
Apply MFA to Remote Desktop Web Access (RD Web Access)
- UserLock detects the servers where IIS is installed and can automatically deploy the UserLock IIS agent. The UserLock...
- The website settings are then configured to redirect the user to enroll for MFA if not already done, and challenge for...
Full Answer
What is most common for remote access?
The top RATs
- The hacker’s choice: FlawedAmmyy. When trying to identify which malware variant is the most effective, it’s useful to take a look at what hackers are actively using.
- Free and open-source: Quasar. For those who what a free and open-source RAT (to avoid potential backdoors), Quasar RAT is widely recommended.
- Mobile access (iOS): PhoneSpector. ...
How to enable remote access for remote management?
To set up remote management:
- Launch a web browser from a computer or mobile device that is connected to your router’s network.
- Enter http://www.routerlogin.net. ...
- Enter the router user name and password. ...
- Select ADVANCED > Advanced Setup > Remote Management. ...
- Select the Turn Remote Management On check box.
How to use remote access?
Windows 10 Fall Creator Update (1709) or later
- On the device you want to connect to, select Start and then click the Settings icon on the left.
- Select the System group followed by the Remote Desktop item.
- Use the slider to enable Remote Desktop.
- It is also recommended to keep the PC awake and discoverable to facilitate connections. ...
Is it safe to allow remote access to my machine?
Remote access is a useful tool to allow a trusted individual access to your computer for support or other purposes. The key is that you must know and trust the individual, just as you would if you handed the computer to them. NEVER allow remote access to someone whom you don’t know or who contacts you.
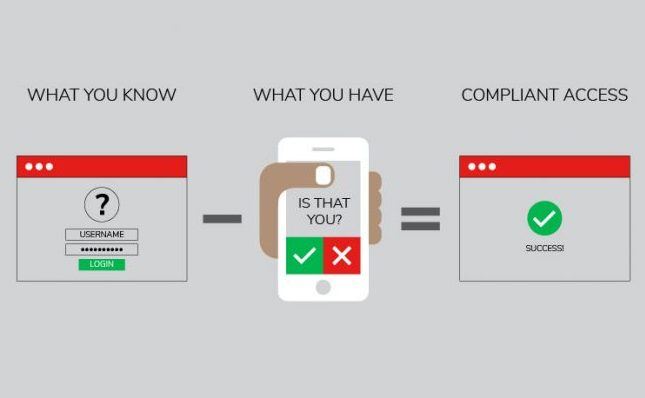
What is MFA remote access?
Multi-factor authentication (MFA) is a more secure access control procedure that combines multiple credentials unique to an individual to verify the user's identity.
Why is MFA important for remote access?
MFA provides an extra layer of security for remote workers. Instead of them working behind a locked door, they're working behind a locked door that also requires thumbprint analysis. MFA can protect your remote team against basic attacks like email phishing as well as more complex attacks.
Can you use MFA with RDP?
On the highest level, multi factor authentication can be added on top of RDP by using: A multi factor authentication vendor/product such as Duo Security, OKTA MFA, … and many more; Using an external Identity Provider (IdP) and the MFA services linked to this IdP.
What is MFA?
Multi-factor authentication is a layered approach to securing data and applications where a system requires a user to present a combination of two or more credentials to verify a user's identity for login.
When should MFA be used?
Why is MFA Important? The main benefit of MFA is it will enhance your organization's security by requiring your users to identify themselves by more than a username and password. While important, usernames and passwords are vulnerable to brute force attacks and can be stolen by third parties.
What is MFA and why do I need it?
MFA Enables Stronger Authentication With MFA, it's about granting access based on multiple weighted factors, thereby reducing the risks of compromised passwords. It adds another layer of protection from the kinds of damaging attacks that cost organizations millions.
How do I enable MFA on RDS?
To configure integration of Azure AD MFA with RDS, you need to specify the use of a central store.On the RD Gateway server, open Server Manager.On the menu, click Tools, point to Remote Desktop Services, and then click Remote Desktop Gateway Manager.More items...•
How do I enable 2FA on Remote Desktop?
0:171:52Enable 2FA when opening Remote Desktop Manager - RDM Pro Tip 001YouTubeStart of suggested clipEnd of suggested clipSo i'm going to go to file. And head down to options. And in the options menu there's a security tabMoreSo i'm going to go to file. And head down to options. And in the options menu there's a security tab.
How do I enable MFA on my server?
