How to connect to Palo Alto VPN?
How To Connect To Palo Alto Vpn Inside? To configure IPSec VPN by setting up a tunnel interface, choose this question in the Network >Interface > Tunnel tab: and click OK. Adding and defining an IKE cryptocurrency profile (IKEv1 Phase-1) can be done through IKE network> profile and profile parameters > IKE Crypto network >.
How to configure GlobalProtect in Palo Alto?
- On the firewall that is hosting your GlobalProtect gateway (s) (or on Panorama if you plan to share the HIP profiles among multiple gateways), select Objects GlobalProtect HIP Profiles , ...
- Enter a Name and Description to identify the profile.
- Click Add Match Criteria to open the HIP Object/Profiles Builder.
Does Palo Alto support L2TP?
does palo alto support l2tp , pptp over ipsec vpn? Hello, Unfortunately, L2TP is currently not supported on PANOS. However, PPTP traffic through the PAN device is available. If you're utilizing a Microsoft VPN solution, you can implement a static nat to make PPTP functional.
How to configure IPsec?
To configure a route-based or policy-based IPsec VPN using autokey IKE:
- Configure interfaces, security zones, and address book information. (For route-based VPNs) Configure a secure tunnel st0.x interface. ...
- Configure Phase 1 of the IPsec VPN tunnel. ...
- Configure Phase 2 of the IPsec VPN tunnel. ...
- Configure a security policy to permit traffic from the source zone to the destination zone. ...
- Update your global VPN settings.
Does remote access VPN use IPsec?
While Remote access VPN supports SSL and IPsec technology.
What is IPsec remote access VPN?
Internet Protocol Security (IPsec) is a suite of protocols that support cryptographically secure communication at the IP layer. With IPsec connections, you can provide secure access between two hosts, two sites, or remote users and a LAN.
How do I access my Palo Alto firewall remotely?
Go to Network > Interfaces > Ethernet, then click on the Interface name, for the external interface. I used ethernet1/3. Click the Advanced tab. Under the Other Info tab, next to Management Profile, use the dropdown to select Remote_management, then click OK.
How do I configure IPsec VPN tunnel in Palo Alto?
Go to Network >Interface > Tunnel tab, click Add to create a new tunnel interface and assign the following parameters:Name: tunnel. ... Virtual router: (select the virtual router you would like your tunnel interface to reside)More items...•
What is the difference between site-to-site VPN and remote access VPN?
A remote access VPN connects remote users from any location to a corporate network. A site-to-site VPN, meanwhile, connects individual networks to each other.
What is difference between SSL VPN and remote access VPN?
Whereas an IPsec VPN enables connections between an authorized remote host and any system inside the enterprise perimeter, an SSL VPN can be configured to enable connections only between authorized remote hosts and specific services offered inside the enterprise perimeter.
How does remote access VPN Work?
A remote access VPN works by creating a virtual tunnel between an employee's device and the company's network. This tunnel goes through the public internet but the data sent back and forth through it is protected by encryption and security protocols to help keep it private and secure.
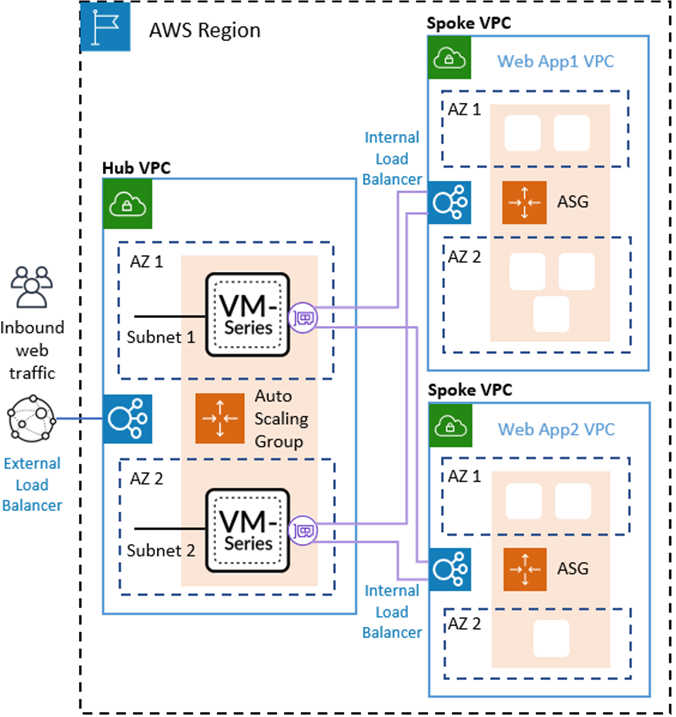
How do I connect to Palo Alto VPN?
