Control panel>System>RemoteSettings (Admin password), Remote tab- click "advanced" box OK, Apply, you may need to restart your computer
Full Answer
What can a remote access trojan do to your computer?
Since a remote access trojan enables administrative control, it is able to do almost everything on the victim machine. Get access to confidential info including usernames, passwords, social security numbers, and credit card accounts. Monitor web browsers and other computer apps to get search history, emails, chat logs, etc.
How to use a virus & threat protection in Windows Security?
Virus & threat protection in Windows Security 1 Run the scans you want. Even though Windows Security is turned on and scans your device automatically, you can perform an additional scan whenever you want. 2 Manage your Virus & threat protection settings. ... 3 Protect your device with the latest updates. ... 4 Learn more
Can I manage DirectAccess clients remotely?
DirectAccess provides a configuration that supports remote management of DirectAccess clients. You can use a deployment wizard option that limits the creation of policies to only those needed for remote management of client computers.
Where can the remote access server be deployed?
The server can be deployed at the edge of the internal network, or behind an edge firewall or other device. If the Remote Access server is located behind an edge firewall or NAT device, the device must be configured to allow traffic to and from the Remote Access server.

Can you get a virus from remote access?
Many remote access software solutions don't scan the remote computer for viruses or malware. If your home or work PC has been infected, and you're using it to access your office network remotely, then a hacker could easily install malware onto your business's servers and spread to every machine in your office.
Can Microsoft access my computer remotely?
You can use Remote Desktop to connect to and control your PC from a remote device by using a Microsoft Remote Desktop client (available for Windows, iOS, macOS and Android).
Is Microsoft remote access safe?
How secure is Windows Remote Desktop? Remote Desktop sessions operate over an encrypted channel, preventing anyone from viewing your session by listening on the network. However, there is a vulnerability in the method used to encrypt sessions in earlier versions of RDP.
Can you tell if someone is remotely accessing your computer?
To see all the login activities on your PC, use Windows Event Viewer. This tool will show you all Windows services that have been accessed and logins, errors and warnings. To access the Windows Event Viewer, click the search icon and type in Event Viewer. Click Windows Logs, then choose Security.
How can I remotely access someones computer?
Share your computer with someone else On your computer, open Chrome. In the address bar at the top, enter remotedesktop.google.com/support , and press Enter. Follow the onscreen directions to download and install Chrome Remote Desktop. Under “Get Support,” select Generate Code.
How do I know if Remote Desktop is enabled Windows 10?
Click the Remote tab. Under the "Remote Desktop" section, check the Allow remote connections to this computer option....Enable remote connections on Windows 10Open Settings.Click on System.Click on Remote Desktop.Turn on the Enable Remote Desktop toggle switch.
What are potential risks associated with remote access?
Five Remote Access Security Risks And How To Protect Against ThemWeak remote access policies. ... A deluge of new devices to protect. ... Lack of visibility into remote user activity. ... Users mixing home and business passwords. ... Opportunistic phishing attempts.
Is remote desktop a security risk?
RDP security risks are unjustifiable for many organizations. Even the slightest incompliance, whether internally or externally when using RDP, is unacceptable. Such organizations require a strategic solution for remote access that is not dependent on native operating system functionality.
Should you disable RDP?
Unfortunately, hackers can exploit Remote Desktop to gain control of remote systems and install malware or steal personal information. It's a good idea to keep the remote access feature turned off unless you actively need it. By default, the feature is disabled.
How can I tell if my computer is being monitored at work 2022?
Open task manager by right-clicking on the taskbar and choosing Task Manager. If there's a suspicious process, that's the monitoring app. Question: Can my company see what I do on my computer? Answer: Your company can see your device activities and track them if they provide you with that computer.
Can someone remotely access my computer without Internet?
Can an Offline Computer be Hacked? Technically — as of right now — the answer is no. If you never connect your computer, you are 100 percent safe from hackers on the internet. There is no way someone can hack and retrieve, alter or monitor information without physical access.
Can someone remotely access my computer with my IP address?
Someone can use your IP to hack your device The internet uses ports as well as your IP address to connect. There are thousands of ports for every IP address, and a hacker who has your IP can try all of those ports to brute-force a connection, taking over your phone for example and stealing your information.
Does Remote Desktop show screen on host?
