Answer: A remote access program such as LogMeIn can be PCI compliant; however, it must be securely implemented using multiple factors of authentication to log in, the connection must be encrypted, and the associated passwords must meet all of the requirements set forth by the PCI Data Security Standard.
Full Answer
Are remote access programs PCI compliant?
It should be noted that remote access programs may be PCI compliant. However, login must be implemented securely using multiple authentication factors, the connection must be encrypted, and associated passwords must meet all requirements set by the PCI Data Security Standard.
What are the PCI DSS requirements for remote access management?
Automatically terminate remote access sessions after a specified time. PCI DSS requirement 12.3.8 requires automatic disconnection of sessions for remote access technologies after a specified period of inactivity. Use remote accesses for third parties only when necessary.
Are employees making remote access connections using home connections?
Employees now make remote access connections using home connections, in some cases using non-corporate computers, exposing organizations to attack vectors that do not exist when these connections are made locally.

Is Remote Desktop PCI compliant?
It should be noted that remote access programs may be PCI compliant. However, login must be implemented securely using multiple authentication factors, the connection must be encrypted, and associated passwords must meet all requirements set by the PCI Data Security Standard.
Can you be PCI compliant working from home?
PCI DSS requirements may apply to work-from-home (WFH) environments in different ways, depending on the entity's business and security needs and how they have configured their infrastructure to support personnel working from home.
What triggers PCI compliance?
A: If you accept credit or debit cards as a form of payment, then PCI compliance applies to you. The storage of card data is risky, so if you don't store card data, then becoming secure and compliant may be easier.
What are the four levels of PCI compliance?
Level 1: Merchants that process over 6 million card transactions annually. Level 2: Merchants that process 1 to 6 million transactions annually. Level 3: Merchants that process 20,000 to 1 million transactions annually. Level 4: Merchants that process fewer than 20,000 transactions annually.
Does PCI allow split tunneling?
In techie terms, DO NOT ALLOW SPLIT-TUNNELING. It's important to remember that devices enforcing network segmentation are also in scope for PCI DSS, and that a segmentation penetration test of at least a representative sample of segmentation points is required every 6 months to ensure the segmentation is effective.
What is a PCI in workplace?
PCI compliance is adherence to a set of security standards of the Payment Card Industry Data Security Standard (PCI DSS). All companies that accept, process, store, or transmit credit card information have to be PCI compliant to ensure optimal security.
What happens if I'm not PCI compliant?
If you're not PCI compliant, you run the risk of losing your merchant account, which means you won't be able to accept credit card payments at all.
How can PCI compliance be avoided?
3 Basic Ways to Avoid PCI ParalysisCombat security threats while achieving PCI compliance. ... 1) Create a culture of awareness and educate employees on a continuous basis. ... 2) Designate a PCI champion. ... 3) Avoid storing payment information whenever and wherever possible. ... Commitment to people, processes and technology.
How do I know if I need to be PCI compliant?
If your company accepts credit card payments online, by phone or at the point of sale (POS), you must be PCI compliant. The steps you must take to ensure compliance depends on the volume of credit card business your company writes and whether it is writing that business at POS or through e-commerce transactions.
What is meant by PCI compliance?
Payment Card Industry Data Security Standard (PCI DSS) compliance is adherence to the set of policies and procedures developed to protect credit, debit and cash card transactions and prevent the misuse of cardholders' personal information. PCI DSS compliance is required by all card brands.
What does Level 1 PCI compliance mean?
PCI DSS Compliance Levels Level 1: Businesses that process over 6 million card transactions per year across all channels or any business that has had a data breach. Level 2: Businesses that process between 1 million and 6 million card transactions per year across all channels.
How do I certify PCI compliance?
How do I get PCI DSS Certified?Identify your compliance 'level'Complete a self-assessment questionnaire (SAQ) or Complete an annual Report on Compliance (ROC)Complete a formal attestation of compliance (AOC)Complete a quarterly network scan by an Approved Scanning Vendor (ASV)Submit the document.
What data falls under PCI compliance?
PCI DSS covers PII when it is related to cardholder data, such as the PAN, cardholder name, service code, and card expiration date, according to InfoSec Institute. It also covers sensitive authentication data such as a card PIN.