Option 1 - Enable MFA on a user by user basis:From the main Azure portal page, select "Azure Active Directory" then "Users"Select "Multi-Factor Authentication" from the top menu.A new page that displays your users and their MFA status will open.Select the user you would like to enable MFA for.
How secure is MFA?
It's more secure than SMS and slightly less than the security key, with between 90% to 100% effectiveness at blocking account attacks. Authentication apps are still fairly convenient, but they do require an additional step to set them up so they can be used for MFA with all your accounts.
How do I get an MFA?
To apply for an MFA in photography or another visual arts specialty, for example, you must provide a portfolio of your work. If you're pursuing creative writing, you must submit an original manuscript. And MFA programs in acting require an audition.
What does MFA protect against?
In addition to combating common cyberattacks, MFA is also effective at preventing ransomware attacks. Ransomware attacks start when an attacker gains access to account credentials. But with MFA, the attackers don't have the additional required information to access the target account.
What are the benefits of using MFA?
Let's take a look at its seven benefits:It provides more layers of security than 2FA. ... It assures consumer identity. ... It meets regulatory compliances. ... It comes with easy implementation. ... It complies with Single Sign-On (SSO) solutions. ... It adds next-level security, even remotely. ... It is an effective cybersecurity solution.
How does MFA improve security?
MFA adds layers of security by requiring users to provide multiple forms of identification. Think of MFA like a bank requiring you to provide ID, account information and a physical key in order to open a safety deposit box. If any of the required forms of identification are missing, access is denied.
Why is it important to implement MFA inside of an organization?
MFA makes sure that your organization remains secure, even if another company has experienced credential theft that's resulted in your employees' passwords being leaked.
What is MFA authentication?
According to TechTarget, MFA is a security system that requires two or more methods of authentication from different categories that verify a user’s identity to log in. One of the benefits of multi-factor authentication is having a layered defense that makes it harder for an unauthorized individual to gain access to any sensitive information, ...
What is MFA card?
Multi-factor authentication (MFA) is talked about, and used, a lot in our day-to-day lives. A classic example of using MFA is a debit card. Not only do you need the physical card, but you also have to enter a personal identification number (PIN) to use it when checking out at a store, or when taking money out of the ATM.
Why does biometric verification fail in spy movies?
Unsurprisingly, someone who shouldn’t be there enters the lair and shuts down all the evil plans. Biometric verification fails in these movies because it was used as the only factor.
How to create a realistic multifactor authentication policy?
Looking to create a realistic multi-factor authentication policy? The first step is to implement MFA for remote access in business practices and regulate vendors. Ultima tely, ensure that all of your third-party access is controlled by a consistent formula for reliable identification, up-to-date credentialing, and multi-factor authentication.
How to increase security measures?
To increase security measures further, add multi-factor authentication to each login and ensure that when a unique user signs on, they are exactly who they say they are . To learn more about the issues that are tied to privileged credentials being used by bad actors, download our eBook that highlights the use of privileged credentials in third-party data breaches.
Why is MFA important?
For both, MFA is great (and very important) to implement because it is a means of controlling access to a network and keeping sensitive data safe.
Do external vendors have to use the same password?
If your external vendors must create their own password to access your network, it’s imperative that they don’t use the same password for all of their accounts. Sure, it’s much easier to remember your password, but if someone steals your password… It’s easy for them to get access to all of your accounts.
How to use MFA?
Start with admin accounts. At a minimum, you want to use MFA for all your admins, so start with privileged users. Administrative accounts are your highest value targets and the most urgent to secure, but you can also treat them as a proof of concept for wider adoption.
How to transition to MFA?
The key is focusing on awareness: in addition to sending emails— put up posters in the elevator, hang banner ads in your buildings, all explaining why you’re making the transition to MFA. Focus on informing your users, explaining why you’re making this change— making it very clear what they will need to do and where they can find instructions, documentation, and support.
What does MFA mean?
If MFA means that a user accessing a non-critical file share or calendar on the corporate network from a known device that has all the current OS and antimalware updates sees fewer challenges—and no longer faces the burden of 90-day password resets —then you can actually improve the user experience with MFA.
How to continue MFA marketing?
Your MFA marketing campaign also needs to continue during and after deployment, actively reaching out to staff and asking them to take back in polls or feedback sessions. Start that with the pilot group and continue it once everyone is using MFA.
Why do you need to move to MFA?
Your CEO, CFO, and other senior leaders need to move to MFA to protect business communications.
How to find out more about Microsoft security?
