
For remotely hosted PoCs, the remote PC infrastructure is hosted at a secure data center and accessed via VPN
Virtual private network
A virtual private network extends a private network across a public network, and enables users to send and receive data across shared or public networks as if their computing devices were directly connected to the private network. Applications running on a computing device, e.g…
Full Answer
What is remote access security?
Remote access security solutions allow organizations to safely extend business applications and services to teleworkers and nomadic users without impairing user experience or productivity.
Why are some remote access protocols not secure?
Some remote access protocols are not inherently secure. For instance, some of them don’t support data-in-motion encryption. Cybercriminals are out to exploit the vulnerabilities of remote access environments in order to steal personal data, financial data, trade secrets, and other valuable information.
How can I secure remote access to my devices?
Your secure remote access policy should also incorporate provisions on which devices are used for access (e.g., you might limit access to company-managed devices), what company files can be downloaded, what applications can be used on the managed device, who to contact when the user suspects malicious activity, etc. 2.
Is remote access to workplaces secure?
While remote work does have several benefits for both employees and employers, it also opens a whole new set of risks. Many of those risks exist during remote access. If businesses can establish secure remote access, remote work can be just as secure as if employees are working onsite.
What is POS security?
Point-of-sale security (POS security) creates safe environments for customers to make purchases and complete transactions. POS security measures are crucial to prevent unauthorized users from accessing electronic payment systems and reduce the risk of credit card information theft or fraud.
What are POS vulnerabilities?
Security vulnerabilities in point-of-sale (PoS) terminals produced by two of the biggest manufacturers of these devices in the world could have allowed cyber criminals to steal credit card details, clone terminals and commit other forms of financial fraud at the cost of both buyers and retailers.
How do you protect from remote access?
Best Tips to Protect Remote Desktop ConnectionUse strong passwords. ... Update your software. ... Limit access using firewalls. ... Enable Network Level Verification. ... Limit users who can log in using remote desktop. ... Use two-factor authentication on highly sensitive systems.
Can POS be hacked?
One of the most common methods hackers use for acquiring access to internal POS systems is with the use of malware software programs that secretly exploit vulnerabilities on business computers and gather data such as credit card numbers, account details, and other types of sensitive information.
What are POS systems attacked with?
One of the most prevalent methods of POS attacks involves using RAM scrapers. RAM scrapers are able to capture card data before it gets encrypted, the malware then digests the card information and transfers it to a file on the attacker's computer.
Is remote access a security risk?
Remote access risks pose a serious threat to your business, but they can be prevented. Remote access risks were responsible for 88% of all hacking breaches and 95% of malware incidents in 2011.
Can VPN stop remote access?
While having some similarities, VPN and remote desktop are functionally different things. A VPN will give you access to a network while remote desktop (or RDP) will give you control of an entire computer. If you want to have full control over a local computer from a remote location, VPN won't let you achieve that.
What is remote access security?
Secure remote access refers to any security policy, solution, strategy or process that exists to prevent unauthorized access to your network, its resources, or any confidential or sensitive data. Essentially, secure remote access is a mix of security strategies and not necessarily one specific technology like a VPN.
How do I stop unauthorized remote access?
Here are our recommendations to help you prevent unauthorized data access:Keep Current on all Security Patches. ... Detect and Respond to Intrusions Quickly. ... Implement Principle of Least Privilege (Minimize Data Access) ... Use Multi-Factor Authentication. ... Implement IP Whitelisting. ... Encrypt Network Traffic Inside the System.More items...•
How do you secure remote access to employees?
7 Best Practices For Securing Remote Access for EmployeesDevelop a Cybersecurity Policy For Remote Workers. ... Choose a Remote Access Software. ... Use Encryption. ... Implement a Password Management Software. ... Apply Two-factor Authentication. ... Employ the Principle of Least Privilege. ... Create Employee Cybersecurity Training.
What is a common way to help protect devices connected to the company network?
What is a common way to help protect devices connected to the company network? A. Only use laptops and other mobile devices with full-disk encryption. This is correct!
Securing Your Remote Workforce
Covid-19 sent the global workforce remote, but has it fundamentally changed the future of work? Early research suggests it has. In fact, Gartner polling of business leaders suggest that close to 75% plan to shift some remote employees to remote work permanently. This has serious implications for security, risk, and compliance.
Remote Access Solutions
Remote access isn't just about data risk - it's also about enablement. Focal Point can help you design a program that allows your workforce to do their jobs seamlessly and securely.
Core Differentiators
At Focal Point, we take a different approach to remote access management.
Contact Us
Focal Point is excited to take on your biggest data risk challenges. Please complete this short form and we will get in touch with you.