What is a PCI violation?
Some of the worst breaches involve stolen payment information, resulting in PCI violations. These violate the Payment Card Industry Data Security Standard (PCI DSS), a standard for organizations that deal with credit card data. A violation doesn't only lead to monetary losses for the person whose data gets stolen.
Who enforces PCI compliance?
Generally speaking, your merchant bank enforces PCI DSS compliance. The PCI Standards Security Council was formed in 2006 by the major card brands (i.e., Visa, MasterCard, American Express, Discover Financial Services, JCB International) to regulate, maintain, evolve and promote PCI DSS compliance.
Which three 3 of these control processes are included in the PCI DSS standard?
There are three ongoing steps for adhering to the PCI DSS: Assess — identifying cardholder data, taking an inventory of your IT assets and business processes for payment card processing, and analyzing them for vulnerabilities that could expose cardholder data.
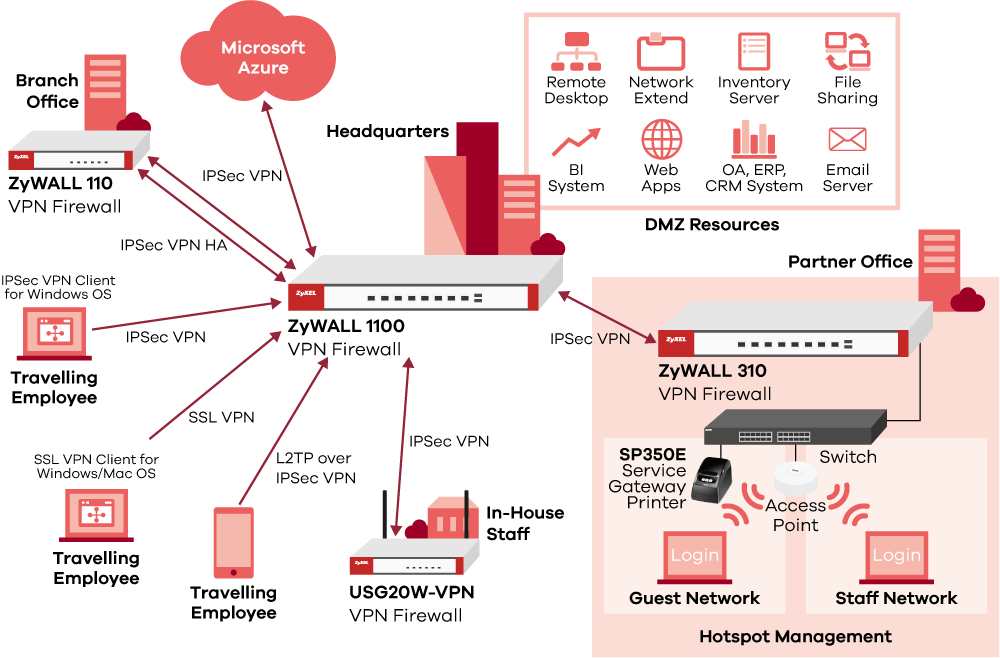
Why engage in PCI compliant remote access software?
A remote access software is designed to let authorized technicians access and troubleshoot computers across the globe. This might involve an exchange of business data in and out of the corporate infrastructure over the internet. If your business typically needs to comply with PCI mandates, then you need to ensure that your remote access software is PCI DSS ready.
What is PCI DSS?
The Payment Card Industry Security Standards Council (PCI SSC) formulated Payment Card Industry Data Security Standard (PCI DSS) to set standards to the organisations that store, process and transmit hard holder data. PCI DSS intends on preventing identity data theft by adding an additional level of protection.
What is Remote Access Plus?
Remote Access Plus lets you define granular permission levels to technicians. You can make technicians access the diagnostic tools but restrict them from remotely controlling client computers.
Can Remote Access Plus be revoked?
Authorization to tools used to send / receive files, access command prompt can be granted or revoked to technicians and administrators.
Can administrators restrict technicians from accessing File Manager?
Furthermore, administrators can restrict technicians from accessing File Manager and Command Prompt. This will forbid them from exporting files from remote computers.
Can technicians access remote access?