1:2726:18Setup GlobalProtect VPN with Palo Alto - YouTubeYouTubeStart of suggested clipEnd of suggested clipThe next step is to set up what's called an authentication profile and to do that let's go ahead andMoreThe next step is to set up what's called an authentication profile and to do that let's go ahead and jump in to our Palo Alto and set that up.
Which type of remote access functions as a secure tunnel through any network?
A VPN creates a “tunnel” that passes traffic privately between the remote network and the user. The tunnel protects the traffic and keeps it safe from being intercepted or tampered with. VPNs are commonly implemented using the protocols IPsec or SSL.
How IPsec VPN works step by step?
Authenticates and protects the identities of the IPSec peers. Negotiates a matching IKE SA policy between peers to protect the IKE exchange. Performs an authenticated Diffie-Hellman exchange with the end result of having matching shared secret keys. Sets up a secure tunnel to negotiate IKE phase two parameters.
How do I configure IPsec VPN site to site?
To configure a route-based or policy-based IPsec VPN using autokey IKE:Configure interfaces, security zones, and address book information. ... Configure Phase 1 of the IPsec VPN tunnel. ... Configure Phase 2 of the IPsec VPN tunnel. ... Configure a security policy to permit traffic from the source zone to the destination zone.More items...
How do I set up IPsec VPN?
Configuring the Server sideIn the administration interface, go to Interfaces.Double-click on VPN Server.In the VPN Server Properties dialog box, check Enable IPsec VPN Server. ... On tab IPsec VPN, select a valid SSL certificate in the Certificate pop-up list.Check Use preshared key and type the key.Save the settings.
What are the 3 protocols used in IPsec?
IPsec is a suite of protocols widely used to secure connections over the internet. The three main protocols comprising IPsec are: Authentication Header (AH), Encapsulating Security Payload (ESP), and Internet Key Exchange (IKE).
Which is better IPsec or OpenVPN?
In site-to-site connections, OpenVPN functions faster and provides more security than IPsec. IPsec encryption operates on a kernel level, whereas OpenVPN functions in user space. Therefore, in terms of endpoint performance, IPsec is more favorable. With OpenVPN, you're limited to the capacity of the software.
What is the difference between SSL and IPsec?
Internet protocol security (IPsec) is a set of protocols that provide security for Internet Protocol. SSL is a secure protocol developed for sending information securely over the Internet. It Work in Internet Layer of the OSI model. It Work in Between the transport layer and application layer of the OSI model.
Why is VPN remote access?
The remote access VPN does this by creating a tunnel between an organization’s network and a remote user that is “virtually private,” even though the user may be in a public location. This is because the traffic is encrypted, which makes it unintelligible to any eavesdropper.
What is remote access VPN?
What Is a Remote Access VPN? A remote access virtual private network (VPN) enables users who are working remotely to securely access and use applications and data that reside in the corporate data center and headquarters, encrypting all traffic the users send and receive. The remote access VPN does this by creating a tunnel between an ...
Does SASE require a VPN?
Using SASE, an organization does not have to maintain a separate stand-alone proxy or VPN. Rather, users connect to a SASE solution (which provides access to the cloud and data center) with consistent security. Some advantages of using a SASE are that it allows companies to:
Does topology require a license?
For such topology, does not require any special license.
Does the PA220 have a VPN?
In case this isn't clear.... the WAN interface of the PA220 would service both the remote access vpn and the ipsec site -to-site vpn.
How to add a VPN tunnel?
Add Primary and Secondary IPSec VPN Tunnels 1 Give the tunnel a descriptive#N#Name#N#. 2 Select the#N#Branch Device Type#N#for the IPSec device at the remote network site that you’re using to establish the tunnel with Prisma Access. 3 For the#N#Branch Device IP Address#N#, choose to use either a#N#Static IP#N#address that identifies the tunnel endpoint or a#N#Dynamic#N#IP address.#N#If you set the#N#Branch Device IP Address#N#to#N#Dynamic#N#, you must also add the IKE ID for the remote network site (#N#IKE Local Identification#N#) or for Prisma Access (#N#IKE Peer Identification#N#) to enable the IPSec peers to authenticate.#N#Because you do not have the values to use for the Prisma Access IKE ID (#N#IKE Peer Identification#N#) until the remote network is fully deployed, you would typically want to set the IKE ID for the remote network site (#N#IKE Local Identification#N#) rather than the Prisma Access IKE ID.
