
How can I integrate MFA into my existing remote access options?
Remember that includes on-premises systems— you can incorporate MFA into your existing remote access options, using Active Directory Federation Services (AD FS), or Network Policy Server and use Azure Active Directory (Azure AD) Application Proxy to publish applications for cloud access.
What are the benefits of MFA for remote networks?
MFA for remote networks reduces the potential for a network security breach caused by a cracked, lost, or stolen password. MFA for administrative access limits an attacker’s ability to gain broader access to a compromised network. MFA for email reduces the potential for access and control of corporate email accounts.
What MFA controls do carriers have in place?
Most carriers now require these MFA controls in place: Multi-factor authentication for administrative access Multi-factor authentication for remote access to email MFA for remote networks reduces the potential for a network security breach caused by a cracked, lost, or stolen password.
What is MFA and why is it mandatory?
MFA is mandatory for purchasing a new cyber policy and the renewal of an existing one. The checklist of MFA rules includes enforcing MFA for all employees accessing email through a website or cloud-based service; remote access to the network provided to employees, contractors, third-party providers.

What is MFA for remote access?
What is Multi-Factor Authentication for Remote Access? Multi-factor authentication is a security system that requires two or more methods of authentication from different categories that verify a user's identity to log in.
Is MFA required for every login?
If you're using Salesforce's MFA functionality, users must respond to an MFA challenge each time they log in to a Salesforce product. This applies to all logins, including those due to inactivity and expired sessions.
How do I use MFA in Remote Desktop?
Launch a desktop or RemoteApp from an RDP file or through a Remote Desktop client application. Upon connecting to the RD Gateway for secure, remote access, receive an SMS or mobile application MFA challenge. Correctly authenticate and get connected to their resource!
Is MFA required for VPN?
Conclusion. Organizations realize they need to use MFA to authenticate remote users when accessing VPN.
How often is MFA required?
every 90 daysApps. Applications, unlike browsers, have a 90 day rolling token, which means that you should not be asked to verify with MFA if you use an app more frequently than every 90 days. Any changes that cause you to login again, such as a software update, will trigger MFA verification.
When should MFA be used?
Why is MFA Important? The main benefit of MFA is it will enhance your organization's security by requiring your users to identify themselves by more than a username and password. While important, usernames and passwords are vulnerable to brute force attacks and can be stolen by third parties.
Does RDP support MFA?
Remote desktop access from off-campus has been protected with multi-factor authentication (MFA). This means you'll need to use your second factor to connect to your on-campus desktop computer.
Can I use Microsoft authenticator for RDP?
Yes, you can protect workstation and RDP logins with 2FA using UserLock. It makes user self-enrollment easy with authenticator applications (including MS Authenticator), or programmable hardware tokens such as YubiKey or Token2.
Does RDP support two-factor authentication?
Two factor authentication for Remote Desktop (RDP) and Local Windows Logon. The LoginTC Windows Logon and RDP Connector integrates natively with Windows Server and Windows Client operating systems to add two-factor authentication for both remote desktop and local logins.
How do I enable MFA for VPN?
Click Select users and groups. Check Users and groups. Click Select to select a group or set of users to be affected by MFA. Click Done....Option 2 - Conditional AccessClick Grant access.Click Require multi-factor authentication.Click Require all the selected controls.Click Select.
How is authentication implemented in a VPN?
In addition to older and less-secure password-based authentication methods (which should be avoided), the built-in VPN solution uses Extensible Authentication Protocol (EAP) to provide secure authentication using both user name and password, and certificate-based methods.
