Azure Active Directory's Application Proxy provides secure remote access to on-premises web applications. After a single sign-on to Azure AD, users can access both cloud and on-premises applications through an external URL or an internal application portal.
Full Answer
How do I provide remote access to on-premises apps and services?
Provide remote access to on-premises apps and services If your organization uses a remote access VPN solution, typically with VPN servers on the edge of your network and VPN clients installed on your users' devices, your users can use remote access VPN connections to access on-premises apps and servers.
Can I use Azure AD application proxy to provide secure remote access?
If your remote workers are not using a traditional VPN client and your on-premises user accounts and groups are synchronized with Azure AD, you can use Azure AD Application Proxy to provide secure remote access for web-based applications hosted on on-premises servers.
How can PrivX be used to provide secure remote access?
Here are five ways how our solution PrivX, typically deployed for privileged user access, can be used to provide easy, secure, restricted and monitored remote access to all employees working out of office with just their favorite modern web browser. . 1. Multi-Factor Authentication (MFA) for employee access
Why choose Splashtop on-prem over BeyondTrust Remote Support (formerly Bomgar)?
Guaranteed savings when you choose Splashtop On-Prem over BeyondTrust Remote Support (formerly Bomgar Remote Support) Get unattended, anytime remote access to Windows and Mac computers as well as many Android devices. Remotely access virtual machines on any hypervisor (VMware, Citrix, Microsoft, and others).
How do you provide secure remote access to on premises applications?
Azure Active Directory's Application Proxy provides secure remote access to on-premises web applications. After a single sign-on to Azure AD, users can access both cloud and on-premises applications through an external URL or an internal application portal.
How do you secure remote access?
Basic Security Tips for Remote DesktopUse strong passwords. ... Use Two-factor authentication. ... Update your software. ... Restrict access using firewalls. ... Enable Network Level Authentication. ... Limit users who can log in using Remote Desktop. ... Set an account lockout policy.
What is meant by secure remote access?
Secure Remote Access is a combination of security processes or solutions that are designed to prevent unauthorized access to an organization's digital assets and prevent the loss of sensitive data.
Is there a secure RDP?
RDP's standard security employs RSA's RC4 encryption algorithm to protect data transmission. Random values are shared between client and server when a connection is initialized while the machines are in the Basic Settings Exchange phase. Remote Desktop encryption protects transmitted data from unauthorized use.
Who is more secure protocol for remote login?
Virtual private networks (VPNs) are a commonly used remote-access solution. They are designed to provide an encrypted tunnel for network traffic between a remote user and the enterprise network. VPNs also support security solutions like MFA that help to mitigate the threat of compromised accounts.
Which is a more secure form of remote access over a network?
Virtual private network (VPN)Virtual private network (VPN) – The most common and well-known form of secure remote access, VPNs typically use the public Internet to connect to a private network resource through an encrypted tunnel.
Why is secure remote access important?
A secure remote access system protects your employees from web-based threats such as phishing attacks, ransomware and malware while they're logged in to your company's network. These cyber incidents can lead to unauthorized access and use of both the company's business data and the employee's personal data.
What is the main purpose of a RAS server?
A remote access server (RAS) is a type of server that provides a suite of services to remotely connected users over a network or the Internet. It operates as a remote gateway or central server that connects remote users with an organization's internal local area network (LAN).
Should I give remote access to my computer?
Remote access solutions could leave you vulnerable. If you don't have proper security solutions in place, remote connections could act as a gateway for cybercriminals to access your devices and data. Hackers could use remote desktop protocol (RDP) to remotely access Windows computers in particular.
Is RDP secure without VPN?
Remote Desktop Protocol (RDP) Integrated in BeyondTrust Establishing remote desktop connections to computers on remote networks usually requires VPN tunneling, port-forwarding, and firewall configurations that compromise security - such as opening the default listening port, TCP 3389.
Why RDP is not safe?
However, the highest risk is the exposure of RDP on the Internet, port 3389, and allowing it to traverse directly through the firewalls to a target on the internal network. This practice is common and should absolutely be avoided.
Is Teamviewer more secure than RDP?
Is Teamviewer safer than RDP? When it comes to safety, RDP is more secure against hackers' attacks. This is because of the powerful encryption method RDP is featured with.