From the remote computer, the user is prompted to enter the IP address of the host. Then, the user is prompted to enter the login credentials of the host. At this point, the remote screen displays information from the host computer, allowing the user to interact with it like normal, even if the computer is miles away.
How can I remotely access another computer over the Internet for free?
10 Best Free Remote Desktop Tools You Should KnowTeamViewer. Available in premium and free versions, TeamViewer is quite an impressive online collaboration tool used for virtual meetings and sharing presentations. ... Splashtop. ... Chrome Remote Desktop. ... Microsoft Remote Desktop. ... TightVNC. ... Mikogo. ... LogMeIn. ... pcAnywhere.More items...
Where is a remote access server deployed?
The Remote Access server must be a domain member. The server can be deployed at the edge of the internal network, or behind an edge firewall or other device.
Where to place remote access server?
Network and server topology: With DirectAccess, you can place your Remote Access server at the edge of your intranet or behind a network address translation (NAT) device or a firewall.
What permissions do remote access users need?
Admins who deploy a Remote Access server require local administrator permissions on the server and domain user permissions. In addition, the administrator requires permissions for the GPOs that are used for DirectAccess deployment.
What is DirectAccess configuration?
DirectAccess provides a configuration that supports remote management of DirectAccess clients. You can use a deployment wizard option that limits the creation of policies to only those needed for remote management of client computers.
What is DirectAccess client?
DirectAccess client computers are connected to the intranet whenever they are connected to the Internet, regardless of whether the user has signed in to the computer. They can be managed as intranet resources and kept current with Group Policy changes, operating system updates, antimalware updates, and other organizational changes.
What is DirectAccess Remote Client Management?
The DirectAccess Remote Client Management deployment scenario uses DirectAccess to maintain clients over the Internet. This section explains the scenario, including its phases, roles, features, and links to additional resources.
How many domain controllers are required for remote access?
At least one domain controller. The Remote Access servers and DirectAccess clients must be domain members.
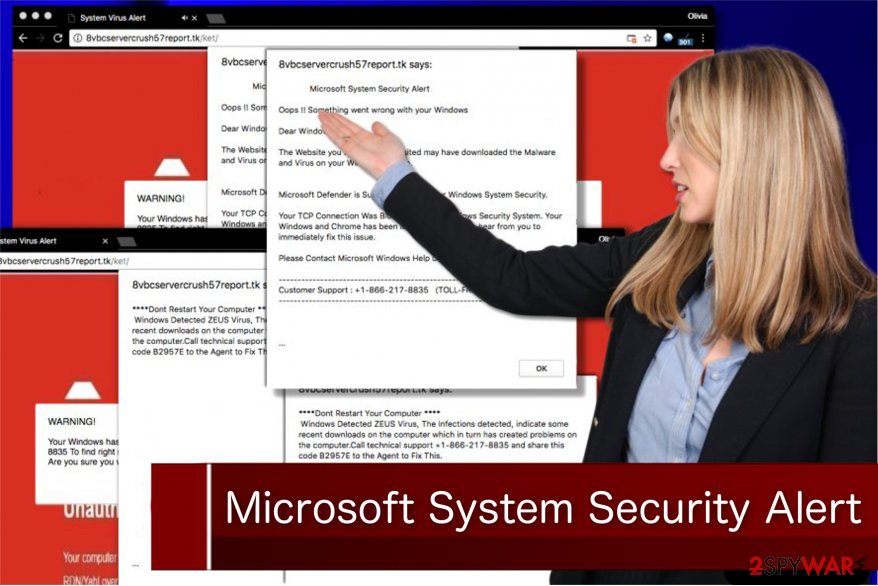
What is "VIRUS ALERT FROM MICROSOFT"?
Displayed by a malicious website, "VIRUS ALERT TO MICROSOFT" is a fake error claiming that the system has detected suspicious activity. In most cases, users visit this website inadvertently - they are redirected by various potentially unwanted programs (PUAs) that infiltrate systems without permission.
What is the number to call Microsoft to protect your data?
Your information (for example, passwords, messages and credit cards) are been extracted from your Device. Call Microsoft. at 1-844-808-7462 to protect your files and identity from misuse, Please do not try to close this page or your Device will be disabled to. protect your data.
How did potentially unwanted programs install on my computer?
Developers proliferate PUAs using a deceptive marketing method called "bundling" and intrusive advertisements. "Bundling" is stealth installation of unwanted programs with regular software/apps.
How to remove malicious add-ons from Internet Explorer?