What is a click policy?
Click policies. A policy is a set of conditions that must be met to apply an action. A policy contains one or more conditions and a single action. You can create a policy with multiple conditions and one action that can be applied to a user’s account.
What is Citrix Analytics for Security?
Citrix Analytics for Security continuously assesses the behavior of Citrix Virtual Apps and Desktops users and Citrix Workspace users and applies actions to protect sensitive corporate information. The aggregation and correlation of data across networks, virtualized applications and desktops, and content collaboration tools enables the generation of valuable insights and more focused actions to address user security threats. More information on Citrix Analytics for Security can be found here and videos demonstrating the Citrix Analytics for Security can be found here.
What is user risk indicator?
User risk indicators are user activities that look suspicious or can pose a security threat to your organization. User risk indicators span across all Citrix products used in your deployment. The indicators are based on user behavior and are triggered where the user’s behavior deviates from the normal.
How long does it take to connect to an agent?
click Connect to Installed Agent. This process can take a few minutes.
Multi-Factor Authentication
MFA functionality helps businesses defend against credential theft and user impersonation by positively confirming a user’s identity.
Adaptive Authentication
The latest remote access security solutions support adaptive authentication to optimize user experience and satisfaction.
Single Sign-On
Single Sign-On functionality allows remote users to access multiple applications and systems using a common set of usernames and passwords. SSO boosts user satisfaction by preventing password fatigue and mitigates risk by eliminating unsecure user behaviors like writing passwords on sticky notes or using a single password for many applications.
Securing Remote Access by Third-Party Vendors
Many businesses rely on third-party vendors to manage their IT infrastructure and applications. These external service organizations need remote privileged access to corporate IT systems to maintain and update them.
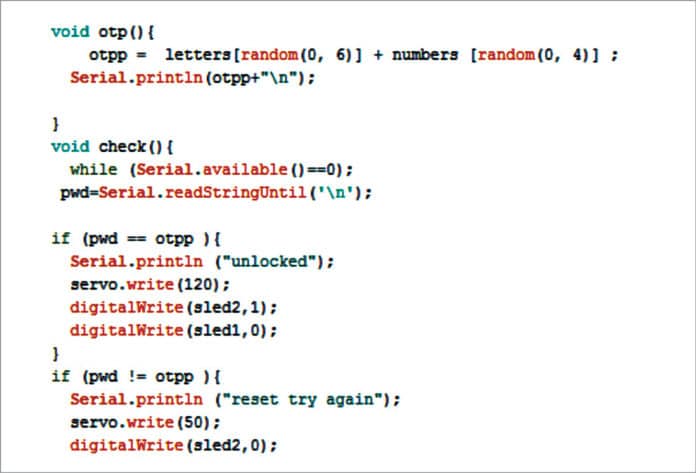
How PoC exploits work
Typically, PoC exploits are done by a vendor working for the company. By simulating an actual attack, it allows the company to patch the security hole without systems or data being compromised.
PoC code and zero-day exploits
PoC code is a term used to describe a code that was developed to demonstrate security flaws in software or networks during a PoC exploit. IT departments use it to simulate attacks to identify vulnerabilities and patch them. PoC code can also be used to determine a threat level.
Publishing PoC code put and cyber-attack
As long as the PoC code is published after any weaknesses in the security is patched, a company should not have to worry about putting their cybersecurity at additional risk.
Demand Generation Lead
Opendorse Maximizing name, image and likeness value for 35,000+ athletes today — and 500,000+ student-athletes tomorrow.
Growth Strategist
Cro Metrics We help companies grow through strategic, data-driven experimentation.
Growth Marketing Manager
RippleMatch Using AI to help employers increase diversity and find the best and brightest early career candidates in the country.
Market Analyst and Research Writer
Ironpaper Ironpaper is a digital agency that specializes in the B2B buyer's journey.
Systems Engineer
Dmarcian Dmarcian provides tools, support, & advocacy to continue growing #DMARC within the email ecosystem. We help prevent #cyberattacks with #cybersecurity for #email
Software Engineer
Dmarcian Dmarcian provides tools, support, & advocacy to continue growing #DMARC within the email ecosystem. We help prevent #cyberattacks with #cybersecurity for #email
QA Automation Engineer
Dmarcian Dmarcian provides tools, support, & advocacy to continue growing #DMARC within the email ecosystem. We help prevent #cyberattacks with #cybersecurity for #email
What is Harmony security?
Harmony unifies endpoint, browser, e-mail, and remote access security components to protect user devices and networks against known and unknown threats. Harmony integrates key security capabilities into a single solution to deliver:
What is Check Point Harmony?
