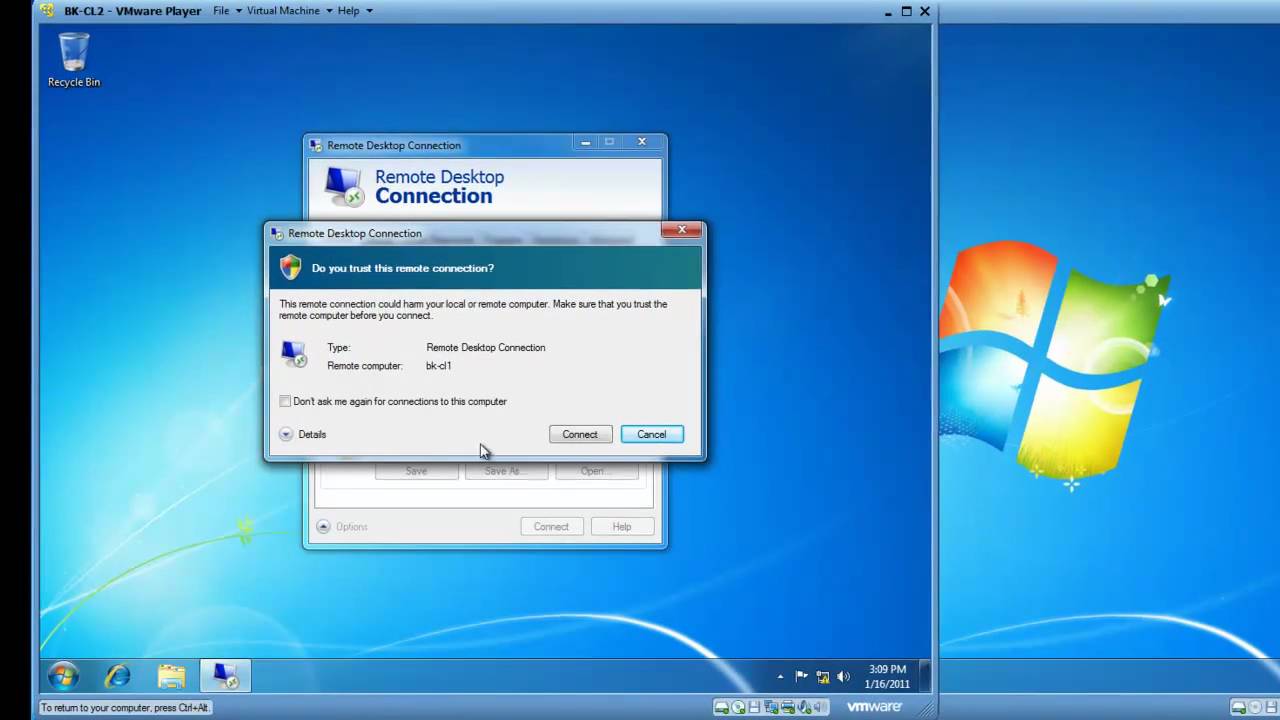
The Ke3chang APT has a substantial list of hacking tools, and one of them is the MirageFox RAT (Remote Access Trojan). The MirageFox RAT is usually utilized as a second-stage payload. The threat allows the Ke3chang group to carry out a variety of threatening tasks on the compromised host.
Full Answer
What is RAT software?
RAT can also stand for remote administration tool, which is software giving a user full control of a tech device remotely. With it, the user can ac...
What’s the difference between the RAT computer virus and RAT software?
As for functions, there is no difference between the two. Yet, while remote administration tool is for legit usage, RAT connotes malicious and crim...
What are the popular remote access applications?
The common remote desktop tools include but are not limited to TeamViewer, AnyDesk, Chrome Remote Desktop, ConnectWise Control, Splashtop Business...
What is Remote Access Trojan? (RAT)
Remote access trojan or RAT is a type of malware that provides attackers with the ability to control a computer or a device via an established remote connection. One of the goals of this malware is to steal information and spy on your system or network. Typically, RAT trojan enters your system by disguising it as legitimate software.
Different Types of Remote Access Trojan (RAT)
Remote access trojan has different types and uses. Below are some of the most commonly known RAT programs:
How to Address Remote Access Trojans (RAT) Malware Detection
The good thing about remote access trojan is that you can defend your system and network against it. However, addressing such malware can sometimes, be difficult to accomplish. This is due to the technological complexity most cybercriminals and attackers use in creating such malware threats.
How to protect yourself from remote access trojans?
Just like protecting yourself from other network malware threats, for remote access trojan protection, in general, you need to avoid downloading unknown items; keep antimalware and firewall up to date, change your usernames and passwords regularly; (for administrative perspective) block unused ports, turn off unused services, and monitor outgoing traffic.
What is a RAT trojan?
