Main PCI-DSS Requirements for Remote Access
- Two-Factor Login. – One of the main requirements for any remote access is that a two-factor authentication method should be used.
- Access from Known Addresses. – When providing remote access using products like Microsoft’s remote Desktop©, access should only be provided to specific assigned locations.
- Remote Support. – Remote access passwords issued for outside vendors, such as your support company, must be temporary and assigned for each event and only be enabled when access is ...
- Install personal firewall software on portable computing devices that access the CDE remotely. ...
- Monitor third-party remote accesses. ...
- Use multi-factor authentication (MFA) controls. ...
- Use unique credentials for each customer, valid only for service providers.
What are the PCI DSS security requirements for remote workers?
PCI DSS provides several security requirements that should be implemented to protect remote workers and their environments. Some examples include: Use multi-factor authentication for all remote network access originating from outside the company’s network.
Are remote access programs PCI compliant?
It should be noted that remote access programs may be PCI compliant. However, login must be implemented securely using multiple authentication factors, the connection must be encrypted, and associated passwords must meet all requirements set by the PCI Data Security Standard.
What are the PCI DSS requirements for facilities management?
PCI DSS Requirement 9.1: Create and use appropriate facility access controls to limit and monitor physical access to systems in the cardholder data environment. PCI DSS Requirement 9.2: Develop procedures to distinguish between staff and visitors easily. PCI DSS Requirement 9.3: Restrict physical access to sensitive areas for employees as follows.
What are the requirements for remote access?
Remote Access is covered by sub-requirements of requirement 1 (firewall) and requirement 8 (authentication), but I prefer managing them together. A personal firewall is required for mobile device (not in a fixed location) that may connect remotely to the network or to a network not controlled by the organization.
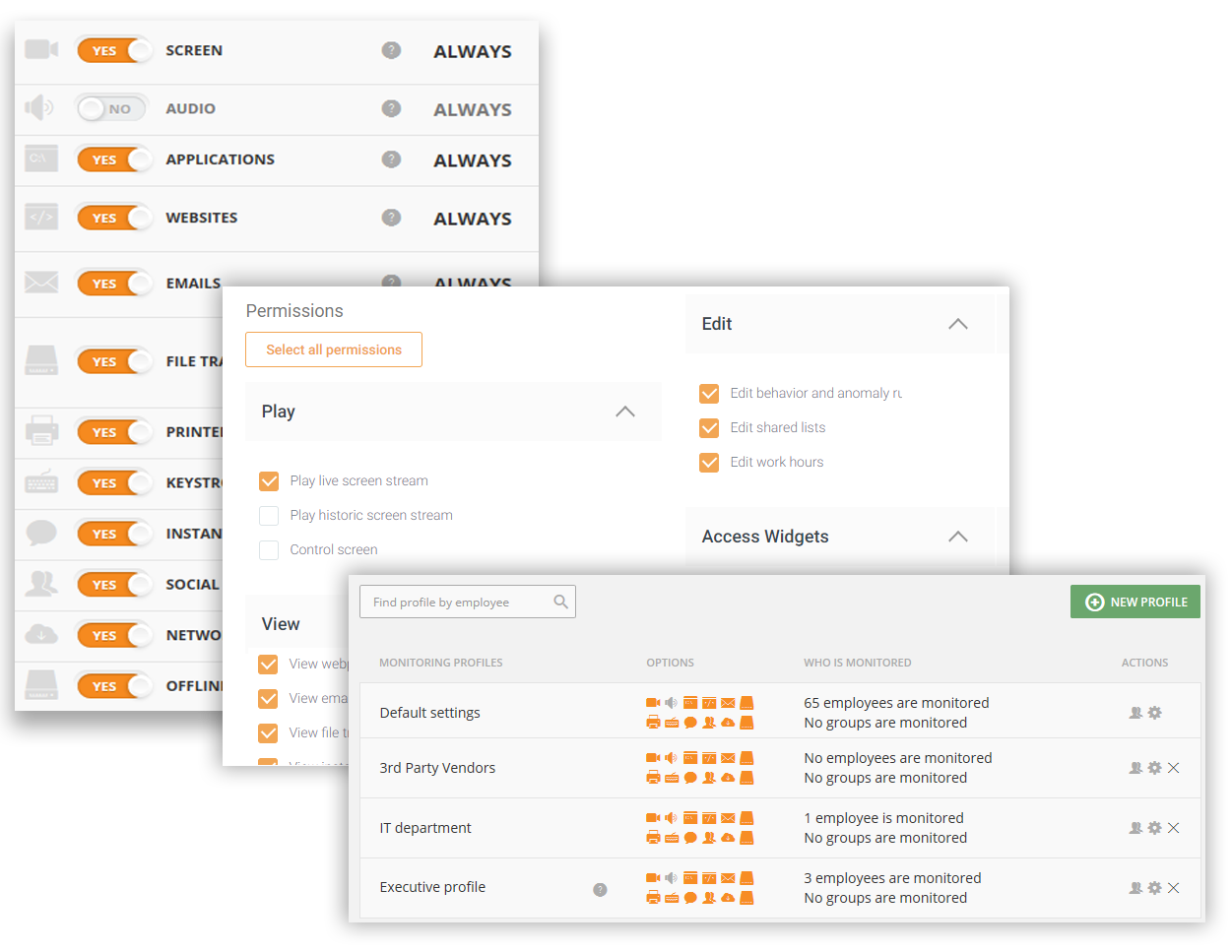
Can you be PCI compliant working from home?
