Main PCI-DSS Requirements for Remote Access
- Two-Factor Login. – One of the main requirements for any remote access is that a two-factor authentication method should be used.
- Access from Known Addresses. – When providing remote access using products like Microsoft’s remote Desktop©, access should only be provided to specific assigned locations.
- Remote Support. – Remote access passwords issued for outside vendors, such as your support company, must be temporary and assigned for each event and only be enabled when access is ...
- Install personal firewall software on portable computing devices that access the CDE remotely. ...
- Monitor third-party remote accesses. ...
- Use multi-factor authentication (MFA) controls. ...
- Use unique credentials for each customer, valid only for service providers.
What are the PCI DSS security requirements for remote workers?
PCI DSS provides several security requirements that should be implemented to protect remote workers and their environments. Some examples include: Use multi-factor authentication for all remote network access originating from outside the company’s network.
What are the PCI DSS requirements for a CDE?
PCI DSS Requirement 8.3: Secure all individual administrative access to the CDE and all remote access to the CDE using multi-factor authentication. PCI DSS Requirement 8.5: Do not use group, shared or public IDs, passwords or other authentication methods.
What are the PCI DSS requirements for multi-factor authentication?
PCI DSS requirement 8.3.2 requires you to use multi-factor authentication for all remote network access from outside the organization’s network, including user, administrator, and third-party access for support or maintenance. Use unique credentials for each customer, valid only for service providers.
What does PCI DSS 1210 require?
It also enabled testing of PCI DSS 12.10 requirement, which requires an incident response plan that includes business disaster recovery and business continuity actions. Below you can find the PCI DSS controls applied to all remote connections to the CDE, based on the overall network architecture.

What is needed for PCI DSS requirements?
You must have documented list of all the users with their roles who need to access card data environment. This list must contain, each role, definition of role, current privilege level, expected privilege level and data resources for each user to perform operations on card data.
Can you be PCI compliant working from home?
PCI DSS requirements may apply to work-from-home (WFH) environments in different ways, depending on the entity's business and security needs and how they have configured their infrastructure to support personnel working from home.
What is requirement 7 PCI DSS?
PCI DSS Requirement 7: Restrict access to cardholder data based on business requirements. Important data should be accessible only by authorized personnel. For this, systems and processes must be to limit access according to their merits and business responsibilities.
Is VNC PCI compliant?
VNC Connect remote access software enables PCI-DSS, HIPAA, and GDPR compliance, meeting all of the provided guidelines. Every connection is end-to-end encrypted with up to 256-bit AES encryption, 2048-bit RSA keys, and perfect forward secrecy, so sessions are entirely private to you now and in the future.
Is a VPN PCI compliant?
Platforms that provide remote connections such as virtual private network connections such as IPSEC/TLS VPN, virtual desktop infrastructure (VDI), remote desktop services (RDS), and workstations connecting remotely to the environment must comply with the following PCI DSS requirements.
Do I need to be PCI compliant if I use PayPal?
You may have heard that by using PayPal, your business is not subject to the PCI DSS. The truth is, even accepting PayPal payments requires you to be PCI compliant.
Is PCI DSS compliance mandatory?
Organizations that accept, store, transmit, or process cardholder data must comply with the PCI DSS. While not federally mandated in the United States, PCI DSS is mandated by the Payment Card Industry Security Standard council. The council is comprised of major credit card bands and is an industry standard.
How many PCI requirements are there?
For most companies, there are 12 main PCI controls to implement. These 12 requirements, spread across six groups, make up the core of the PCI DSS v. 3.2.
Which three 3 of these are PCI DSS requirements for any company handling processing or transmitting credit card data?
PCI REQUIREMENT 1: Install and Maintain Network Security Controls. PCI REQUIREMENT 2: Apply Secure Configurations to All System Components. Protect Account Data Maintain a Vulnerability Management Program. PCI REQUIREMENT 3: Protect Stored Account Data.
What is the difference between VNC and RDP?
Both protocols provide access to remote desktops for quick and easy remote working and troubleshooting. The main difference is that RDP is a virtual session and VNC captures the physical display; you see exactly what the remote user sees.
