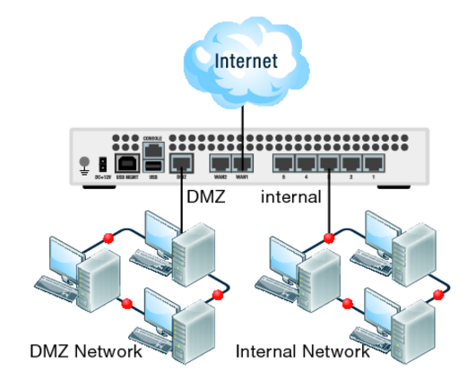
How do you connect to a remote network?
How to Remotely Access Another Computer Over the Internet Within Your Network
- Click the magnifying glass icon in the bottom-left corner of your screen. ...
- Then type About into the search bar and click Open.
- Next, copy your computer’s name. ...
- Then open the Windows search bar and type remote desktop connection. ...
- Next, click Open.
- Then click Show Options. ...
- Next, enter the computer’s name. ...
- Also, enter the username. ...
- Then click Connect. ...
How to access home network remotely?
To allow a remote PC to accept remote connections, do the following:
- Open Control Panel.
- Click on System and Security.
- Click on Allow remote access.
- Under Remote Desktop make sure to select Allow remote connections to this computer.
How do access remote network with OpenVPN?
Using OpenVPN to Securely Access Your Network Remotely
- Visit http://tplinkwifi.net, and log in with your TP-Link ID or the password you set for the router.
- Go to Advanced > VPN Server > OpenVPN, select the checkbox to enable VPN Server.
- Select the Service Type (communication protocol) for OpenVPN Server: UDP, TCP.
How to accept remote network connection?
- In the Windows Firewall with Advanced Security dialog click on the Inbound Rules option and select the New Rule command:
- In the New Inbound Rule wizard select the Port option and click Next:
- In the Protocols and Ports window specify the protocols and ports to which a rule applies. ...

What is remote access in networking?
Remote access is the act of connecting to IT services, applications, or data from a location other than headquarters. This connection allows users to access a network or computer remotely via the internet.
How do you protect remote access?
Basic Security Tips for Remote DesktopUse strong passwords. ... Use Two-factor authentication. ... Update your software. ... Restrict access using firewalls. ... Enable Network Level Authentication. ... Limit users who can log in using Remote Desktop. ... Set an account lockout policy.
What are the security threats with remote access and how can it be secured?
Many remote access security risks abound, but below is a list of the ones that jump out.Lack of information. ... Password sharing. ... Software. ... Personal devices. ... Patching. ... Vulnerable backups. ... Device hygiene. ... Phishing attacks.
What are some security issues in remote access?
Five Remote Access Security Risks And How To Protect Against ThemWeak remote access policies. ... A deluge of new devices to protect. ... Lack of visibility into remote user activity. ... Users mixing home and business passwords. ... Opportunistic phishing attempts.
Is remote access security secure?
Yes. A robust cloud-based, highly secure remote access solution can provide unified protection for virtually all users against web-based threats — independent of a VPN connection.
What is the best practice for accessing a network remotely?
Here are some best practices to make remote access as secure as possible:Enable encryption. ... Install antivirus and anti-malware. ... Ensure all operating systems and applications are up to date. ... Enforce a strong password policy. ... Use Mobile Device Management (MDM) ... Use Virtual Private Network (VPN) ... Use two-factor authentication.More items...•
What types of attacks are remote access servers vulnerable to?
Other attacks which hackers can facilitate through remote access include email phishing, third-party vendor compromise, insider threats, social engineering, and the use of vulnerable applications to compromise systems. Hackers use Common remote access tools to penetrate third-party access to merchant information ...
What is required for remote access?
Remote computer access requires a reliable internet connection. You'll need to activate or install software on the device you want to access, as well as on the device — or devices — you want to use to get that access.
Can VPN stop remote access?
While having some similarities, VPN and remote desktop are functionally different things. A VPN will give you access to a network while remote desktop (or RDP) will give you control of an entire computer. If you want to have full control over a local computer from a remote location, VPN won't let you achieve that.
How do I stop unauthorized remote access?
Here are our recommendations to help you prevent unauthorized data access:Keep Current on all Security Patches. ... Detect and Respond to Intrusions Quickly. ... Implement Principle of Least Privilege (Minimize Data Access) ... Use Multi-Factor Authentication. ... Implement IP Whitelisting. ... Encrypt Network Traffic Inside the System.More items...•
What can we do in order to limit or prevent remote access?
Firewalls can be your first line of defense in network security by limiting those who have remote access. You should set up firewalls to restrict access using software or hardware or both. Update your software regularly. Make sure your software updates automatically so you're working with the latest security fixes.
What is a common way to help protect devices connected to the company network?
What is a common way to help protect devices connected to the company network? A. Only use laptops and other mobile devices with full-disk encryption. This is correct!
What does SASE mean for remote access?
