Orcus is a Remote Access Trojan (RAT). Programs of this type are used to remotely access or control computers. Generally, these tools can be used by anyone legitimately, however, in many cases, cyber criminals use them for malicious purposes.
Full Answer
What is the Orcus remote access Tool (RAT)?
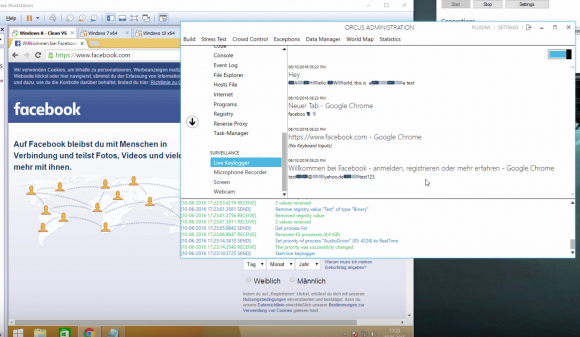
In a successful attack, the Orcus RAT can steal browser cookies and passwords, launch server stress tests (DDoS attacks), disable the webcam activity light, record microphone input, spoof file extensions, log keystrokes and more. ( More about Orcus RAT below .)
What is a remote access trojan (RAT)?
Thanks! Hackers often access and control operating systems using remote access Trojans (RATs). Tools like these are available in abundance on the dark market. In this article, I am going to write about six popular breeds of RATs that cybercriminals use in the wild.
What is the Orcus program?
They often trick people into installing these programs and then use them to steal various information to generate revenue. The Orcus program can be downloaded from its website and is promoted as having features similar to TeamViewer and other software.
What is the Orcus Rat Attack?
The attack uses multiple advanced evasive techniques to bypass security tools. In a successful attack, the Orcus RAT can steal browser cookies and passwords, launch server stress tests (DDoS attacks), disable the webcam activity light, record microphone input, spoof file extensions, log keystrokes and more. ( More about Orcus RAT below .)
Can remote access Trojans be detected?
AIDE—short for Advanced Intrusion Detection Environment—is a HIDS designed specifically to focus on rootkit detection and file signature comparisons, both of which are incredibly useful for detecting APTs like Remote Access Trojans.
What is orcus client?
What is Orcus? Orcus is a Remote Access Trojan (RAT). Programs of this type are used to remotely access or control computers. Generally, these tools can be used by anyone legitimately, however, in many cases, cyber criminals use them for malicious purposes.
Is remote access Trojan a malware?
Remote access trojans (RATs) are malware designed to allow an attacker to remotely control an infected computer. Once the RAT is running on a compromised system, the attacker can send commands to it and receive data back in response.
What is orcus software?
Orcus is a modular Remote Access Trojan with some unusual functions. This RAT enables attackers to create plugins using a custom development library and offers a robust core feature set that makes it one of the most dangerous malicious programs in its class.
Who is Orcus?
Orcus (Latin: Orcus) was a god of the underworld, punisher of broken oaths in Etruscan and Roman mythology. As with Hades, the name of the god was also used for the underworld itself.
What is backdoor Orcus?
Backdoor. Orcus is a Remote Access Trojan (RAT) that is being sold on underground forums.
How are remote access Trojans delivered?
A remote access Trojan (RAT) is a malware program that includes a back door for administrative control over the target computer. RATs are usually downloaded invisibly with a user-requested program -- such as a game -- or sent as an email attachment.
How can I find a hidden virus on my computer?
You can also head to Settings > Update & Security > Windows Security > Open Windows Security on Windows 10, or Settings > Privacy and Security > Windows Security > Open Windows Security on Windows 11. To perform an anti-malware scan, click “Virus & threat protection.” Click “Quick Scan” to scan your system for malware.
Can an Iphone get a remote access Trojan?
The iOS Trojan is smart and spies discretely, i.e. does not drain a battery. The RCS mobile Trojans are capable of performing all kinds of spying you can expect from such a tool, including location reporting, taking photos, spying on SMS, WhatsApp and other messengers, stealing contacts and so on.
What happened orcus rat?
This RAT has been sold for $40 since April 2016, with the ability to build custom plugins. Orcus RAT is primarily distributed via spear-phishing emails and drive-by-downloads. The Remote Access Trojan's capabilities include: Keylogging and remote administration.