Is VNC a security risk?
Because it is ubiquitous and powerful, VNC has had several vulnerabilities exposed. The BleepingComputer link below lists 37 such vulnerabilities, affecting four VNC products. Most of these allow an attacker to execute code on the remote computer.
What protocol does VNC use?
Remote Frame Buffer protocol (RFB)In computing, Virtual Network Computing (VNC) is a graphical desktop-sharing system that uses the Remote Frame Buffer protocol (RFB) to remotely control another computer. It transmits the keyboard and mouse input from one computer to another, relaying the graphical-screen updates, over a network.
What is a PCI in workplace?
PCI compliance is adherence to a set of security standards of the Payment Card Industry Data Security Standard (PCI DSS). All companies that accept, process, store, or transmit credit card information have to be PCI compliant to ensure optimal security.
What rules must be practiced by merchants at POS terminals for PCI DSS compliance?
The 12 requirements of PCI DSS are:Install and maintain a firewall configuration to protect cardholder data.Do not use vendor-supplied defaults for system passwords and other security parameters.Protect stored cardholder data.Encrypt transmission of cardholder data across open, public networks.More items...•
How many PCI DSS requirements are there?
All organizations are required to meet a total of 12 PCI DSS requirements.
What is required to secure cardholder data transmitted over the network?
Strict policies and procedures are required to secure the cardholder data transmitted over the network. Certificate usage with robust encryption procedures, encrypted protocols and a secure key will ensure sensitive data transmission security.
What is a compliance requirement for hosting?
This requirement is designed for hosting service providers that offer hosting on a single server and share the system for multiple customers. Compliance with these requirements aims to protect the cardholder data of shared hosting service providers in shared environments by providing a secure environment.
What do employees need to know about their organization's information security policies and daily business procedures?
Employees need to be aware of and know about their organization’s information security policies and daily business procedures. To this end, the implementation of the policy should be reviewed. Also, all stakeholders should be made aware of the documentation.
Can you store sensitive authentication data on a card?
If there is a business reason for storing sensitive data, and the data is stored securely, it is permitted for organizations that provide services to store sensitive authentication data. Do not store the content of the magnetic stripe on the back of the card or data on the chip after authorization.
Why allow third party access to network 24/7?
Allowing third-party service providers unlimited access to your network 24/7 when they need to support your systems increases an unauthorized user’s chances in the environment or a malicious person finding and using an existing external entry point.
Why assigning an ID to each person with access is necessary?
To ensure that people are responsible for their actions , assigning a unique identification (ID) to each person with access is necessary. In this way, accountability is in question, and transactions on critical data and systems can be performed and monitored by known and authorized users and processes.
Can attackers guess passwords?
In the absence of account lockout mechanisms, attackers can continuously try to guess passwords through manual or automatic password cracking and guessing tools until they succeed and access a user’s account.
Do all users have to have a unique ID?
All users must be assigned a unique ID before they can access system components or cardholder data. Instead of using a single identity for several employees, an organization can maintain individual responsibility for actions and an adequate audit trail per employee, ensuring that they are uniquely identified.
Is multifactor authentication required for remote access?
In that case, it is unnecessary to use multi-factor authentication for remote access to that network. However, multi-factor authentication is required for any remote access to systems that have access to the cardholder data environment. It is recommended to use the organization’s networks for all remote access.
Why disconnect remote access sessions?
Automatically disconnect remote access sessions after a period of inactivity, to avoid idle, open connections being used for unauthorized access.
Why is it important to be aware of remote staff?
Remote staff additionally need to be aware of their physical surroundings, taking care to prevent sensitive information from being viewed by unauthorized persons. The organization’s security processes should be kept up to date and ready for any eventuality caused by threats originating from remote environments.
What is the first requirement for PCI DSS?
The first requirement of the PCI DSS is to protect your system with firewalls. Properly configured firewalls protect your card data environment. Firewalls restrict incoming and outgoing network traffic through rules and criteria configured by your organization.
What are the 12 requirements of PCI?