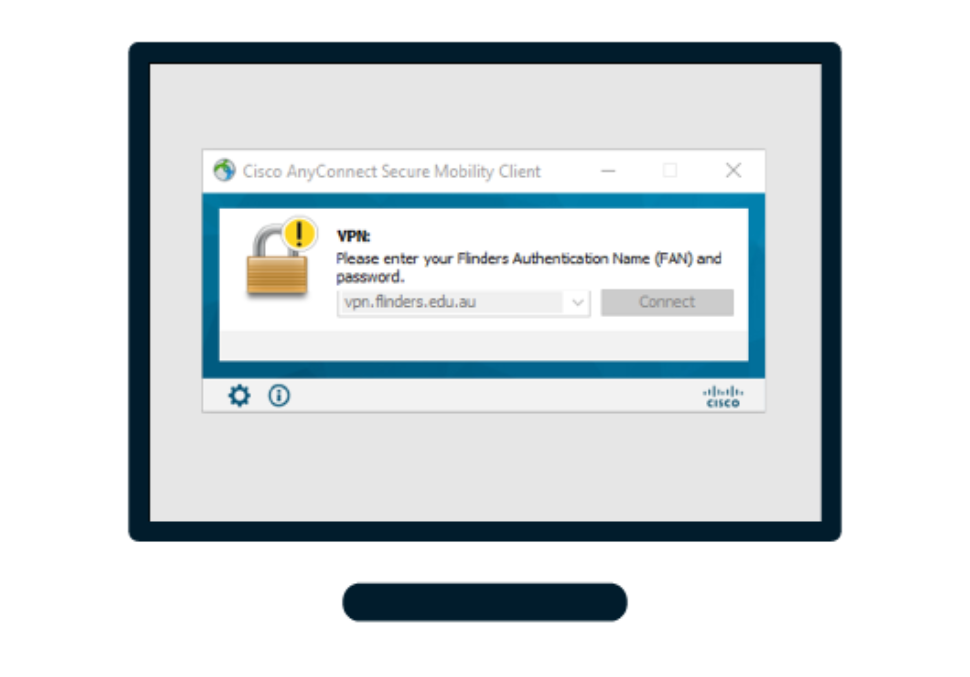
Does Cisco AnyConnect have MFA?
Duo's multi-factor authentication (MFA) is the easiest MFA solution to protect your Cisco AnyConnect VPN. Duo integrates seamlessly with Cisco's AnyConnect VPN, providing an additional layer of security for your remote access strategy.
Is MFA a functional requirement?
This type of requirements does not describe the product's functions, but it does describe the properties and rules to which it must comply. For example, there is a multifactor authentication function.
Can you have both SSO and MFA?
As cyber threats become more complex, companies need to adapt. Implementing single sign-on (SSO) and multi-factor authentication (MFA) is a fairly easy way to do that. To protect both your employees and your organization, Huntress highly recommends implementing both SSO and MFA.
What is difference between MFA and SSO?
SSO is all about users gaining access to their resources with a single sign-on authentication. Two-factor authentication uses just two of these methods to verify and authorize a user's login attempts, whereas MFA uses two or more of these checkpoints.
Is SSO more secure than MFA?
MFA and SSO are both coming at the issue of security and authentication from different areas. SSO is more convenient for users but has higher inherent security risks. MFA is more secure but less convenient.
What is MFA authentication?
According to TechTarget, MFA is a security system that requires two or more methods of authentication from different categories that verify a user’s identity to log in. One of the benefits of multi-factor authentication is having a layered defense that makes it harder for an unauthorized individual to gain access to any sensitive information, ...
What is MFA card?
Multi-factor authentication (MFA) is talked about, and used, a lot in our day-to-day lives. A classic example of using MFA is a debit card. Not only do you need the physical card, but you also have to enter a personal identification number (PIN) to use it when checking out at a store, or when taking money out of the ATM.
Why does biometric verification fail in spy movies?
Unsurprisingly, someone who shouldn’t be there enters the lair and shuts down all the evil plans. Biometric verification fails in these movies because it was used as the only factor.
How to create a realistic multifactor authentication policy?
Looking to create a realistic multi-factor authentication policy? The first step is to implement MFA for remote access in business practices and regulate vendors. Ultima tely, ensure that all of your third-party access is controlled by a consistent formula for reliable identification, up-to-date credentialing, and multi-factor authentication.
Why is MFA important?
For both, MFA is great (and very important) to implement because it is a means of controlling access to a network and keeping sensitive data safe.
Do external vendors have to use the same password?
If your external vendors must create their own password to access your network, it’s imperative that they don’t use the same password for all of their accounts. Sure, it’s much easier to remember your password, but if someone steals your password… It’s easy for them to get access to all of your accounts.
Is a debit card a multifactor authentication?
A debit card is a relatively basic example of multi-factor authentication, but the principle should be used in both your personal and professional life. For example, MFA for remote access should be used in situations that involve relationships between third parties and organizations.
How to use MFA?
Start with admin accounts. At a minimum, you want to use MFA for all your admins, so start with privileged users. Administrative accounts are your highest value targets and the most urgent to secure, but you can also treat them as a proof of concept for wider adoption.
