
How to access remote systems using SSH
- Remote access methods. Secure Shell (SSH) provides a text console on a server, with the option to forward graphics as...
- Install SSH. OpenSSH is usually installed by default on Linux servers. ... You can then access the server with most...
- Log in over SSH. ED25519 key fingerprint is...
- Use a remote shell. SSH is a powerful tool for...
Full Answer
What is OpenSSH and how to use it?
OpenSSH is a connectivity tool for remote login that uses the SSH protocol. It encrypts all traffic between client and server to eliminate eavesdropping, connection hijacking, and other attacks. OpenSSH can be used to connect Window 10 clients to Windows Server 2019.
How to use SSH to connect to a remote system?
SSH, or Secure Shell, is a protocol used to securely log onto remote systems. It is the most common way to access remote Linux servers. In this guide, we will discuss how to use SSH to connect to a remote system. Basic Syntax. To connect to a remote system using SSH, we’ll use the ssh command. The most basic form of the command is: ssh remote_host
How do I install OpenSSH on Ubuntu?
Installing OpenSSH is relatively easy. It requires access to the terminal on the server and the computer that you use for connecting. Note that Ubuntu does not have SSH server installed by default. Before you proceed with installing an SSH client, make sure it is not already installed.
How do I enable SSH port 22 in OpenSSH server?
Installing OpenSSH Server will create and enable a firewall rule named OpenSSH-Server-In-TCP. This allows inbound SSH traffic on port 22. If this rule is not enabled and this port is not open, connections will be refused or reset.

Can SSH be used remotely?
SSH is used by anyone who needs to remotely manage a computer in a secure manner, as well as system and network administrators. Secure Shell SSH provides public key authentication and password authentication, and encrypted data communications between the two computers connected over an open network.
What is SSH remote access?
SSH or Secure Shell is a network protocol that connects users to a remote computer over a secure connection. This allows administrators and other authorized users to connect to secure computers over a network that is not secure, like the Internet. This is accomplished through the use of encryption.
How do I access a Linux server remotely?
Connect to Linux Remotely Using SSH in PuTTYSelect Session > Host Name.Input the Linux computer's network name, or enter the IP address you noted earlier.Select SSH, then Open.When prompted to accept the certificate for the connection, do so.Enter the username and password to sign in to your Linux device.
How do I enable SSH remotely?
Enable root login over SSH:As root, edit the sshd_config file in /etc/ssh/sshd_config : nano /etc/ssh/sshd_config.Add a line in the Authentication section of the file that says PermitRootLogin yes . ... Save the updated /etc/ssh/sshd_config file.Restart the SSH server: service sshd restart.
What can I do with SSH?
The ssh command provides a secure encrypted connection between two hosts over an insecure network. This connection can also be used for terminal access, file transfers, and for tunneling other applications. Graphical X11 applications can also be run securely over SSH from a remote location.
How do I connect to a SSH server?
How to connect via SSH:Open the list of your servers. Click the one you need and click the button "Instructions". ... Open a terminal (for Linux) or a command line (for Windows) on your computer. Enter the command: ssh [username]@[server IP] ... The connection will ask for a password.
How do I SSH to another server without password?
Follow the steps below to set up SSH without passwords on your Linux system.Generate A New SSH Key Pair on Local Machine.Copy Public Key to Remote Machine.Add Private Key to SSH Authentication Agent on Local Server.Login to Remote Server Using SSH Keys.
How do I SSH from the command line?
How to start a SSH session from the command line1) Type the path to Putty.exe here.2) Then type the connection type you wish to use (i.e. -ssh, -telnet, -rlogin, -raw)3) Type the username...4) Then type '@' followed by the server IP address.5) Finally, type the port number to connect to, then press
Does Linux have RDP?
The “RDP” Method The simplest option to enable remote connections to Linux desktops is by using the remote access tool built directly into the Windows OS: Remote Desktop Protocol (RDP).
How can I remotely access a server by IP address?
Remote Desktop to Your Server From a Local Windows ComputerClick the Start button.Click Run...Type “mstsc” and press the Enter key.Next to Computer: type in the IP address of your server.Click Connect.If all goes well, you will see the Windows login prompt.
How do I enable SSH on Windows?