What is Prisma Access?
Based on the IPSec device type you selected, Prisma Access provides a recommended set of IPSec protocol and key lifetime settings to secure data within the IPSec tunnel between your branch device and Prisma Access in IKE Phase 2 for the Security Association (SA). You can use the recommended settings, or customize the settings as needed for your environment.
What is the authentication algorithm for Prisma Access?
Prisma Access supports the following authentication algorithms: sha1 (160 bits), sha256 (256 bits), sha384 (384 bits), sha512 (512 bits), and md5 (128 bits). You can also select null (no authentication).
Does Prisma Access initiate IKE connections?
so that Prisma Access only response to IKE connections and does not initiate them.
Does Prisma Access have IKE?
Based on the IPSec device you use to establish the tunnel at the remote network site, Prisma Access provides built-in, recommended IKE and IPSec security settings. You can use the recommended settings to get started quickly, or customize them as needed for your environment.
What is site to site VPN?
A site-to-site VPN is a connection between two or more networks, such as a corporate network and a branch office network. Site-to-site VPNs are frequently used by companies with multiple offices in different geographic locations that need to access and use the corporate network on an ongoing basis.
What is VPN tunnel?
As mentioned above, a VPN creates a private connection known as a tunnel. All information traveling from a device connected to a VPN will get encrypted and go through this tunnel. When connected to a VPN, a device behaves as if it’s on the same local network as the VPN.
How does VPN work?
The VPN will forward device traffic to and from the intended website or network through its secure connection. This allows your remote users and offices to connect securely to a corporate network or website. It also hides your IP addresses from hackers and prying eyes.
Why is VPN important?
A VPN establishes the secure connection necessary for enabling the mobile workforce.
How to secure remote workforce?
The only way to secure your remote workforce is a secure VPN. Employees must connect from their laptops, desktops and mobile devices over a VPN connection. It’s the secure, private method for virtually entering the corporate office, so to speak. In many cases, remote workforce technology requires hardware.
Why do people use VPNs?
A VPN makes your internet connection more secure and offers privacy online. Organizations, governments and businesses of all sizes use VPNs to secure remote connections to the internet for protection against malicious actors, malware and other cyberthreats. Personal VPNs have also become widely popular as they keep users’ locations private, safely encrypt data and allow users to browse the internet anonymously.
Why do we need VPN?
A VPN makes your internet connection more secure and offers privacy online. Organizations, governments and businesses of all sizes use VPNs to secure remote connections to the internet for protection against malicious actors, malware and other cyberthreats.
What is VPN in a VPN?
A VPN is a technology that creates a secured network connection over a traditional network by encrypting all communication between two hosts. We'll take a look at how to set up a site-to-site tunnel that uses strong IPSec encryption. When preparing for a site-to-site VPN configuration, many times you will need to have a conversation with ...
What is the authentication method on IKE?
The Authentication method can be set to a pre-shared key to be used on both peers to initiate negotiation, or a certificate can be imported to authenticate the handshake. On the IKE Gateway, under Advanced Options, several options can be set to accomodate certain situations:
How to add IKE crypto to network?
Go to Network >> Network Profile >> IKE Crypto and click Add. Now add below details-
What IP address is Sitea to Siteb?
We need to add routes to reach SITEA to SITEB and vise-versa. Below are the route from SITEA to SITEB, where gateway is IPSec peer IP , which is 10.10.10.2
Can we reach SiteB from SiteA?
We can successfully reach SiteB from SiteA. Let’s verify IPSec information from palo alto using below command-
What is remote work AP?
In a home office scenario, the Remote Workplace AP is cloud-managed and it forms an IPSec tunnel to the corporate data center (CDC). CDC is the head end tunnel terminator. The Remote Workplace AP uses 802.1X authentication such as Pre-Shared Key or Captive Portal to authenticate clients.
What is a full tunnel AP?
In a full tunnel mode, the Remote Workplace AP sends all data traffic to the CDC. The CDC processes the data using existing corporate security tools.
Is a wildcard SSL certificate valid?
You have a valid or publicly signed SSL certificate. Wildcard SSL certificates are also acceptable.