How to transition to MFA?
The key is focusing on awareness: in addition to sending emails— put up posters in the elevator, hang banner ads in your buildings, all explaining why you’re making the transition to MFA. Focus on informing your users, explaining why you’re making this change— making it very clear what they will need to do and where they can find instructions, documentation, and support.
What does MFA mean?
If MFA means that a user accessing a non-critical file share or calendar on the corporate network from a known device that has all the current OS and antimalware updates sees fewer challenges—and no longer faces the burden of 90-day password resets —then you can actually improve the user experience with MFA.
How to continue MFA marketing?
Your MFA marketing campaign also needs to continue during and after deployment, actively reaching out to staff and asking them to take back in polls or feedback sessions. Start that with the pilot group and continue it once everyone is using MFA.
Why do you need to move to MFA?
Your CEO, CFO, and other senior leaders need to move to MFA to protect business communications.
Is MFA implementation always straightforward?
The problem is that deploying MFA at scale is not always straightforward. There are technical issues that may hold you up, but the people side is where you have to start. The eventual goal of an MFA implementation is to enable it for all your users on all of your systems all of the time, but you won’t be able to do that on day one.
Can you combine MFA with self service password reset?
You may be able to combine MFA registration with self-service password reset (SSPR) in a ‘one stop shop,’ but it’s important to get users to register quickly so that attackers can’t take over their account by registering for MFA, especially if it’s for a high-value application they don’t use frequently.
What is service account?
Service accounts are non-interactive accounts that are not tied to any particular user. They are normally used by back-end services allowing programmatic access to applications, but are also used to sign in to systems for administrative purposes.
Do all cloud applications require equal security?
Organizations may have many cloud applications in use. Not all of those applications may require equal security. For example, the payroll and attendance applications may require MFA but the cafeteria probably doesn't. Administrators can choose to exclude specific applications from their policy.
Does MFA matter?
Your password doesn't matter , but MFA does! Based on our studies, your account is more than 99.9% less likely to be compromised if you use MFA.
What is MFA for remote access?
Most carriers now require these MFA controls in place: Multi-factor authentication for administrative access. Multi-factor authentication for remote access to email. MFA for remote networks reduces the potential for a network security breach caused by a cracked, lost, or stolen password.
Why is MFA important for email?
MFA for email reduces the potential for access and control of corporate email accounts. Keep in mind that with access to a corporate email account an attacker not only has access to sensitive data contained in email; the attacker also likely has the ability to perform self-service resets of passwords that protect other services.
What is MFA in insurance?
Multi-Factor Authentication (MFA) is now commonly a minimum requirement for cyber insurance. Stated bluntly: if MFA is not enabled in your computing environment, you are engaging in behavior so risky that insurance carriers will not offer cyber insurance coverage to your business.
How much can MFA block?
In fact, Microsoft famously reported, “By providing an extra barrier and layer of security that makes it incredibly difficult for attackers to get past, MFA can block over 99.9 percent of account compromise attacks. With MFA, knowing or cracking the password won’t be enough to gain access.”.
What are the factors of multifactor authentication?
Multi-Factor Authentication adds another layer of protection, in addition to your passwords. It requires that a user provides multiple credentials (factors) to validate his or her identity. The factors used to validate identity typically consist of some combination of three things: 1 Something you KNOW 2 Something you HAVE 3 Something you ARE
What is MFA in a game?
MFA places an incredibly challenging obstacle before an attacker. Faced with this sort of obstacle, an attacker will likely move on to another attack vector or another target altogether.
How much does a duo MFA cost?
We often recommend Duo MFA which, at a list price of $3/user per month, is a relatively inexpensive tool that will protect your workforce with simple yet robust access security.
Enabling MFA on admin level access to On premise AD
Hello everyone. I've run into a puzzler and I'm hoping someone can give me a tip on how to solve this. I have received a "cyber security attestation" document from a major insurance provider and must be able to say yes to all of the items on it as a baseline to receive a policy. Here's the one I'm stuck on:
Re: Enabling MFA on admin level access to On premise AD
Windows Hello for Business is considered by Microsoft to be a multi-factor solution. There is a certificate on the device (something you have) and then you typically sign in with a PIN (something you know) or a biometric (something you are).
