Go to Policies > Network Policies, double-click Connections to Microsoft Routing and Remote Access server policy, select Grant access, and then click OK. Log on to Azure portal. Open the virtual network gateway that you created. Make sure that the gateway type is set to VPN and that the VPN type is route-based.
Full Answer
How to enable Microsoft routing and remote access server (Ras)?
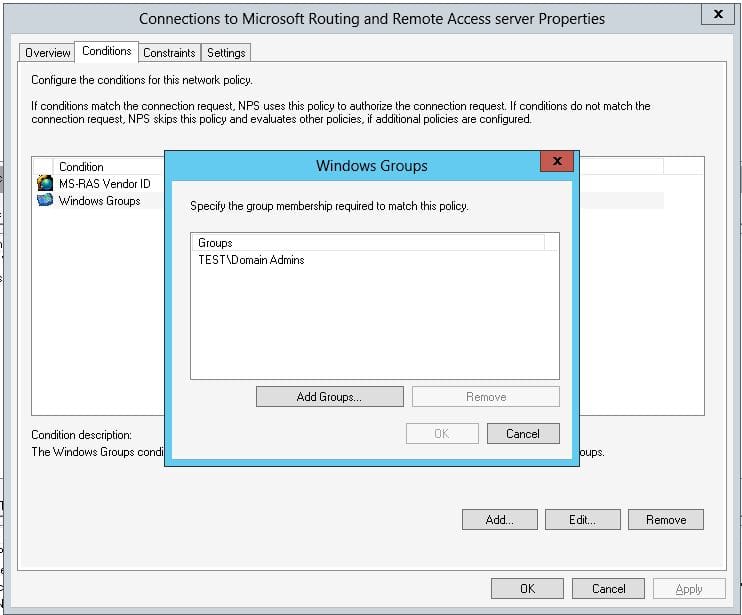
Some Internet Forums claim to have had success by setting the “Connections to Microsoft Routing and Remote Access server” to enabled. To do this, click on the “Network Policies” item on the left, then right-click “Connections to Microsoft Routing and Remote Access Server” and select “Properties”.
How do I grant remote access to my Network in Windows?
To do this, click on the “Network Policies” item on the left, then right-click “Connections to Microsoft Routing and Remote Access Server” and select “Properties”. On the “Overview” tab, in the “Access Permissions” section, set the radio button to “Grant Access” and apply. In our particular case we had to go one step further.
How do I create a remote access policy in Windows 10?
Create a group that contains members who are permitted to create VPN connections. Click Start, point to Administrative Tools, and then click Routing and Remote Access. In the console tree, expand Routing and Remote Access, expand the server name, and then click Remote Access Policies.
How do I set up a network policy in NPS?
Open the NPS UI, click Policies, and then click Network Policies. Right-click Connections to Microsoft Routing and Remote Access Server, and then select Properties. On the Properties UI, click the Constraints tab.

What is Microsoft Network Policy Server?
Network Policy Server (NPS) is the Microsoft implementation of a Remote Authentication Dial-in User Service (RADIUS) server and proxy. It is the successor of Internet Authentication Service (IAS).
How are network connection request policies processed by NPS?
NPS does not process any connection requests on the local server. Instead, it forwards connection requests to NPS or other RADIUS servers that are configured as members of remote RADIUS server groups.
What is network policy and Access Services?
Microsoft Network Policy and Access Services (Microsoft NPAS) is a server role in Windows Server 2008 and Windows Server 2012 that allows administrators to provide local and remote network access.
What are the three components that make up a NPS network policy?
As seen in Figure 4.36, NPS includes a configuration wizard that allows you to do a basic configuration. You have three options: Network Access Protection (NAP), RADIUS server for Dial-up or VPN Connections, and RADIUS server for 802.1X Wireless or Wired Connections.
What is Network Policy Server NPS and when should it be implemented on a given network?
Network Policy Server (NPS) allows you to create and enforce organization-wide network access policies for connection request authentication and authorization.
What is control access through NPS network policy?
An NPS policy is a set of permissions or restrictions that are used by remote access authenticating servers that determine who, when, and how a client can connect to a network. With remote access policies, connections can be authorized or denied based on user attributes, group membership, and so on.
Why is it important to have network Policy and Access Services?
Network Policy and Access Services (NPAS) is a component of Windows Server 2008. It replaces the Internet Authentication Service (IAS) from Windows Server 2003. NPAS helps you safeguard the health and security of a network.
What are the roles of network policy?
Network policies are sets of conditions, constraints, and settings that allow you to designate who is authorized to connect to the network and the circumstances under which they can or cannot connect.
How do I find my Network Policy Server?