Enter Check Point Harmony, the industry’s first unified solution for remote work. Harmony consolidates six security products to provide uncompromised protection, safeguarding devices and Internet connections from attack while ensuring Zero-Trust Access for corporate applications.
Is remote work permanent?
The business world has comprehensively shifted over the last year into remote work, a way of life that may be permanent for many organizations. Staying connected at a time of widespread change is paramount, as your employees must be able to work from anywhere on any device, and have access to work-related applications at all times.
How to restrict RPC access to terminal server?
Restrict RPC management access to the terminal server by requiring security – For management purposes , restrict RPC access to the TS. This is done through either a GPO linked to the OU where the TS computer accounts are located, or by using local policies.
How to control who can connect to a terminal server?
Use granular permissions to control who can connect to the terminal server – Typically, default settings are adequate for regular TS deployments, however in order to increase security you should consider manually changing the scope of users and groups that are allowed to log on to the TS, and what they can do. For example, who can reset a connection, who can remote control another session, and who can send messages to other concurrent sessions.
What is TS gateway in Windows Server 2008?
When using Windows Server 2008 Terminal Server, consider using TS Gateway – Using the new capabilities of Microsoft Windows Server 2008 TS Gateway provides further protection of RDP traffic by encapsulating it into SSL packets – much like SSL VPN, but without the need to deploy special VPN servers. The benefit of using the TS Gateway capabilities of Microsoft Windows Server 2008 is that remote users will only be granted access to the internal servers based upon a strict policy that can be enforced on the TS Gateway, and when combined with the NAP capabilities of the system, will only allow connection of computers that fully meet the security requirements set by the administrator.
What port does a firewall use to connect to a terminal server?
While your mileage may vary, it’s worth noting that RDP communication uses TCP port 3389, and all firewalls, routers and NAT devices between the remote clients and the terminal servers should be configured to properly allow (or block) traffic based upon your design.
How to configure IP address filtering on terminal server?
Use a mechanism to configure IP Address filtering on the terminal server – This will allow only specific IP Addresses to connect to the terminal server. To do that, you can either use the built-in Windows Firewall (depending on the version of Windows that you’re using), or a 3rd-party firewall that is installed on the servers. You can also use IPSec to implement blocking filters (In Windows Server 2008 IPSec blocking filters is a part of the Windows Firewall with Advanced Security).
Why use IPSEC?
Consider implementing IPSec between the client and the terminal server – If the protection of the traffic between the clients and the terminal server is important, use IPSec to add an extra layer or security and encryption to the traffic.
How does encryption work in terminal services?
Implement data encryption on the terminal server – For Terminal Services connections, data encryption can protect your data by encrypting it on the communications link between the client and the server. Encryption protects against the risk of unauthorized transmission interception on the link between server and client. By default, Terminal Services connections are encrypted at the highest level of security available (128-bit). However, some older versions of the Terminal Services client do not support this high level of encryption. You can select the level of encryption, with higher encryption offering better security, but adding extra CPU cycles to the server.

Overview
Scope
- In this Proof-of-Concept guide, you experience the role of a Citrix administrator and you create a connection between your organization’s Secure Private Access deployment and Citrix Secure Internet Access for Corporately Owned Devices. This guide showcases how to perform the following actions: 1. Logging into Citrix Secure Internet Access (CSIA) 2. Interfacing CSIA Securi…
Prerequisites
- Microsoft Windows 7, 8, 10 (x86, x64, and ARM64)
- Microsoft Server 2008R2, 2012, 2016, 2019
- Microsoft .NET 4.5, or above
- PowerShell 7 (only for Windows 7)
Configure Web Security Policies
- In this section we focus on the configuration of CSIA Web Security Policies within the administration console. This is the main place where we set actions on web categories.
Citrix Secure Internet Access Agent Configuration
- In this section we focus on the configuration and the installation of the Citrix Secure Internet Access (CSIA) Agent.
Troubleshooting
- Important Tools for Troubleshooting
1. Windows Event Log 2. CSIA Real-Time Dashboard (Reporting & Analytics > Real-Time Log) 3. CSIA Event Logs (Reporting & Analytics > Logs > Event Log) 4. CSIA IPS Logs (Reporting & Analytics > Logs > IPS Log) 5. Registration Information for Connected Devices (Users, Groups … - A Keyword is not Being Blocked
There is a multitude of policies and variables within and surrounding the operations of the CSIA cloud platform that can interfere with properly blocking configured keywords. Refer to the following; 1. Ensure that SSL decryption is active for this website. Keywords cannot be observe…
Appendix
- Main Category List
Note:Be careful with the “Not Rated” category, as it matches against many sites that are not categorized.