What is Nanocore rat?
Nanocore RAT Propose Change Nanocore is a Remote Access Tool used to steal credentials and to spy on cameras. It as been used for a while by numerous criminal actors as well as by nation state threat actors.
Who is orcus in Happy?
Orcus is a demonic entity and the overall overarching antagonist of the Syfy original series Happy!. He serves as a minor antagonist in the first season and the overarching antagonist in the second season. He is a hereditary demon who has been passed down the Scaramucci bloodline since the dawn of time.
What does the Horn of Orcus do?
Able to enhance the powers of whomever the horn is attached to. Capable of reanimating the body to which it is attached should the creature die. Consumes the necrotic energies of creatures slain by the one to which it is attached, healing its bearer. Naturally corrupting in nature.
How much health does orcus have?
StatsHPAC40517 (natural armor; 20 with the Wand of Orcus)
What is Orcus RAT?
What is Orcus? Orcus is a Remote Access Trojan (RAT). Programs of this type are used to remotely access or control computers. Generally, these tools can be used by anyone legitimately, however, in many cases, cyber criminals use them for malicious purposes.
How much does an Orcus microphone cost?
These features are not included in the basic version of Orcus, however, they can be purchased for $40.
Is Orcus a program?
The Orcus program can be downloaded from its website and is promoted as having features similar to TeamViewer and other software. In fact, Orcus includes some illegal features such as the ability to disable the webcam activity light, retrieve passwords from well-known applications, and retrieve browser cookies.
How does Orcus RAT work?
This malware often disguises itself as a cheat code or crack, so it is mostly delivered to a system as an archive file with the compressed executable file inside. Since this trojan was written in C#, it often uses .NET infrastructure, available in Windows. To compile the C# source code, our sample started Visual C# compiler, which, in turn, started the Resource File To COFF Object Conversion Utility. After it was compiled, the executable file began its execution and malicious activity. Note that Orcus remote access tool does not always make its way into an infected system, as described above. In some cases, it comes as a precompiled executable file which only needs a user to double click on it to start the execution.
Who developed Orcus RAT?
Speaking of Orcus RAT malware authors, we know that the virus was developed by a 36-year-old John Revesz, also known as “Armada" on the underground forums. In 2019, Canadian authorities accused Revesz of operating an international malware distribution scheme.
What is Adwind RAT?
Adwind RAT, sometimes also called Unrecom, Sockrat, Frutas, jRat, and JSocket, is a Malware As A Service Remote Access Trojan that attackers can use to collect information from infected machines. It was one of the most popular RATs in the market in 2015. Read More.
Is Orcus RAT malware a RAT?
Although Orcus RAT malware is mostly a typical member of the RAT family, it has some competitive advantages over similar malware and unique features. In addition, Orcus RAT has a modular structure, and it gives users the ability to create custom plugins for the malware.
Does Orcus detect if it's being launched on a virtual machine?
In addition, Orcus comes with the ability to detect if it’s being launched on a virtual machine to complicate the analysis by security researchers. The functions described above already make this malware quite capable. However, it offers a few unusual functions that enhance its functionality.
Is RAT a legitimate program?
In his defense, Revesz claimed that the RAT is, in fact, a legitimate program for remote administration, and his company “Orcus Technologies” is a legal business. However, an examination of the functionality clearly revealed that the software is intended for malicious use cases, which resulted in the arrest of Revesz.
Does Orcus RAT steal passwords?
Apart from a few exceptions, Orcus RAT malware has a relatively standard but robust feature set for a technologically advanced Remote Access Trojan. The malware can grab screenshots and record user input, activate the webcam, steal passwords, record audio, and steal information. In addition, Orcus comes with the ability to detect if it’s being launched on a virtual machine to complicate the analysis by security researchers.
Technical explanation
Based on the initial attack data, we could see that the attack flow proceeds as follows: A persistent VBscript executes a PowerShell script that downloads a .NET executable obfuscated and encrypted by ConfuserEx. The downloaded executable performs known UAC bypass through event viewer registry hijacking to get the highest privileges.
more on Orcus rat
The Orcus RAT masquerades as a legitimate remote administration tool, although it is clear from its features and functionality that it is not and was never intended to be.
Conclusions
Given that Orcus Trojan was recently made freely available, we expect to see more attacks delivering new Orcus RAT variants as a payload.