Configure NPSIn Server Manager, select Tools, and then select Network Policy Server. The NPS console opens.In the NPS console, right-click NPS (Local), then select Register server in Active Directory. The Network Policy Server dialog box opens.In the Network Policy Server dialog box, select OK twice.
What are the 5 network policies?
They include Acceptable Use, Disaster Recovery, Back-up, Archiving and Failover policies. People who need access to a network to do their job are usually asked to sign an agreement that they will only use it for legitimate reasons related to doing their job before they are allowed access.
What should be included in a network access policy?
What Should You Address in a Remote Access Policy?Standardized hardware and software, including firewalls and antivirus/antimalware programs.Data and network encryption standards.Information security and confidentiality.Email usage.Physical and virtual device security.Network connectivity, e.g., VPN access.More items...•
What should be in a network policy?
Any policy guidelines created for organisational implementation should include the following four areas: overview, policy, scope, and enforcement. In the overview section, you must give a summary of each policy outlined in the document. This will allow the reader to understand it at a glance.
Where are NPS logs in Event Viewer?
On the Log File tab, in Directory, type the location where you want to store NPS log files. The default location is the systemroot\System32\LogFiles folder.
Which authentication type is used with the Extensible authentication Protocol?
EAP uses the 802.1x standard as its authentication mechanism over a local area network or a wireless LAN (WLAN). There are three primary components of 802.1X authentication: the user's wireless device; the wireless access point (AP) or authenticator; and.
Which of the following options is a requirement for a client to accept a certificate from an NPS server?
Which of the following options is a requirement for a client to accept a certificate from an NPS server? The RADIUS server sends an Access-Request message, including a user name and password combination or a certificate from the user, to an NPS server acting as a RADIUS client.
Which form of authentication is used for smart cards and certificates along with MSCHAPv2?
Authentication With EAP-TLS and PEAP-MSCHAPv2 With PEAP-MSCHAPv2, the user must enter their credentials to be sent to the RADIUS Server that verifies the credentials and authenticates them for network access. EAP-TLS utilizes certificate-based authentication.
How to install Remote Access Role in VPN?
On the VPN server, in Server Manager, select Manage and select Add Roles and Features. The Add Roles and Features Wizard opens. On the Before you begin page, select Next.
How to start remote access?
Select Start service to start Remote Access. In the Remote Access MMC, right-click the VPN server, then select Properties. In Properties, select the Security tab and do: a. Select Authentication provider and select RADIUS Authentication.
How to select a server from the server pool?
On the Select destination server page, select the Select a server from the server pool option. Under Server Pool, select the local computer and select Next. On the Select server roles page, in Roles, select Remote Access, then Next. On the Select features page, select Next. On the Remote Access page, select Next.
How many Ethernet adapters are needed for VPN?
Install two Ethernet network adapters in the physical server. If you are installing the VPN server on a VM, you must create two External virtual switches, one for each physical network adapter; and then create two virtual network adapters for the VM, with each network adapter connected to one virtual switch.
What is NAS in a network?
A NAS is a device that provides some level of access to a larger network. A NAS using a RADIUS infrastructure is also a RADIUS client, sending connection requests and accounting messages to a RADIUS server for authentication, authorization, and accounting. Review the setting for Accounting provider: Table 1.
What is MMC in Microsoft?
The Routing and Remote Access Microsoft Management Console (MMC) opens.
Can you assign a VPN to a pool?
Additionally, configure the server to assign addresses to VPN clients from a static address pool. You can feasibly assign addresses from either a pool or a DHCP server; however, using a DHCP server adds complexity to the design and delivers minimal benefits.
What is NAP in computer security?
Network Access Protection (NAP) includes client components and server components that allow you to define the required software and system configurations for computers that connect to your network. NAP enforces health requirements by inspecting and assessing the health of client computers, limiting network access when client computers are noncompliant, and remediating noncompliant client computers for unlimited network access. NAP enforces health requirements on client computers that are attempting to connect to a network. NAP also provides ongoing health compliance enforcement while a compliant client computer is connected to a network.
What certificate is used for PEAP-MS-CHAP v2?
If you are using PEAP-MS-CHAP v2, issue server certificates with either AD CS or purchase server certificates from a trusted root certification authority (CA).
What is OSI model?
7 layers OSI model is a short name for the Open Systems Interconnection (OSI) reference model for networking. This theoretical model explains how networks behave within an orderly, seven-layered...
What is a rras?
What is RRAS (Routing and Remote Access Service)? RRAS stands for Routing and Remote Access Service is a feature of Windows Server operating systems family that provides additional support for TCP/IP internetworking.
