NIST also recommends placing remote access servers at the network perimeter and defines four types of remote access methods: Tunneling servers provide administrators control over the internal resources for remote worker access at the network perimeter. Portal servers that run the application client software on the servers themselves.
What are the NIST guidelines for remote work security?
Below are key guidelines recommended by the National Institute of Standards and Technology ( NIST) in supporting standard users, privileged administrators, BYOD and third parties. Plan remote work-related security policies and controls based on the assumption that external environments contain hostile threats.
What is NIST Special Publication 800-46 Revision 2?
This bulletin summarizes highlights from NIST Special Publication 800-46 Revision 2, Guide to Enterprise Telework, Remote Access, and Bring Your Own Device (BYOD) Security, which helps organizations protect their IT systems and information from the security risks that accompany the use of telework and remote access technologies.
Do I need a NIST credential to access NIST?
NIST credentials are required to use either of these services. If a user encounters trouble accessing NIST remotely, the following questions/answers may assist in troubleshooting. I tried to connect to inside.nist.gov, and got the error message: "If you are experiencing connectivity issues, please click here for possible solutions, or call iTAC."
How do I enforce access restrictions for remote access?
Enforcing access restrictions for remote access is addressed via AC-3. Employ automated mechanisms to monitor and control remote access methods. Implement cryptographic mechanisms to protect the confidentiality and integrity of remote access sessions. Route remote accesses through authorized and managed network access control points.

What is a remote access standard?
PURPOSE. Remote Access refers to the ability to access UMW network resources while off campus. Security measures for remote access should be implemented based on sensitivity and risk to University systems and data. Standard.
What are the security requirements for remote access?
7 Best Practices For Securing Remote Access for EmployeesDevelop a Cybersecurity Policy For Remote Workers. ... Choose a Remote Access Software. ... Use Encryption. ... Implement a Password Management Software. ... Apply Two-factor Authentication. ... Employ the Principle of Least Privilege. ... Create Employee Cybersecurity Training.
What is the NIST 800 171?
NIST SP 800-171 is a NIST Special Publication that provides recommended requirements for protecting the confidentiality of controlled unclassified information (CUI).
What is remote access examples?
Accessing, writing to and reading from, files that are not local to a computer can be considered remote access. For example, storing and access files in the cloud grants remote access to a network that stores those files. Examples of include services such as Dropbox, Microsoft One Drive, and Google Drive.
Which protocol would be best to use to securely access the remote network devices?