The point of the 12 requirements of PCI is to protect and secure stored cardholder data and prevent data breaches. And according to requirement 3, stored card data must be encrypted using industry-accepted algorithms (e.g., AES-256).
Why is PCI compliance important?
Its purpose is to help secure and protect the entire payment card ecosystem. Data breaches and data theft are unfortunately common, and negatively impact all payments parties in different ways—from retailers to consumers to banks—so the need for PCI compliance has never been greater.
What is the second part of requirement 12?
The second part of requirement 12 is to perform an annual, formal risk assessment that identifies critical assets, threats, and vulnerabilities. This requirement will help you identify, prioritize, and manage your information security risks.
When does physical security only apply?
Employees may think physical security only applies after hours. However, most data thefts (e.g., social engineering attacks) occur in the middle of the day, when staff is often too busy with their various assignments to notice someone walking out of the office with a server, company laptop, phone, etc.
Do you need a group password for PCI DSS?
According to PCI DSS requirement 8, user IDs and passwords need to be sufficiently complex and unique. You should not use group or shared passwords. However, your system security should not be based solely on the complexity of a single password.
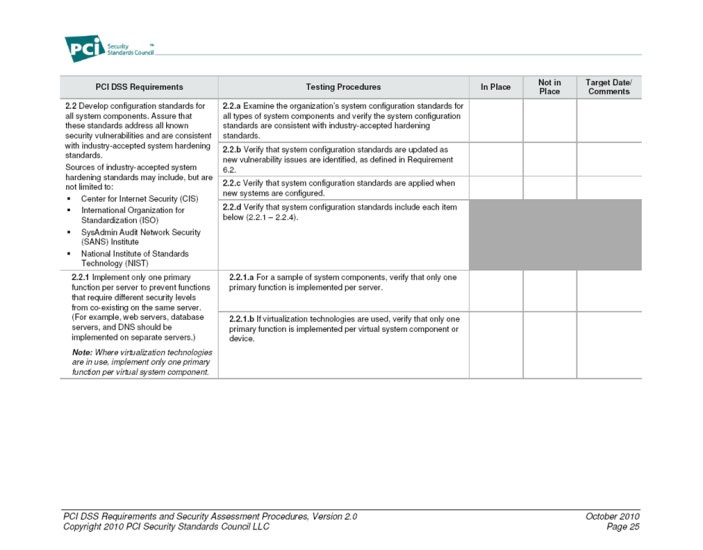
What is PCI DSS 2.2.1?
PCI DSS Requirement 2.2.1: Do not host functions that require different levels of security on the same server. Ensure that there is only one application that performs one primary function per server. PCI DSS Requirement 2.2.2: Enable only the services, protocols, and procedures required for the system to work.
Why is it important to keep a PCI DSS list up to date?
Keeping an up-to-date list of all system components covered by P CI will enable the organization to accurately and efficiently define the scope of their environment for PCI DSS audits. Most device components can be forgotten, ignored without inventory, and accidentally removed from the organization’s configuration standards.
What happens when the default settings of wireless networks are not changed?
When the default settings of wireless networks are not changed, and appropriate security configurations are not installed, attackers can quickly enter the network and monitor traffic passing over wireless networks, and easily capture data and passwords.
Why do employees need to be aware of security policies and day-to-day operating procedures?
Employees need to be aware of and support security policies and day-to-day operating procedures to ensure that vendor defaults and other compliance features are continuously managed to prevent unsafe configurations and installations.
When functions requiring different levels of security are placed on the same server with lower security functions, the level of protection for
When functions requiring different levels of security are placed on the same server with lower security functions, the level of protection for higher security requirements decreases , also, server functions with a lower level of security can create additional vulnerabilities on the same server.
Can malicious individuals compromise a corporate network?
Only appropriate resources and protocols should be allowed as part of the organization’s configuration standards and associated processes.
Is 802.11x encryption disabled?
Also, the key exchange protocol is disabled for older versions of 802.11x encryption, which can make encryption useless. Device software should be updated or replaced to support more reliable protocols.