How do you keep security when employees work remotely?
Remote Work Security Best PracticesEstablish and enforce a data security policy. ... Equip your employees with the right tools and technology. ... Frequently update your network security systems. ... Regulate the use of personal devices. ... Institute a “Zero Trust” approach. ... Make sure all internet connections are secure.More items...
Which is the secure standard function for remote access?
MFA is imperative to authenticate users for secure remote access. Many regulations and compliance standards require MFA for privileged remote access.
Secure your on-premises apps under one integrated identity control plane
Exposing on-premises apps to the internet for remote access leads to increased complexity and a larger surface area that security teams need to protect. It is important to put the right controls in place so that you can have confidence only the right people are accessing your organization’s applications and data.
Simplify access to apps with classic authentication modes
A common pain point of managing on-premises apps is supporting different kinds of authentication modes. Users get frustrated if they cannot easily log in or must call the helpdesk to get unblocked.
Give users a consistent experience when accessing on-premises apps
Some users get to their company’s SharePoint or intranet portal by going straight to their browser to visit the website. When publishing your application for remote access, a best practice is to configure the external domain name of your application to match the internal domain name.
Ensure high availability for remote access to apps
Many companies are dealing with unprecedented levels of remote traffic and it is important to have high availability to remote access connection points. App Proxy connectors minimize the overhead in planning for high availability by taking care of all the high-availability tasks.
Consider a lift-and-shift approach for your apps for increased resiliency
You can also increase the resiliency of your applications by lifting and shifting critical apps to cloud platforms like Azure. You can leverage Azure AD Domain Services to serve as a virtual directory for your applications on the cloud without extending your on-premises domain controllers for rapid application deployments.
Scale up access to desktop and app virtualization solutions
We know that in certain scenarios, especially critical and industries like healthcare and financial services, you might need to use on-demand compute capacity to provide secure access to a remote desktop endpoint. This can also be secured with the same Conditional Access policies using Windows Virtual Desktop.
Where to install splashtop on-prem?
Install the Splashtop On-Prem Gateway in your DMZ or behind your firewall. Remote sessions can be peer to peer across local or routable networks; or bridged through the Splashtop On-Prem Gateway for cross network access.
What is splashtop on premise?
Splashtop On-Prem is the best value on-premise solution for secure remote access, remote control, and remote support to any device. This all-in-one solution offers both unattended anytime access and attended on-demand connections, making it the perfect solution for all your remote access needs. Enable employees to access to work computers from anywhere and IT and help desks to efficiently support computers and devices.
Is splashtop encrypted?
All Splashtop connections are protected with TLS and 256-bit AES encryption. All user ID and passwords are encrypted in-flight and at rest. All connections and management events are logged. Global and group policies to enforce password / login behavior, network access, device activation and Streamer behavior. Supports private SSL certificates and two-factor authentication for extra layers of security.
Does splashtop use Active Directory?
For ease of deployment and maintenance, Splashtop can use Active Directory to easily provision user’s accounts and authenticate / authorize each user session request with Active Directory.
What is the name of the service that retrieves the UPN and SPN from the token?
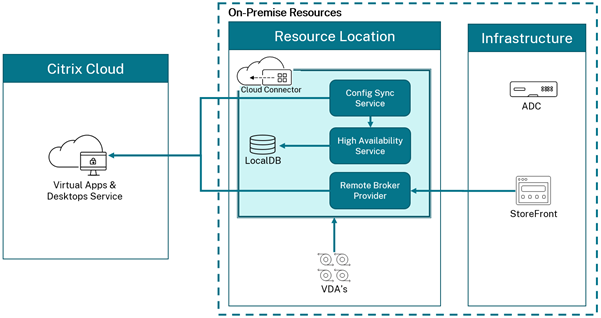
The client sends the token to the Application Proxy service , which retrieves the user principal name (UPN) and security principal name (SPN) from the token. Application Proxy then sends the request to the Application Proxy connector.
How to use Azure AD proxy?
