What the common Remote Access domain policies are?
Through remote access policies you can define the following: Grant or deny dial-in based on connection parameters such as type and time of the day. Authentication protocols (Password Authentication Protocol (PAP), CHAP, EAP, MS-CHAP) Validation of the caller id.
What should be included in a remote access policy?
What Should You Address in a Remote Access Policy?Standardized hardware and software, including firewalls and antivirus/antimalware programs.Data and network encryption standards.Information security and confidentiality.Email usage.Physical and virtual device security.Network connectivity, e.g., VPN access.More items...•
What constraints are available for use in a remote access policy?
Once a remote access policy has authorized a connection, it can also set connection restrictions (called constraints) based on the following: Encryption strength. Idle timeout. IP packet filters.
Why is a remote access policy definition a best practice for handling remote employees and authorized users who require Remote Access from home or on business trips?
A remote access policy aims to keep corporate data safe from exposure to hackers, malware, and other cybersecurity risks while allowing employees the flexibility to work from remote locations.
What is a access policy?
n. Principles or procedures that control the conditions under which individuals have permission and ability to consult a repository's holdings.
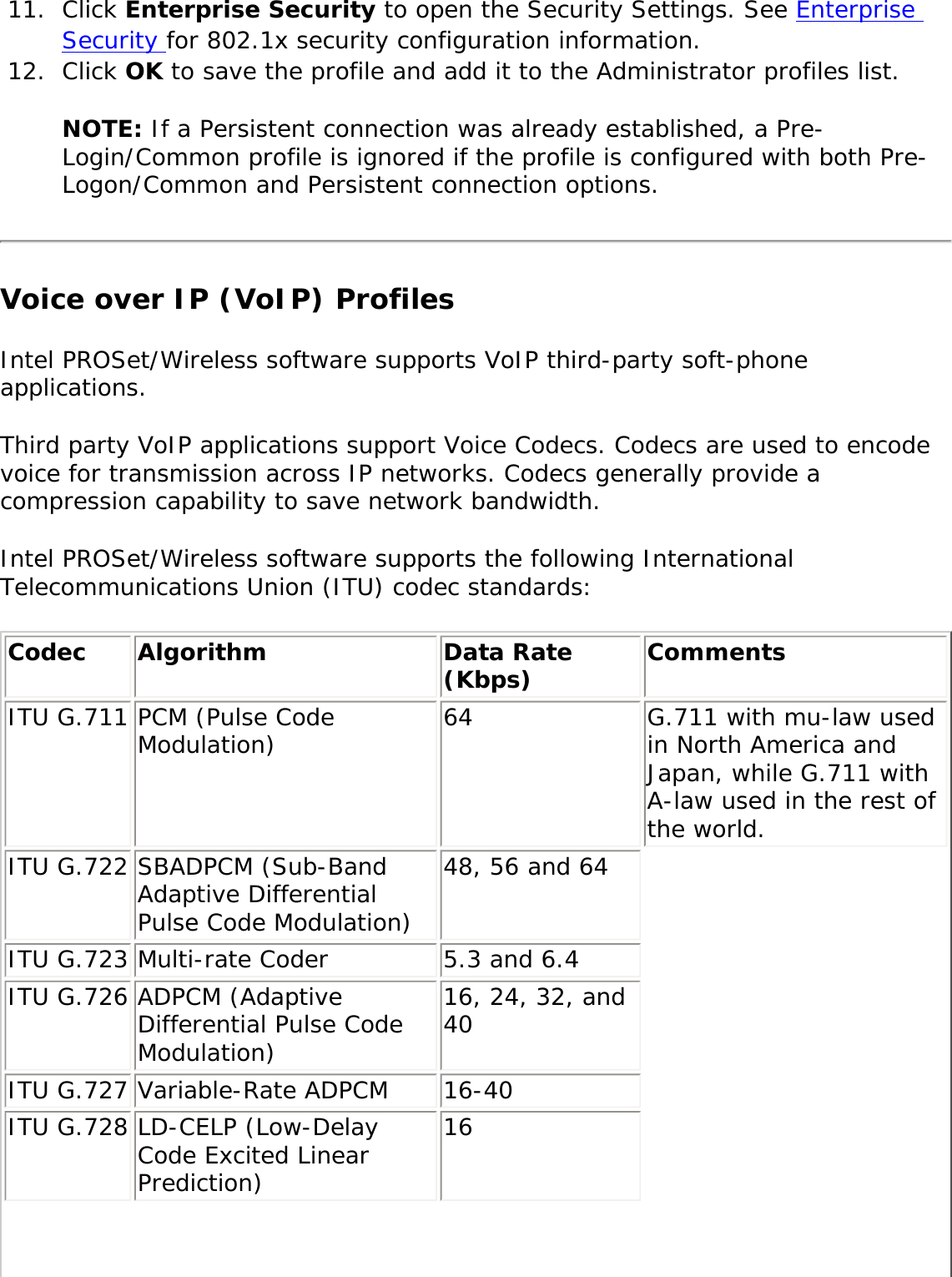
What is a network access policy?
Network policies are sets of conditions, constraints, and settings that allow you to designate who is authorized to connect to the network and the circumstances under which they can or cannot connect.
What is an example of acceptable use policy?
Refrain from monopolizing systems, overloading networks with excessive data, degrading services, or wasting computer time, connection time, disk space, printer paper, manuals, or other resources.
What security best practices are for connecting to remote systems?
7 Best Practices For Securing Remote Access for EmployeesDevelop a Cybersecurity Policy For Remote Workers. ... Choose a Remote Access Software. ... Use Encryption. ... Implement a Password Management Software. ... Apply Two-factor Authentication. ... Employ the Principle of Least Privilege. ... Create Employee Cybersecurity Training.
What is the use of policy?
A policy is a set of rules or guidelines for your organization and employees to follow in or to achieve compliance. Policies answer questions about what employees do and why they do it. A procedure is the instructions on how a policy is followed.
Why is it a best practice of remote access policy definition to require employees and fill in a separate VPN remote access authorization form?
Why is it a best practice of a remote access policy definition to require employees and users to fill in a separate VPN remote access authorization form? It is best practice of a remote access policy as it makes sure there are no repudiation of the user so that only authorized person can access the important documents.
Why you must create a remote access policy for VPN connectivity?
Remote access VPN can be an attractive ground for hackers and malicious attackers, so an organization's server must be protected by a security or network administrator. By having an effective VPN remote access policy, you can reduce the risk of your organization's network assets and support calls from end users.
What is a remote access standard?
PURPOSE. Remote Access refers to the ability to access UMW network resources while off campus. Security measures for remote access should be implemented based on sensitivity and risk to University systems and data.
Why you must create a remote access policy for VPN connectivity?
Remote access VPN can be an attractive ground for hackers and malicious attackers, so an organization's server must be protected by a security or network administrator. By having an effective VPN remote access policy, you can reduce the risk of your organization's network assets and support calls from end users.
Where are the implementation instructions defined in a remote access policy definition?
Where are the implementation instructions defined in a remote access policy definition? Does this section describe how to support the two different remote access users and requirements as described in this lab's XYZ Health Care Provider scenario? · The implementation instructions are defined in Remote Access Domain.
What is a VPN policy?
A VPN security policy is a policy that defines. just about everything that anyone would need to know about your VPN. It defines. things like who can use the VPN, what they can use it for, and what it is that. keeps them from using improperly or maliciously.