PCI DSS requirements may apply to work-from-home (WFH) environments in different ways, depending on the entity's business and security needs and how they have configured their infrastructure to support personnel working from home.
What is needed for PCI DSS requirements?
You must have documented list of all the users with their roles who need to access card data environment. This list must contain, each role, definition of role, current privilege level, expected privilege level and data resources for each user to perform operations on card data.
Is MFA required for PCI?
The PCI DSS requires multi-factor authentication (MFA) mechanism for remote access to the Cardholder Data Environment (CDE).
How many requirements are there for PCI PSS?
12 RequirementsThe requirements set forth by the PCI SSC are both operational and technical, and the core focus of these rules is to protect cardholder data at all times.
What are the 4 PCI standards?
Level 1: Merchants that process over 6 million card transactions annually. Level 2: Merchants that process 1 to 6 million transactions annually. Level 3: Merchants that process 20,000 to 1 million transactions annually. Level 4: Merchants that process fewer than 20,000 transactions annually.
What is PCI compliance checklist?
This is essentially a policy that sets the tone for your entire organization's information security strategy. It needs to address all of your employees and reflect your attitude toward PCI compliance and overall data security. This includes training programs and continuing education to ensure proper practices.
What are MFA standards?
Definition(s): The means used to confirm the identity of a user, process, or device (e.g., user password or token).
What is MFA compliance?
Multi-factor authentication (MFA) is a powerful solution for achieving and maintaining compliance with the leading industry regulations. Lately it has also become a necessity to qualify for cyber insurance. This is because MFA significantly reduces the risk of system penetration, up to a remarkable 99%.
Is MFA an industry standard?
Multi-Factor Authentication (a.k.a. MFA, two-factor authentication or two-step verification) is a financial industry standard in which a user is required to provide additional verification when signing in.
Is PCI compliance mandatory?
Although the PCI DSS must be implemented by all entities that process, store or transmit cardholder data, formal validation of PCI DSS compliance is not mandatory for all entities. Currently, both Visa and MasterCard require merchants and service providers to be validated according to the PCI DSS.
What is Level 1 PCI compliance?
Stated, PCI DSS Level 1 is a set of requirements designed to ensure the highest level of security for businesses that store, transmit, or process credit card data. The highest compliance level, PCI DSS Level 1, identifies any merchant who processes more than 6 million Visa transactions per year.
How do I become PCI compliant for free?
How do I become PCI compliant for free? If your merchant account provider does not charge for PCI compliance, you can become PCI compliant at no additional cost by completing and filing your Self-Assessment Questionnaires each year and maintaining records of any required security scans.
Who does PCI DSS requirements apply to?
The PCI DSS applies to all entities that store, process, and/or transmit cardholder data. It covers technical and operational system components included in or connected to cardholder data. If you are a merchant who accepts or processes payment cards, you must comply with the PCI DSS.
Is PCI DSS a legal requirement?
The PCI DSS is a standard not a law, and is enforced through contracts between merchants, acquiring banks that process payment card transactions and the payment brands.
Is PCI DSS a regulatory requirement?
Organizations that accept, store, transmit, or process cardholder data must comply with the PCI DSS. While not federally mandated in the United States, PCI DSS is mandated by the Payment Card Industry Security Standard council. The council is comprised of major credit card bands and is an industry standard.
Which of the following web application security requirements is mandated by the PCI DSS?
