- Navigate to VPN > IPsec, Mobile Clients tab in the pfSense software GUI.
- Configure the settings as follows: Enable IPsec Mobile Client Support. Checked. User Authentication. Local Database (Not used, but the option must have something selected) Provide a virtual IP address to clients. Unchecked. ...
- Click Save.
How to access inside network pfSense?
In the pfSense® webGUI, go to Interfaces > (new OPT interface), and Enable the interface. Give it an IP address in the same subnet as the modem, such as 192.168.1.5/24. Do not set a gateway.
How to set up an OpenVPN client in pfSense?
on PFSense Simply navigate to VPN – OpenVPN and click on their Clients’ tab. The form will then pop up once you click the ‘+Add’ button. In this window you’ll open a tool to edit OpenVPN, which has sections such as General information, User Authentication Settings, Cryptographic settings, Tunnel settings, and Advanced Configurations.
How to setup NordVPN on pfSense?
pfSense 2.5 Setup with NordVPN 1. To set up OpenVPN on pfSense 2.5.0, access your pfSense from your browser, then navigate to System > Certificate... 2. For this tutorial, we will configure our pfSense to connect to a server in the Netherlands, but you should connect to... 3. Navigate to VPN > ...
How to configure IPsec?
To configure a route-based or policy-based IPsec VPN using autokey IKE:
- Configure interfaces, security zones, and address book information. (For route-based VPNs) Configure a secure tunnel st0.x interface. ...
- Configure Phase 1 of the IPsec VPN tunnel. ...
- Configure Phase 2 of the IPsec VPN tunnel. ...
- Configure a security policy to permit traffic from the source zone to the destination zone. ...
- Update your global VPN settings.

Which is better IPsec or OpenVPN?
In site-to-site connections, OpenVPN functions faster and provides more security than IPsec. IPsec encryption operates on a kernel level, whereas OpenVPN functions in user space. Therefore, in terms of endpoint performance, IPsec is more favorable. With OpenVPN, you're limited to the capacity of the software.
Which rules are added automatically in pfSense for IPsec connections?
pfSense® software automatically adds hidden firewall rules which allow traffic required to establish enabled IPsec tunnels. The traffic required to establish a tunnel includes: UDP port 500 (or a custom configured Remote IKE Port on a tunnel) UDP port 4500 (or a custom configured Remote NAT-T Port on a tunnel)
Does pfSense support IKEv2?
To make Windows 10 clients work, we need to add support to the following algorithms on the server-end. With these two slightly weaker algorithms added, the Windows 10 built-in VPN client will be able to connect to the pfSense IKEv2 VPN server.
What is IPsec pfSense?
IPsec on pfSense® software offers numerous configuration options which influence the performance and security of IPsec connections.
What ports need to be open for IPSec VPN?
Mobile VPN with IPSec requires the client to access the Firebox on UDP ports 500 and 4500, and ESP IP Protocol 50. This often requires a specific configuration on the client's internet gateway, so clients might not be able to connect from hotspots or with mobile Internet connections.
Why does IPSec not work with NAT?
Unfortunately, conventional NAT does not work on IPSec packets because when the packet goes through a NAT device, the source address in the packet changes, thereby invalidating the packet. When this happens, the receiving end of the VPN connection discards the packet and the VPN connection negotiations fail.
Does pfSense use Strongswan?
PfSense firewall uses an open source tool Strongswan which provides the IPsec VPN functionality. Both phases of IPsec (Key sharing and encryption) is implemented by Strongswan tool on Linux/Unix platforms.
What is IPsec identifier?
The L2TP/IPsec client on Android has the ability to set a custom identifier, which allows L2TP/IPsec to function with the server on pfSense® software using Pre-Shared Keys. Clients on other operating systems do not allow for this, which makes them incompatible with current versions of pfSense software.
How do I enable Mobike option in IPsec tunnel?
Mobile Client SettingsNavigate to VPN > IPsec, Mobile Clients tab.Enable IPsec: Enable IPsec Mobile Client Support. Checked. ... Set the authentication options as follows: User Authentication. ... Set the Client Configuration options. ... Click Save.Click Create Phase 1 at the top of the screen if it appears.
Is L2TP the same as IPsec?
for L2TP. L2TP is a networking protocol used by the ISPs to enable VPN operations. IPsec. IPsec is a protocol suite for secure IP communications that authenticates and encrypts each IP packet in a communication session.
Does WireGuard use IPsec?
WireGuard is a more modern, simpler VPN protocol than IPsec, as well as being more secure by default. As of 2021, most operating systems support WireGuard through a kernel-based implementation.
What are pfSense floating rules?
Floating Rules are a special type of advanced rule that can perform complicated actions not possible with rules on interface or group tabs. Floating rules can act on multiple interfaces in the inbound, outbound, or both directions.
