Why choose access pm group?
They always respond to my emails instantly, like... As an out of town owner for the past year, Access PM Group has been a critical partner in managing the house preparation, tenant search, and ongoing tenant... I work with Access Property Management on the contractor side -- I appreciate the timely and clear communication I receive from the staff.
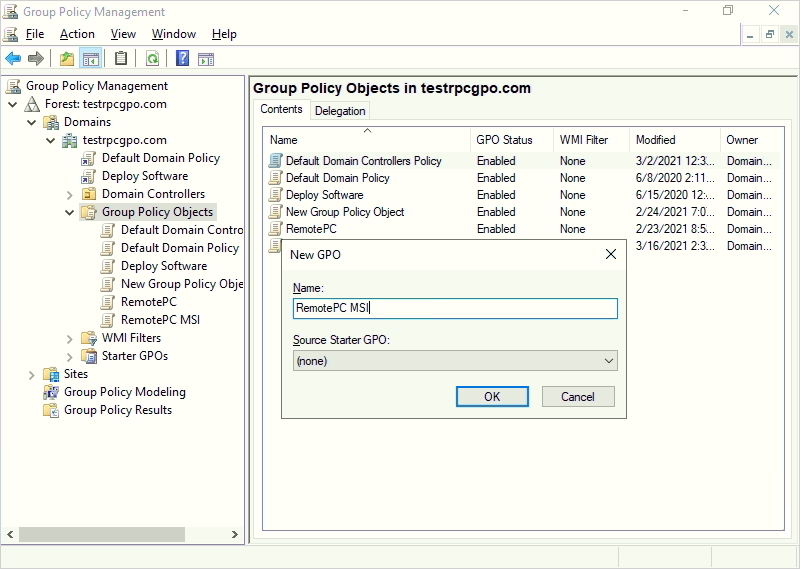
How do I manage Remote Desktop Services log on policies?
This section describes different features and tools available to help you manage this policy. To use Remote Desktop Services to successfully log on to a remote device, the user or group must be a member of the Remote Desktop Users or Administrators group and be granted the Allow log on through Remote Desktop Services right.
How fast does login pmgroup-global load?
+ How fast does login.pmgroup-global.com load? Average Load Time: (1644 ms) 50 % of sites are slower Page Speed(Google PageSpeed Insights) - Desktop 85 0-4950-8990-100i Field Data Over the last 30 days, the field data shows that this page has a speed compared to other pages in the Chrome User Experience Report.
Is pm Hotel Group a good company to work for?
“PM Hotel Group performed highest in the most categories identified as indicators of a strong culture.” “PM Hotel Group was named to the 2019 Inc. 5000 list, which ranks the country’s top 5000 fastest-growing private companies according to percentage revenue growth over a three-year period.”
How to exclude users from remote desktop?
To exclude users or groups, you can assign the Deny log on through Remote Desktop Servicesuser right to those users or groups. However, be careful when you use this method because you could create conflicts for legitimate users or groups that have been allowed access through the Allow log on through Remote Desktop Servicesuser right.
What is remote desktop policy?
This policy setting determines which users or groups can access the logon screen of a remote device through a Remote Desktop Services connection. It is possible for a user to establish a Remote Desktop Services connection to a particular server but not be able to log on to the console of that same server.
Can you remove allow log on through Remote Desktop Services?
You should confirm that delegated activities are not adversely affected.
Can you log on to a domain controller?
For domain controllers, assign the Allow log on through Remote Desktop Servicesuser right only to the Administrators group. For other server roles and devices, add the Remote Desktop Users group. For servers that have the Remote Desktop (RD) Session Host role service enabled and do not run in Application Server mode, ensure that only authorized IT personnel who must manage the computers remotely belong to these groups.
Can you log on to Remote Desktop Services?
To use Remote Desktop Services to successfully log on to a remote device, the user or group must be a member of the Remote Desktop Users or Administrators group and be granted the Allow log on through Remote Desktop Servicesright. It is possible for a user to establish an Remote Desktop Services session to a particular server, but not be able to log on to the console of that same server.
When does a user rights assignment become effective?
Any change to the user rights assignment for an account becomes effective the next time the owner of the account logs on.
Can you deny log on to a group?
Alternatively, you can assign the Deny log on through Remote Desktop Servicesuser right to groups such as Account Operators, Server Operators, and Guests. However, be careful when you use this method because you could block access to legitimate administrators who also belong to a group that has the Deny log on through Remote Desktop Servicesuser right.
How to Protect Yourself Against Cyber Fraud
In order to help prevent Cyber Fraud, you should be aware of potential external threats and leverage the security features and functionality available to you within J.P. Morgan Access ® .
How to Protect Yourself Against Malware and Social Engineering Attacks
J.P. Morgan has received reports of fraudsters successfully installing on clients' computers malware that requests the user to make multiple log on attempts, enter token codes multiple times as part of the log on, or asks the user to have someone else log on from their machine.
What to do if you suspect fraud or a cyber security attack
At J.P. Morgan, we use a variety of technologies and techniques to help protect the security of our products and services. It also necessary for you to protect yourself when you use your computer or conduct business online.