Remove malicious add-ons from Internet Explorer: Click the "gear" icon (at the top right corner of Internet Explorer), select "Manage Add-ons". Look for any recently-installed suspicious browser extensions, select these entries and click "Remove". Optional method: If you continue to have problems with removal of the "virus alert from microsoft" ...
Why do PUAs infiltrate systems without permission?
As mentioned above, PUAs usually infiltrate systems without permission due to the lack of knowledge and careless behavior of many users . Developers proliferate PUAs using a deceptive marketing method called "bundling" and intrusive advertisements. "Bundling" is stealth installation of unwanted programs with regular software/apps.
What to do after uninstalling malware?
After uninstalling the potentially unwanted program, scan your computer for any remaining unwanted components or possible malware infections. To scan your computer, use recommended malware removal software .
Where is the Control Panel on my computer?
Right-click in the lower left corner of the screen, in the Quick Access Menu select Control Panel. In the opened window choose Programs and Features.
What does it mean when you turn on control folder access?
This means that content in any of these folders cannot be accessed or changed by any unknown or untrusted apps. If you add additional folders, they become protected as well.
How to make files safer from ransomware?
Use the Controlled folder access setting to manage which folders untrusted apps can make changes to. You can also add additional apps to the trusted list so they can make changes in those folders. This is a powerful tool to make your files safer from ransomware.
What is Microsoft Defender offline scan?
Scans only files and folders that you select. Microsoft Defender Offline scan. Uses the latest definitions to scan your device for the latest threats. Run it when you are concerned that your device has been exposed to malware or a virus, or if you want to scan your device without being connected to the Internet.
How to run a scan on Windows 10?
Run the scans you want 1 Quick scan. Concerned that you may have done something to introduce a suspicious file or virus to your device? Select Quick scan (called Scan now in previous versions of Windows 10) to immediately check your device for any recent threats. This option is useful when you don’t want to spend the time running a full scan on all your files and folders. If Windows Security recommends that you run one of the other types of scans, you'll be notified when the Quick scan is done. 2 Scan options. Select this link (called Run a new advanced scan in previous versions of Windows 10) to choose from one of the following advanced scan options:#N#Full scan. Scans every file or program that’s currently running on your device to make sure there’s nothing dangerous in progress.#N#Custom scan. Scans only files and folders that you select.#N#Microsoft Defender Offline scan. Uses the latest definitions to scan your device for the latest threats. Run it when you are concerned that your device has been exposed to malware or a virus, or if you want to scan your device without being connected to the Internet. This will restart your device, so be sure to save files you may have open.
How to turn off notifications on Windows Security?
You can turn these notifications on, or off, on the notifications page. In Virus & threat protection, under Virus & threat protection settings, select Manage settings, scroll down to Notifications and select Change notification settings.
Can a system administrator turn off real time protection?
Note: If the device you’re using is part of an organization, your system administrator may prevent you from turning off real-time protection.
Can you turn off Tamper Protection on Microsoft Defender?
With Tamper Protection turned on, important settings like real -time protection, can't be easily or accidentally turned off.
What is the virus alert from Microsoft?
The “Virus Alert from Microsoft” notification will always appear in your web browser. Even if you’re not surfing the web, malware on your PC can open your web browser and redirect you to the fake “Virus Alert from Microsoft” web page.
How to get rid of Microsoft virus alert?
So first, try to close your web browser normally. If that doesn’t work, press “Ctrl+Shift+Delete” to open your Task Manager. Find your web browser among the running processes, and click “End Task” to force it to close.
What is a virus scan?
A full virus scan will check everywhere on your computer for malware. The virus scanner will quarantine any malware it finds and then allow you to remove it from your system. This includes rootkits, worms, spyware, and other threats that often run undetected.
What happens if you cancel a virus scan?
If you cancel the virus scan before it hits 100%, the malware will continue to replicate and still infect your system. Unfortunately, this means you’ll likely start getting the “Virus Alert from Microsoft” pop-up again.
What does it mean when you see a virus alert on your computer?
If you see “Virus Alert from Microsoft” on your computer, you’re either on a sketchy website that is trying to hack your device, or you have a malware file on your computer that is issuing false pop-ups.
How long does it take to scan a computer for viruses?
The full scan can take anywhere between 1–4 hours. Your PC may run slowly while running the scan since virus scans can be CPU-demanding. A good idea is to schedule the scan at night. Then, you can leave your PC until the following morning, when the scan will be completed.