Which firewall rules you will need to add to permit IPsec VPN connections?
A: To make IPSec work through your firewalls, you should open UDP port 500 and permit IP protocol numbers 50 and 51 on both inbound and outbound firewall filters.
Which of the following statements is not true of IPsec?
Which of the following statements is NOT true of IPsec? SelectedAnswer:IPsec can provide authentication but notencryption. IPsec may offer authentication but not encryption, according to a common misconception.
What is IPsec configuration?
Internet Protocol Security (IPsec) is a set of security protocols used to transfer IP packets confidentially across the Internet. IPsec is mandatory for all IPv6 implementations and optional for IPv4.
In which layer does IPsec operate in the TCP IP model?
layer 3What is IPsec? IPsec helps keep private data secure when it is transmitted over a public network. More specifically, IPsec is a group of protocols that are used together to set up secure connections between devices at layer 3 of the OSI model (the network layer).
How to enable IPsec on a VPN?
First, enable IPsec on the firewall if it has not already been enabled: Navigate to VPN > IPsec. Check Enable IPsec. Click Save. Mobile client support must also be enabled: Navigate to VPN > IPsec. Click on the Mobile clients tab (Figure Enable Mobile IPsec Clients ). Check Enable IPsec Mobile Client Support.
How to enter hostname in VPN?
Choose Distinguished Name from the drop-down list and then enter the hostname of the firewall, same as it was entered into the server certificate, vpn.example.com
What settings are pushed to the client?
Some settings may be pushed to the client, such as the client IP address and DNS servers. These options are shown in Figure Mobile Clients Pushed Settings. Support for these options varies between clients, but is common and well-supported in most current operating systems.
How many times can you repeat a VPN?
Repeat as many times as needed for additional VPN users.
When Provide a DNS server list to clients is checked, and IP addresses are entered for the local DNS servers, such?
When Provide a DNS server list to clients is checked, and IP addresses are entered for the local DNS servers, such as 10.3.0.1, these values are sent to clients for use while the VPN is connected.
What is PfSense firewall?
PfSense firewall uses an open source tool Strongswan which provides the IPsec VPN functionality. Both phases of IPsec (Key sharing and encryption) is implemented by Strongswan tool on Linux/Unix platforms. It provides the internet key exchange (IKE) or automatic sharing of keys among nodes or gateways of IPsec VPN and then uses the Linux/Unix kernel implementation of authentication (AH) and encryption ( ESP). Stongswan uses the OpenSSL implementation of cryptographics algorithms ( such as AES128/256, MD5/SHA1 etc) in the first phase (IKE phase) of IPsec VPN. Encapsulated security payload (ESP) of IPsec VPN is available in Linux / Unix kernels which is uses by Strongswan in the second phase of VPN.
How to create a tunnel on PfSense?
Check Enable IPsec option to create tunnel on PfSense. Click on plus button to add new policy of IPsec tunnel on local side (side-a in this case). Following snapshots show the setting for IKE phase (1st phase) of IPsec.
What is the default encryption algorithm for first phase?
The Main mode is selected because it is more secure than aggressive mode. The Pre shared key or shared secret for both devices is "test12345" . The following snapshot also shows the encryption setting for first phase. Default selection of encryption algorithm is AES256 and SHA1 for hashing algorithm.
What is the second phase of IPsec?
In the first phase, IKE is configured and encryption/authentication algorithm are selected. Second phase of IPsec is setting ESP parameters such as encryption/authentication on both VM. Setting such as local/remote ip, local/remote networks, encryption/authentication algorithms ) of IPsec VPN on both VM's should be correct to establish tunnel between VM.
What is IPsec rule?
IPsec rule is also configured in firewall to pass traffic through the established VPN. It is also important to make sure that remote device is available for IPsec VPN. Following snapshot shows that, remote device is up and replying back. After ensuring gateway to gateway connectivity, next step is to configure VPN (both phase 1 and phase 2) on VM's.
What is IPsec protocol?
Two components of IPsec protocol are Authentication Header (AH) and Encapsulating Security Payload (ESP) to provide packet integrity, authentication and confidentiality security features. Cryptographic security mechanism are used in IPsec to protect communications over IP layer. IPSec protocol allows to encrypt and authenticate all IP layer traffic between local and remote location.
Is VPN policy successfully created on PfSense?
The following snapshot shows that VPN policy is successfully created on the PfSense device -a.
How to add P2 to IPsec?
On the IPsec VPN tunnels page (where you should be right now), for our P1 entry we just created, we click successively on the “Show Phase 2 Entries (0)”, then on “+ Add P2”.
How many rules are there for VPN?
There is at least two rules to configure: one rule for the traffic from the LAN to the IPsec VPN ; and another one for the traffic from the VPN to the LAN.
What encryption algorithm should I use for AES?