Remote Desktop Protocol or RDP is a communications protocol designed to manage remote access to desktops, files, systems, and even private networks.
What is remote access in cyber security?
Secure Remote Access is a combination of security processes or solutions that are designed to prevent unauthorized access to an organization's digital assets and prevent the loss of sensitive data.
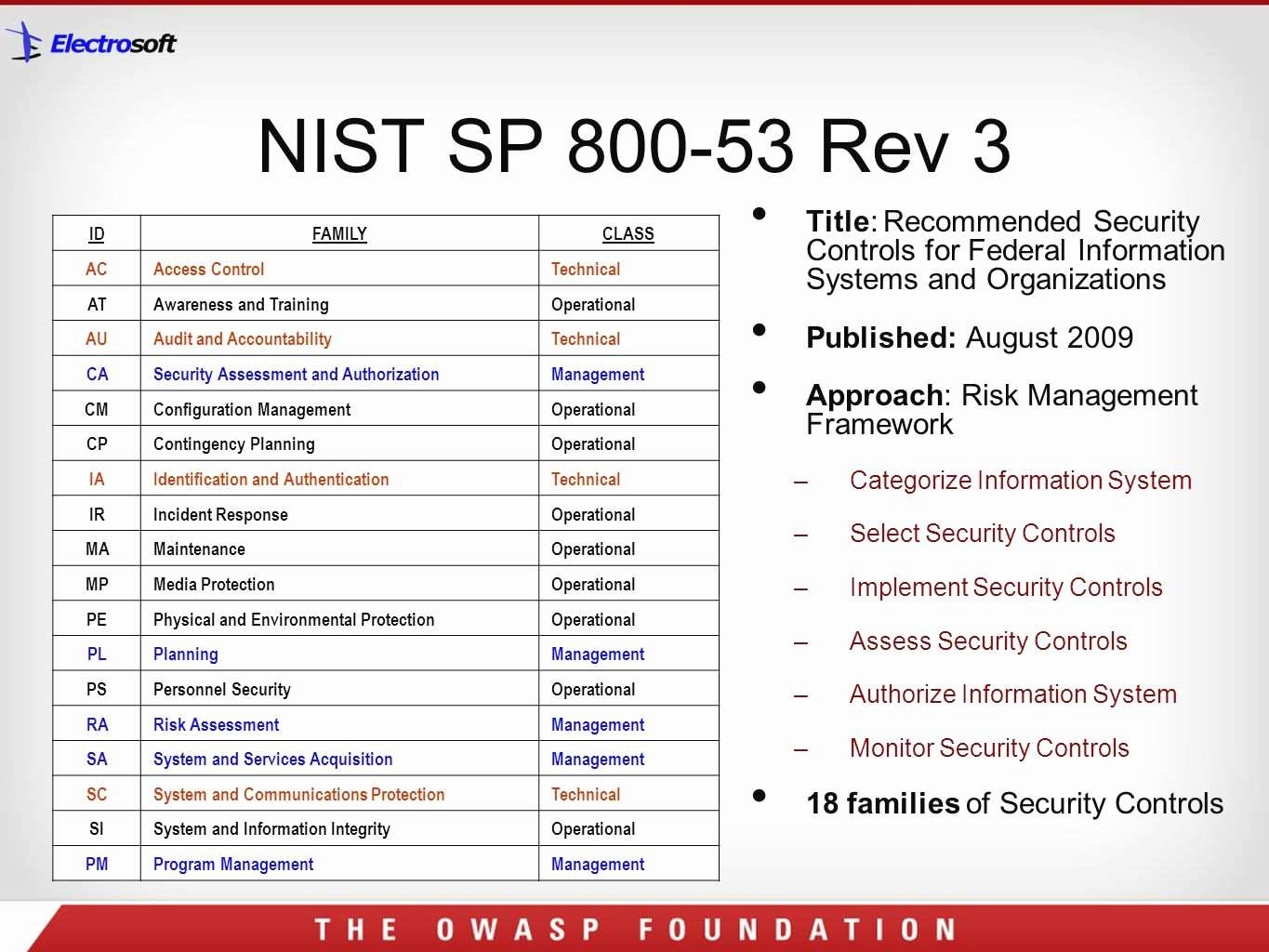
What is the purpose of NIST 800-53?
What is the purpose of NIST 800-53? The NIST 800-53 framework is designed to provide a foundation of guiding elements, strategies, systems, and controls, that can agnostically support any organization's cybersecurity needs and priorities.
What is NIST 800-39?
NIST Special Publication 800-39 is the guidance for an organization-wide program for information security risk management. It uses multi-tiered approach (see below) and describes the information security risk management cycle.
What is NIST 800 30?
The purpose of Special Publication 800-30 is to provide guidance for conducting risk assessments of federal information systems and organizations, amplifying the guidance in Special Publication 800-39.
What are the three types of remote connections?
Remote Access Control MethodsDirect (Physical) Line. The first direct remote access control that can be implemented is a direct line from a computer to the company's LAN. ... Virtual Private Network. Another method which is more common is establishing a VPN. ... Deploying Microsoft RDS.
Can someone remotely access my computer when IT's off?
Without appropriate security software installed, such as anti-malware tools like Auslogics Anti-Malware, it is possible for hackers to access the computer remotely even if it is turned off.
Can someone remotely access my computer without my knowledge?
There are two ways someone can access your computer without your consent. Either a family member or work college is physically logging in to your computer or phone when you are not around, or someone is accessing your computer remotely.
How do I make my remote work secure?
Here are the top remote working security tips to ensure you and your staff are working from home safely.Use antivirus and internet security software at home. ... Keep family members away from work devices. ... Invest in a sliding webcam cover. ... Use a VPN. ... Use a centralized storage solution. ... Secure your home Wi-Fi.More items...
How do you keep security when employees work remotely?
Remote Work Security Best PracticesEstablish and enforce a data security policy. ... Equip your employees with the right tools and technology. ... Frequently update your network security systems. ... Regulate the use of personal devices. ... Institute a “Zero Trust” approach. ... Make sure all internet connections are secure.More items...
What security considerations do you think are important for users accessing their company desktops remotely?
Why do I need to secure remote access?1) Assume threats will occur.2) Create a telework policy.3) Encrypt sensitive information.4) Designate and secure specific remote work devices.5) Employ user authentication.6) Set up a VPN.7) Manage sensitive data securely.8) Collaborate with third-party partners and vendors.