Technicians cannot view, access, or modify settings established by administrators. Technicians are assigned with unique passwords. In case of Remote Access Plus cloud, technicians can set-up their own passwords. The administrators can also instantly revoke access to terminated technician (s).
Is Remote Access Plus cloud secure?
The data is stored within the customer's database. In case of Remote Access Plus cloud, the data transfer is completely secure under a highly reliable environment.
What is PCI DSS?
The Payment Card Industry Data Security Standard (PCI DSS) requires that any business handling customer payment information, namely credit cards, must do so securely and with customer privacy in mind. A main focal point of the requirement is the cardholder data environment (CDE), the core location where organizations store and/or process payment information.
What is PCI Section 7?
PCI Section 7 is concerned with how organizations control access to their CDE. Users need to be allowed access based on a least privilege basis: Only those who absolutely need access to customer data are allowed access to it. IT admins need to control how their users access virtually all of their resources, ensuring that only the requisite group of users are able to leverage the CDE.
What is Coalfire's audit?
Independent auditing firm Coalfire evaluates products in regard to helping organizations achieve compliance standards. In their assessment of the JumpCloud product, Coalfire found that using Directory-as-a-Service provides organizations with most of the requirements of PCI Section 8 and 10. You can read more about their findings here.
Why do employees open the floodgates to cybercrime?
One of the biggest reasons employees open the floodgates to cybercrime is that they’re frankly unaware of the dangers.#N#From day one, it’s essential to educate all personnel about internal security policies and the appropriate way to use computers for work purposes. At least once a year, ensure that your workforce is up-to-date on any changes to procedures, especially those related to work-at-home and BYOD.
What is a secure workspace environment?
Like VDI, a secure workspace environment can turn a non-corporate or personal Windows device into a secure BYOD solution that facilitates PCI-compliant remote access.# N#These platforms provide a secure, PCI DSS-compliant workspace environment with endpoint lockdown security and application control. Some of them include built-in location awareness and enable dynamic permissions updates based on an endpoint's local network and centrally managed policies. Look for a solution with the tools to manage, troubleshoot, update, and scale your entire BYOD environment from a single console, like Thinscale’s Secure Remote Worker.#N#Remember that PCI compliance with BYOD requires more than one solution; it also takes a firm commitment from both the organisation and its employees to adhere to specific practices and handle data responsibly.#N#That said, if your company is interested in adopting a secure workspace environment solution as part of a complete PCI compliance plan for BYOD, Thinscale can help with that.
Can a payment brand be fined for non-compliance?
On top of that, payment brands can fine financial institutions for non-compliance, and financial institutions can withdraw the ability to accept card payments from non-compliant merchants. Aside from the financial damage, non-compliant companies face significant long-term damage to their brand’s reputation.
Taking Back Control With Controlled Access
Guest post by Simon Parker, Minerva Building a Case for Next-Generation Access Control Identities are stolen more during the holidays than any other time of the year. That’s because this is the season in which shoppers use their credit and debit cards the most. And … Read more
PCI DSS v3.1 and SSL: What you should do NOW
12/21/15 Update: The PCI SSC is extending the migration completion date to 30 June 2018 for transitioning from SSL and TLS 1.0 to a secure version of TLS (currently v1.1 or higher). Learn more here. 4/15/15 Update: The PCI SSC released PCI DSS v3.1 on its … Read more
Visa Issues Security Alert Regarding Insecure Remote Access
The recent rash of data security breaches stemming from insecure remote access and user credential management issues has prompted Visa to issue a Data Security Alert to all merchants and the acquirers who serve them. Here is the statement from Visa’s email, which ControlScan received … Read more
How many computers do you need to run a remote desktop?
However they need 3 computers to have remote desktop setup. Bus being as such, they fail the test.
How to build and maintain a secure network?
Build and Maintain a Secure Network 1. Install and maintain a firewall configuration to protect cardholder data. 2. Do not use vendor-supplied defaults for system passwords and other security parameters . Protect Cardholder Data 3. Protect stored cardholder data.
Is Pertino safe for remote access?
After speaking with a PCI compliance auditor, they said that using Pertino is acceptable under the guidelines as long as the rest of the set up maintains compliance.