PCI Requirement 6.6 requires that you ensure that all Web-facing applications are protected against known attacks by applying either of the following methods: Having all custom application code reviewed for common vulnerabilities by an organization that specializes in application security.
What are the requirements of the PCI DSS?
PCI DSS requirements apply to all system components, including people, processes and technologies included in the cardholder data or cardholder data environment, and to the storage, processing or transmission of card data linked to that environment.
What is a compliance requirement for hosting?
This requirement is designed for hosting service providers that offer hosting on a single server and share the system for multiple customers. Compliance with these requirements aims to protect the cardholder data of shared hosting service providers in shared environments by providing a secure environment.
How to ensure compliance with data retention requirements?
Compliance with this requirement can be achieved through the establishment of an official policy on data retention . The policy will determine what kind of data should be protected and what data should be destroyed if it is no longer needed.
What do employees need to know about their organization's information security policies and daily business procedures?
Employees need to be aware of and know about their organization’s information security policies and daily business procedures. To this end, the implementation of the policy should be reviewed. Also, all stakeholders should be made aware of the documentation.
Where should physical security measures be implemented?
Physical security measures should be implemented in data centers, server rooms and all other facilities where confidential data is stored, thus preventing unauthorized access.
Can you store sensitive authentication data on a card?
If there is a business reason for storing sensitive data, and the data is stored securely, it is permitted for organizations that provide services to store sensitive authentication data. Do not store the content of the magnetic stripe on the back of the card or data on the chip after authorization.
Payment Security: A Perspective from Europe
In the eighteen months plus since the outbreak of the COVID-19 global pandemic many businesses hav... READ MORE
Be On Alert This Holiday Season
In this blog we explore the challenges around security of payment data during the hectic holiday s... READ MORE
Resource Guide: Defending Against Ransomware
Ransomware attacks have been front and center in the news recently due to high-profile breaches that... READ MORE
Cybersecurity Month: Be Cyber Smart
As an Official Champion of National Cyber Security Awareness Month (NCSAM), the Council will be sha... READ MORE
Back-to-Basics: Secure Remote Access
As small and medium businesses begin to re-open following the pandemic, it’s important to do so se... READ MORE
Guidance: How PCI DSS Requirements Apply to WFH Environments
PCI DSS requirements may apply to work-from-home (WFH) environments in different ways, depending o... READ MORE
Beware of ATM Cash-Outs
PCI SSC and ATMIA share guidance and information on protecting against ATM Cash-outs. READ MORE
What is PCI DSS 8?
PCI DSS Requirement 8 covers identification and authentication for all access to system components.
Why allow third party access to network 24/7?
Allowing third-party service providers unlimited access to your network 24/7 when they need to support your systems increases an unauthorized user’s chances in the environment or a malicious person finding and using an existing external entry point.
Why assigning an ID to each person with access is necessary?
To ensure that people are responsible for their actions , assigning a unique identification (ID) to each person with access is necessary. In this way, accountability is in question, and transactions on critical data and systems can be performed and monitored by known and authorized users and processes.
Do all users have to have a unique ID?
All users must be assigned a unique ID before they can access system components or cardholder data. Instead of using a single identity for several employees, an organization can maintain individual responsibility for actions and an adequate audit trail per employee, ensuring that they are uniquely identified.
Do privileged user IDs have privileges?
Privileged user IDs and general user IDs should be reviewed and verified that each user ID and privileged user IDs only have the privileges specified in the documented approvals.
Why disconnect remote access sessions?
Automatically disconnect remote access sessions after a period of inactivity, to avoid idle, open connections being used for unauthorized access.
Why is it important to be aware of remote staff?
Remote staff additionally need to be aware of their physical surroundings, taking care to prevent sensitive information from being viewed by unauthorized persons. The organization’s security processes should be kept up to date and ready for any eventuality caused by threats originating from remote environments.
What is PCI SSC?
The PCI Security Standards Council (PCI SSC) is a global forum that brings together payments industry stakeholders to develop and drive adoption of data security standards and resources for safe payments worldwide. < Return to Blog Home Print.
What is MFA in PCI?
To help organizations combat this growing threat, the PCI Security Standards Council (PCI SSC) has issued guidance on the proper use of multi-factor authentication (MFA) for preventing unauthorized access to computers and systems that process payment transactions.
Does PCI DSS require MFA?
While PCI DSS does not currently require MFA implementations to meet all the principles described in this guidance document, it may in the future, and these industry-recognized best practices provide a roadmap for future security considerations.