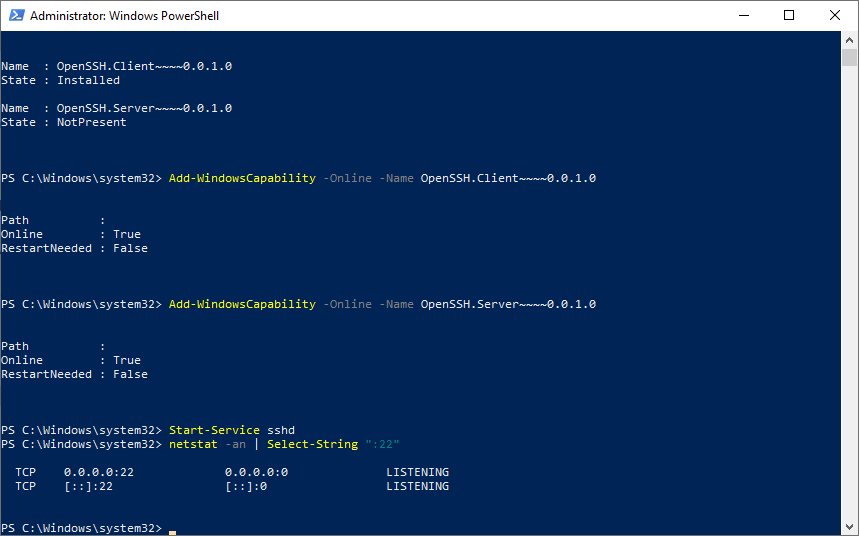
Install OpenSSH for WindowsOpen Settings, select Apps, then select Optional Features.Scan the list to see if the OpenSSH is already installed. If not, at the top of the page, select Add a feature, then: Find OpenSSH Client, then select Install. Find OpenSSH Server, then select Install.
How do I open a port for SSH?
To change the port for the SSH server, follow these steps:Log in to the server as root using SSH.Open the /etc/ssh/sshd_config file in your preferred text editor (nano, vi, etc.).Locate the following line: Port 7822. ... Change 7822 to the new port number that you want to use.More items...
Why do we need SSH?
SSH provides password or public-key based authentication and encrypts connections between two network endpoints. It is a secure alternative to legacy login protocols (such as telnet, rlogin) and insecure file transfer methods (such as FTP).
What is SSH protocol and how it works?
SSH refers to the protocol by which network communications can take place safely and remotely via an unsecured network. SSH enables a variety of crucial functions: protected file transfers, automated processes, command execution, and remote access to private network systems, devices, and applications.
What is the difference between https and SSH?
Any time someone uses a website with a URL that starts with HTTPS, he is on a site with SSL/TLS. SSH is for securely executing commands on a server. SSL is used for securely communicating personal information. SSH uses a username/password authentication system to establish a secure connection.
What is SSH client?
An SSH client is an application you install on the computer which you will use to connect to another computer or a server. The client uses the provided remote host information to initiate the connection and if the credentials are verified, establishes the encrypted connection.
How to enable remote access in Windows 7?
Enabling Remote Access in Windows 7, 8, 10 and Windows Server Versions. Step 1: Allow Remote Connections. Step 2: Add Users to the List of Remote Users. How to Use the Remove Desktop Connection Client.
What is SSH?
Secure Shell, sometimes referred to as Secure Socket Shell, is a protocol which allows you to connect securely to a remote computer or a server by using a text-based interface.
What is needed to accept SSH connections?
In order to accept SSH connections, a machine needs to have the server-side part of the SSH software toolkit.
How to get remote desktop on Windows 7?
You can find it in a couple of different ways: For Windows 7, click on Start -> All Programs, go to the ‘Accessories’ folder and click on Remote Desktop Connection.
What is the component of SSH?
On the server’s side, there is a component called an SSH daemon that is constantly listening to a specific TCP/IP port for possible client connection requests. Once a client initiates a connection, the SSH daemon will respond with the software and the protocol versions it supports and the two will exchange their identification data. If the provided credentials are correct, SSH creates a new session for the appropriate environment.
What is the protocol used to connect to a remote machine?
There are many ways to establish a connection with a remote machine depending on the operating system you are running, but the two most used protocols are: Secure Shell (SSH) for Linux-based machines. Remote Desktop Protocol (RDP) for Windows-based machines.
What is SSH in Linux?
SSH, or Secure Shell, is a protocol used to securely log onto remote systems. It is the most common way to access remote Linux servers. In this guide, we will discuss how to use SSH to connect to a remote system.
Where do you generate SSH keys?