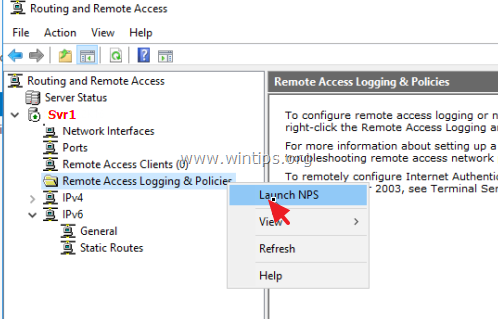
How to launch NPS?
Open the “Routing and Remote Access” console, expand the server, right-click “Remote Access Logging & Policies” and select “Launch NPS”.
Does RAS VPN need to be adjusted?
Typically in a RAS VPN setup on a Windows Server, the NPS settings do not need to be adjusted and work with the defaults. In this particular case it was the default NPS settings on the RAS server that were causing the authentication error.
How to check security of RRAS server?
In the RRAS Server Management window, open the Server Properties dialog box, and then click the Security tab.
What is the Microsoft Challenge Handshake Authentication Protocol version 2?
Microsoft Challenge Handshake Authentication Protocol version 2 (MS-CHAP v2) is a password-based authentication protocol which is widely used as an authentication method in PPTP-based (Point to Point Tunneling Protocol) VPNs. Microsoft cautions that any organizations that use MS-CHAP v2 without encapsulation in conjunction with PPTP tunnels for VPN connectivity are running in a potentially nonsecure configuration.
How to configure NPS?
Configure connections for NPS#N#Configure the Network Policy Server (NPS) to only allow connections from clients that use the PEAP-MS-CHAP v2 authentication method. To configure NPS, follow these steps: 1 Open the NPS UI, click Policies, and then click Network Policies. 2 Right-click Connections to Microsoft Routing and Remote Access Server, and then select Properties. 3 On the Properties UI, click the Constraints tab. 4 In the left Constraints pane, select Authentication Methods, and then click to clear the check boxes for the MS-CHAP and MS-CHAP-v2 methods. 5 Remove EAP-MS-CHAP v2 from the EAP Types list. 6 Click Add, select PEAP authentication method, and then click OK.#N#Note A valid Server certificate must be installed in the "Personal" store, and a valid root certificate must be installed in the "Trusted Root CA" store of the server before configuring the NPS connection. 7 Click Edit, and then select EAP-MS-CHAP v2 as the authentication method.
How to clear the checkboxes for MS-CHAP?
Open the NPS UI , click Policies, and then click Network Policies. Right-click Connections to Microsoft Routing and Remote Access Server, and then select Properties. On the Properties UI, click the Constra ints tab. In the left Constraints pane, select Authentication Methods, and then click to clear the check boxes for the MS-CHAP ...
What is a RRAS in Windows Server 2008?
In the RRAS there are a number of snap-in roles that can be used in configuring and setting up your network access needs for Windows Server 2008. In previous incarnations of Windows Server 2003, Internet Authentication Service (IAS) snap-in was Microsoft's implementation of a Remote Authentication Dial-in User Service (RADIUS) server and proxy. It was capable of performing localized connection AAA Protocol for many types of network access, including wireless and VPN connections.
What is access control?
Access control in general terms is a relationship triad among internal users, intranet resources, and the actions internal users can take on those resources. The idea is to give users only the least amount of access they require to perform their job. The tools used to ensure this in Windows shops utilize Active Directory for Windows logon scripting and Windows user profiles. Granular classification is needed for users, actions, and resources to form a logical and comprehensive access control policy that addresses who gets to connect to what, yet keeping the intranet safe from unauthorized access or data-security breaches. Quite a few off-the-shelf solutions geared toward this market often combine inventory control and access control under a “desktop life-cycle” planning umbrella.
How to install NPS in Windows Server 2012?
To install the NPS role service in Windows Server 2012 using PowerShell, you first need to right-click the PowerShell icon on the taskbar and select Run as administrator in order to open a PowerShell session with administrative privileges. Then perform the following steps:
Why is user authentication important?
The reason this is important is because without validating the client that is being used to dial into the remote access mechanism, there is not a way to protect the network from the security state that the client might be in.
What is the first priority of an information security officer?
The first priority of an information security officer in most organizations is to ensure that there is a relevant corporate policy on access controls. Simple on the surface, the subject of access control is often complicated by the variety of ways the intranet is connected to the external world.
What is a Deny All policy?
Typically, security administrators start with a “Deny-All” policy as a baseline before slowly building in the access permissions. As users migrate from one department to another, are promoted, or leave the company, in large organizations this job can involve one person by herself. This person often has a very close working relationship with Purchasing, Helpdesk, and HR, getting coordination and information from these departments on users who have separated from the organization and computers that have been surplused, deleting and modifying user accounts and assignments of PCs and laptops.
How to load server manager module?
Load the Server Manager module by typing: Import-Module Servermanager