System (IDS) and Intrusion Prevention System (IPS) are network security appliances that can be host-based, network-based or a combination of both.
Network Security Traps
A honeypot is a computer host that has been set up to attract hackers to learn what tactics they are using to infiltrate a network. It monitors their movements and gives a network administrator insight to where future attacks may come from.

Serial Line Internet Protocol (Slip)`
Point-To-Point Protocol
- PPP is a remote access protocol that allows you to implement TCP/IP. It establishes a connection via point-to-point links (i.e., dedicated leased lines and dial-up). PPP is used most often for remote connections to LANs and ISPs. PPP utilizes the Link Control Protocol (LCP), which tests the link between client and PPP host and specifies PPP client configuration, to communicate between h…
Windows Remote Access Services
- Windows 2000 and Windows NT let users dial up a server and connect to both the server and the server’s host network. This is referred to as RAS, which is used in smaller networks where a dedicated dial-up router would not be possible or practical. With a RAS setup, you can connect a modem to a Windows 2000 or Windows NT server and configure the modem as dial-out only, di…
Remote Desktop Protocol
- Finally, there is the RDP, which is very similar to the Independent Computing Architecture (ICA) protocol used by Citrix products. RDP is utilized to access Windows Terminal Services, which is a close relative of the product line provided by Citrix WinFrame. RDP offers the same core functions as ICA, although there are some limitations. RDP provides remote access for Windows clients o…
Serial Line Internet Protocol
Point-To-Point Protocol
Point-To-Point Tunneling Protocol
Windows Remote Access Services
Independent Computing Architecture (ICA) Protocol
- A relatively new technology for remote access is the Citrix WinFrame (or MetaFrame) products (including Windows Terminal Server), which use the ICA protocol. Put simply, Citrix WinFrame allows multiple computers to take control of a virtual computer and use it as if it were their desktop. The advantage is that a company can put all of its time and ...