To find out more about Microsoft’s Cybersecurity Solutions, visit the Microsoft Security site, or follow Microsoft Security on Twitter at Microsoft Security Twitter or Microsoft WDSecurity Twitter .
Is MFA implementation always straightforward?
The problem is that deploying MFA at scale is not always straightforward. There are technical issues that may hold you up, but the people side is where you have to start. The eventual goal of an MFA implementation is to enable it for all your users on all of your systems all of the time, but you won’t be able to do that on day one.
Why is MFA important for remote teams?
Organizations must now look to improve the security protocols for remote teams as employees would be using personal devices and networks to do tasks that would have otherwise been done on a secure network. That underscores the importance of setting up MFA for remote employees.
What Solutions Easily Deliver MFA To Remote Employees?
Organizations can rely on JumpCloud’s solution to layer MFA in front of the access transaction of almost any resource they need to: cloud applications, networks, devices including Windows, Mac and Linux, infrastructure and more.
What are The Challenges Around Setting Up MFA For Remote Employees?
Organizations can choose to require a second factor for authentication when the user logs into a system or an application. However, this is easier said than done when dealing with remote workers. No matter how sophisticated the IT department may be, there are many challenges facing MFA adoption.
Why is multifactor authentication important?
This is why multi-factor authentication is so important for remote employees. It not only adds an extra layer of security to the login process by requiring the user to validate that they are, in fact , who they say they are, but it’s become a familiar security technology in everyone’s personal lives as well, helping to promote adoption and continued use. While that additional factor can vary greatly, from one-time codes sent to through email or registered numbers, accessed via a dedicated app on a mobile device, delivered through a push notification, physical security key, or even biometrics, chances are the workforce has come across and had to implement it.
What happens if MFA is dictated by the resources themselves?
As mentioned above, an inconsistent experience will hinder adoption and create an incentive to bypass the process.
Why do we need access to IT resources?
No matter where employees work, they need access to an organization’s IT resources in order to do their jobs effectively . When the work environment is fully contained within the domain (generally determined by a physical office space and a managed network, with heavy requirements to leverage VPN access for the occasional remote work), an IT organization has much more control over the security posture of their environment. Physical access to office locations are limited to employees and the occasional temp, contractor or stand-alone vendor meeting, with a layer of physical security protecting the premises in the form of security personnel, cameras and security motion sensors. On top of that, access into and out of the network can be monitored and controlled via strong perimeter defenses like firewalls, internal network monitoring tools and more.
Can remote employees use MFA?
Setting up MFA for remote employees can prove to be a hassle in such instances as organizations are unable to deploy a uniform MFA solution that keeps it simple for employees to use.
Step 1: Security - MFA Setup
Multi-Factor Authentication (MFA) is required for safely and securely accessing Trinity Health resources while working off-site.
Step 2: How to Connect to Trinity Health Resources
Instructions: Please choose the job aid that best reflects the application and type of device you’ll use to remotely access Trinity Health resources.
Need Help?
Please follow the instructions on this page before calling the Service Desk, unless your issue is critical, e.g., one that impacts patient care.
Frequently Asked Questions
Most people use the Trinity-Health domain EXCEPT in the following locations:
Enabling MFA on admin level access to On premise AD
Hello everyone. I've run into a puzzler and I'm hoping someone can give me a tip on how to solve this. I have received a "cyber security attestation" document from a major insurance provider and must be able to say yes to all of the items on it as a baseline to receive a policy. Here's the one I'm stuck on:
Re: Enabling MFA on admin level access to On premise AD
Windows Hello for Business is considered by Microsoft to be a multi-factor solution. There is a certificate on the device (something you have) and then you typically sign in with a PIN (something you know) or a biometric (something you are).
Re: Enabling MFA on admin level access to On premise AD
https://techcommunity.microsoft.com/t5/security-compliance-and-identity/how-to-enabling-mfa-for-acti...
Re: Enabling MFA on admin level access to On premise AD
As I said here, the only option I investigated thoroughly enough to complete a POC is the one I personally chose, which is Authlite.
Re: Enabling MFA on admin level access to On premise AD
Dabona, I glanced over the outline of your post and that's a lot to take in, in a good way. Thank you for the info. I am going to take the time to read through all the concepts you have, as well as how you have them strung together. I anticipate being a better sysadmin afterwards!
Re: Enabling MFA on admin level access to On premise AD
Hello, please check if this can be an alternative to third party tools.