Azure AD Application Proxy is: 1 Simple to use. Users can access your on-premises applications the same way they access Microsoft 365 and other SaaS apps integrated with Azure AD. You don't need to change or update your applications to work with Application Proxy. 2 Secure. On-premises applications can use Azure's authorization controls and security analytics. For example, on-premises applications can use Conditional Access and two-step verification. Application Proxy doesn't require you to open inbound connections through your firewall. 3 Cost-effective. On-premises solutions typically require you to set up and maintain demilitarized zones (DMZs), edge servers, or other complex infrastructures. Application Proxy runs in the cloud, which makes it easy to use. To use Application Proxy, you don't need to change the network infrastructure or install additional appliances in your on-premises environment.
How does Azure AD work?
Azure AD, the Application Proxy service, and the Application Proxy connector work together to securely pass the user sign-on token from Azure AD to the web application. Application Proxy works with: Web applications that use Integrated Windows Authentication for authentication. Web applications that use form-based or header-based access.
What does a single sign on connector do?
If you have configured single sign-on, the connector performs any additional authentication required on behalf of the user.
Is application proxy cost effective?
Application Proxy runs in the cloud, which makes it easy to use. To use Application Proxy, you don't need to change the network infrastructure or install additional appliances in your on-premises environment.
Does Application Proxy support single sign on?
Application Proxy supports single sign-on. For more information on supported methods, see Choosing a single sign-on method.
Does Azure AD require a proxy?
Like most Azure AD hybrid agents, the Application Proxy Connector doesn't require you to open inbound connections through your firewall. User traffic in step 3 terminates at the Application Proxy Service (in Azure AD). The Application Proxy Connector (on-premises) is responsible for the rest of the communication.
Why is Verify all sessions encrypted?
Verify all sessions are encrypted and use analytics to gain visibility, drive threat detection, and improve defenses. In the diagram above, you can see how access is unified across users, devices, and networks; all the various conditions that feed into the risk of a session.
How to learn more about Microsoft security?
To learn more about Microsoft Security solutions visit our website . Bookmark the Security blog to keep up with our expert coverage on security matters. Also, follow us at @MSFTSecurity for the latest news and updates on cybersecurity.
What is zero trust security?
In a Zero Trust security model, every access request is strongly inspected for anomalies before granting access. Everything from the user’s identity to the application’s hosting environment is authenticated and authorized using micro-segmentation and least privileged-access principles to minimize lateral movement.
Will remote work change in 2020?
Change came quickly in 2020. More likely than not, a big chunk of your workforce has been forced into remote access. And with remote work came an explosion of bring-your-own-device (BYOD) scenarios, requiring your organization to extend the bounds of your network to include the entire internet (and the added security risks that come with it).
Does Azure AD require a VPN?
Your apps won’t need to change, and Azure AD Application Proxy also supports multiple authentication modes; so your users can still get a single sign-on (SSO) experience. Users can then access the app from an external URL using any device— no VPN required.
How to optimize access to Microsoft 365 cloud?
To optimize access to Microsoft 365 cloud resources, configure your split tunneling VPN clients to exclude traffic to the Optimize category Microsoft 365 endpoints over the VPN connection. For more information, see Office 365 endpoint categories. See this list of Optimize category endpoints.
How to configure a VPN?
Here are the primary configurations for remote access: 1 You are already using a remote access VPN solution. 2 You are not using a remote access VPN solution and you want your remote workers to use their personal computers. 3 You are not using a remote access VPN solution, you have hybrid identity, and you need remote access only to on-premises web-based apps. 4 You are not using a remote access VPN solution and you need access to on-premises apps, some of which are not web-based.
What is P2S VPN?
A P2S VPN connection creates a secure connection from a remote worker’s device to your organization network through an Azure virtual network.
Does Microsoft 365 have P2S VPN?
Azure P2S VPN is not included with a Microsoft 365 subscription. You must pay for usage with a separate Azure subscription.
Can a VPN client be used to access a remote network?
If your remote workers are using a traditional VPN client to obtain remote access to your organization network, verify that the VPN client has split tunneling support.
Can you share PrivX credentials?
So even when using shared accounts, the user cannot share any credentials to anyone else.
Can you restrict access to specific networks?
You can also restrict access to only to specific networks/target hosts when connecting from the PrivX GUI to websites. Login as self to web target is possible if the user provides own credentials for the web service. Again, optional session recording is possible. If needed, additional PrivX Extender component can be used to access Web targets (as well as SSH and RDP targets) in a private network or virtual private clouds (VPC).