RAT trojan is typically installed on a computer without its owner’s knowledge and often as a trojan horse or payload. For example, it is usually downloaded invisibly with an email attachment, torrent files, weblinks, or a user-desired program like a game. While targeted attacks by a motivated attacker may deceive desired targets into installing RAT ...
How does RAT malware work?
Once get into the victim’s machine, RAT malware will hide its harmful operations from either the victim or the antivirus or firewall and use the infected host to spread itself to other vulnerable computers to build a botnet.
Why is Darkcomet no longer available?
The reason is due to its usage in the Syrian civil war to monitor activists as well as its author’s fear of being arrested for unnamed reasons.
Why do RATs use a randomized filename?
It is kind of difficult. RATs are covert by nature and may make use of a randomized filename or file path structure to try to prevent identification of itself. Commonly, a RAT worm virus does not show up in the lists of running programs or tasks and its actions are similar to those of legal programs.
Is Sub 7 a trojan horse?
Typically, Sub 7 allows undetected and unauthorized access. So, it is usually regarded as a trojan horse by the security industry. Sub7 worked on the Windows 9x and Windows NT family of OSes, up to and including Windows 8.1. Sub7 has not been maintained since 2014. 4.
Who created DarkComet?
5. DarkComet. DarkComet is created by Jean-Pierre Lesueur, known as DarkCoderSc, an independent programmer and computer security coder from France. Although this RAT application was developed back in 2008, it began to proliferate at the start of 2012.
What is intrusion detection?
Intrusion detection systems are important tools for blocking software intrusion that can evade detection by antivirus software and firewall utilities. The SolarWinds Security Event Manager is a Host-based Intrusion Detection System. However, there is a section of the tool that works as a Network-based Intrusion Detection System. This is the Snort Log Analyzer. You can read more about Snort below, however, you should know here that it is a widely used packet sniffer. By employing Snort as a data collector to feed into the Snort Log Analyzer, you get both real-time and historic data analysis out of the Security Event Manager.
Who created DarkComet?
French hacker Jean-Pierre Lesueur developed DarkComet in 2008, but the system didn’t really proliferate until 2012. This is another hacker system that targets the Windows operating system from Windows 95 up to Windows 10. It has a very easy-to-use interface and enables those without technical skills to perform hacker attacks.
Can a Remote Access Trojan be installed to BIOS?
Access to the BIOS has been known to the world’s hackers since 2015. Many believe that the NSA was planting RATs and trackers on BIOS even earlier.
What ports does Mirage use?
From the activity CTU researchers have observed when executing Mirage in a malware sandbox, this communication commonly occurs over ports 80, 443 and 8080, and it can implement SSL for added security.
What is Mirage's malware family?
The data sent by Mirage shares attributes with the malware family known as JKDDOS, which was researched by Arbor Networks. In its initial phone-home connection, JKDDOS sends a system profile to the C2 server. This profile contains the CPU speed, memory size, system name and username. Similar information and encoding techniques are seen in the initial phone-home requests of Mirage infections.
What are the droppers in Mirage?
However, the droppers are stand-alone executable files that open an embedded PDF file and execute the Mirage trojan. In one example, CTU researchers observed an executable file (MD5 hash ce1cdc9c95a6808945f54164b2e4d9d2) that upon execution drops a copy of Mirage and opens an embedded PDF of a news story titled " Yemeni Women can participate in politics just like men, says President Saleh " that was posted on the Yemen Observer's website.
What malware family uses the same encoding algorithm as Mirage?
The CTU research team has seen the encoding used in variant 2 in other malware families. One such malware family is Lingbo, which uses a similar encoding algorithm but does not contain some of the major characteristics of Mirage. Samples from both malware families have included strange embedded quotes. Instead of Mirage's quote from The Matrix, Lingbo contains the embedded quote "It is the end of the world and I feel Fine", from the REM song "It's the end of the world."
What is the initial payload of Mirage?
From there, Mirage encodes and sends the MAC address, CPU information, system name and username in the initial request to the C2 server.
What happens when Mirage is executed?
When Mirage executes, the original file copies itself to a folder under C:Documents and Settings<USER> or C:Windows and then deletes the original file. After the initial copy, Mirage starts the newly created file and exits the original. The newly started copy creates registry keys to ensure that the system remains infected after every reboot. CTU researchers have observed the following filenames created after execution:
What is the second variant of Mirage?
The second variant of Mirage uses HTTP GET requests instead of HTTP POST requests to transmit the phone-home requests' payload. This evolved variant's initial phone-home request's payload is contained in a Base64-encoded string in the initial request. The decoded Base64 payload contains a second level of encoding that has several variations. The data being transmitted in the encoded string contains the same data as the previous variant, as well as some additional data. One change is the text at the beginning of the phone-home payload. Instead of the word "Mirage" used in earlier variants, later variants use the phrase "Neo, welcome to the desert of the real", a quote from the movie The Matrix.