What is remote access?
Definition (s): Access to an organizational information system by a user (or an information system) communicating through an external, non-organization-controlled network (e.g., the Internet). Source (s):
Where to send comments on a NIST publication?
Comments about specific definitions should be sent to the authors of the linked Source publication. For NIST publications, an email is usually found within the document.
What is an access system?
Access by users (or information systems) communicating external to an information system security perimeter. Access to an organizational system by a user (or a process acting on behalf of a user) communicating through an external network.
What is access to an organizational system?
Access to an organizational system by a user (or a process acting on behalf of a user) communicating through an external network (e.g., the Internet).
What is remote work security?
Remote work security policies should define the forms of remote access permitted, the types of devices that can be used and the type of access allowed for each type of remote worker. The policies should also cover how remote access servers are administered and how their policies are updated. Organizations should make risk-based decisions about ...
What is cloud native service?
Using the cloud-native service, administrators can leverage the cloud-native service to effortlessly provision and deprovision access to virtual machines, applications and services with granular role-based access profiles.
What is check point corporate access?
By supporting a variety of protocols, Check Point Corporate Access enables secure access to databases (SQL), administration terminals (SSH) and remote desktops (RDP). Integrating with any Identity Provider, its lightweight Privileged Access management (PAM) module offers built-in SSH server key management to ensure the security of an organization’s crown jewels.
Does remote desktop access involve remote access?
Remote desktop access does not involve remote access servers, so there is no issue with the placement of the remote access server. Direct application access servers run the application server software on the servers themselves. Placing them at the network perimeter has a similar effect as the remote access user is only running applications on ...
Why is remote access important?
The security of remote access servers, such as VPN gateways and portal servers, is particularly important because they provide a way for external hosts to gain access to internal resources, as well as a secured, isolated telework environment for organization-issued, third-party-controlled, and BYOD client devices. In addition to permitting unauthorized access to enterprise resources and telework client devices, a compromised server could be used to eavesdrop on communications and manipulate them, as well as a “jumping off” point for attacking other hosts within the organization. Recommendations for general server security are available from NIST SP 800-123, Guide to General Server Security. Remote access servers should be kept fully patched, operated using an organization-defined security configuration baseline, and managed only from trusted hosts by authorized administrators.
Where should a remote access server be placed?
Intermediate remote access servers connect external hosts to internal resources, so they should usually be placed at the network perimeter. The server acts as a single point of entry to the network from the perimeter and enforces the telework security policy. If remote access is needed to a particular sub-network within the organization, there are generally two options: 1) place the remote access server at the edge of the sub-network, where the sub-network joins the full network; or 2) place it at the perimeter of the full network and use additional mechanisms to restrict the teleworkers to only be able to access the specified sub-network. The value of placing the remote access server at the network perimeter versus the sub-network perimeter differs for the four types of remote access methods:
What is the key component of controlling access to network communications and protecting their content?
major component of controlling access to network communications and protecting their content is the use of cryptography. At a minimum, any sensitive information passing over the Internet, wireless networks, and other untrusted networks should have its confidentiality and integrity preserved through use of cryptography. Federal agencies are required to use cryptographic algorithms that are NIST-approved and contained in FIPS-validated modules. The FIPS 140 specification, Security Requirements for Cryptographic Modules, defines how cryptographic modules are validated.24 It is important to note that for a remote access system to be considered compliant to FIPS 140, both sides of the interaction must have passed FIPS 140 validation. Many remote access systems, such as SSL VPNs, support the use of remote access client software from other vendors, so there may be two or more distinct validation certificates for a particular remote access system.
What is remote desktop access?
remote desktop access solution gives a teleworker the ability to remotely control a particular PC at the organization, most often the user’s own computer at the organization’s office, from a telework client device. The teleworker has keyboard and mouse control over the remote computer and sees that computer’s screen on the local telework client device’s screen. Remote desktop access allows the user to access all of the applications, data, and other resources that are normally available from their PC in the office. Figure 2-3 shows the basic remote desktop access architecture. A remote desktop access client program or web browser plug-in is installed on each telework client device, and it connects directly with the teleworker’s corresponding internal workstation on the organization’s internal network.
What is a portal in remote access?