What does this mean for the remote access worker? SASE makes it very quick and easy to give optimized and highly secure access to any and all workers. For users in the office, access can be limited only to designated resources, complying with zero-trust principles.
What is a SASE network?
SASE converges Zero Trust Network Access, NextGen firewall (NGFW), and other security services along with network services such as SD-WAN, WAN optimization, and bandwidth aggregation into a cloud-native platform. Enterprises that leverage a SASE networking architecture receive the benefits of ZTNA, plus a full suite of converged network and security solutions that is both simple to manage and highly-scalable. SASE provides all this in a cloud-native platform.
Why are VPNs so secure?
While VPNs provide traffic encryption and user authentication, they still present a security risk because they grant access to the entire network without the option of controlling granular user access to specific resources. There is no scrutiny of the security posture of the connecting device, which could allow malware to enter the network. To maintain proper security, traffic must be routed through a security stack at the VPN’s terminus on the network. In addition to inefficient routing and increased network latency, this can result in having to purchase, deploy, monitor, and maintain security stacks at multiple sites to decentralize the security load. Simply put, VPNs are a challenge – an expensive one at that – when it comes to remote access security.
What are the security considerations when deploying a remote access solution?
Security considerations are always a major issue when deploying a remote access solution, and the difficulties are compounded when solutions must include support for embedded systems. Successful implementations must provide effective authentication and access control, and care must also be taken to ensure that data is secured during transport over the network.
What is network based access control?
Network-based access controls are used to ensure that only authorized hosts are allowed to establish connections to your networked devices. Such access control usually takes the form of Firewalls that may work at Layer 2 (also referred to as the data link layer in the OSI Seven Layer Networking Model) or Layer 3 (the network layer).
What is machine to machine remote management?
One commercial offering that addresses these challenges is a machine-to-machine remote management device capable of providing easy yet secure remote Internet access to IP-enabled equipment– even when such equipment is located behind remote firewalls or a VPN. Readily adaptable to a wide range of management tasks, such devices are suited for accessing and managing embedded systems located on remote customer networks. They are also appropriate where support staff do not have administrator privileges on the remote network.
What is a VPN?
The networking industry’s initial response to the growing remote access challenge was the virtual private network (VPN). As its name implies, a VPN replaces dedicated leased lines, cellular links or other costly physical connections with a secure mechanism over which traffic from a remote device can be tunneled to the target network using an existing network connection.
What is additional consideration when target devices are hosted as guests on remote networks administered by others?
In such cases particular care must be taken to ensure that your systems do not open the hosting network to outside threats.
Does firewall technology help with external threats?
The success of firewall technology in addressing external network threats did not come without a price – universal deployment of firewalls has greatly aggravated the difficulty of providing remote access to network devices.
Is network security based on technology?
Effective network security is not based on any one technology or component; it is most successful when it is built up using a layered approach, following the OSI Seven Layer Networking Model, with multiple defenses contributing to the overall solution. Here we review some common technologies for developing secure remote access solutions, along with some of the real-world challenges faced. We will also examine one commercial offering that addresses these challenges in an innovative and cost-effect way.
Types of Tunneling and Encryption
Tunneling involves using protocols to encapsulate or encrypt data packets so that will pass through the Internet in a secure fashion. Think of encapsulation and tunneling like peas in a pod. The peas are the data packets (unencrypted) and the pod encapsulates or encrypts the peas so they cannot be seen.
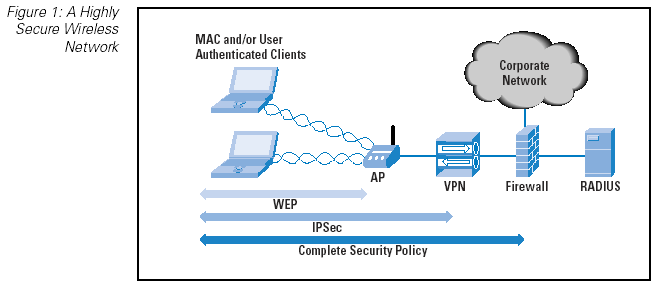
Remote Access
Here is a high level example (Figure 1) of how a remote host can connect to an internal corporate network which can be referred to when reviewing the types of remote access solutions: Remote Access Service (RAS), Point-to-Point over Ethernet (PPPoE), Remote Desktop Protocol (RDP), Independent Computing Architecture (ICA), and Secure Shell (SSH).
Network Intrusion & Protection
An Intrusion Detection System (IDS) and Intrusion Prevention System (IPS) are network security appliances that can be host-based, network-based or a combination of both.
Network Security Traps
A honeypot is a computer host that has been set up to attract hackers to learn what tactics they are using to infiltrate a network. It monitors their movements and gives a network administrator insight to where future attacks may come from.
What is remote access VPN?
The most basic form of VPN remote access is through a RAS. This type of VPN connection is also referred to as a Virtual Private Dial-up Network (VPDN) due to its early adoption on dial-up internet.
What is the first thing that’s required to ensure smooth remote access via a VPN?