Encryption Algorithm: if both parties support AES-GCM, we recommend the use of AES256-GCM or AES128-GCM; this will provide a good level of encryption and will be compatible with the cryptographic acceleration offered by AES-NI. Otherwise, ideally choose AES with a key length of 256 bits. Finally, we keep SHA256 for hash function and 14 or 16 for the value of the Diffie-Hellman group (DH group – used for key exchange).
What is PfSense Plus?
pfSense Plus is a powerful product with a rich set of add-in packages that allow customers to tailor it to almost any edge or cloud secure networking need. We have conveniently grouped its capability set into the five most commonly needed applications.
What is remote access VPN?
A remote-access VPN requires the employee’s device to be equipped with client software which communicates with the VPN gateway, authenticates you as a remote user, and creates a secure tunnel between the employee device to the LAN.
What is VPN gateway?
For businesses, remote-access VPNs enable employees working anywhere to securely connect to the company’s local area network (LAN) via a VPN gateway, as if the employee was physically or wirelessly plugged into the LAN.
What is IPsec used for?
It helps keep data sent over public networks secure. IPsec is often used to set up VPNs, where it both encrypts IP packets and authenticates the source from where the packets originated.
What is VPN in the internet?
What is a VPN? A Virtual Private Network (VPN) provides secure network connections to traverse a public network, like the Internet. VPNs encrypt your internet traffic and conceal your online identity in real-time, making it more difficult for third parties to track your online activity or steal your data.
Why is VPN important?
significantly improves security posture. Business, Education, Government. A VPN is an essential tool for keeping organizations protected from data breaches.
Why do people use OpenVPN?
Many home users use OpenVPN at home to provide secure access to their home network as well as privacy on public networks. Remote Workers. Remote working creates a security risk in many ways, including giving cybercriminals new attack paths. Hackers can intercept unencrypted connections, for example.
The IPSec tunnel
First of, setting up the IPSec tunnels between the two PFSense firewalls is easily done and there is a ton of guides/howtos on the Internet, here is one that will do the trick: https://lifeoverlinux.com/how-to-setup-ipsec-vpn-on-pfsense-2-3/
The OpenVPN Server setup
Next up is configuring the OpenVPN Server of PFSense. In our environment, we have setup the full shabang with Active Directory integration for User authentication, but less can do it.
IPSec works, OpenVPN remote access works – but not together – what now ?
The first two parts of this blog post was the easy parts – again there is a ton of guides on the Internet and I think it should be reasonable easy to get this far – however now you find out that:

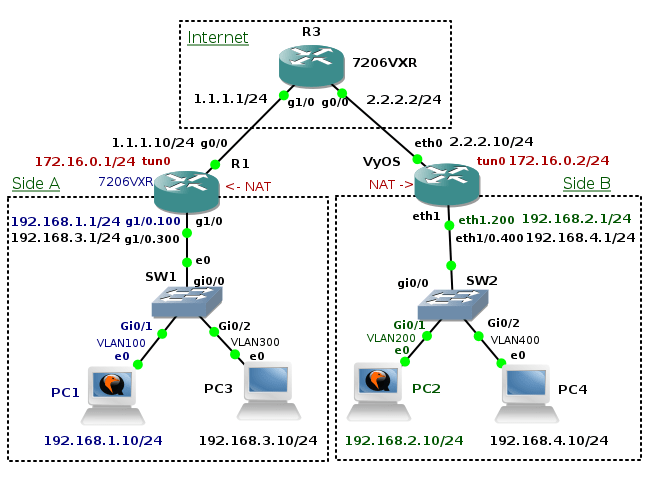
Network Diagram
1/3 – Configuring The Phase 1
- Go to VPN > IPsec: Click on the “+ Add” button. The fields to be filled in are the following: 1. Disabled: check this case to disable this phase 1 (and thus to disable the IPsec VPN). 2. Key Exchange version: allows you to choose the version of the IKE (Internet Key Exchange) protocol. Choose “IKEv2“. If the other peer does not support IKEv2 or if ...
2/3 – Configuring The Phase 2
- On the IPsec VPN tunnels page (where you should be right now), for our P1 entry we just created, we click successively on the “Show Phase 2 Entries (0)”, then on “+ Add P2”. The fields to be filled in are the following: 1. Disabled: check this case to disable this phase 2. 2. Mode: keep the default value “Tunnel IPv4”. 3. Local Network: the local subnet reachable through this VPN. In our case …
3/3 – Configuring The Firewall Rules
- There is at least two rules to configure: one rule for the traffic from the LAN to the IPsec VPN ; and another one for the traffic from the VPN to the LAN. For the LAN rule, look for an example: For the IPsec VPN rule, look for an example: The configuration is done. It should work. Did you like this article? Are you looking for professional equipment? Visit our shop.