SSH keys should be generated on the computer you wish to log in from. This is usually your local machine.
How Does SSH Work?
SSH works by connecting a client program to an ssh server, called sshd.
Why is SSH so popular?
SSH has remained popular because it is secure, light-weight, and useful in diverse situations.
Where is the sshd file located?
In Ubuntu, the main sshd configuration file is located at /etc/ssh/sshd_config.
Is ID_RSA readable?
As you can see, the id_rsa file is readable and writable only to the owner. This is how it should be to keep it secret.
Can you execute a single command on a remote system?
If you only wish to execute a single command on a remote system, you can specify it after the host like so:
What is OpenSSH compatible?
An OpenSSH-compatible client can be used to connect to Windows 10 (build 1809 and later) and Windows Server 2019 devices.
What port does OpenSSH use?
Installing OpenSSH Server will create and enable a firewall rule named OpenSSH-Server-In-TCP. This allows inbound SSH traffic on port 22. If this rule is not enabled and this port is not open, connections will be refused or reset.
What is OpenSSH on Windows Server 2019?
Applies to Windows Server 2019, Windows 10. OpenSSH is a connectivity tool for remote login that uses the SSH protocol. It encrypts all traffic between client and server to eliminate eavesdropping, connection hijacking, and other attacks. OpenSSH can be used to connect Window 10 (build 1809 and later) or Windows Server 2019 devices ...
How to uninstall OpenSSH?
To uninstall OpenSSH using Windows Settings: 1 Open Settings, then go to Apps > Apps & Features. 2 Go to Optional Features. 3 In the list, select OpenSSH Client or OpenSSH Server. 4 Select Uninstall.
Does SSH add a host to the list?
Selecting yes adds that server to the list of known SSH hosts on your Windows client .
Can OpenSSH be installed on Windows Server 2019?
Both OpenSSH components can be installed using Windows Settings on Windows Server 2019 and Windows 10 devices.
How to install OpenSSH client?
If the OpenSSH Client feature is not installed, click the Add a feature button at the top of the page. A dropdown menu appears. Select OpenSSH Client and press the Install button.
What is SSH in web hosting?
When most people refer to SSH, it is within the context of a connecting from a local computer to a remote server, commonly for administration tasks related to website hosting.
What port does SSH connect to?
The SSH client attempts to connect to the remote server over port 22 (the default SSH port).
How to use WSL?
By default, WSL uses a fairly basic terminal emulator. You can also use a more customizable terminal, such as Windows Terminal or Hyper.
When you connect to a server for the first time, the SSH client prompts you to check and verify the?
When you connect with a server for the first time, the SSH client prompts you to check and verify the host key’s fingerprint. This is normal, and results in output similar to:
How to open up Windows Search?
Open up Windows Search by selecting the search area (or search button) on the taskbar or by pressing Windows + S on the keyboard.
Where to install Linux distribution?
Install your preferred Linux distribution, such as Ubuntu, directly from the Microsoft Store. A full list of available distributions can be found under Step 6 - Install your Linux distribution of choice of the previously mentioned guide.
Where is OpenSSH installed?
Add the path where OpenSSH is installed to your Path environment variable. For example, C:Program FilesOpenSSH. This entry allows for the ssh.exe to be found.
What is SSH remoting?
SSH remoting lets you do basic PowerShell session remoting between Windows and Linux computers. SSH remoting creates a PowerShell host process on the target computer as an SSH subsystem. Eventually we'll implement a general hosting model, similar to WinRM, to support endpoint configuration and JEA.
How to tell if PowerShell supports SSH?
You can confirm that PowerShell has SSH remoting support by listing the New-PSSession parameter sets. You'll notice there are parameter set names that begin with SSH. Those parameter sets include SSH parameters.
What is SSH in PowerShell?
SSH is now available for Linux and Windows platforms and allows true multiplatform PowerShell remoting. WinRM provides a robust hosting model for PowerShell remote sessions.
How to create a remote session?
To create a remote session, you specify the target computer with the HostName parameter and provide the user name with UserName. When running the cmdlets interactively, you're prompted for a password. You can also use SSH key authentication using a private key file with the KeyFilePath parameter. Creating keys for SSH authentication varies by platform.
Where is the PowerShell executable located?
The default location of the PowerShell executable is /usr/local/bin/pwsh. The location can vary depending on how you installed PowerShell.
Does SSH use multifactor authentication?