The first thing that’s required to ensure smooth remote access via a VPN is to plan out a comprehensive network security policy.
Why is IPSEC used?
This allows IPSec to protect data transmission in a variety of ways. IPSec is used to connect a remote user to an entire network. This gives the user access to all IP based applications. The VPN gateway is located at the perimeter of the network, and the firewall too is setup right at the gateway.
What are the implications of IPSec connections for corporations?
What are the implications of IPSec connections for corporations, considering the very nature of this connection? Well, your employee will only be able to access the network from a single, authorized device. Security is further boosted by the enforcement of antivirus and firewall policies.
What is IPSEC encryption?
IPSec is an IP packet authentication and encryption method. It uses cryptographic keys to protect data flows between hosts and security gateways.
Why use two factor authentication for VPN?
Adopting two-factor authentication for remote access through VPN further boosts your network security. Now let’s take a look at why you should choose a particular VPN type as a secure connection methodology instead of the alternatives.
What is the line of defense for remote access?
So, you have a three-layer line of defense working to protect remote access to your network: anti-virus, firewall, and VPN. The network security team should monitor alerts from these defenses constantly.
What is secure remote access?
Secure remote access refers to any security policy, solution, strategy or process that exists to prevent unauthorized access to your network, its resources, or any confidential or sensitive data. Essentially, secure remote access is a mix of security strategies and not necessarily one specific technology like a VPN.
What technologies are used for secure remote access?
Secure remote access is comprised of a multitude of security solutions and technologies. Some of the most prominent include the following:
Secure remote access solution
Enables employees with precise access to the applications and data required to do their job from anywhere.
Why is secure remote access important?
With the work from home shift in the workforce, endpoints are accessing corporate networks from multiple locations. Today, employees’ home networks are often the originating point for network connections, multiplying the risk on both home and corporate networks.
What are the benefits of secure remote access?
While the benefits of secure remote access are numerous, there are four key advantages in which to focus on:
Can secure remote access be achieved without VPN?
Yes. A robust cloud-based, highly secure remote access solution can provide unified protection for virtually all users against web-based threats — independent of a VPN connection.
How can AT&T help organizations with secure remote access?
AT&T Cybersecurity is uniquely positioned to help organizations address these immediate challenges with an eye toward the future by helping them balance connectivity, collaboration, and cybersecurity affordably.
Author: Haris Khan
Remote work is the new normal for IT teams around the globe, and there is no surprise as to why remote work is becoming so increasingly popular for organizations. The modern employee workforce is no longer restricted to one physical location.
What is secure remote access?
Secure remote access refers to the technology used for securely accessing a system or application remotely. Cybercriminals and malicious actors are consistently looking out for vulnerabilities and loopholes in remote work infrastructures to exploit and plan cyber attacks.
Which technologies are used for remote work access?
Secure remote access can be effectively implemented by utilizing a collection of highly innovative, secure, and flexible technologies while accessing a system or application from a remote location A few prominent examples of such technologies are listed below:
10 Best Practices for Secure Remote Work Access
Some of the best practices that you can adopt to improvise remote access security in your organization are described below:
Why cloud desktops are an optimal choice for secure remote access?
Cloud desktop solutions offer greater flexibility and ease of access as all of your files, applications and desktop reside on the cloud. Cloud desktops are one of the most resilient and secure forms of remote access.
All-In-One Secure Remote Access with V2 Cloud
As the organizational trend keeps transitioning to remote work, it’s crucial to comprehend the numerous cybersecurity risks and threats that are associated with remote access security. Remote work has become an increasingly viable option with tons of advantages.
What should security teams do if on-premises network and email security mechanisms are no longer available?
Recommendation: If some on-premises network and email security mechanisms are no longer available, security teams should double down on educating users to identify phishing attempts and to choose strong, unique passwords, encouraging the use of a password manager. They should also implement client certificates and multi-factor authentication in order to prevent attackers from gaining access through unsecured devices.
Why is it important to enforce access based on user identity?
Recommendation: It’s critical that companies enforce access based on user identity, allowing specific groups access to only what they need to get their jobs done, and expanding access from there on an as-needed basis.
Why do companies use VPNs?
Historically, many companies deployed VPNs primarily for technical people needing access to critical technology assets. Not so much the case anymore – VPNs are often encouraged for all users as a more secure connection than home or public networks.
What are the risks of using a VPN?
Here are five top security risks that teams must deal with, as well as technology and user education best practices to keep users and data safe: 1. Weak remote access policies. Once attackers get access to a virtual private network (VPN), they can often penetrate the rest of the network like a hot knife through butter.
What is XDR in security?
Recommendation: Rather than invest in point solutions, consider security platforms that maximize integration between systems, limiting the amount of switching between tools and providing visibility into all data – including remote user activity. Extended detection and response (XDR) not only protects endpoints, but also applies analytics across all your data to find threats like unusual access or lateral movement, and simplifies investigations by stitching together data and identifying the root cause.