Re: Enabling MFA on admin level access to On premise AD
Thanks JHanson, please test if you have time and let me know your feedback... I am trying to find people who can test my POC :) !!
What is Azure AD MFA?
Recall that the NPS server with the Azure AD MFA extension is the designated central policy store for the Connection Authorization Policy (CAP). Therefore, you need to implement a CAP on the NPS server to authorize valid connections requests.
What to do if Azure AD MFA is not working?
If the configuration is not working as expected, the first place to start to troubleshoot is to verify that the user is configured to use Azure AD MFA. Have the user connect to the Azure portal. If users are prompted for secondary verification and can successfully authenticate, you can eliminate an incorrect configuration of Azure AD MFA.
How to register NPS server in Active Directory?
On the NPS server, open Server Manager. In Server Manager, click Tools, and then click Network Policy Server. In the Network Policy Server console, right-click NPS (Local), and then click Register server in Active Directory. Click OK two times. Leave the console open for the next procedure.
What is a RD CAP?
Remote Desktop connection authorization policies (RD CAPs) specify the requirements for connecting to a Remote Desktop Gateway server. RD CAPs can be stored locally (default) or they can be stored in a central RD CAP store that is running NPS. To configure integration of Azure AD MFA with RDS, you need to specify the use of a central store.
What is required for Azure AD MFA?
Required is a license for Azure AD MFA, which is available through Azure AD Premium or other bundles that include it. Consumption-based licenses for Azure AD MFA, such as per user or per authentication licenses, are not compatible with the NPS extension. For more information, see How to get Azure AD Multi-Factor Authentication. For testing purposes, you can use a trial subscription.
How to grant access to RDG_CAP?
In the Copy of Connections to other access servers dialog box, in Policy name, enter a suitable name, such as RDG_CAP. Check Policy enabled, and select Grant access. Optionally, in Type of network access server, select Remote Desktop Gateway, or you can leave it as Unspecified.
Can you manually create an RDS infrastructure?
If you wish to manually create an on-premises RDS infrastructure quickly for testing purposes, follow the steps to deploy one. Learn more: Deploy RDS with Azure quickstart and Basic RDS infrastructure deployment.

Campaign and Train
Start with Admin Accounts
- At a minimum, you want to use MFA for all your admins, so start with privileged users. Administrative accounts are your highest value targets and the most urgent to secure, but you can also treat them as a proof of concept for wider adoption. Review who these users are and what privileges they have—there are probably more accounts than you expect with far more privilege…
Plan For Wider Deployment
- Start by looking at what systems you have that users need to sign in to that you can secure with MFA. Remember that includes on-premises systems—you can incorporate MFA into your existing remote access options, using Active Directory Federation Services (AD FS), or Network Policy Server and use Azure Active Directory (Azure AD) Application Proxyto ...
Make MFA Easier on Employees
- MFA is always going to be an extra step, but you can choose MFA options with less friction, like using biometrics in devices or FIDO2 compliant factors such as Feitan or Yubico security keys. Avoid using SMS if possible. Phone-based authentication apps like the Microsoft Authenticator App are an option, and they don’t require a user to hand over control of their personal device. Bu…
Have A Support Plan
- Spend some time planning how you will handle failed sign-ins and account lockouts. Even with training, some failed sign-ins will be legitimate users getting it wrong and you need to make it easy for them to get help. Similarly, have a plan for lost devices. If a security key is lost, the process for reporting that needs to be easy and blame free, so that employees will notify you im…
Measure and Monitor
- As you deploy MFA, monitor the rollout to see what impact it has on both security and productivity and be prepared to make changes to policies or invest in better hardware to make it successful. Track security metrics for failed login attempts, credential phishing that gets blocked and privilege escalations that are denied. Your MFA marketing campaign also needs to continue during and a…
About The Authors
- Ann Johnsonis the Corporate Vice President for Cybersecurity Solutions Group for Microsoft. She is a member of the board of advisors for FS-ISAC (The Financial Services Information Sharing and Analysis Center), an advisory board member for EWF (Executive Women’s Forum on Information Security, Risk Management & Privacy), and an advisory board member for HYPR Corp. Ann recen…
Learn More
- To find out more about Microsoft’s Cybersecurity Solutions, visit the Microsoft Security site, or follow Microsoft Security on Twitter at Microsoft Security Twitter or Microsoft WDSecurity Twitter. To learn more about Microsoft Azure Identity Management solutions, visit this Microsoft overview page and follow our Identity blog. You can also follow us @AzureADon Twitter. Bookmark the Se…