A portal is a server that offers access to one or more applications through a single centralized interface. A teleworker uses a portal client on a telework client device to access the portal. Most portals are web-based—for them, the portal client is a regular web browser. Figure 2-2 shows the basic portal solution architecture. The application client software is installed on the portal server, and it communicates with application server software on servers within the organization. The portal server communicates securely with the portal client as needed; the exact nature of this depends on the type of portal solution in use, as discussed below.
What is a telework document?
The purpose of this document is to assist organizations in mitigating the risks associated with the enterprise technologies used for telework, such as remote access servers, telework client devices (including bring your own device [BYOD] and contractor, business partner, and vendor-controlled client devices, also known as third-party-controlled devices), and remote access communications. The document emphasizes the importance of securing sensitive information stored on telework devices and transmitted through remote access across external networks. This document provides recommendations for creating telework-related policies and for selecting, implementing, and maintaining the necessary security controls for remote access servers and clients.
Which framework is most pertinent for securing enterprise telework, remote access, and BYOD technologies?
This appendix lists the Cybersecurity Framework48 subcategories that are most pertinent for securing enterprise telework, remote access, and BYOD technologies. Next to each subcategory is an explanation of its implications particular to enterprise telework, remote access, and BYOD security.
What is remote access?
Remote access is access to organizational systems (or processes acting on behalf of users) that communicate through external networks such as the Internet. Types of remote access include dial-up, broadband, and wireless. Organizations use encrypted virtual private networks (VPNs) to enhance confidentiality and integrity for remote connections. The use of encrypted VPNs provides sufficient assurance to the organization that it can effectively treat such connections as internal networks if the cryptographic mechanisms used are implemented in accordance with applicable laws, executive orders, directives, regulations, policies, standards, and guidelines. Still, VPN connections traverse external networks, and the encrypted VPN does not enhance the availability of remote connections. VPNs with encrypted tunnels can also affect the ability to adequately monitor network communications traffic for malicious code. Remote access controls apply to systems other than public web servers or systems designed for public access. Authorization of each remote access type addresses authorization prior to allowing remote access without specifying the specific formats for such authorization. While organizations may use information exchange and system connection security agreements to manage remote access connections to other systems, such agreements are addressed as part of CA-3. Enforcing access restrictions for remote access is addressed via AC-3.
Does VPN allow remote access?
Still, VPN connections traverse external networks, and the encrypted VPN does not enhance the availability of remote connections. VPNs with encrypted tunnels can also affect the ability to adequately monitor network communications traffic for malicious code. Remote access controls apply to systems other than public web servers or systems designed ...
What is remote access in database?
Remote Database Access provides standard protocols for establishing a remote connection between a database client and a database server. The client is acting on behalf of an application program while the server is interfacing to a process that controls data transfers to and from a database. The goal is to promote the interconnection of database applications among heterogeneous environments.
What is RDA service interface?
The RDA Service Interface consists of service elements for association control, for transfer of database operations and parameters from client to server, for transfer of resulting data from server to client, and for transaction management. Association control includes establishing an association between the client and server remote sites and managing connections to specific databases at the server site. Database operations are sent as character strings conforming to the SQL language. Resulting data and/or errors and exceptions are described and represented using the ISO ASN.1 standard. Transaction management includes capabilities for both one-phase and two-phase commit protocols.
What is RDA dialogue?
An RDA dialogue is a cooperative relationship between and RDA client and an RDA server. The RDA client initializes the RDA dialogue and requests RDA operations that are to be performed by the RDA server.
What is RDA communication?
The RDA standard provides an RDA Service Interface to an RDA Communication Element that exists both at the client site and at the server site. The RDA Communication Element converts RDA service requests into underlying ACSE and TP service requests as part of an open systems interconnection.
What happens if RDA dialogue fails?
In the event of dialogue failure, it is a requirement that all changes made to data resources by any RDA transaction that is not already terminating when RDA dialogue failure occurs be rolled back by the database server during its recovery process.
What is RDA transaction?
An RDA transaction is a logically complete unit of processing as determined by the RDA client. Execution during an RDA transaction of a sequence of database access services that change data resources enables the set of changes to be handled as an atomic unit. When the RDA transaction is terminated, either the whole set ...
What is the part of a database server that uses RDA service-provider to communicate with an RDA client?
The part of the database server that uses the RDA service-provider to communicate with an RDA client is called an RDA server. The RDA client has the ability to initiate RDA service requests, while the RDA server can only issue RDA service responses to reply to such requests. A data resource is a named collection of data and/or capabilities on ...