Re: Enabling MFA on admin level access to On premise AD
https://techcommunity.microsoft.com/t5/security-compliance-and-identity/how-to-enabling-mfa-for-acti...
Re: Enabling MFA on admin level access to On premise AD
As I said here, the only option I investigated thoroughly enough to complete a POC is the one I personally chose, which is Authlite.
Re: Enabling MFA on admin level access to On premise AD
Dabona, I glanced over the outline of your post and that's a lot to take in, in a good way. Thank you for the info. I am going to take the time to read through all the concepts you have, as well as how you have them strung together. I anticipate being a better sysadmin afterwards!
Re: Enabling MFA on admin level access to On premise AD
Hello, please check if this can be an alternative to third party tools.
Re: Enabling MFA on admin level access to On premise AD
Thanks JHanson, please test if you have time and let me know your feedback... I am trying to find people who can test my POC :) !!
What are the principles of MFA?
Principles of a good MFA implementation include independence of authentication mechanisms, protection of authentication factors, and ensuring that no knowledge of the success or failure of a factor is provided to the individual until all factors have been submitted .
What is the purpose of MFA?
The intent of MFA is to provide a higher degree of assurance of the identity of the individual attempting to access a resource — such as a physical location, computing device, network, or database — by creating a multi-layered mechanism that an unauthorized user would have to defeat in order to gain access.
What is MFA in PCI?
To help organizations combat this growing threat, the PCI Security Standards Council (PCI SSC) has issued guidance on the proper use of multi-factor authentication (MFA) for preventing unauthorized access to computers and systems that process payment transactions.
Is MFA good?
Something you know, such as a password or passphrase; Something you have, such as a token device or smart card; Something you are, such as a biometric. You’ve said that MFA is only as good as its implementation.
Does PCI DSS require MFA?
While PCI DSS does not currently require MFA implementations to meet all the principles described in this guidance document, it may in the future, and these industry-recognized best practices provide a roadmap for future security considerations.
Campaign and Train
Start with Admin Accounts
- At a minimum, you want to use MFA for all your admins, so start with privileged users. Administrative accounts are your highest value targets and the most urgent to secure, but you can also treat them as a proof of concept for wider adoption. Review who these users are and what privileges they have—there are probably more accounts than you expect with far more privilege…
Plan For Wider Deployment
- Start by looking at what systems you have that users need to sign in to that you can secure with MFA. Remember that includes on-premises systems—you can incorporate MFA into your existing remote access options, using Active Directory Federation Services (AD FS), or Network Policy Server and use Azure Active Directory (Azure AD) Application Proxyto ...
Make MFA Easier on Employees
- MFA is always going to be an extra step, but you can choose MFA options with less friction, like using biometrics in devices or FIDO2 compliant factors such as Feitan or Yubico security keys. Avoid using SMS if possible. Phone-based authentication apps like the Microsoft Authenticator App are an option, and they don’t require a user to hand over control of their personal device. Bu…
Have A Support Plan
- Spend some time planning how you will handle failed sign-ins and account lockouts. Even with training, some failed sign-ins will be legitimate users getting it wrong and you need to make it easy for them to get help. Similarly, have a plan for lost devices. If a security key is lost, the process for reporting that needs to be easy and blame free, so that employees will notify you im…
Measure and Monitor
- As you deploy MFA, monitor the rollout to see what impact it has on both security and productivity and be prepared to make changes to policies or invest in better hardware to make it successful. Track security metrics for failed login attempts, credential phishing that gets blocked and privilege escalations that are denied. Your MFA marketing campaign also needs to continue during and a…
About The Authors
- Ann Johnsonis the Corporate Vice President for Cybersecurity Solutions Group for Microsoft. She is a member of the board of advisors for FS-ISAC (The Financial Services Information Sharing and Analysis Center), an advisory board member for EWF (Executive Women’s Forum on Information Security, Risk Management & Privacy), and an advisory board member for HYPR Corp. Ann recen…
Learn More
- To find out more about Microsoft’s Cybersecurity Solutions, visit the Microsoft Security site, or follow Microsoft Security on Twitter at Microsoft Security Twitter or Microsoft WDSecurity Twitter. To learn more about Microsoft Azure Identity Management solutions, visit this Microsoft overview page and follow our Identity blog. You can also follow us @AzureADon Twitter. Bookmark the Se…