What happens if my antivirus doesn't detect my files?
If your antivirus hasn’t detected any compromised files, then chances are you’ve just accidentally visited a dangerous website. If this is the case, you can skip ahead to keeping your device protected.
What is MFA in remote work?
Multi-factor authentication (MFA) is the single best thing you can do to improve security for remote work. If you’re not able to distribute hardware security devices, use biometrics or mobile device authentication apps like Microsoft Authenticator as the second factor. Enable MFA and create Conditional Access policies.
Why use Microsoft Cloud App Security?
Use Microsoft Cloud App Security to monitor session risk, gain visibility into usage, and enforce app and file usage policies in real time. Maintain productivity by educating and guiding workers to access the cloud resources they need through more secure methods.
What is Azure AD conditional access?
Azure AD Conditional Access is the Microsoft identity security policy hub. Create Conditional Access policies according to user, device, application, and risk. Enforce controls that allow a device trying to access a specific resource only if it’s compliant.
Is Microsoft Defender antiphishing?
Phishing is a primary point of entry for attackers and recent world events have provided them a new opportunity to trick users into clicking on lures. For security against malicious emails, Microsoft Defender for Office 365 lets you set up antiphishing protections to help protect your employees from increasingly sophisticated attacks.
Is remote work important?
Now, more than ever, remote work capabilities are vital . Ensure your workforce is as efficient working from home as they were at the office. In this webinar you’ll learn how Microsoft Azure Active Directory helps improve efficiency while maintaining the right balance of productivity and security for remote workers.
Is Microsoft Fasttrack available?
Microsoft FastTrack is now available to assist organizations setting up remote work.
How to protect yourself from remote access trojans?
Just like protecting yourself from other network malware threats, for remote access trojan protection, in general, you need to avoid downloading unknown items; keep antimalware and firewall up to date, change your usernames and passwords regularly; (for administrative perspective) block unused ports, turn off unused services, and monitor outgoing traffic.
What Does a RAT Virus Do?
Since a remote access trojan enables administrative control , it is able to do almost everything on the victim machine.
How does RAT malware work?
Once get into the victim’s machine, RAT malware will hide its harmful operations from either the victim or the antivirus or firewall and use the infected host to spread itself to other vulnerable computers to build a botnet.
What is a RAT trojan?
RAT trojan is typically installed on a computer without its owner’s knowledge and often as a trojan horse or payload. For example, it is usually downloaded invisibly with an email attachment, torrent files, weblinks, or a user-desired program like a game. While targeted attacks by a motivated attacker may deceive desired targets into installing RAT ...
Why do RATs use a randomized filename?
It is kind of difficult. RATs are covert by nature and may make use of a randomized filename or file path structure to try to prevent identification of itself. Commonly, a RAT worm virus does not show up in the lists of running programs or tasks and its actions are similar to those of legal programs.
How to check if my computer is safe?
Open the command prompt better as administrator, type “ system.ini ”, and press Enter. Then, a notepad will pop up showing you a few details of your system. Take a look at the drivers section, if it looks brief as what the below picture shows, you are safe. if there are some other odd characters, there may be some remote devices accessing your system via some of your network ports.
Can a RAT remote access trojan be used on a computer?
Since RAT remote access trojan will probably utilize the legitimate apps on your computer, you’d better upgrade those apps to their latest versions. Those programs include your browsers, chat apps, games, email servers, video/audio/photo/screenshot tools, work applications…

Overview
Introduction
Symptoms
- Deploying a single Remote Access server for managing DirectAccess clients provides the following: 1. Ease-of-access: Managed client computers running Windows 8 or Windows 7 can be configured as DirectAccess client computers. These clients can access internal network resources through DirectAccess any time they are connected to the Internet without ...
More information
- Windows
Applies to: - Windows Server 2022, all editions
Windows Server 2019, all editions
Resolution
- This article contains recommendations to help an administrator determine the cause of potentia…
The issue occurs on a computer that is running a version of Windows or Windows Server that is listed in the “Applies to” section.
Workaround
- Your Windows-based or Windows Server-based computer experiences the following issues:
System performance - High CPU or increased CPU use
User mode
References
- System-specific information
For more information, see the following articles: - You might experience various issues when you work with files over the network on a Windows S…
System stops responding, slow file server performance, or delays occur when you work with files that are located on a file server