PowerShell remoting over SSH relies on the authentication exchange between the SSH client and SSH service and doesn't implement any authentication schemes itself. The result is that any configured authentication schemes including multi-factor authentication are handled by SSH and independent of PowerShell. For example, you can configure the SSH service to require public key authentication and a one-time password for added security. Configuration of multi-factor authentication is outside the scope of this documentation. Refer to documentation for SSH on how to correctly configure multi-factor authentication and validate it works outside of PowerShell before attempting to use it with PowerShell remoting.
How does SSH authentication work?
How SSH key authentication works. SSH public key authentication works with an asymmetric pair of generated encryption keys. The public key is shared with Azure DevOps and used to verify the initial ssh connection. The private key is kept safe and secure on your system.
What happens when you register a new SSH key?
A: Whenever you register a new SSH Key with Azure DevOps Services, you will receive an email notification informing you that a new SSH key has been added to your account.
Can you configure multiple keys for SSH?
A: Generally, if you configure multiple keys for an SSH client and connect to an SSH server, the client can try the keys one at a time until the server accepts one.
Can you change SSH key in Azure DevOps?
Once saved, you cannot change the key. You can delete the key or create a new entry for another key. There are no restrictions on how many keys you can add to your user profile. Also note that SSH keys stored in Azure DevOps expire after five years.
Does Fedora Linux support SSH?
A: Some Linux distributions, such as Fedora Linux, have crypto policies that require stronger SSH signature algorithms than Azure DevOps supports (as of January 2021). There's an open feature request to add this support.
CORE Syntax
- To connect to a remote system using SSH, we’ll use the sshcommand. If you are using Windows, you’ll need to install a version of OpenSSH in order to be able to ssh from a terminal. If you prefer to work in PowerShell, you can follow Microsoft’s documentation to add OpenSSH to PowerShell. If you would rather have a full Linux environment available, ...
How Does Ssh Work?
- SSH works by connecting a client program to an ssh server, called sshd. In the previous section, ssh was the client program. The ssh server was already running on the remote_hostthat we specified. On nearly all Linux environments, the sshdserver should start automatically. If it is not running for any reason, you may need to temporarily access your server through a web-based co…
How to Configure Ssh
- When you change the configuration of SSH, you are changing the settings of the sshd server. In Ubuntu, the main sshd configuration file is located at /etc/ssh/sshd_config. Back up the current version of this file before editing: Open it using nanoor your favourite text editor: You will want to leave most of the options in this file alone. However, there are a few you may want to take a loo…
How to Log Into Ssh with Keys
- While it is helpful to be able to log in to a remote system using passwords, it is faster and more secure to set up key-based authentication.
Client-Side Options
- There are a number of optional flags that you can provide when connecting through SSH. Some of these may be necessary to match the settings in the remote host’s sshdconfiguration. For instance, if you changed the port number in your sshdconfiguration, you will need to match that port on the client-side by typing: If you only want to execute a single command on a remote syst…
Disabling Password Authentication
- If you have created SSH keys, you can enhance your server’s security by disabling password-only authentication. Apart from the console, the only way to log into your server will be through the private key that pairs with the public key you have installed on the server. As root or user with sudo privileges, open the sshdconfiguration file: Locate the line that reads Password Authentica…
Conclusion
- Learning your way around SSH will greatly benefit any of your future cloud computing endeavours. As you use the various options, you will discover more advanced functionality that can make your life easier. SSH has remained popular because it is secure, light-weight, and useful in diverse situations. Next, you may want to learn about working with SFTPto perform command line file tr…
Prerequisites
- Before you start, your computer must meet the following requirements: 1. A device running at least Windows Server 2019 or Windows 10 (build 1809). 2. PowerShell 5.1 or later. 3. An account that is a member of the built-in Administrators group.
Connect to Openssh Server
- Once installed, you can connect to OpenSSH Server from a Windows or Windows Server device with the OpenSSH client installed. From a PowerShell prompt, run the following command. Once connected, you get a message similar to the following output. Entering yesadds that server to the list of known SSH hosts on your Windows client. At this point, you'll...
Uninstall Openssh For Windows
- You may need to restart Windows afterwards if the service was in use at the time it was uninstalled.
Next Steps
- Now that you've installed OpenSSH Server for Windows, here are some articles that might help you as you use it: 1. Learn more about using key pairs for authentication in OpenSSH key management 2. Learn more about the OpenSSH Server configuration for Windows